Common principles of service-orientation
In Chapter 3 we established that there is no single definition of SOA. There is also no single governing standards body that defines the principles behind service-orientation. Instead, there are many opinions, originating from public IT organizations to vendors and consulting firms, about what constitutes service-orientation.
Service-orientation is said to have its roots in a software engineering theory known as "separation of concerns." This theory is based on the notion that it is beneficial to break down a large problem into a series of individual concerns. This allows the logic required to solve the problem to be decomposed into a collection of smaller, related pieces. Each piece of logic addresses a specific concern.
This theory has been implemented in different ways with different development platforms. Object-oriented programming and component-based programming approaches, for example, achieve a separation of concerns through the use of objects, classes, and components.
Service-orientation can be viewed as a distinct manner in which to realize a separation of concerns. The principles of service-orientation provide a means of supporting this theory while achieving a foundation paradigm upon which many contemporary SOA characteristics can be built. In fact, if you study these characteristics again, you will notice that several are (directly or indirectly) linked to the separation of concerns theory.
As previously mentioned, there is no official set of service-orientation principles. There are, however, a common set of principles most associated with service-orientation. These are listed below and described further in this section.
- Services are reusable Regardless of whether immediate reuse opportunities exist, services are designed to support potential reuse.
- Services share a formal contract For services to interact, they need not share anything but a formal contract that describes each service and defines the terms of information exchange.
- Services are loosely coupled Services must be designed to interact without the need for tight, cross-service dependencies.
- Services abstract underlying logic The only part of a service that is visible to the outside world is what is exposed via the service contract. Underlying logic, beyond what is expressed in the descriptions that comprise the contract, is invisible and irrelevant to service requestors.
- Services are composable Services may compose other services. This allows logic to be represented at different levels of granularity and promotes reusability and the creation of abstraction layers.
- Services are autonomous The logic governed by a service resides within an explicit boundary. The service has control within this boundary and is not dependent on other services for it to execute its governance.
- Services are stateless Services should not be required to manage state information, as that can impede their ability to remain loosely coupled. Services should be designed to maximize statelessness even if that means deferring state management elsewhere.
- Services are discoverable Services should allow their descriptions to be discovered and understood by humans and service requestors that may be able to make use of their logic.
Of these eight, autonomy, loose coupling, abstraction, and the need for a formal contract can be considered the core principles that form the baseline foundation for SOA. As explained in the How service-orientation principles inter-relate section later in this chapter, these four principles directly support the realization of other principles (as well as each other).
There are other qualities commonly associated with services and service-orientation. Examples include self-descriptive and coarse-grained interface design characteristics. We classify these more as service design guidelines, and they are therefore discussed as part of the design guidelines provided in Chapter 15.
Note
You may have noticed that the reusability and autonomy principles also were mentioned as part of the contemporary SOA characteristics described in Chapter 3. This overlap is intentional, as we simply are identifying qualities commonly associated with SOA as a whole as well as services designed for use in SOA. We further clarify the relationship between contemporary SOA characteristics and service-orientation principles in Chapter 9.
To fully understand how service-orientation principles shape service-oriented architecture, we need to explore the implications their application will have on all of the primary parts that comprise SOA. Let's take a closer look at each of the principles.
8.3.1. Services are reusable
Service-orientation encourages reuse in all services, regardless if immediate requirements for reuse exist. By applying design standards that make each service potentially reusable, the chances of being able to accommodate future requirements with less development effort are increased. Inherently reusable services also reduce the need for creating wrapper services that expose a generic interface over top of less reusable services.
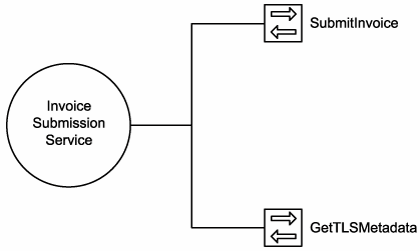
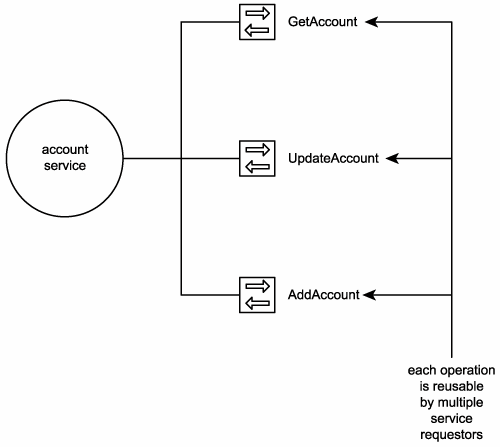
This principle facilitates all forms of reuse, including inter-application interoperability, composition, and the creation of cross-cutting or utility services. As we established earlier in this chapter, a service is simply a collection of related operations. It is therefore the logic encapsulated by the individual operations that must be deemed reusable to warrant representation as a reusable service (Figure 8.13).
