Lesson 3: Securing Connectivity Devices
Lesson 3: Securing Connectivity Devices
Many connectivity devices on your network have both physical components and logical configurations. A spy or an attacker might compromise both the physical components and the logical configuration of your network devices. In this lesson, specific network devices are examined with emphasis on ways in which these devices might be compromised, attacked, or in other ways exploited. Methods for increasing the security of these devices are also discussed in this lesson.
After this lesson, you will be able to
-
Describe exploitation and choose appropriate security measures for hubs, bridges or switches, and routers
-
Document ways in which a firewall could be compromised and select related security solutions
-
List the potential for private branch exchange (PBX) exploitations and choose appropriate methods for securing a PBX
-
Describe modem exploitations and select appropriate security measures
-
Explain the risks and choose the appropriate security measures for wireless networks
Estimated lesson time: 40 minutes
Hubs
You should already be familiar with hubs as connectivity devices on Ethernet networks. As you know, hubs can be active or passive. Active hubs repeat network signals and are sometimes referred to as multiport repeaters. Because hubs are central connectivity devices, they could be targets for attack. The remainder of this section focuses on how hubs can be compromised and secured.
Compromising Hubs
Hubs are simple to sabotage if the saboteur has physical access to the device. A hub can be disconnected or destroyed, or simply turned off, if it is an active hub. When a hub is disabled, the devices attached to it are unable to communicate.
Eavesdropping through a hub is also possible. If there is an open hub port or one of the legitimately connected devices can be disconnected, an attacker or spy could use the port to gain information or attack another device on the network. The open or disconnected port could be used to place a hacking device (or another computer to which the hacker has full control) to gather information from the network or to attack other devices.
Securing Hubs
Because hubs are physical devices, they should be physically protected. Try to lock hubs in wiring closets. If the hub cannot be locked in a room or closet, try to secure it in some other type of protective encasement. At a minimum, you should periodically check hubs to be sure that all cables are connected properly and that no rogue connections exist.
Managed hubs can be used to detect physical configuration changes. Managed hubs report hub statistics and connection information to management software. You can configure a managed hub to send an alert when a configuration is modified. Of course, because a managed hub has a (software) configuration, an attacker could compromise the hub's configuration to disrupt network communication or mask evidence of another attack.
Switches and Bridges
Switches and bridges communicate at the Data Link layer (Layer 2) of the Open Systems Interconnection (OSI) model. They make switching and bridging decisions based on the media access control (MAC) address of each network interface. Switches and bridges maintain tables that allow them to transfer packets to the appropriate network segment. Bridges are typically used to divide a network segment in half. Switches typically divide a network segment into many smaller segments, one segment for each port on the switch. These devices typically only separate unicast traffic; broadcast and multicast traffic is often allowed to pass through the bridge or switch (because these types of traffic are destined for multiple hosts). The remainder of this section covers compromising and securing switches and bridges.
You might see the terms Layer 3 and Layer 4 switching in marketing and technical documents from some networking vendors. If you carefully analyze descriptions of these devices, you should see that they are hybrid technologies that incorporate the functions of traditional switches and traditional routers. These devices are also called high-performance routers.
Compromising Switches and Bridges
As previously mentioned, switches and bridges maintain a table that contains MAC address mappings to each of their connection points. The table allows the switch or bridge to direct Layer 2 communications to the correct network segment or port, making it a potential target for attack. A central switch could also be the target of a saboteur. Destroying a central switch, disconnecting power, or disconnecting all of the network cables would disrupt all communications passing through the device.
Along the lines of disrupting communication, there are scripts such as macof that can be used to flood bridges and switches with random MAC addresses. Assuming the switch or bridge is able to learn new addresses, such an attack could reduce the performance of the switching or bridging device and slow network traffic.
