Access Control Objectives
|
|
When working with access control, there are several primary objectives that must be met. They are:
-
Identification
-
Authentication
-
Authorization
-
Confidentiality
-
Integrity
-
Availability
-
Accountability
All of these are part of access control as a whole and work with the access control systems, objects, and subjects.
Obtaining Access
For an access control subject to obtain access to an access control object, the subject must go through three levels of access control.
-
The access control subject must be identified, which requires the transfer of some proof of identity.
-
Next, the access control subject must be authenticated based on the information transferred during the identification process.
-
After the subject has been identified and authenticated, it must be authorized for a level of access to the access control subject.
This flow of identification, authentication, and authorization is controlled by predefined rules stored in the access control system. These rules determine which access control subjects are authorized to gain access to the access control objects. They also define the methods used to authenticate and identify the access control subject. Figure 2.2 shows how the three parts of the access control system work together in order to allow an access control subject to gain access to an access control object.
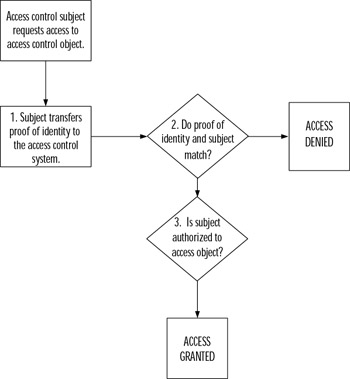
Figure 2.2: Obtaining Access Flowchart
Figure 2.2 starts with the access control subject requesting some type of access to an access control object. The access control system performs the step of identification to ensure that the access control subject is who or what it says it is (Step 1). Authentication then occurs between the access control subject and the access control system (Step 2). Depending on the outcome of this step, either access is denied or authorization is received. The access control system checks within its policies and pre-defined rules to determine whether or not an access control subject should have the level of access requested by the access control object (Step 3). Based on this determination, access to the access control object is either granted or denied at the level requested by the access control subject.
| Exam Warning | It is critical to know and understand how the authentication process works and how access control subjects obtain access-to-access control objects. |
Identification
Identification works hand-in-hand with authentication, and is defined as a process through which the identity of an object is ascertained. Typically, identification takes place by using some form of authentication to ascertain the identity of the object. To properly identify an object, it must prove that it is indeed what it appears to be. This is where authentication comes into play. As an example, when requesting access to a secure data center, technical personnel may be required to use a biometric hand scanner prior to gaining access to the building. The hand scanner authenticates that the technician is who he claims to be; therefore he has been positively identified and is allowed access to the building. (This is covered this in more detail within the "Authentication and Identification Techniques" section later in this chapter.)
Authentication
Authentication is defined as the process through which specific information is proven and verified. It is through the process of authentication that any form of access information is verified to be true. In the physical world, this can be the keyhole of a door lock verifying that the correct key has been inserted or that the correct fingerprint has been scanned. Authentication can occur with either the access control object or the access control subject and is controlled by the access control system. For example, when a user requests access to a file on a remote server, the access control system could require both the user and the remote server to be authenticated prior to allowing the user to access the file. (This is covered in more detail later in this chapter.)
Authorization
Authorization is a part of access control that is determined by the access control system. Authorization is defined as a process through which specific levels of access are granted to an access control subject. After an access control subject is authenticated and identified, the subject is authorized to have a specific level or type of access to the access control object. The level of access granted depends on the object being accessed and the specific rules defined in the access control system. Exercise 2.01 goes through the entire process of obtaining access to an object and demonstrates how the three parts of this process work together.
Exercise 2.01: Obtaining Access to Objects
This exercise examines the three-step process of obtaining access to objects. In this exercise, you will be logging into a site via FTP to demonstrate how the access control process works.
-
The first step is the process of identification. This will be done from the command line, so open up a command window and connect to the FTP site, as shown in Figure 2.3.
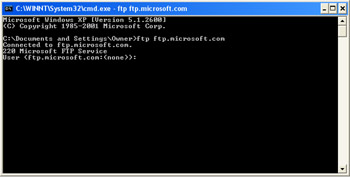
Figure 2.3: Connecting to an FTP Site -
To identify yourself, enter a user ID at the User prompt, as shown in Figure 2.4.
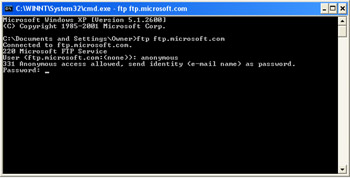
Figure 2.4: FTP User ID -
You are then prompted for a password. When you enter the password as shown in Figure 2.5, you will have completed the submission of your identification information.
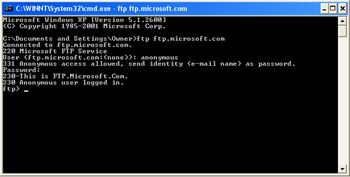
Figure 2.5: FTP Password -
As seen in Figure 2.5, the access control system accepted your identification information and authenticated you using the user ID and password given. The server also granted you a specific authorization level based on its rules for this account.
-
This process can be easily captured and analyzed with a sniffer and you can see each part of the access control process occur. A sniffer trace of this is shown in Figure 2.6.