Figure 8.13. A reusable service exposes reusable operations.
Messaging also indirectly supports service reusability through the use of SOAP headers. These allow for messages to become increasingly self-reliant by grouping metadata details with message content into a single package (the SOAP envelope). Messages can be equipped with processing instructions and business rules that allow them to dictate to recipient services how they should be processed.
The processing-specific logic embedded in a message alleviates the need for a service to contain this logic. More importantly, it imposes a requirement that service operations become less activity-specificin other words, more generic. The more generic a service's operations are, the more reusable the service.
8.3.2. Services share a formal contract
Service contracts provide a formal definition of:
- the service endpoint
- each service operation
- every input and output message supported by each operation
- rules and characteristics of the service and its operations
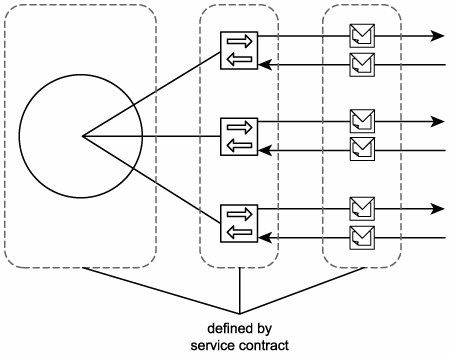
Service contracts therefore define almost all of the primary parts of an SOA (Figure 8.15). Good service contracts also may provide semantic information that explains how a service may go about accomplishing a particular task. Either way, this information establishes the agreement made by a service provider and its service requestors.
Figure 8.15. Service contracts formally define the service, operation, and message components of a service-oriented architecture.
Because this contract is shared among services, its design is extremely important. Service requestors that agree to this contract can become dependent on its definition. Therefore, contracts need to be carefully maintained and versioned after their initial release.
As explained in Chapter 5, service description documents, such as the WSDL definition, XSD schemas, and policies, can be viewed collectively as a communications contract that expresses exactly how a service can be programmatically accessed.
8.3.3. Services are loosely coupled
No one can predict how an IT environment will evolve. How automation solutions grow, integrate, or are replaced over time can never be accurately planned out because the requirements that drive these changes are almost always external to the IT environment. Being able to ultimately respond to unforeseen changes in an efficient manner is a key goal of applying service-orientation. Realizing this form of agility is directly supported by establishing a loosely coupled relationship between services (Figure 8.16).
Figure 8.16. Services limit dependencies to the service contract, allowing underlying provider and requestor logic to remain loosely coupled.
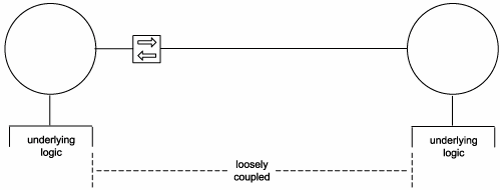
Loose coupling is a condition wherein a service acquires knowledge of another service while still remaining independent of that service. Loose coupling is achieved through the use of service contracts that allow services to interact within predefined parameters.
It is interesting to note that within a loosely coupled architecture, service contracts actually tightly couple operations to services. When a service is formally described as being the location of an operation, other services will depend on that operation-to-service association.
8.3.4. Services abstract underlying logic
Also referred to as service interface-level abstraction, it is this principle that allows services to act as black boxes, hiding their details from the outside world. The scope of logic represented by a service significantly influences the design of its operations and its position within a process.