Gaining Administrative Access
If an attacker can gain administrative access to the switch or bridge, he or she can reroute network communications. These communications can be redirected to a host on the network under the control of the attacker, which could be the attacker's system or a system the attacker was able to gain control over using some other technique. If the attacker decides to sabotage communications on the network, he or she can do so at any time once administrative access is obtained. Of course, the attacker must gain administrative access to the bridge or switch first. A skilled attacker can do this by trying default administrative passwords or running a password attack against the device. Switches in particular often have a function called port mirroring, which allows an administrator to map the input and output from one or more ports on the switch to a single port. This is meant to help in troubleshooting communication problems on a network. However, if an attacker is configuring port mirroring, he or she could watch all network traffic that passes through the switch. The attacker might do this to gather information about other systems on the network or in hopes of decoding a password or other valuable information, such as trade secrets.
Occasionally, connectivity devices might have software configuration problems or security vulnerabilities. For example, someone might discover that a switching table can be updated without any administrative authorization, meaning anyone could compromise your switch, if they had access to your network. Vendors usually resolve problems like these quickly once they are discovered. To protect your connectivity devices, be sure to keep track of vendor patches and install them when they are available.
ARP Cache Poisoning
Although switches and bridges segment the network, it might be possible for an attacker to use Address Resolution Protocol (ARP) cache poisoning (also known as ARP spoofing) to propagate traffic through a switch. ARP cache poisoning was introduced in Chapter 2 as a method for placing incorrect information in computers' ARP caches to misroute packets. The ARP cache is used to store Internet Protocol (IP) to MAC address mappings.
For an attacker to conduct ARP cache poisoning, he or she must typically gain physical connectivity to the local segment. The attacker must then compromise the ARP caches of the hosts on that segment. ARP cache poisoning involves overwriting entries in the ARP cache to cause a computer to send all network traffic directly to the attacker's computer. If an attacker is able to do this to all the computers on the segment, he or she could effectively listen to (and forward) data packets without network users realizing it. The attacker would then be able to listen to the network traffic sent on that network, most likely to steal trade secrets or obtain unencrypted passwords.
Attackers might use arpspoof (part of the dsniff toolset) to poison an ARP cache.
Securing Switches and Bridges
There are several measures you can take to prevent attacks against your switches and bridges. As with other network devices, you should physically secure them so they cannot be tampered with or destroyed. Here are other suggestions that can help to secure your switches and bridges:
-
Secure all physical connections on your network segments. Be sure that no unauthorized connections can be made. Also, limit physical access to your switch locations and use security personnel and monitoring devices to ensure connectivity devices are secure.
-
Set complex passwords for administrative consoles. Restrict device administration to as few people as possible from as few locations as possible. Also, be sure to change administrative passwords routinely and whenever an administrator leaves the company.
-
Manually enter ARP mappings on critical devices, such as central servers, switches, bridges, and so on. If you manually enter all necessary MAC addresses, prevent the switch or bridge from learning new addresses.
-
Keep your switches and bridges current with the latest vendor security patches.
-
Document your device configurations so you know for sure what is normal and authorized.
-
Monitor your network with management tools that alert you to unauthorized connections. Tools such as ARPWATCH can monitor activity on your network and keep a database of MAC-to-IP address mappings. The tool can also alert you to changes in these ARP mappings.
Routers
As you know, routers communicate at the Network layer (Layer 3) of the OSI reference model. Routers also maintain ARP caches and routing tables to perform their task of routing network packets. The remainder of this section focuses on ways in which routers can be compromised and secured.
Compromising Routers
As previously mentioned, routers maintain both ARP caches and routing tables. These tables allow the router to transfer and route communications appropriately on the network, and they are also potential points of attack. A central router might also be the target of a saboteur. Destroying a central router, disconnecting power, or disconnecting its network cables would disrupt all communications passing through the device.
Because routers maintain ARP caches, they could be susceptible to ARP cache poisoning. In addition to ARP caches, routers maintain routing tables that can be modified by a remote connection or a physical connection through a console cable to the router. Routing tables can also be updated automatically using a routing protocol. If an attacker is able to modify a routing table, network traffic could be misrouted to a host chosen by the attacker. If the host is under the attacker's control, it could be used to decode network packets (to steal or modify data). As stated earlier, you should secure and monitor physical connection points to your network to prevent ARP cache poisoning.
