DETERMINING IF THE SYSTEM IS ALIVE
| | ||
| | ||
| | ||
DETERMINING IF THE SYSTEM IS ALIVE
One of the most basic steps in mapping out a network is performing an automated ping sweep on a range of IP addresses and network blocks to determine if individual devices or systems are alive. Ping is traditionally used to send ICMP ECHO (Type 8) packets to a target system in an attempt to elicit an ICMP ECHO_REPLY (Type 0) indicating the target system is alive. Although ping is acceptable to determine the number of systems alive in a small-to-midsize network, it is inefficient for larger, enterprise networks. Scanning larger Class A networks can take hours if not days to complete. You must learn a number of ways for discovering live systems; the following sections present a sample of the available techniques.
Network Ping Sweeps
| Popularity: | 10 |
| Simplicity: | 9 |
| Impact: | 3 |
| Risk Rating: | 7 |
Network pinging is the act of sending certain types of traffic to a target and analyzing the results (or lack thereof). Typically, pinging utilizes ICMP (Internet Control Message Protocol). And although not the only packets available for this function, ICMP tends to be the most heavily supported. Alternatively, one could use either TCP or UDP as well to perform the same functionfinding a host that is alive on the network.
To perform an ICMP ping sweep, you can use a myriad of tools available for both UNIX and Windows. One of the tried-and-true techniques of performing ping sweeps in the UNIX world is to use fping (http://packetstorm. securify .com/Exploit_Code_Archive/fping.tar.gz). Unlike more traditional ping sweep utilities, which wait for a response from each system before moving on to the next potential host, fping is a utility that will send out massively parallel ping requests in a round- robin fashion. Thus, fping will sweep many IP addresses significantly faster than ping. fping can be used in one of two waysyou can feed it a series of IP addresses from standard input (stdin) or you can have it read from a file. Having fping read from a file is easy; simply create your file with IP addresses on each line:
192.168.51.1 192.168.51.2 192.168.51.3 ... 192.168.51.253 192.168.51.254
Then use the -f parameter to read in the file:
[root]$ fping -a -f in.txt 192.168.1.254 is alive 192.168.1.227 is alive 192.168.1.224 is alive ... 192.168.1.3 is alive 192.168.1.2 is alive 192.168.1.1 is alive 192.168.1.190 is alive
The -a option of fping will show only systems that are alive. You can also combine it with the -d option to resolve hostnames if you choose. We prefer to use the -a option with shell scripts and the -d option when we are interested in targeting systems that have unique hostnames. Other options such as -f may interest you when scripting ping sweeps. Type fping -h for a full listing of available options. Another utility that is highlighted throughout this book is nmap from Fyodor (http://www. insecure .org/nmap). Although this utility is discussed in much more detail later in this chapter, it is worth noting that it does offer ping sweep capabilities with the - sP option.
[root] nmap -sP 192.168.1.0/24 Starting nmap V. 3.70 by fyodor@insecure.org (www.insecure.org/nmap/) Host (192.168.1.0) seems to be a subnet broadcast address (returned 3 extra pings). Host (192.168.1.1) appears to be up. Host (192.168.1.10)appears to be up. Host (192.168.1.11) appears to be up. Host (192.168.1.15) appears to be up. Host (192.168.1.20) appears to be up. Host (192.168.1.50) appears to be up. Host (192.168.1.101) appears to be up. Host (192.168.1.102) appears to be up. Host (192.168.1.255) seems to be a subnet broadcast address (returned 3 extra pings). Nmap run completed -256 IP addresses (10 hosts up) scanned in 21 seconds
For the Windows-inclined, we like the tried-and-true freeware product SuperScan from Foundstone (http://www.foundstone.com), shown in Figure 2-1. It is one of the fastest ping sweep utilities available. Like fping, SuperScan sends out multiple ICMP ECHO packets (in addition to three other types of ICMP) in parallel and simply waits and listens for responses. Also like fping, SuperScan allows you to resolve hostnames and view the output in an HTML file.
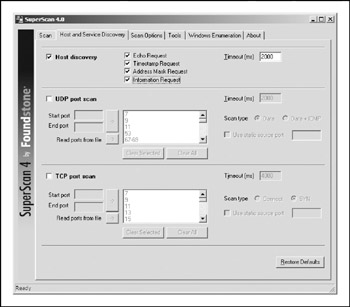
Figure 2-1: SuperScan from Foundstone is one of the fastest and most flexible ping sweep utilities availableand it's free.
