The Nature of Security
|
As in a chain, the security of the whole computer system is only as strong as the weakest link. A global or systemic model is critical to the formulation of an effective approach to security in the enterprise. It is not uncommon for large companies to decide, almost arbitrarily, that a particular area of their network is open to attack and invest tens of thousands of dollars to "patch the fence" without realizing that someone could walk right through the front gate. In one case we worked with, a company invested $50,000 in an Internet firewall without setting up a system to enforce strong passwords. With the firewall in place, no one could enter the system from the Internet—that is, unless the intruder could guess that the system administrator's password was his daughter's first name and birthday.
Taking a global view of security for the enterprise can be intimidating, which may account for the woefully inadequate attention paid to the subject by many companies. It is important to realize however, that the effects of securing your infrastructure are cumulative. Even a few simple changes to secure certain access points to the network can make a huge difference. For example, installing an effective Internet firewall can be a strong deterrent to the casual hacker. Before deciding to install such a system, however, you need to assess the overall security posture of the infrastructure. Without such an assessment, you could be securing part of your network while leaving another part open to attack. When getting started, it is useful to ask yourself: what are you trying to protect?
What Are You Trying to Protect?
The generic answer, more often than not, is "corporate data." Corporate data must be protected from
-
Data access Access must be limited only to appropriate users without impacting authorized access to data or application performance when manipulating data. Figure 8-1 shows the correlation between the level of security and its impact on a user's ability to work. The three security paradigms, Open, Restricted, and Closed, are discussed later in this chapter. The common criteria linked to data access are Authentication, Authorization, and Accounting (AAA), and are described as follows:
-
Authentication The ability to positively identify the authorized user, often via two or more factors (username and password, plus biometric, one-time security code tokens).
-
Authorization The determination of which resources an authenticated user may access, and what rights or permissions they have for each resource. This can be very broad as in file and directory permissions, or very granular as in record-level access controls within a structured database.
-
Accounting The ability to track what a user did or attempted to do. This is particularly critical with regard to audit trails required in most regulated industries.
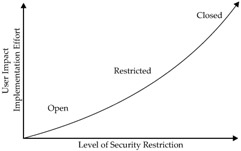
Figure 8-1: Security model vs. user impact -
-
Data integrity Data must not be modified or altered except by authorized individuals or processes. AAA rules determine which individuals have the right to perform these operations on the data, and can record what modifications were actually made. Data integrity during transport becomes a serious problem when classic client-server applications are deployed over non-secure (unencrypted) media. A "man-in-the-middle" attack may compromise data integrity yet remain undetected. In an SBC environment, transaction information remains within the local network, and screen updates and data input (mouse clicks and keystrokes) are contained within the RDP or ICA data stream. The nature of an ICA session makes "man-in-the-middle" or session hijacking attacks extremely difficult to complete since attackers cannot easily synchronize with the video stream.
-
Network resources Both processing capability and network capacity must be protected to ensure business continuity. Inappropriate or unauthorized use of processing power may deny service to legitimate applications or processes. Improper control of data storage may allow unauthorized data to consume storage capacity. Network bandwidth and access must be protected from intentional and inadvertent disruption. Denial of service (DoS) events may be intentional (directed at corporate servers, firewalls, and so on), or unintentional (a side effect of unauthorized use of resources). As an example, a customer uses Citrix to deploy Geographic Information Systems (GIS) data to a large remote customer. Overall performance of Internet access and Citrix access slowed to a crawl. The cause was isolated to saturation of the customer's Internet T1 by FTP downloads from an internal web server. The server had been hacked, hidden directories created for bootleg copies of a non-English version of Windows 2000, and the download instructions circulated through a European chat room. A single incident deprived the company of processing power (the hacked server), application services (Citrix access was unstable), storage capacity (drive space), and network access bandwidth. Further, it created a potential for liability as their FTP site hosted bootleg software.
-
Liability, reputation, business continuity These categories are included because companies may actually have to close their doors if certain data becomes public. Engineering designs, business merger and acquisition plans, or other data that constitutes a competitive advantage, if exposed, could have a crippling effect on operations. If it can be proven that a company's officers knew about the lack of security and were negligent in correcting it, they could be liable for damages to the stockholders. A company that allowed its security weaknesses to be used to exploit another company or network could be liable for damages. Corporate image and reputation are extremely sensitive for some businesses. For instance, who would keep their money in a bank with a history of security problems? Worse yet, what if security weaknesses allowed a business's web site to host child pornography, and the business's servers and data were seized as part of a criminal investigation?
The key to securing the corporate infrastructure is a comprehensive security policy. Although addressing all aspects of information security is well beyond the scope of this book, a basic understanding of the breadth of security issues and the security measures necessary in a corporate SBC environment is essential knowledge. Most governmental entities, "regulated" industries (banking, stock trading, healthcare services), and many large businesses mandate certification and accreditation processes, with a concise written security policy as a prerequisite for certification or accreditation. Examples of these mandates include
-
Department of Defense Information Technology Security Certification and Accreditation Process (DITSCAP)
-
Health Insurance Portability and Accountability Act (HIPAA)
-
Gramm-Leach-Bliley (GLB) Act of 1999 (Financial Services Modernization Bill)
Toward that end, a number of leading vendors and industry groups have produced methodologies and guidance for developing and implementing a corporate security policy. Among the leaders are
-
BS 7799-1/ISO-I7799 Standard for Information Security Management Systems (ISMS) (complex and detailed, analogous to ISO 9000 for security)
-
Internet Security Systems' ADDME (Assess, Design, Deploy, Manage, Educate) Security Lifecycle Methodology (based on ISO 17799) (www.iss.net)
-
Cisco System's SAFE: A Security Blueprint for Enterprise Networks (www.cisco.com/safe)
-
The SANS Institute (www.sans.org)
All of these methodologies vary in complexity and depth, but maintain the same two-part theme: policy and process. The policy component must provide a comprehensive security policy that includes a combination of physical security measures, technical security measures, and administrative security measures to protect the information system. The process component must provide an iterative process to monitor and maintain the policy and associated measures. Cisco Systems' Security Wheel (Figure 8-2) provides a superb illustration of the iterative security management process.

Figure 8-2: Cisco Systems' Security Wheel
|
EAN: 2147483647
Pages: 158
- Measuring and Managing E-Business Initiatives Through the Balanced Scorecard
- Technical Issues Related to IT Governance Tactics: Product Metrics, Measurements and Process Control
- Governing Information Technology Through COBIT
- Governance in IT Outsourcing Partnerships
- The Evolution of IT Governance at NB Power