If an attacker can gain administrative access to the router, he or she can reroute communications on the network. These communications can be redirected to a host on the network under the control of the attacker, which could be the attacker's system or a system the attacker was able to gain control over using some other technique. If the attacker decides to sabotage communications on the network, he or she can do so at any time once administrative access is obtained. Of course, the attacker must gain administrative access to the router first. A skilled attacker can do this by trying default administrative passwords or running a password attack against the device.
Attackers could also utilize routing protocols such as the Routing Information Protocol (RIP) to update routing tables with bogus information. This is called RIP spoofing, and it is a problem for devices that utilize RIP version 1 (RIPv1). However, RIP version 2 (RIPv2) allows for passwords to be set at the routers. Therefore, on a RIPv2-enabled router an attacker would have to compromise the router's password to submit bogus routes.
As stated previously, connectivity devices might have software configuration problems or security vulnerabilities. For example, someone might discover that a router can be updated or disabled without any administrative authorization (meaning anyone could compromise your router, if they had access to your network). Vendors usually resolve problems like these quickly once they are discovered. To protect your connectivity devices, be sure to keep track of vendor patches and install them when they are available.
Securing Routers
A central router could also be the target of a saboteur. Destroying a central router, disconnecting power, or disconnecting all of the network cables would disrupt all communications passing through the device. To increase the security of your routers, consider the following suggestions:
-
Ensure the routers are kept in locked rooms or containers.
-
Check the security of all incoming and outgoing connections.
-
Limit physical access to your network cable infrastructure, wiring closets, and server rooms.
-
Use security personnel and monitoring equipment to protect connection points and devices.
-
Utilize complex passwords for administrative consoles. Be sure to change administrative passwords routinely and whenever an administrator leaves your organization.
-
Set access list entries to prevent inappropriate connections and routing of traffic. For example, packets with the IP address of your internal network should not be coming from the external interface on the router. If this happens, it is usually an indication that someone is trying to perform IP address spoofing as described in Chapter 2.
-
Keep your routers current with the latest vendor security patches.
-
Be sure to document and regularly review your network configuration.
-
Disable RIPv1 and utilize only RIPv2 or other routing protocols that allow you to secure router updates with passwords.
Firewalls
The term firewall is used generically to describe any device that protects an internal network (or host) from malicious hackers or software on an external network (or network to which the host is connected). Firewalls perform a variety of tasks to filter out potentially harmful incoming or outgoing traffic or connections. They are often implemented between an organization's internal network and the Internet. However, this is not always the case. Some firewalls are used to subdivide internal networks or even to protect individual computers.
The five main services that firewalls provide are packet filtering, application filtering, proxy server, circuit-level, and stateful inspection. These services are described in more detail in the following sections.
Packet Filtering
A packet filtering firewall or gateway checks each packet traversing the device. The firewall inspects the packet headers of all network packets going through the firewall. Packets are passed or rejected based on a set of predefined or administrator-defined rules. Packet filter rules can accept or reject network packets based on whether they are inbound or outbound, or due to the information contained in any of the following network data packet fields:
- Source IP Address.
This field is used to identify the host that is sending the packet. Attackers could modify this field in an attempt to conduct IP spoofing. Firewalls are typically configured to reject packets that arrive at the external interface bearing a source address of the internal network because that is either an erroneous host configuration or an attempt at IP spoofing.
- Destination IP Address.
This is the IP address that the packet is trying to reach.
- IP Protocol ID.
Each IP header has a protocol ID that follows. For example, Transmission Control Protocol (TCP) is ID 6, User Datagram Protocol (UDP) is ID 17, and Internet Control Message Protocol (ICMP) is ID 1.
A table listing common Protocol IDs can be found in Appendix B, "Ports and Protocol IDs."