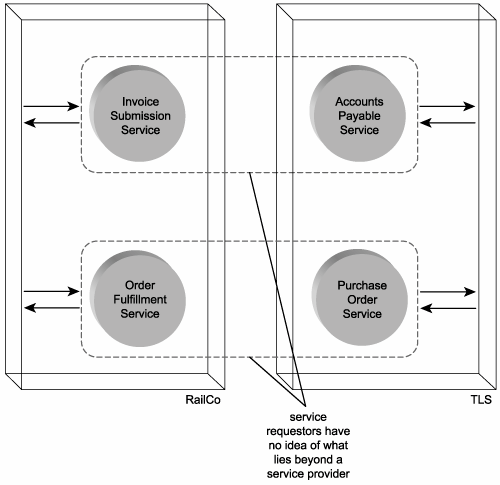
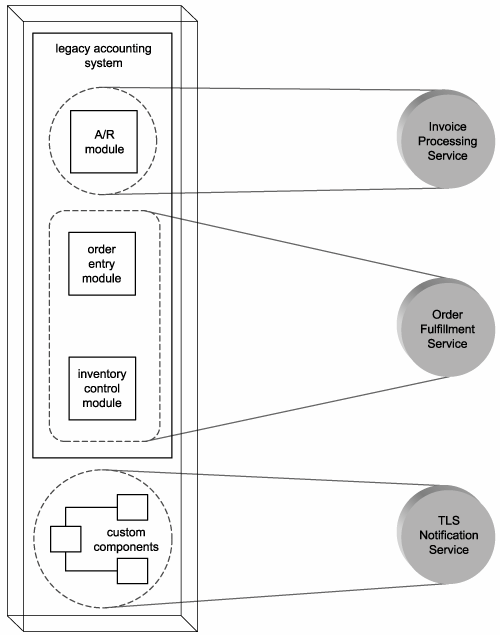
There is no limit to the amount of logic a service can represent. A service may be designed to perform a simple task, or it may be positioned as a gateway to an entire automation solution. There is also no restriction as to the source of application logic a service can draw upon. For example, a single service can, technically, expose application logic from two different systems (Figure 8.17).
Figure 8.17. Service operations abstract the underlying details of the functionality they expose.
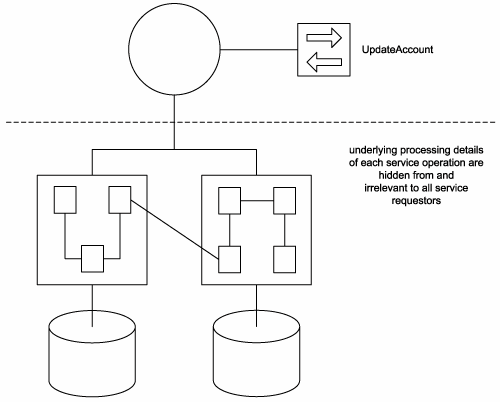
Operation granularity is therefore a primary design consideration that is directly related to the range and nature of functionality being exposed by the service. Again, it is the individual operations that collectively abstract the underlying logic. Services simply act as containers for these operations.
Service interface-level abstraction is one of the inherent qualities provided by Web services. The loosely coupled communications structure requires that the only piece of knowledge services need to interact is each others' service descriptions.
8.3.5. Services are composable
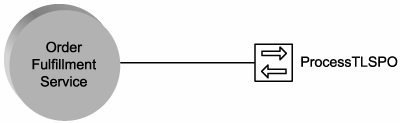
A service can represent any range of logic from any types of sources, including other services. The main reason to implement this principle is to ensure that services are designed so that they can participate as effective members of other service compositions if ever required. This requirement is irrespective of whether the service itself composes others to accomplish its work (Figure 8.19).
Figure 8.19. The UpdateEverything operation encapsulating a service composition.
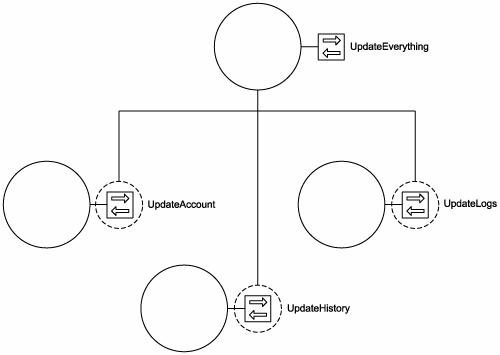
A common SOA extension that underlines composability is the concept of orchestration. Here, a service-oriented process (which essentially can be classified as a service composition) is controlled by a parent process service that composes process participants.
The requirement for any service to be composable also places an emphasis on the design of service operations. Composability is simply another form of reuse, and therefore operations need to be designed in a standardized manner and with an appropriate level of granularity to maximize composition opportunities.
