Network Design
| The constant and variable changes in traffic patterns are just two things that are reshaping the approach that designers have to take in designing campus intranets. The following are important requirements in the new campus intranet, at both Layers 2 and 3:
The following sections cover some concepts that Cisco uses when designing campus networks. AVVIDAVVID (Architecture for Voice, Video, and Integrated Data) is a process Cisco developed to help design complex networks with multiple coexisting technologies. Cisco created this architecture to simplify the planning, designing, and implementing of networks for companies. AVVID has three main components:
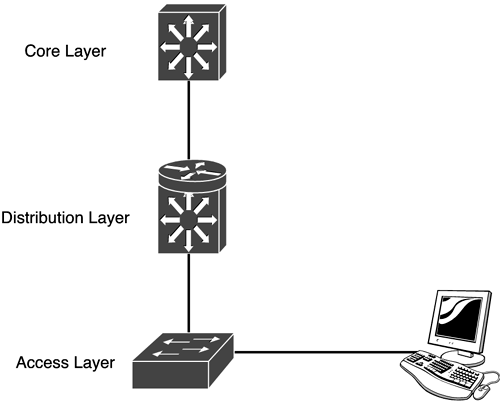
Network ModelOver the last few years, the design of campus networks has radically changed. Traditionally, most services (sometimes even local services) were placed at the center of the network, with Layer 2 switching providing the transport between the users and their resources. Today, a three-layer design is used to provide scalability and efficiency for a growing intranet. This three-layer design is composed of the following layers:
Figure 2.1 displays the three-layer hierarchy and the devices at each layer. Figure 2.1. Three-layer hierarchy.
Core LayerThe function of the core layer is to offer a high-speed Layer 2 switching backbone between different distribution layers, which provides packet switching that is as fast as possible. Note that implementing Layer 3 services at the core is not recommended. That means features such as packet filters and policy-based decisions should not be performed here, but rather at the lower distribution layer. This is applicable even to multilayer switching in the core because the core devices must perform packet manipulating or rewriting to perform their services, thereby slowing down the packet flow. There's an exception to implementing Layer 3 services at the core: If the campus in question is very large and you're having issues with Layer 3 convergence at the distribution layers, it might be necessary to implement Layer 3 switching at the core. However, this should be approached with caution. Distribution LayerThe distribution layer provides the demarcation point between the core and the access layers of a campus network. The distribution layer switches should perform all Layer 3 and policy functions. These include the following tasks:
Because the distribution layer aggregates the connection of many different access switches, the distribution switch needs a high-speed Layer 3 or multilayer switching function to handle all the intra- and inter-VLAN traffic. Access LayerThe access layer provides the user entry point into the switched network. It allows for the connection of different users and their servers. At this layer, you can provide shared or switched access. An example of shared access is when you have computers attached to a hub that's in turn attached to a switch. Switched access occurs when a computer has its own connection on the switch it's not sharing bandwidth with other networking devices. Switched access provides more bandwidth for users, but is more costly because it requires more ports on your switch. The following are some of the tasks and items that this layer handles:
Switches are the most common devices used at this layer to provide users with their connections. Note that the access layer can include routers when connecting branch offices to their corporate site by using technologies such as frame relay, ISDN, or even dedicated links. It is sometimes mistaken that the three layers core, distribution, and access must exist in distinct physical entities, which obviously does not have to be the case. These layers are defined more for representing functionality than for physical boundaries. The way that the layers are implemented is based on your specific networking design. However, a hierarchical structure must be maintained for optimal functionality.