- TCP or UDP Port Number.
The port number that indicates the service this packet is destined for, such as TCP port 80 for Web services.
A table listing common TCP and UDP ports can be found in Appendix B, "Ports and Protocol IDs."
- ICMP Message Type.
ICMP supports several different functions that help to control and manage IP traffic. Some of these messages can be used to attack networks, so they are frequently blocked at the firewall. For example, ICMP echo requests can be exploited to cause a broadcast storm. You can read more about ICMP message types in Request for Comments (RFC) 793. (RFC articles can be found at http://www.rfc-editor.org.)
- Fragmentation Flags.
IP fragmentation was described in detail in Chapter 2. Firewalls can examine and forward or reject fragmented packets. Some flawed implementations of TCP/IP allow for the reassembly of fragmented packets as whole packets (without receipt of the first packet, which contains the full header information). A successful fragmentation attack can allow an attacker to send packets that could compromise an internal host.
- IP Options Setting.
This field is used for diagnostics. The firewall should be configured to drop network packets that use this field. Attackers could potentially use this field in conjunction with IP spoofing to redirect network packets to their systems.
Application Filtering
An application filtering firewall intercepts connections and performs security inspections. The firewall must be equipped with the appropriate applications to perform this task. In this way, the firewall acts as a proxy for connections between the internal and external network. The firewall can check and enforce access control rules specific to the application. Application filtering firewalls are used to check incoming e-mails for virus attachments; these firewalls are often called e-mail gateways.
Proxy Server
Like an application filtering firewall, a proxy server takes on responsibility for providing services between the internal and external network. However, the proxy server can actually be the server providing the services or it can create a separate connection to the requested server. In this way, a proxy server can be used to hide the addressing scheme of the internal network. Proxy servers can also be used to filter requests based on the protocol and address requested. For example, the proxy server could be configured to reject incoming connections to http://www.internal.local or outgoing connections to http://www.external.net.
Circuit-Level
A circuit-level firewall controls TCP and UDP ports, but doesn't watch the data transferred over them. Therefore, if a connection is established, the traffic is transferred without any further checking.
Stateful Inspection
A stateful inspection firewall works at the Network layer. The firewall evaluates the IP header information and monitors the state of each connection. Connections are rejected if they attempt any actions that are not standard for the given protocol.
Any of these listed firewall features can be implemented in combination by a given firewall implementation. Placing multiple firewalls in series is a common practice to increase security at the network perimeter. If an attacker is able to breach the first firewall, the second offers additional protection. Using multiple firewalls in series (back-to-back) is one example of creating a defense-in-depth, as shown in Figure 4-1, which means that you are using multiple layers of protection to keep your network secure.
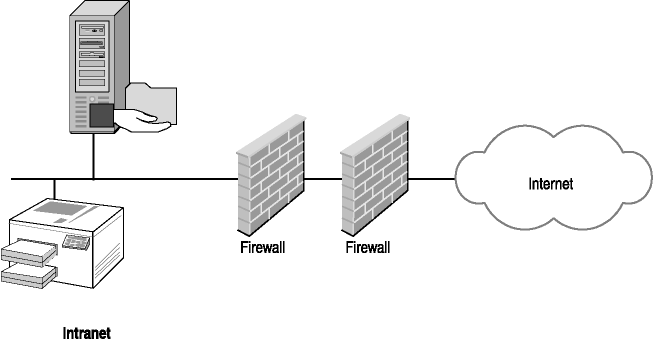
Figure 4-1. Defense-in-depth using multiple firewalls back-to-back
Another type of network infrastructure defense method is called defense-in-breadth, which refers to using multiple layers of protection with different configuration mechanisms. This means than an attacker requires a breadth of knowledge to exploit your layers of protection. For example, you could create a defense-in-breadth by using multiple firewalls in series from different manufacturers. The idea is that two firewall products from different manufacturers are less likely to be exploited than two firewall products from the same manufacturer.