8.3.6. Services are autonomous
Autonomy requires that the range of logic exposed by a service exist within an explicit boundary. This allows the service to execute self-governance of all its processing. It also eliminates dependencies on other services, which frees a service from ties that could inhibit its deployment and evolution (Figure 8.22). Service autonomy is a primary consideration when deciding how application logic should be divided up into services and which operations should be grouped together within a service context.
Figure 8.22. Autonomous services have control over underlying resources.
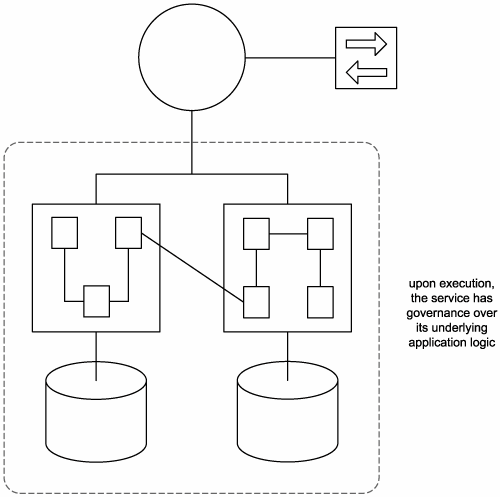
Deferring the location of business rules is one way to strengthen autonomy and keep services more generic. Processes generally assume this role by owning the business rules that determine how the process is structured and, subsequently, how services are composed to automate the process logic. This is another aspect of orchestration explored in the Orchestration service layer section in Chapter 9.
Note that autonomy does not necessarily grant a service exclusive ownership of the logic it encapsulates. It only guarantees that at the time of execution, the service has control over whatever logic it represents. We therefore can make a distinction between two types of autonomy.
- Service-level autonomy Service boundaries are distinct from each other, but the service may share underlying resources. For example, a wrapper service that encapsulates a legacy environment that also is used independently from the service has service-level autonomy. It governs the legacy system but also shares resources with other legacy clients.
- Pure autonomy The underlying logic is under complete control and ownership of the service. This is typically the case when the underlying logic is built from the ground up in support of the service.
8.3.7. Services are stateless
Services should minimize the amount of state information they manage and the duration for which they hold it. State information is data-specific to a current activity. While a service is processing a message, for example, it is temporarily stateful (Figure 8.24). If a service is responsible for retaining state for longer periods of time, its ability to remain available to other requestors will be impeded.
Figure 8.24. Stateless and stateful stages a service passes through while processing a message.
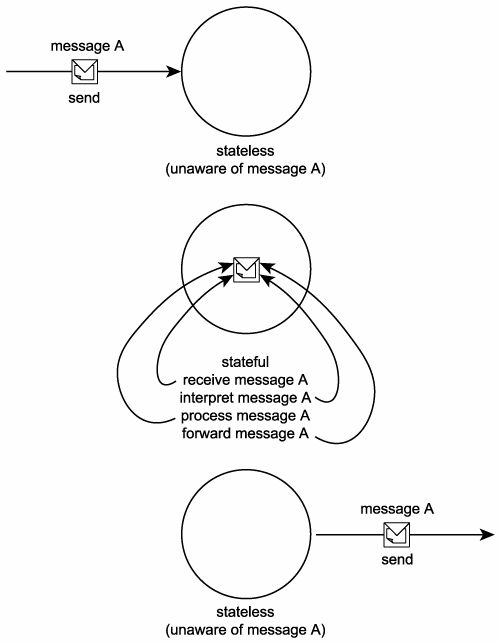
Statelessness is a preferred condition for services and one that promotes reusability and scalability. For a service to retain as little state as possible, its individual operations need to be designed with stateless processing considerations.
A primary quality of SOA that supports statelessness is the use of document-style messages. The more intelligence added to a message, the more independent and self-sufficient it remains. Chapters 6 and 7 explore various WS-* extensions that rely on the use of SOAP headers to carry different types of state data.
8.3.8. Services are discoverable
Discovery helps avoid the accidental creation of redundant services or services that implement redundant logic. Because each operation provides a potentially reusable piece of processing logic, metadata attached to a service needs to sufficiently describe not only the service's overall purpose, but also the functionality offered by its operations.
Note that this service-orientation principle is related to but distinct from the contemporary SOA characteristic of discoverability. On an SOA level, discoverability refers to the architecture's ability to provide a discovery mechanism, such as a service registry or directory. This effectively becomes part of the IT infrastructure and can support numerous implementations of SOA. On a service level, the principle of discoverability refers to the design of an individual service so that it can be as discoverable as possible.
|
SUMMARY OF KEY POINTS |
|---|
|
Introduction
- Why this book is important
- Objectives of this book
- Who this book is for
- What this book does not cover
- How this book is organized
- Additional information
Case Studies
- Case Studies
- How case studies are used
- Case #1 background: RailCo Ltd.
