Managing BusinessObjects Enterprise System Settings
| The BusinessObjects Enterprise Settings area contains a number of system wide settings that aren't specific to a particular server. Information on system properties, metrics, clustering, instance limits, and user rights are available in this section. To configure system settings, select Settings from the Crystal drop-down menu in the CMC. Managing AuthenticationThere are two key components to managing BusinessObjects Enterprise authentication:
The first one is a less technical topic but still important to understand. The second is discussed in subsequent sections. Managing LicensingThe License Keys tab displays important information about each license key (see Figure 27.45). Highlight a license key to display specific information about the key. BusinessObjects Enterprise supports three types of licensing: named licenses, concurrent licenses, and processor licenses. Figure 27.45. The License Keys tab provides information about each of the BusinessObjects Enterprise license keys.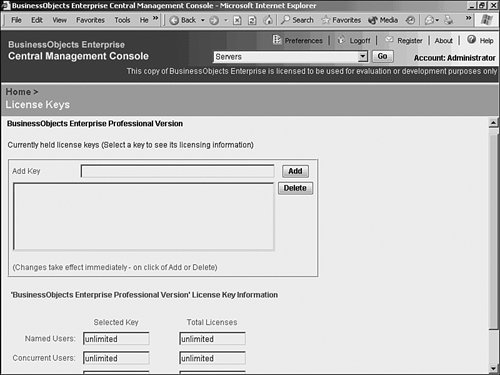 Note The license certificate keys determine the number and type of licenses available (name user or concurrent access). During the initial install of BusinessObjects Enterprise, a license key was entered. Additional licenses can be added to BusinessObjects Enterprise from the License Keys tab on the Authentication section of the CMC. BusinessObjects Enterprise gives you the flexibility to mix and match named and concurrent license types. Named licenses are assigned to specific users. Any number of named licenses can be simultaneously logged in to the system. Concurrent licenses permit an unlimited number of named users to be added to the BusinessObjects Enterprise, but only a certain number of those users can access the system simultaneously. Processor licenses enable an unlimited number of both named and concurrent users for a specific processor. Processor licenses are most efficient in high-powered server environments where the server CPU is robust enough to support a large number of concurrent users. It's best to contact Business Objects and discuss the optimum licensing strategy for your organization. Managing AuthenticationThe different types of authentication that can be leveraged with BusinessObjects Enterprise are also found under the Authorization portion of the CMC. BusinessObjects Enterprise provides several authentication models for providing secure report access, including Native BusinessObjects Enterprise authentication, Windows NT Authentication, Active Directory authentication, and LDAP authentication. BusinessObjects Enterprise supports single sign-on for both the Windows NT and Active Directory methods, so users won't have to constantly enter credentials after exiting and reentering the system. The reason BusinessObjects Enterprise supports more security models than its own is simple: If an IT organization has already implemented an existing security model, it is more efficient to leverage existing entities such as user accounts and passwords. Fortunately, none of these options is mutually exclusive; they can all be used simultaneously. This can cause some management headaches, so proceed with caution. Every topic in this chapter up until this point, with the exception of the Page Server, has used native BusinessObjects Enterprise security as an example. This does not imply that if Windows Active Directory authentication is used, for example, that administration is done exclusively from Active Directory. It simply implies that objects such as user accounts and passwords can be maintained within Active Directory, yet BusinessObjects Enterprise feeds off those existing accounts when users try to retrieve reports. The configuration of BusinessObjects Enterprise groups and objects, as well as relevant restrictions to those objects, are still created and configured from the CMC, in the same way that this chapter has shown. This is reviewed in greater detail later. To configure system authentication settings, select Authentication from the drop-down menu in the CMC. BusinessObjects Enterprise AuthenticationBusinessObjects Enterprise provides its own native security model. This means that BusinessObjects Enterprise is not dependent on a foreign, third-party security database to configure and restrict access to any system function, object, or entity. The BusinessObjects Enterprise authentication model is the default model. To leverage another security database, select the appropriate tab. Selecting the Enterprise tab, shown in Figure 27.46, enables you to enforce password rules when using BusinessObjects Enterprise authentication. You can use this tab to control the frequency that users are forced to change their passwords, as well as the length of the passwords and whether or not the password must contain mixed-case letters. Figure 27.46. You can set BusinessObjects Enterprise password expiration rules on the Enterprise tab. This tab only applies to the BusinessObjects Enterprise native authentication method, not LDAP or Windows NT.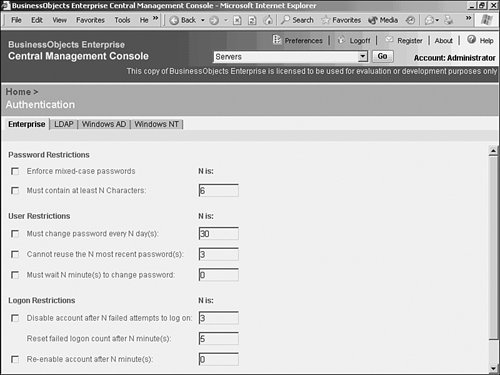 In general, the password options offered are similar to those provided by the Windows NT and Solaris operating systems. Directory Server Authentication Through LDAPSelecting the LDAP tab enables a system administrator to configure LDAP connectivity to a directory server, as shown in Figure 27.47. LDAP (Lightweight Directory Access Protocol) enables a network administrator to maintain a central directory server for managing user access to a variety of applications and operating systems. BusinessObjects Enterprise can be configured to work with a variety of directory servers via LDAP. BusinessObjects Enterprise support for LDAP was designed and tested to the LDAP version 3 specification. Figure 27.47. Configuring LDAP enables BusinessObjects Enterprise to connect to a Directory server, such as Netscape iPlanet, and leverage existing usernames and passwords.