Defense-in-depth and defense-in-breadth configurations go beyond placing multiple firewalls in series. Defense of the network can involve a combination of virus scanners, e-mail gateways, firewalls, secure host configurations, and routine security inspections.
Exploiting Firewalls
Poorly implemented firewall configuration is a common reason firewalls are compromised. For example, firewalls can be configured with a default-allow rule or a default-deny rule. The default-allow rule (also known as allow-all) means that a firewall permits all inbound network packets except those that are specifically prohibited. Network administrators and security personnel usually view this setting as too permissive. The other option is the default-deny rule, which rejects all inbound packets except those that are specifically permitted. This is the standard configuration of a secure firewall.
Flaws in firewall software are another reason firewalls are compromised. Usually, vendors release software patches or temporary solutions quickly after they are made publicly known. The following list describes other ways in which firewalls might be compromised:
- Compromising the firewall management console or password.
Firewalls can be configured through a management console. Management of the firewall might be restricted to a connection through a serial cable or it could be open to remote network connections. An attacker might try to gain access to the firewall through these administrative connections. If successful, the attacker could take control of the firewall.
- Circumventing the firewall.
If there is another way into the network, or another path can be created, then compromising the firewall would be as simple as using a different path. A dial-up connection from a server on your internal network, for example, could provide another path to your network.
- Physically tampering with the firewall.
If attackers can gain physical access to your firewall, they might attempt to disconnect it, reroute network cables to avoid it, or sabotage it in some other way.
Securing Firewalls
As described in the previous section, there are several ways an attacker might attempt to neutralize your firewall, so protecting it requires vigilance. To protect your firewall, follow this advice:
-
Keep track of security bulletins concerning your firewall product. Apply all software patches as they are made available.
-
Update virus definition files routinely.
-
Physically protect the firewall.
-
Document the firewall configuration and review that configuration regularly.
-
Limit the methods for managing the firewall. If remote management is allowed, use the most secure authentication available.
-
Use complex passwords. Be sure to change administrative passwords routinely, and always change them when an administrator leaves your organization.
-
Know and test the firewall rules by trying to make connections to unauthorized ports or services from outside the firewall.
-
Ensure that there are no network paths or connections that can be used to circumvent the firewall.
Remote Access
Remote Access Service (RAS) servers allow clients to use dial-up connections to access servers and internal networks. The RAS server typically has a modem (or bank of modems) that allows incoming connections from clients that might be compromised by an attacker. Compromises of RAS servers typically involve exploitation of the RAS software itself. These are usually the result of an oversight in the software programming by the RAS server vendor. The RAS server vendor should provide software patches to correct these programming flaws. Check for software patches from your RAS server and apply them as they are made available.
This section and the two that follow present a brief introduction to RAS as it relates to your network infrastructure. More in-depth coverage of these concepts is presented in Chapter 5, "Communications Security."
Attackers might also try to make unauthorized connections by guessing passwords. To protect against this, some RAS servers allow for password policies. When possible you should configure a password policy to lock out accounts after several incorrect logon attempts. Lockout settings are typically configured for three to five incorrect logon attempts, and the lockout period is often about 30 minutes. Such a policy helps prevent someone from successfully guessing a password. (You must ensure that user passwords are complex enough to prevent an attacker from guessing them with a limited number of guesses, however.)
Some RAS server implementations allow you to implement security measures that require some physical component or card (such as a smart card) that uses a digital certificate to grant access. Further, the access card itself typically requires a personal identification number (PIN) that is required to allow access. This is called two-factor authentication because the user must have the card (first factor) and know a PIN (second factor) to access the system.
Attackers might also attempt to decode passwords by packet sniffing connections from legitimate users. To do this, the attacker would have to eavesdrop on the dial-up circuit through which the user is connecting to your RAS server. This means the hacker must connect to the physical telephone line that is used to make the connection (or compromise a telephone switching device to propagate that information to the attacker). This is difficult and requires a highly skilled attacker. The best protection against such an exploitation would be to use strong authentication and data encryption between the client and RAS server.
