Symmetric Encryption
In symmetric encryption, a single shared secret key is used for encryption and decryption, as shown in Figure 11.2. These dual-use keys can be used to lock and unlock data. Symmetric encryption is the oldest form of encryption. Systems such as scytale and Caesar's cipher are examples of symmetric encryption. Symmetric encryption provides confidentiality by keeping individuals who do not have the key from knowing the true contents of the message.
Figure 11.2. Symmetric encryption.
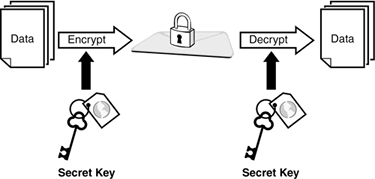
For symmetric encryption systems to be effective, there must be a secure method in which to transfer keys; therein lies the weakness of symmetric encryption. Movement of the secret key from one party to another must typically be done in some type of out-of-band method. If email is to be secured, it does little good to send the key via unsecured email because anyone could intercept the email and thereby compromise the security of the encrypted information. Because of this, an out-of-band key exchange must be used. Common out-of-band methods include in-person delivery and snail mail.
Symmetric encryption also suffers from scalability issues. For example, if you need to communicate details about this book to 10 people in a secure manner, the total keys needed would be calculated as follows: N (N 1) / 2 or [10 (10 1) / 2 = 45 keys]. Therefore, key management becomes the second big issue when dealing with symmetric encryption.
You might be thinking that I have offered you nothing but bad news about symmetric encryption, but it does have features that make it an excellent choice for securing data and providing confidentiality. Symmetric encryption is fast. It can encrypt and decrypt very quickly. It also is considered strong. Symmetric encryption is very hard to break if a large key is used. Symmetric algorithms include these:
- DES Data Encryption Standard was once the most common symmetric algorithm used. It has now been officially retired by NIST.
- Blowfish This is a general-purpose symmetric algorithm intended as a replacement for the DES replaced by AES and Twofish.
- Rijndael This is a block cipher adopted as the Advanced Encryption Standard (AES) by the U.S. government to replace DES.
- RC4 Rivest Cipher 4 is a stream-based cipher. Stream ciphers treat the data as a stream of bits.
- RC5 Rivest Cipher 5 is a block-based cipher. RC5 processes data in blocks of 32, 64, or 128 bits.
- SAFER Secure and Fast Encryption Routine is a block-based cipher that processes data in blocks of 64 and 128 bits.
Data Encryption Standard (DES)
DES grew out of an early 1970s project that was originally developed by IBM. IBM and the National Institute of Standards and Technology (NIST) modified IBM's original encryption standard, known as Lucifer, to use a 56-bit key. The revised standard was endorsed by the NSA. The DES standard was published in 1977 and was released by the American National Standards Institute (ANSI) in 1981.
DES is a symmetric encryption standard that is based on a 64-bit block. DES processes 64 bits of plain text at a time to output 64-bit blocks of cipher text. DES uses a 56-bit key and has four modes of operation: Electronic Codebook (ECB) mode, Cipher Block Chaining (CBC) mode, Cipher Feedback (CFB) mode, and Output Feedback (OFB) mode.
All four modes use the 56-bit key. Although the standard reports the key to be 64 bits, 8 bits are actually used for parity; their purpose is to ensure the integrity of the remaining 56 bits. Therefore, for all practical purposes, the key is really only 56 bits long. Each 64-bit plain-text block is separated into two 32-bit blocks and then processed by the 56-bit key. The plain text is processed by the key through 16 rounds of transpositions and substitutions.
Electronic Codebook (ECB) Mode
ECB is the native encryption mode of DES. Although it produces the highest throughput, it is also the easiest form of DES encryption to break. If used with large amounts of data, it can be easily attacked because the same plain text encrypted with the same key will always produce the same cipher text. This is why it is best used on small amounts of data, such as the encryption of PIN numbers at ATM machines.