For those technically minded, here's a brief synopsis of the different types of ICMP packets that can be used to ping a host (see RFC 792 for a more complete description). The primary ICMP types are:
-
Message Type: 0 - Echo Reply
-
Message Type: 3 - Destination Unreachable
-
Message Type: 4 - Source Quench
-
Message Type: 5 - Redirect
-
Message Type: 8 - Echo
-
Message Type: 11 - Time Exceeded
-
Message Type: 12 - Parameter Problem
-
Message Type: 13 - Timestamp
-
Message Type: 14 - Timestamp Reply
-
Message Type: 15 - Information Request
-
Message Type: 16 - Information Reply
Any of these ICMP message types could potentially be used to discover a host on the network; it just depends on the target's ICMP implementation and how it responds to these packet types. How the different operating systems respond or don't respond to the various ICMP types also aids in remote OS detection.
Another extremely fast ping tool (albeit a commercial product) is Ping Sweep from SolarWinds (http://www.solarwinds.net). Ping Sweep can be blazingly fast because it allows you to specify the delay time between packets sent. By setting this value to 0 or 1, you can scan an entire Class C network and resolve hostnames in less than seven seconds. Be careful with these tools, however, because you can easily saturate a slow link such as a 128K ISDN or Frame Relay linknot to mention satellite and infrared (IR) links.
Other Windows ping sweep utilities include WS_Ping ProPack (http://www.ipswitch.com) and NetScanTools (http://www.nwpsw.com). These later tools will suffice for a small network sweep. However, they are significantly slower than SuperScan and Ping Sweep. Keep in mind that while these GUI-based tools provide eye-pleasing output, they can sometimes limit your ability to script and automate decision-making during your ping sweeps.
You may be wondering what happens if ICMP is blocked by the target site. Good question. It is not uncommon to come across a security-conscious site that has blocked ICMP at the border router or firewall. Although ICMP may be blocked, some additional tools and techniques can be used to determine if systems are actually alive. However, they are not as accurate or as efficient as a normal ping sweep.
When ICMP traffic is blocked, port scanning is the first alternate technique to determine live hosts. (Port scanning is discussed in great detail later in this chapter.) By scanning for common ports on every potential IP address, we can determine which hosts are alive if we can identify open or listening ports on the target system. This technique can be timeconsuming, but it can often unearth rogue systems or highly protected systems.
For Windows, the tool we recommend is SuperScan. As discussed earlier, SuperScan will perform both host and service discovery using ICMP and TCP/UDP, respectively. Using the TCP/UDP port scan options, you can determine whether a host is alive or notwithout using ICMP at all. As you can see in Figure 2-2, simply select the check box for each protocol you wish to use and the type of technique you desire , and you are off to the races.
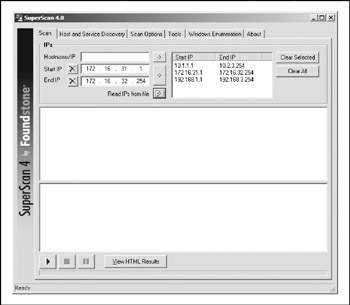
Figure 2-2: Using SuperScan from Foundstone, you can discover hosts hidden behind traditional firewalls.
Another tool used for this host discovery technique is the UNIX/Windows tool nmap. As mentioned previously, nmap does provide the capability to perform ICMP sweeps. However, it offers a more advanced option called TCP ping scan. A TCP ping scan is initiated with the -PT option and a port number such as 80. We use 80 because it is a common port that sites will allow through their border routers to systems on their demilitarized zone (DMZ), or even better, through their main firewall(s). This option will spew out TCP ACK packets to the target network and wait for RST packets indicating the host is alive. ACK packets are sent because they are more likely to get through a non-stateful firewall such as Cisco IOS. Here's an example:
[root] nmap -sP -PT80 192.168.1.0/24 TCP probe port is 80 Starting nmap V. 3.70 Host (192.168.1.0) appears to be up. Host (192.168.1.1) appears to be up. Host shadow (192.168.1.10) appears to be up. Host (192.168.1.11) appears to be up. Host (192.168.1.15) appears to be up. Host (192.168.1.20) appears to be up. Host (192.168.1.50) appears to be up. Host (192.168.1.101) appears to be up. Host (192.168.1.102) appears to be up. Host (192.168.1.255) appears to be up. Nmap run completed (10 hosts up) scanned in 5 seconds
As you can see, this method is quite effective in determining if systems are alive, even if the site blocks ICMP. It is worth trying a few iterations of this type of scan with common ports such as SMTP (25), POP (110), AUTH (113), IMAP (143), or other ports that may be unique to the site.
For the technical reader, Hping2 from http://www.hping.org is another TCP ping utility for UNIX with additional TCP functionality beyond nmap. Hping2 allows the user to control specific options of the UDP, TCP, or Raw IP packet that may allow it to pass through certain access control devices.
