Hack 72 Get a List of Local Administrators
| < Day Day Up > |
| Local administrators can do anything on their machines. Here's a quick way to determine who has this power . When an intruder penetrates a network's defenses, the intruder generally tries to elevate the privileges of his account to that of local administrator on the machine. Once the intruder has achieved this, he can do anything he wants to do on the machine. So, if you think your network defenses have been penetrated, it's a good idea during the triage stage to check which accounts are local administrators on your machines. Using the GUI, this can be done using the Local Users and Groups node in Computer Management, but that is tedious . A faster way to identify individuals who have local computer administrator rights is to use the following VBScript, which you can customize further as desired. The CodeJust open a text editor such as Notepad (make sure you have Word Wrap disabled), type the following code, and save it with a .vbs extension as GetAdmins.vbs : computername = createobject("wscript.network").computername set group = getobject("WinNT://" & computername & "/administrators,group") s = "" for each account in group.members s = s & account.name & vbcrlf next msgbox s Running the HackRunning the hack is simple. Just create a shortcut to it and double-click on the shortcut. A dialog box will display which user accounts are local administrators on the machine, as shown in Figure 8-3. From this list, you can easily detect any unauthorized administrator-level accounts, such as backd00r, that might indicate that the system has been compromised by a malicious hacker. Figure 8-3. A list of local administrators on a member server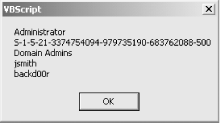 Make sure you have the latest scripting engines on the workstation from which you run this script. Download the latest scripting engines from the Microsoft Scripting home page (http://msdn.microsoft.com/library/default.asp?url=/nhp/default.asp?contentid=28001169). Note also that, when working with the Active Directory Services Interface (ADSI) you must have the same applicable rights you need to use the built-in administrative tools. Hacking the HackThe script gets the contents of the local administrators group, but you can easily alter the group information in the script to retrieve the information from any local computer group if you desire . For example, to display members of the Users group just change this line: set group = getobject("WinNT://" & computername & "/administrators,group") to this: set group = getobject("WinNT://" & computername & "/ users ,group") Then, run the hack again. Rod Trent |
| < Day Day Up > |