Cipher Block Chaining (CBC) Mode
The CBC mode of DES is widely used and is similar to ECB. CBC processes 64-bit blocks of data but inserts some of the cipher text created from the previous block into the next one. This process is called XORing, and it makes the cipher text more secure and less susceptible to cracking. CBC is aptly named because data from one block is used in the next; therefore, the blocks are chained together. As they are chained, any error in one block can be propagated to others. This can make it impossible to decrypt that block and the following blocks as well.
Cipher Feedback (CFB) Mode
CFB is a stream cipher that can be used to encrypt individual characters. Although it is a stream cipher, it is similar to OFB, in that previously generated cipher text is added to subsequent streams. Because the cipher text is streamed together, errors and corruption can propagate through the encryption process.
Output Feedback (OFB) Mode
OFB is also a stream cipher. Unlike CFB, OFB uses plain text to feed back into stream of cipher text. Transmission errors do not propagate throughout the encryption process. An initialization vector is used to create the seed value for the first encrypted block. DES XORs the plain text with a seed value to be applied with subsequent data.
|
Although DES remained secure for many years, the Electronic Frontier Foundation (EFF) was able to crack DES in 1998 in about 23 hours. Now that DES has been officially retired, it is recommended that Triple-DES (3DES) be used to ensure security. Triple-DES is scheduled to be replaced by the Advanced Encryption Standard (AES). |
Triple-DES (3DES)
Before discussing Triple-DES, some of you must be wondering what happened to Double-DES. Although Double-DES has a 112-bit key, it is no more secure than DES; it requires the same work factor to crack as that of DES.
To extend the usefulness of the DES encryption standard, Triple-DES is now being used. Triple-DES can use two or three keys to encrypt data, depending on how it is implemented. Although it is much more secure, it is up to three times as slow as 56-bit DES:
- DES EEE2 uses two keys. The first key is reused during the third round of encryption. The encryption process is performed three times (encrypt, encrypt, encrypt).
- DES EDE2 uses two keys. Again, the first key is reused during the third round of encryption. Unlike DES EEE2, DES EDE2 encrypts, decrypts, and then encrypts.
- DES EEE3 uses three keys and performs the encryption process three times.
- DES EDE3 uses three keys but operates by encrypting, decrypting, and then encrypting the data.
Advanced Encryption Standard (AES)
All good things must end, and that is what NIST decided in 2002 when Rijindael replaced DES and became the new U.S. standard for encrypting sensitive but unclassified data. Rijindael can be implemented in one of three key sizes, including 128, 192, and 256 bits. It is considered a fast, simple, robust encryption mechanism.
International Data Encryption Algorithm (IDEA)
This 64-bit block cipher uses a 128-bit key. Although it has been patented by a Swiss company, it is freely available for noncommercial use. It is considered a secure encryption standard, and there have been no known attacks against it. It operates in four distinct modes, similar to DES. At one time, it was thought that IDEA would replace DES, but patent fees prevented that from happening.
Other Symmetric Algorithms
Other symmetric algorithms include these:
- Blowfish This is a 64-bit block cipher that can support key lengths up to 448 bits.
- Twofish A finalist in the AES selection process, Twofish operates on 128-bit blocks and can support a key length up to 256 bits.
- RC5 RC5, or Rivest Cipher 5, is a fast block cipher. It is different than other symmetric algorithms, in that it supports a variable block size, a variable key size, and a variable number of rounds. Allowable choices for the block size are 32, 64, and 128 bits. The number of rounds can range from 0 to 255, and the key can range up to 2040 bits.
- Skipjack Skipjack and the clipper chip are both government-devised methods for commercial encryption. Skipjack faces opposition because the government would maintain a portion of the information required to reconstruct a Skipjack key, so that legal authorities could decrypt communications between the affected parties when approved by a warrant or approval of the court.
|
Be sure to take the time to review the various encryption types, block sizes, and key lengths; you can expect to see these items on the exam. |
The CISSP Cram Sheet
- PHYSICAL SECURITY
- SECURITY-MANAGEMENT PRACTICES
- ACCESS-CONTROL SYSTEMS AND METHODOLOGY
- SECURITY MODELS AND ARCHITECTURES
- TELECOMMUNICATIONS AND NETWORK SECURITY
- APPLICATION AND SYSTEMS-DEVELOPMENT SECURITY
- OPERATIONS SECURITY
- BUSINESS CONTINUITY PLANNING
- LAW, INVESTIGATIONS, AND ETHICS
- CRYPTOGRAPHY
A Note from Series Editor Ed Tittel
About the Author
Acknowledgments
We Want to Hear from You!