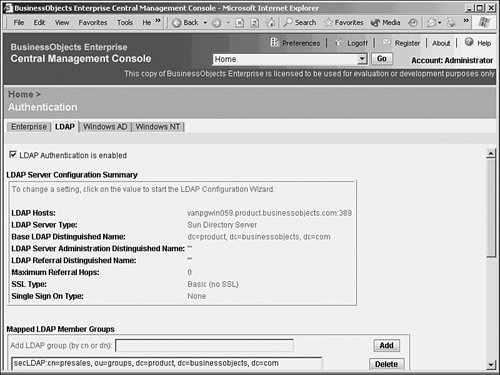 BusinessObjects Enterprise can tie into an LDAP server for User and Group information. Folder and Object permissions (that is, authorization) are still defined within BusinessObjects Enterprise. When BusinessObjects Enterprise is tied to an LDAP server, equivalent BusinessObjects Enterprise accounts are either created, if they don't already exist, or aliased if they do exist. The BusinessObjects Enterprise system must have references to users and groups inside the system such that report object restrictions can be configured. User passwords are not stored in BusinessObjects Enterprise. When using LDAP, it's the job of the directory server to verify passwords. Any time a user attempts to access BusinessObjects Enterprise resources, a password confirmation request is sent to the directory server. If the user authenticates properly, BusinessObjects Enterprise then compares the user's group membership and associated privileges assigned to those groups in BusinessObjects Enterprise. If, for example, a large number of users and groups were added to the directory server and the BusinessObjects Enterprise administrator needed to configure BusinessObjects Enterprise security settings, clicking the Update button on the LDAP page forces synchronization. Windows NT or Active Directory AuthenticationBusinessObjects Enterprise provides the capability to tie in user authentication to the Windows NT or Active Directory security model. If the primary network operating system and application authentication method in an organization is Windows NT or Active Directory, this feature can be a useful timesaver. Although there are material differences between the methods, they are similar enough to be discussed as Windows authentication. Windows authentication can be configured from the Windows AD or NT tabs, as shown in Figure 27.48. To enable Windows authentication, select the Is Enabled option. Enter the name of the Default Domain. The default domain should be the same domain that contains the majority of the Windows users that will also be BusinessObjects Enterprise end users. Figure 27.48. Selecting the Windows AD tab enables you to configure BusinessObjects Enterprise to support Active Directory authentication.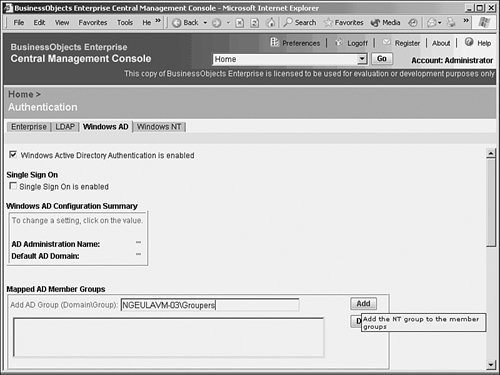 Users who do not have accounts in the specified default domain need to specify their domain name each time they log in to BusinessObjects Enterprise. The Mapped Member Groups section enables specification of which Windows user groups are permitted to access BusinessObjects Enterprise. Any Windows users who belong to mapped Windows member groups are able to log in to BusinessObjects Enterprise using single sign on. Users who are not a member of at least one mapped Windows group will not be able to access BusinessObjects Enterprise unless the administrator has specifically created a BusinessObjects Enterprise user ID for them in the CMC. To import a new Windows group to BusinessObjects Enterprise, type in the name of the Windows group (preceded by the group's domain or machine name) and click the Add button. Remember to click the Update button when you're finished adding or removing Windows groups. The bottom of the Windows tab has two additional options for configuring NT integration. Assign Each Added Windows Alias to an Account with the Same Name forces BusinessObjects Enterprise to match imported Windows usernames with existing BusinessObjects Enterprise usernames. If BusinessObjects Enterprise already has a username with the same name as an incoming Windows username, the two usernames are mapped to each other so that a duplicate account name is not created. In other words, an alias is created. On the other hand, the Create a New Account for Every Added Windows Alias option causes BusinessObjects Enterprise to add a new BusinessObjects Enterprise username for each incoming Windows username. If a duplicate username exists in BusinessObjects Enterprise, an alias is not created; instead, a new username is created with a slightly different name. When the group is added, navigate to the Manage Groups section of the CMC. Note that \\NGEULAVM-03\RUHI is now listed as a group within BusinessObjects Enterprise. Selecting this user group allows access to the same options as a native BusinessObjects Enterprise group. Managing Crystal ApplicationsBusinessObjects Enterprise allows for the configuration of applications via a central location which simplifies system administration. For instance, setting default colors or preferences (even setting a custom logo for InfoView!) can be accomplished from this location. As more applications, such as the Ad-Hoc application, are installed, these applications also add to this section. By default, the InfoView area appears to allow configuration of the InfoView's preferences (see Chapter 23, "Introduction to BusinessObjects Enterprise," for more information on the Web Desktop, and Chapter 21, "Using Reports Explorer for Ad Hoc Web Reporting and Microsoft Integration," for more information on the ad hoc application). These settings become global for this installation. |
EAN: 2147483647
Pages: 365