- Case #2 background: Transit Line Systems Inc.
Part I: SOA and Web Services Fundamentals
Introducing SOA
- Introducing SOA
- Fundamental SOA
- Common characteristics of contemporary SOA
- Common misperceptions about SOA
- Common tangible benefits of SOA
- Common pitfalls of adopting SOA
The Evolution of SOA
- The Evolution of SOA
- An SOA timeline (from XML to Web services to SOA)
- The continuing evolution of SOA (standards organizations and contributing vendors)
- The roots of SOA (comparing SOA to past architectures)
Web Services and Primitive SOA
- Web Services and Primitive SOA
- The Web services framework
- Services (as Web services)
- Service descriptions (with WSDL)
- Messaging (with SOAP)
Part II: SOA and WS-* Extensions
Web Services and Contemporary SOA (Part I: Activity Management and Composition)
- Web Services and Contemporary SOA (Part I: Activity Management and Composition)
- Message exchange patterns
- Service activity
- Coordination
- Atomic transactions
- Business activities
- Orchestration
- Choreography
Web Services and Contemporary SOA (Part II: Advanced Messaging, Metadata, and Security)
- Web Services and Contemporary SOA (Part II: Advanced Messaging, Metadata, and Security)
- Addressing
- Reliable messaging
- Correlation
- Policies
- Metadata exchange
- Security
- Notification and eventing
Part III: SOA and Service-Orientation
Principles of Service-Orientation
- Principles of Service-Orientation
- Service-orientation and the enterprise
- Anatomy of a service-oriented architecture
- Common principles of service-orientation
- How service-orientation principles inter-relate
- Service-orientation and object-orientation (Part II)
- Native Web service support for service-orientation principles
Service Layers
- Service Layers
- Service-orientation and contemporary SOA
- Service layer abstraction
- Application service layer
- Business service layer
- Orchestration service layer
- Agnostic services
- Service layer configuration scenarios
Part IV: Building SOA (Planning and Analysis)
SOA Delivery Strategies
- SOA Delivery Strategies
- SOA delivery lifecycle phases
- The top-down strategy
- The bottom-up strategy
- The agile strategy
Service-Oriented Analysis (Part I: Introduction)
- Service-Oriented Analysis (Part I: Introduction)
- Service-oriented architecture vs. Service-oriented environment
- Introduction to service-oriented analysis
- Benefits of a business-centric SOA
- Deriving business services
Service-Oriented Analysis (Part II: Service Modeling)
- Service-Oriented Analysis (Part II: Service Modeling)
- Service modeling (a step-by-step process)
- Service modeling guidelines
- Classifying service model logic
- Contrasting service modeling approaches (an example)
Part V: Building SOA (Technology and Design)
Service-Oriented Design (Part I: Introduction)
- Service-Oriented Design (Part I: Introduction)
- Introduction to service-oriented design
- WSDL-related XML Schema language basics
- WSDL language basics
- SOAP language basics
- Service interface design tools
Service-Oriented Design (Part II: SOA Composition Guidelines)
- Service-Oriented Design (Part II: SOA Composition Guidelines)
- Steps to composing SOA
- Considerations for choosing service layers
- Considerations for positioning core SOA standards
- Considerations for choosing SOA extensions
Service-Oriented Design (Part III: Service Design)
- Service-Oriented Design (Part III: Service Design)
- Service design overview
- Entity-centric business service design (a step-by-step process)
- Application service design (a step-by-step process)
- Task-centric business service design (a step-by-step process)
- Service design guidelines
Service-Oriented Design (Part IV: Business Process Design)
- Service-Oriented Design (Part IV: Business Process Design)
- WS-BPEL language basics
- WS-Coordination overview
- Service-oriented business process design (a step-by-step process)
Fundamental WS-* Extensions
- Fundamental WS-* Extensions
- You mustUnderstand this
- WS-Addressing language basics
- WS-ReliableMessaging language basics
- WS-Policy language basics
- WS-MetadataExchange language basics
- WS-Security language basics
SOA Platforms
Appendix A. Case Studies: Conclusion
EAN: 2147483647
Pages: 150