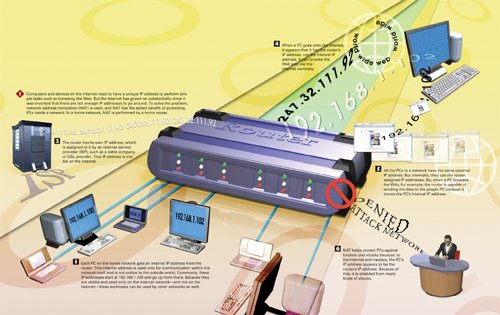
How Network Address Translation Protects Home Networks
 |
How Personal & Internet Security Works
ISBN: 0789735539
EAN: 2147483647
EAN: 2147483647
Year: 2004
Pages: 161
Pages: 161
Authors: Preston Gralla
- Case Study-Hub and Spoke MPLS VPN Network Using BGP PE-CE Routing for Sites Using Unique AS Numbers
- Option 2: Inter-Provider VPNs Using ASBR-to-ASBR Approach
- Option 3: Multi-Hop MP-eBGP Between RR and eBGP Between ASBRs
- MPLS QoS Implementation
- Case Study 4: Implementing Layer 3 VPNs over Layer 2 VPN Topologies and Providing L2 VPN Redundancy