TACACS+
Terminal Access Controller Access Control System Plus (TACACS+) is an authentication protocol that provides a method for a remote access client to authenticate with an RAS server. Authentication is used to determine whether a remote user should be allowed to access the network. The TACACS+ server can be configured with an access control list or it can contact a central server, such as a UNIX Network File Service (NFS) server running Network Information Service (NIS). NFS is the standard file sharing mechanism used by UNIX servers. An NIS server provides a master accounts database for users on a UNIX-based network.
Previous versions of TACACS+ were TACACS and XTACACS. Although they share similar names and have the same goals, the older versions are not compatible with the newer TACACS+ protocol.
The TACACS authentication system started with UNIX. Today it is used in both UNIX and non-UNIX network devices (such as routers) that provide remote access. Users authenticate with a TACACS+ server by providing a user name and password. TACACS+ allows for Challenge Handshake Authentication Protocol (CHAP) encrypted passwords. CHAP is an algorithm that is used to encrypt passwords that are passed between two points, protecting them from eavesdropping attacks. TACACS+ encrypts the entire authentication packet between the TACACS+ client and server.
RADIUS
Remote Authentication and Dial-In User Service (RADIUS) is a protocol similar to TACACS that provides authentication to RAS connection attempts. RADIUS is a widely supported protocol standardized by the Internet Engineering Task Force (IETF). RADIUS servers can provide authentication to remote access connections using their own internal user database. RADIUS servers can also be configured as RADIUS proxy servers, which are able to authenticate against another RADIUS server or RADIUS-enabled directory service. RADIUS servers and clients are also capable of supporting CHAP to encrypt password exchanges.
Figure 4-2 illustrates possible RADIUS and RADIUS proxy server authentication. The RADIUS server can grant remote access from its own local database or be configured to contact another directory service, such as UNIX NIS, Novell NetWare e-Directory, or Microsoft's Active Directory service. Users dial in remotely to the appropriate dial-in location. Authentication is relayed to the RADIUS server. If the RADIUS server is a RADIUS proxy server, it consults the appropriate directory service accounts database.
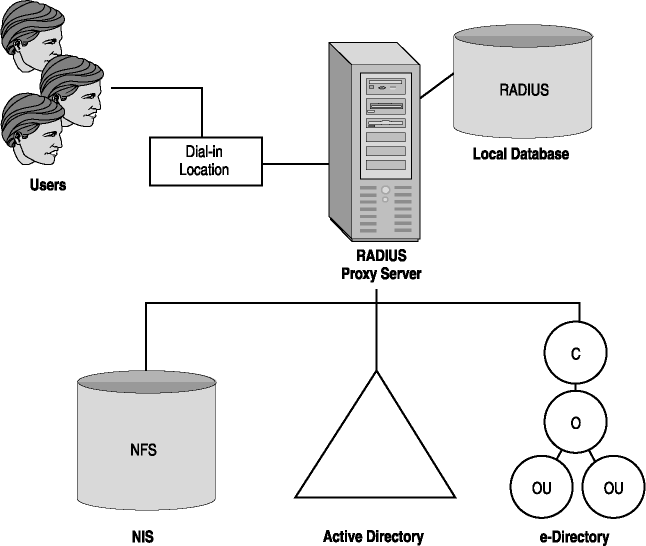
Figure 4-2. RADIUS and RADIUS proxy authentication services
Shiva Access Manager and Cisco Secure ACS are examples of products that support both the RADIUS and TACACS+ protocols.
Telecommunications Hacking
Telecommunications systems provide internal phone services for many organizations. These private telecommunications systems are known as PBX systems. They usually offer a variety of features such as voice mail, multiple-party calling, long-distance access restrictions, and call tracking. PBX systems are potential targets for attackers. Attackers who gain unauthorized access to the PBX system could potentially use it to do the following:
-
Make free long-distance calls by changing billing records.