Introduction
- Introduction
- How to Prepare for the Exam
- Taking a Certification Exam
- Tracking Your CISSP Status
- About This Book
Self-Assessment
- Self-Assessment
- CISSPs in the Real World
- The Ideal CISSP Candidate
- Put Yourself to the Test
- After the Exam
The CISSP Certification Exam
- The CISSP Certification Exam
- Assessing Exam Readiness
- Taking the Exam
- Multiple-Choice Question Format
- Exam Strategy
- Question-Handling Strategies
- Mastering the Inner Game
Physical Security
- Physical Security
- Physical Security Risks
- Requirements for New Site Locations
- Building Defense in Depth
- Environmental Controls
- Electrical Power
- Equipment Life Cycle
- Fire Prevention, Detection, and Suppression
- Exam Prep Questions
- Answers to Exam Prep Questions
Security-Management Practices
- Security-Management Practices
- The Risk of Poor Security Management
- The Role of CIA
- Risk Assessment
- Policies, Procedures, Standards, Baselines, and Guidelines
- Implementation
- Training and Education
- Auditing Your Security Infrastructure
- Exam Prep Questions
- Answers to Exam Prep Questions
Access-Control Systems and Methodology
- Access-Control Systems and Methodology
- Threats Against Access Control
- Access-Control Types
- Identification, Authentication, and Authorization
- Single Sign-On
- Data Access Controls
- Intrusion-Detection Systems (IDS)
- Penetration Testing
- Honeypots
- Exam Prep Questions
- Answers to Exam Prep Questions
System Architecture and Models
- System Architecture and Models
- Common Flaws in the Security Architecture
- Computer System Architecture
- Security Mechanisms
- Security Models of Control
- Documents and Guidelines
- System Validation
- Exam Prep Questions
- Answers to Exam Prep Questions
Telecommunications and Network Security
- Telecommunications and Network Security
- Threats to Network Security
- LANs and Their Components
- WANS and Their Components
- Network Models and Standards
- Network Equipment
- Access Methods and Remote Connectivity
- Message Privacy
- Network Access Controls
- Exam Prep Questions
- Answers to Exam Prep Questions
Applications and Systems-Development Security
- Applications and Systems-Development Security
- Malicious Code
- Failure States
- The System Development Life Cycle
- Software-Development Methods
- Change Management
- Programming Languages
- Database Management
- Exam Prep Questions
- Answers to Exam Prep Questions
Operations Security
- Operations Security
- Hack Attacks
- Operational Security
- Auditing and Monitoring
- Categories of Control
- Fax Control
- Ethical Hacking
- Contingency Planning, Backup, and Recovery
- Exam Prep Questions
- Answers to Exam Prep Questions
Business Continuity Planning
- Business Continuity Planning
- The Risks of Poor Business Planning
- Business Continuity Management
- Business Continuity Plan (BCP)
- Disaster Recovery Planning (DRP)
- Exam Prep Questions
- Answers to Exam Prep Questions
Law, Investigations, and Ethics
- Law, Investigations, and Ethics
- Computer Crimes
- Common Attacks
- Ethics
- International Property Laws
- Parameters of Investigation
- Forensics
- Major Legal Systems
- Exam Prep Questions
- Answers to Exam Prep Questions
Cryptography
- Cryptography
- Cryptographic Basics
- History of Encryption
- Symmetric Encryption
- Asymmetric Encryption
- Integrity and Authentication
- Steganography
- Public Key Infrastructure (PKI)
- Cryptographic Services
- Cryptographic Attacks
- Exam Prep Questions
- Answers to Exam Prep Questions
Practice Exam 1
Answers to Practice Exam 1
Practice Exam 2
Answers to Practice Exam 2
