Securing Management Access
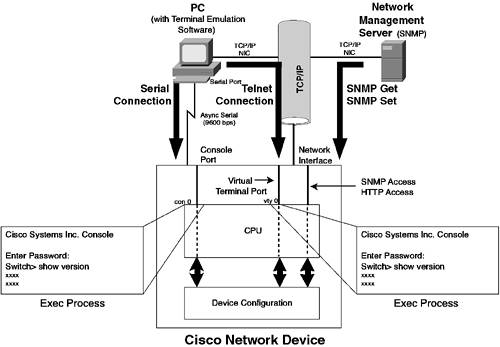
| Cisco networking devices provide rich management access capabilities that give the network administrator powerful configuration and diagnostics tools. The most common form of management access to a Cisco networking device is via an EXEC session. An EXEC session is similar to a UNIX shell and is accessible via Telnet, secure shell, or the console port. Cisco devices also support management via Simple Network Management Protocol (SNMP) and Hypertext Transfer Protocol (HTTP). Figure 8-1 illustrates the various management interfaces and how they interact with a Cisco switch. Figure 8-1. Cisco Management Interfaces
The first step to securing your switching infrastructure is to secure the switch's management interfaces. Next, you should implement techniques that improve the overall security of the switch. The following switch security techniques are available:
Configuring Authentication, Authorization, and Accounting (AAA)The default authentication policy on a Cisco CatOS switch is extremely lax. Cisco IOS-based switches are slightly more secure by default, but the security of both platforms can be significantly improved. Table 8-1 shows the default authentication methods for accessing a CatOS and IOS switch.
Table 8-1 represents the access policy for obtaining management access to the switch. Since default passwords should never be used in a production environment, the first thing you should do is configure passwords for all access methods (e.g., console, Telnet) and then configure an enable secret to protect privileged access. You can further secure switch management access through the implementation of the techniques detailed in Table 8-2.
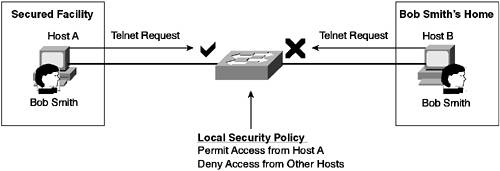
Restricting Management AccessIn most networks, only a select handful of people need management access to switches. CatOS and Cisco IOS allow you to restrict which hosts can establish management sessions based on the source IP address. NOTE Known as host-based authentication, this type of access control is extremely weak because any user on the allowed host could establish a management session. Host-based authentication should be used only to supplement user-based authentication mechanisms. Figure 8-2 illustrates restricting management access. Figure 8-2. Restricting Management Access
Through the use of permit lists on CatOS and access classes on IOS, management sessions can be controlled on a source IP address basis for the following protocols:
Using Secure Management ProtocolsIn previous sections, we discussed secure access control mechanisms. Most of the time, management access is remote, which means that management communications are passed through the network. These communications could contain sensitive information, such as username/password combinations or device configuration information. If your management communications are transmitted in clear text, it is possible for other parties on the network to eavesdrop on your management session, gleaning sensitive information such as a username/password pair. To circumvent this issue, you need to employ secure management protocols that protect the confidentiality of your management session. Table 8-3 details the secure management protocols available on CatOS and IOS devices.
Reducing Other VulnerabilitiesSo far we have discussed switch access methods and protocols; now you can leverage a few other configuration tips to protect against some of the less common security vulnerabilities.
|
EAN: 2147483647
Pages: 135