8.4 The Concept of CodeSource
| < Day Day Up > |
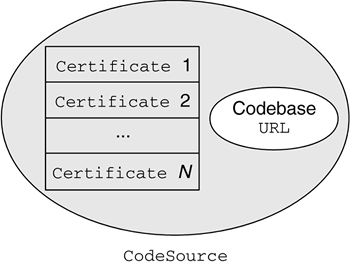
8.4 The Concept of CodeSourceListings 8.1 and 8.2 show that Permission s in the basic Java security model are granted based on the entities that signed the code and the URL location, called codebase , from which the code is coming. When a Java class is loaded onto the JVM, these two pieces of information, which are fundamental for access-control decisions, are encapsulated into a java.security.CodeSource object. Basically, Permission s in Java 2 are granted to CodeSource s. If two classes have been signed by the same signers and are loaded from the same codebase, they will also have the same CodeSource and therefore will be granted the same Permission s. In a CodeSource object, the signers are represented as an array of java.security.cert.Certificate objects, whereas the codebase is a java.net.URL object, as shown in Figure 8.6. The certificates stored in a CodeSource are for the public keys corresponding to the private keys that signed the code. Figure 8.6. Graphical Representation of a CodeSource |
| < Day Day Up > |
EAN: 2147483647
Pages: 164