Introduction
|
|
When looking at the domains of the SSCP exam, the first subject listed is access controls. The heart and soul of information security is controlling access to objects. All other security measures and techniques are pointless if the objects they are protecting have no access controls. This is the foundation upon which all other security-related subjects are based.
So what is access control? Access control encompasses the security controls, processes, or procedures whereby access to specific objects is either granted or denied based on pre-established policies or rules. Access control is made up of many different parts, but at its roots is a very simple concept: Allow objects to be accessed (limiting the manner in which they are accessed) by authorized users, while denying access to unauthorized users.
To understand access control, it is best to first break it down into individual parts. First, there are the objects that need to be accessed. These objects are referred to as access control objects because they are objects that need to have controlled access. Objects consist not only of data, but also hardware devices, data networks, and buildings. When working with information security, almost anything can be considered an access control object.
Another part of access control are access control subjects, which are the users, programs, and processes that request permission to access control objects. It is these access control subjects that must be identified, authenticated, and either granted or denied access to the access control objects.
The final part of access control is the procedures, processes, and controls in place that verify the authenticity of the request, the identity of the access control subject, and determines the levels of access that should be granted to the object. These are called access control systems and interface directly with the access control objects and access control subjects.
When all three parts of access control are combined, there is an overall security approach that determines what should be accessed by whom and at what level. It is upon this foundation that all information security is based. A diagram of how all of this ties together is shown in Figure 2.1.
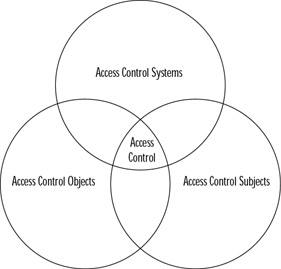
Figure 2.1: Access Control
Access control can be implemented in many different ways, all of which control access to data, systems, or hardware.
-
Physical (that is, biometric device to secure a door)
-
Hardware (that is, a dedicated firewall)
-
Software (that is, built-in application security)
-
Policy (that is, a workplace security policy)
-
Network (that is, secure networking protocols)
This chapter covers the three parts of access control and how they work together. The different access control systems and how they are implemented and operate are also discussed. This chapter also examines the dark side of information security by showing how these controls can be bypassed or overridden by intruders.
|
|
EAN: 2147483647
Pages: 135