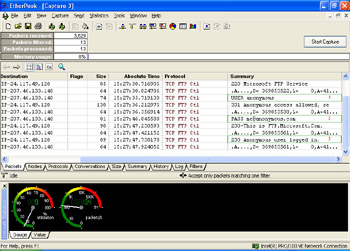
Figure 2.6: FTP Capture -
The capture shown in Figure 2.6 has three pieces of data outlined and numbered. The first shows the "USER" FTP command that sent part of your identification information. Next is the "PASS" FTP command that shows the other part of your identification information. It should be noted that your password was sent in cleartext. And finally, it shows a response from the server stating that you were authenticated.
| Test Day Tip | Knowing the three-step process for obtaining access will help you a great deal in understanding any questions presented regarding how an access control subject is granted access to an access control object. |
Assurance
Confidentiality, integrity, availability, and accountability are all parts of access control that relate specifically with the access control object. To ensure that the access control subject is able to gain access to the object, these three parts of access control must be maintained. By ensuring that these three parts of access control are performed, the access control system is able to assure the access control subject that the access control object will be held and maintained safely and reliably.
Ensuring that transactions between the access control subject and the access control object are kept confidential provides assurance. Also, guaranteeing that the access control object is kept safe by ensuring its integrity is part of providing assurance. Next, in order to assure that the access control object is properly controlled, availability must be ensured. Finally, ensuring that the access control system is accountable for its actions assures that the access control system is doing its job.
To provide assurance, the following four questions must be affirmatively answered:
-
Are transactions between the access control subject and the access control object confidential?
-
Is the integrity of the access control object ensured and guaranteed?
-
Is the access control object available to be accessed when needed?
-
Is the access control system accountable for what it authenticates?
If the answer to all of these questions is "yes," then assurance has been properly ensured. The following sections examine each part of assurance and define them in detail.
Confidentiality
Confidentiality is a required part of access control due to the nature of the objects for which access is controlled. Access to these objects must be kept confidential, which means that no access control object can be accessible to an unauthorized access control subject. For example, if a person uses online banking, they must be authenticated, identified, and authorized to access the data in their account. If the transactions between their computer and the bank's servers are available to be eavesdropped upon, there is no point in controlling access to the data. Keeping information confidential is key to controlling access to it.
Integrity
Integrity is the part of access control that ensures that the access control object is safe from being modified by unauthorized subjects. By ensuring the integrity of an object, you are offering a guarantee that the object is what it is supposed to be. Ensuring access control object integrity is done in many different ways, ranging from verifying the checksum of a file to putting a time-based lock on a door. The basic principal of integrity is simply ensuring that an access control object is safe from being modified or changed when it is not supposed to be.
Availability
By ensuring availability, administrators are assuring the access control subject that the access control object will be available when needed. To provide reliable access control, they must be able to ensure that any access control object will be available to the access control subject at the times specified by the access control system. This does not imply that the access control object is always accessible; indeed, being available at only certain times may be part of the security provided by the access control system. This is akin to keeping important documents in a secure document warehouse. The keeper of the warehouse is responsible for controlling access to the documents, but they are also responsible for ensuring that the documents will be accessible when needed. Many times with computer systems, availability is destroyed by a denial of service (DoS) attack. This type of attack is designed to make the access control object unavailable, which can undermine the overall reliability of the access control system.
Accountability and Logging
In a good access control system, the access control system itself is responsible for all authentication, identification, and authorization. Because of this, it is the most powerful part of access control. Any portion of a system asserting that much control over the operation of the system as a whole must be accountable for its actions. In the context of access control, ensuring that the access control system is accountable for any security-related transaction provides accountability. The security-related changes that the access control system must be accountable for include not only the three parts of granting access, but also any transactions occurring and any changes in the way the access control system itself works.
Whenever a transaction controlled by the access control system occurs, it should be logged in. This log is known as an audit trail or transaction log. These transactions may include an access control subject creating an access control object, changing an object, or viewing an object. Basically, anything that occurs that falls under the domain of access control should be logged in.
Another logging item that needs to be specifically addressed is the authentication audit trail or authentication log. This type of log is typically smaller than the overall transaction log, but is very important for providing accountability. Any time the access control system authenticates a request, it is accepting the proof of identity that the access control subject and object has presented and, based on that, grants or denies the request based on its policies or pre-defined rules. If the decisions made by the access control system are ever questioned, it must have a method of proving that it did exactly what it was supposed to. The authentication audit trail provides for this and allows a system of checks and balances to exist within access control.
| Exam Warning | Logging is a very important part of information security and plays a vital role in keeping systems secure. It is important to have a good understanding of this subject for the SSCP exam. |
An access control system must be aware not only of changes or access requests between the access control subjects and access control objects, but also within itself. For example, the access control system must know when an authorized (or unauthorized) access control subject attempts to change the way that the access control system operates. This may include changing the access control policies, changing the permission requirements on an access control object, or elevating the privileges of an access control subject. Most of these changes are recorded within the transaction log, but transactions regarding the changing of privileges of access control subjects are important enough to warrant having their own audit trail. This log is called the privilege elevation audit trail or privilege elevation log. This log is designed to provide accountability for any changes in the privileges of access control subjects. As this is one of the most frequently examined transactions when a security breach occurs, it is very important that the access control system maintain a log of what changes have occurred related to privilege elevation.
Maintaining all of these logs is critical to ensuring that the access control system is accountable for all changes that it makes. This provides assurance that the access control system is doing what it is supposed to, and if it is ever questioned, it can be tracked through one of the audit trails. Keep in mind that the audit trails are there not only to track the functionality of the access control system itself, but also the administrators of that system. If someone is abusing their administrative privileges, this can be easily tracked and proven by the audit logs. This is yet another way of providing assurance that the overall access control system is safe and effective.
|
|
EAN: 2147483647
Pages: 135