To perform a simple TCP ping scan, set the TCP destination port with the -p option. By doing this you can circumvent some access control devices similar to the traceroute technique mentioned in Chapter 1. Hping2 can be used to perform TCP and UDP ping sweeps, and it has the ability to fragment packets, potentially bypassing some access control devices. Here's an example:
[root]# hping2 192.168.0.2 -S -p 80 -f HPING 192.168.0.2 (eth0 192.168.0.2): S set, 40 data bytes 60 bytes from 192.168.0.2: flags=SA seq=0 ttl=64 id=418 win=5840 time=3.2 ms 60 bytes from 192.168.0.2: flags=SA seq=1 ttl=64 id=420 win=5840 time=2.1 ms 60 bytes from 192.168.0.2: flags=SA seq=2 ttl=64 id=422 win=5840 time=2.0 ms ---192.168.0.2 hping statistic --- 3 packets tramitted, 3 packets received, 0% packet loss
In some cases, simple access control devices cannot handle fragmented packets correctly, thus allowing our packets to pass through and determine if the target system is alive. Notice that the TCP SYN (S) flag and the TCP ACK (A) flag are returned whenever a port is open (flags=SA). Hping2 can easily be integrated into shell scripts by using the -cN packet count option, where N is the number of packets to send before moving on. Although this method is not as fast as some of the ICMP ping sweep methods mentioned earlier, it may be necessary given the configuration of the target network. We discuss Hping2 in more detail in Chapter 9.
The final tool we will analyze is icmpenum, from Simple Nomad (http://www.nmrc.org/files/sunix/icmpenum-1.1.1.tgz). This UNIX utility is a handy ICMP enumeration tool that allows you to quickly identify systems that are alive by sending the traditional ICMP ECHO packets as well as ICMP TIME STAMP REQUEST and ICMP INFO requests (similar to SuperScan). Thus, if ingress (inbound) ICMP ECHO packets are dropped by a border router or firewall, it may still be possible to identify systems using an alternate ICMP type:
[shadow] icmpenum -i2 -c 192.168.1.0 192.168.1.1 is up 192.168.1.10 is up 192.168.1.11 is up 192.168.1.15 is up 192.168.1.20 is up 192.168.1.103 is up
In this example, we enumerated the entire 192.168.1.0 Class C network using an ICMP TIME STAMP REQUEST. However, the real power of icmpenum is to identify systems using spoofed packets to avoid detection. This technique is possible because icmpenum supports the ability to spoof packets with the -s option and passively listen for responses with the -p switch.
To summarize, this step allows us to determine exactly what systems are alive via ICMP or through selective port scans . Out of 255 potentiaotential addresses within the Class C range, we have determined that several hosts are alive and have now become our targets for subsequent interrogation .
Ping Sweeps Countermeasures
Although ping sweeps may seem like an annoyance, it is important to detect this activity when it happens. Depending on your security paradigm, you may also want to block ping sweeps. We explore both options next.
Detection As mentioned, network mapping via ping sweeps is a proven method for performing network reconnaissance before an actual attack ensues. Therefore, detecting ping sweep activity is critical to understanding when and by whom an attack may occur. The primary method for detecting ping sweep attacks involves using network-based IDS programs such as Snort (http://www.snort.org).
From a host-based perspective, several UNIX utilities will detect and log such attacks. If you begin to see a pattern of ICMP ECHO packets from a particular system or network, it may indicate that someone is performing network reconnaissance on your site. Pay close attention to this activity, as a full-scale attack may be imminent.
Many commercial network and desktop firewall tools (from Cisco, Check Point, and Microsoft, and McAfee, Symantec, and ISS, respectively) can detect ICMP, TCP, and UDP ping sweeps. However, just because the technologies exist to detect this behavior, it does not mean that someone will be watching when it occurs.
Some freeware Windows host-based ping-detection tools do exist. A shareware/freeware product worth looking at is Genius. Genius is now in version 3.1 and is located at http://www.indiesoft.com. Although Genius does not detect ICMP ECHO (ping) scans of a system, it will detect TCP ping scans of a particular port. Table 2-1 lists additional UNIX ping-detection tools that can enhance your monitoring capabilities.