-
Compromise or shut down the organization's voice mail system.
-
Reroute incoming, transferred, or outgoing calls.
-
Compromise the rest of your organization's network, as PBX systems are part of your network infrastructure. For example, locate a modem-equipped PC. Use that PC to create an analog connection to the internal network, and then use the analog connection to access the internal network.
Hacking PBX Systems
PBX systems are frequently an organization's most valuable communication asset. If the PBX system is compromised, the organization could lose business. There are relatively few brands of PBX systems available, so an attacker could use knowledge of a few select systems to compromise a wide variety of businesses. Although PBX systems are complex, a skilled attacker could use the system to compromise your network infrastructure. There are a variety of methods that an attacker might use to compromise the PBX system:
-
PBX systems come with default passwords for system maintenance. Attackers could run password attacks to guess these PBX maintenance passwords. Once an attacker acquires a management password, he or she can reconfigure the PBX system.
-
PBX systems are often expensive and upgrades are difficult. Therefore, many businesses use older PBX systems that might have unencrypted databases with obvious data structures that could be manipulated.
-
PBX security is not as popular a topic as computer security. Many businesses don't think to protect their PBX systems or know how to do so. Users might be tricked into giving up passwords for the telephone system because awareness of exploitation is not as high as it is with computer systems.
-
Remote management and upgrades of PBX systems are commonplace. Remote connections could be used to install malicious software or reconfigure the PBX system.
-
Many people use and have access to the PBX-connected telephones. These terminals could be used to attack or reconfigure the PBX system.
-
Telecommunications infrastructure might extend into unused floors and offices, making it easier for someone to hide an unauthorized connection (or conceal hacking attempts).
Protecting Your PBX
Physically securing PBX equipment should be a high priority. Ensure that access to the main PBX wiring room and switching equipment is controlled. The telecommunications infrastructure should be carefully documented and routinely checked for unauthorized connections. Other items to consider when protecting your PBX system are as follows:
-
Shut down or secure off-site transfers with passwords. Off-site transfers are typically enabled so that the vendor or a contracted service provider can update your PBX automatically. Attackers could exploit this system to reconfigure your PBX.
-
Program system exclusion lists to limit long-distance calling. Consider blocking 900 numbers and other toll numbers.
-
Program system schedules to shut down services that are not required during off hours and days.
-
Educate users about PBX security. Ask users not to write down passwords or program their phones with passwords in auto-dial. Tell users to clear phones that display dialed numbers after resetting passwords (so their password is not stored in the redial feature of the phone).
-
Enforce a PBX password change and audit policy. Ensure that passwords are not left at default values and that they are routinely changed.
-
Audit PBX access to ensure that former employees, partners, and contractors who no longer need access are removed from the system.
-
Secure maintenance ports and limit the number of entry points. Disable unnecessary remote management features. Implement the highest available security features for maintenance and remote management.
-
Routinely check for vendor software and hardware updates, and verify all software updates to the PBX system.
-
Log maintenance, software updates, remote management, and all other system access.
-
Consider implementing a dynamic telemanagement system that tracks system access, checks for fraud, and performs audits. It can also alert you to unauthorized usage and log suspicious usage.

Modems
Modems connect computers to the Internet and to private networks, but those connections could be susceptible to compromise or attack. As explained earlier, modems can be used to circumvent the security provided by your organization's firewall and other security devices. Modems can provide direct access to a system on a network and potentially be used to access other systems on that network. Exploited modem dialing software can be used to erase hard drives or cause the modem to dial emergency services, for example.
To protect your network from modem exploits, follow these procedures:
-
Remove all unnecessary modems from computers on your network.
-
Check for software updates for all computers that must have modems.
-
Monitor security bulletins from modem vendors for newly discovered security gaps and apply software patches as soon as they are available.
-
Isolate computers configured with modems to limit the damage that can be caused by those systems should the modem be compromised.
-
Monitor computers with modems regularly to ensure they have not been compromised.