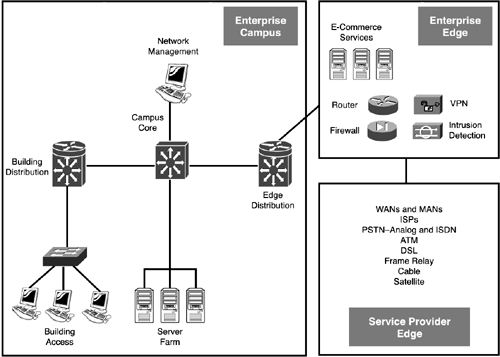
Enterprise ModelOne of the limitations of the three-layer hierarchical model is that it covers only a single campus design and doesn't allow different types of treatments based on the function of a particular layer(s) in a campus. Cisco has expanded on this and created the Enterprise Composite Network Model (ECNM), which breaks a network into three functional areas, depicted in Figure 2.2:
Figure 2.2. Enterprise model.
The main purpose of the ECNM is to define clear boundaries or demarcation points between different modules, or areas, of your network. By modularizing your network, your network becomes easier to troubleshoot and maintain as well as more scalable. Also, by modularizing your network, it becomes easier to add new modules to your existing design without having to redesign your entire network infrastructure and services. Each of these functional areas can have its own access, distribution, and core. Those three layers are typically contained within the Enterprise Campus area, but the other functional areas can contain one, two, or all three of these. The following three sections cover these functional areas. Enterprise CampusThe Enterprise Campus area provides the three-layer hierarchical campus model, but it doesn't include remote or Internet connections (these are in the Enterprise Edge area). Within the Enterprise Campus module, you'll find the following sub-modules: Campus Infrastructure, Edge Distribution, Server Farm, and Network Management. The Campus Infrastructure module includes the following sub-modules:
In addition to these three sub-modules, Cisco has introduced some new ones. The Edge Distribution sub-module is responsible for connecting to the Enterprise Edge module, which separates you from the outside world (Service Provider module). Its functions are similar to the Building Distribution module in Campus Infrastructure. However, it can perform additional security tasks as well as summarize routing information. The Server Farm sub-module contains corporate resources, such as database applications, corporate email, DNS and WINS, file and print services, and so on. Because access to these resources is critical, dual connections are used between the Server Farm and the Campus Backbone sub-modules. Please note that you might have other servers in your network, typically at the Building Distribution, for separate divisions or departments within your company. The Network Management sub-module is responsible for managing your network infrastructure, providing for authentication services, capturing logging information, configuration management, and other functions. Enterprise EdgeThe Enterprise Edge sub-module controls traffic between the Service Provider Edge and the Enterprise Campus. The Enterprise Edge contains four sub-modules: E-commerce, Internet Connectivity, Remote Access and VPNs, and WAN Access. The E-commerce sub-module contains services offered to the public. Those services can include Web servers, database servers, online transactions, and application servers. They're all protected by security products such as authentication servers, firewalls, and intrusion detection. The Internet Connectivity sub-module provides a connection between you and the Internet. This sub-module contains the following services: DNS, FTP, email, and Web servers. It is protected by security products such as firewalls, basic filtering on perimeter routers, and intrusion detection systems. The Remote Access and VPN sub-module is responsible for remote access and remote access VPN connections from your external users and sites. The types of devices involved with this sub-module include dial-up access servers, VPN concentrators, firewalls, routers, and intrusion detection systems. The WAN Access sub-module is responsible for connecting remote sites to the Enterprise Edge via a private network. Traffic from these sites does not traverse a public network, like the Internet, and is therefore more secure. Types of technologies employed for these connections included leased lines, DSL, cable, optical, wireless, frame relay, ATM, and others. Service Provider EdgeThe Service Provider Edge sub-module provides WAN and MAN connections to private and public networks for customers and is connected to a company's Enterprise Edge. There are three sub-modules in the Service Provider Edge: ISP, PSTN, and WAN technologies. The ISP sub-module is responsible for providing Internet access to a customer. It can host services for customers who want to outsource the management of specific e-commerce applications. The PSTN sub-module provides dial-up access (analog, ISDN, and wireless) for remote access users. The WAN Technologies sub-module provides permanent connections to remote sites using media types like leased lines, frame relay, ATM, and others. |
EAN: 2147483647
Pages: 171