| Program | Resource |
|---|---|
| Scanlogd | http://www.openwall.com/scanlogd |
| Courtney | http://packetstormsecurity.org/UNIX/audit/courtney-1.3.tar.Z |
| Ippl | http://pltplp.net/ippl |
| Protolog | http://packetstormsecurity.org/UNIX/loggers/protolog-1.0.8.tar.gz |
Prevention Although detection of ping sweep activity is critical, a dose of prevention will go even further. We recommend that you carefully evaluate the type of ICMP traffic you allow into your networks or into specific systems. There are many different types of ICMP trafficECHO and ECHO_REPLY are only two such types. Most routers do not require all types of ICMP traffic to all systems directly connected to the Internet. Although almost any firewall can filter ICMP packets, organizational needs may dictate that the firewall pass some ICMP traffic. If a true need exists, you should carefully consider which types of ICMP traffic you allow to pass. A minimalist approach may be to only allow ICMP ECHO_REPLY, HOST_UNREACHABLE, and TIME_EXCEEDED packets into the DMZ network and only to specific hosts. In addition, if ICMP traffic can be limited with access control lists (ACLs) to specific IP addresses of your ISP, you are better off. This will allow your ISP to check for connectivity, while making it more difficult to perform ICMP sweeps against systems connected directly to the Internet.
ICMP is a powerful protocol for diagnosing network problems, but it is also easily abused. Allowing unrestricted ICMP traffic into your border gateway may allow attackers to mount a denial of service attack, bringing down a system or affecting its availability. Even worse , if attackers actually manage to compromise one of your systems, they may be able to back-door the operating system and covertly tunnel data within an ICMP ECHO packet using a program such as loki. For more information on loki, check out Article 6 in Phrack Magazine, Volume 7, Issue 51 , from September 1, 1997 (http://www.phrack.org/show.php?p=51&a=6).
Another interesting concept is pingd, which was developed by Tom Ptacek and ported to Linux by Mike Schiffman. pingd is a userland daemon that handles all ICMP ECHO and ICMP ECHO_REPLY traffic at the host level. This feat is accomplished by removing support of ICMP ECHO processing from the kernel and implementing a userland daemon with a raw ICMP socket to handle these packets. Essentially, it provides an access control mechanism for ping at the system level. pingd is available for Linux at http://packetstormsecurity.org/UNIX/misc/pingd-0.5.1.tgz.
ICMP Queries
| Popularity: | 2 |
| Simplicity: | 9 |
| Impact: | 5 |
| Risk Rating: | 5 |
Ping sweeps (or ICMP ECHO packets) are only the tip of the iceberg when it comes to ICMP information about a system. You can gather all kinds of valuable information about a system simply by sending an ICMP packet to it. For example, with the UNIX tool icmpquery (http://packetstormsecurity.org/UNIX/scanners/icmpquery.c) or icmpush (http://packetstormsecurity.org/UNIX/ scanners /icmpush22.tgz), you can request the time on the system (to see the time zone the system is in) by sending an ICMP type 13 message (TIMESTAMP). Also, you can request the netmask of a particular device with the ICMP type 17 message (ADDRESS MASK REQUEST). The netmask of a network card is important because you can determine all the subnets being used. With knowledge of the subnets, you can orient your attacks to only particular subnets and avoid hitting broadcast addresses, for example. icmpquery has both a timestamp and an address mask request option:
icmpquery <query> [-B] [-f fromhost] [-d delay] [-T time] targets where query is one of: -t : icmp timestamp request (default) -m : icmp address mask request The delay is in microseconds to sleep between packets. targets is a list of hostnames or addresses -T specifies the number of seconds to wait for a host to respond. The default is 5. -B specifies 'broadcast' mode. icmpquery will wait for timeout seconds and print all responses. If you're on a modem, you may wish to use a larger -d and -T
To use icmpquery to query a router's time, you can run this command:
[root] icmpquery -t 192.168.1.1 192.168.1.1 : 11:36:19
To use icmpquery to query a router's netmask, you can run this command:
[root] icmpquery -m 192.168.1.1 192.168.1.1 : 0xFFFFFFE0
Not all routers and systems allow an ICMP TIMESTAMP or NETMASK response, so your mileage with icmpquery and icmpush may vary greatly from host to host.
ICMP Query Countermeasures
One of the best prevention methods is to block the ICMP types that give out information at your border routers. At minimum, you should restrict TIMESTAMP (ICMP type 13) and ADDRESS MASK (ICMP type 17) packet requests from entering your network. If you deploy Cisco routers at your borders, you can restrict them from responding to these ICMP request packets with the following ACLs:
access-list 101 deny icmp any any 13 ! timestamp request access-list 101 deny icmp any any 17 ! address mask request
It is possible to detect this activity with a network intrusion detection system (NIDS) such as Snort. Here is a snippet of this type of activity being flagged by Snort:
[**] PING-ICMP Timestamp [**] 05/29-12:04:40.535502 192.168.1.10 -> 192.168.1.1 ICMP TTL:255 TOS:0x0 ID:4321 TIMESTAMP REQUEST
EAN: N/A
Pages: 127