Wireless
Many different manufacturers have released wireless access points (APs) that can be used with wireless network cards. The communication between the AP and the network card travels as radio or infrared signals through the air. Attackers who are as far as more than a mile away from the AP could potentially intercept these signals. There is no need for the attacker to splice into wires or add connectivity devices to gain access to a wireless network in this way. APs can also function as hubs, switches, and routers and are therefore vulnerable to the same exploits mentioned earlier concerning those devices.
There is a growing trend of people driving around neighborhoods and business areas with wireless network identification equipment to locate APs. These people then mark and map places where they can gain free Internet access. This trend makes the implementation of wireless networks even more dangerous because it could open your network up to individuals and equipment beyond your control. For this reason, the United States Federal Bureau of Investigation (FBI) and the Computer Emergency Response Team (CERT) urge individuals and businesses to use the most secure authentication and encryption on their wireless networks.
There are numerous exploits that compromise wireless networks. Many wireless network devices allow you to enable strong authentication and encryption mechanisms to prevent unauthorized network access and packet sniffing. However, additional "hacker tools" are available that could allow attackers to compromise data encryption, steal passwords, and even hijack (or take over) sessions between clients and servers. To keep a wireless network reasonably secure you must stay current on the latest security bulletins and vendor patches. You should also implement the most secure authentication and encryption methods available.
IEEE 802.11b defines a method for user authentication called Extensible Authentication Protocol over LANs (EAPOL). EAPOL allows vendors to provide a standard method for granting access to authorized wireless users. Most APs allow you to secure authentication by allowing you to set a specific access code on the wireless network interface card (NIC) and AP. Most wireless vendors also support Wired Equivalent Privacy (WEP) encryption, which allows you to configure a shared key to encrypt communications between the wireless NIC and the AP. Specifications for authentication and access are evolving quickly, so you should check the wireless vendors (such as Linksys, NetGear, Cisco, and Dlink) for the latest security improvements before implementing a wireless network. Another potential method for increasing wireless security is to implement your wireless networks in a location that is designed to reduce signal leakage, such as an underground facility with thick walls.
Wireless networks can also be interrupted by EMI and RFI and the only real countermeasure to that is a stronger signal. This is something the wireless user or administrator can typically only control by purchasing an AP that offers a stronger signal. When laying out a wireless network you should ensure that you don't place workstations or APs near any obvious sources of EMI and RFI, such as elevators, copier machines, radio transmitters, or industrial equipment.

Match the equipment exploits in the left column with the appropriate devices in the right column. Some exploits can be used on multiple device types.
|
|

The following questions are intended to reinforce key information presented in this lesson. If you are unable to answer a question, review the lesson and then try the question again. Answers to the questions can be found in Appendix A, "Questions and Answers."
-
List security issues that are common to managed hubs, switches, and routers.
-
Describe security issues that are common to switches and routers.
-
How might an attacker compromise a firewall implementation?
-
List ways in which a PBX can be compromised.
-
What are the security implementations available for wireless networks?
Lesson Summary
-
Physically secure as much of your network infrastructure as possible. This includes locking central connectivity devices in rooms or protective enclosures.
-
Managed devices on your network infrastructure can be vulnerable to password guessing attacks. Any device that can be managed locally and especially remotely should be configured with the most secure authentication and encryption available.
-
Monitor software and hardware vendor Web sites and bulletins for information on security exploits. You should apply all available security fixes as soon as possible.
-
Configure managed devices such as hubs, switches, routers, PBX systems, and firewalls to alert you of unauthorized connections.
-
Configure the most secure authentication and encryption on all wireless devices.
-
Ensure that your firewall virus definition files are routinely updated.
-
Document your network infrastructure, including the configuration of all connectivity devices, computers with modems, PBX system configuration, and all network cable attachments.
-
Routinely audit your network infrastructure to ensure there are no unauthorized connections, configurations, or devices.
EAN: 2147483647
Pages: 55