Authentication Types
|
|
Authentication is basically the transfer of some form of information that proves that you are who you say you are. This can be in many different forms, but there are three basic types under which all of the different forms of authentication fall.
-
Something you know
-
Something you have
-
Something you are
In addition to these three primary types of authentication, there are also combinations of these types, which are much more secure and difficult to crack. The following sections cover several of these combinations and discuss how they increase the overall security of the access control system.
Something You Know
The something you know authentication type basically relies on the access control subject to memorize and know specific facts that can be used to prove who they are. For example, this type of authentication includes passwords, personal identification numbers (PINs), facts about the subject's life or family, code words, and so on. All of these require the subject to know a specific fact and respond with it when requested.
The most popular among these as it relates to IT security is the password. In a good access control system, passwords are required to gain access to any access control object. The advantage to passwords is that they are very common and easy to use. There are several different types of passwords, which are shown in Table 2.1.
| Password Type | Definition |
|---|---|
| Cognitive | Cognitive data that the user knows such as mother's maiden name or favorite color |
| Dynamic | Passwords that change upon each consecutive login |
| One Time | Passwords that are only valid for a single use and are thereafter useless |
| Passphrase | A password based on a group of words or phrase |
| Static | A normal password which is only changed on request |
For a password to be easy to remember, it must be something that the user can relate to and understand. Any combination of symbols, letters, and numbers work for a password, but the more secure the password is, the easier it is for the user to forget. This leads to the problem where the user writes down their password. Going through a typical office building, more than 20 percent of users will typically have their passwords written down somewhere in the vicinity of their computers. This is a major security problem and one that is battled in almost every office building in the world.
Based on this, users typically choose their own password rather than having one randomly generated, and they generally make it a password that is easy for them to remember. For instance, most users will use their birthdays, names, or favorite pet's name for their password. Unfortunately, this also makes their passwords easy to guess.
A major disadvantage of password authentication comes into play after an intruder obtains the password in some manner. This type of authentication is repudable, meaning there is no proof that it is actually the password owner who is using the password. Using combinations of authentication types, which is covered later in this section, typically solves this problem.
Since passwords are something that must be used in current access control systems, there are several best practices that will help make the passwords as secure as possible. First, use words that are easy to remember (so it is not tempting to write them down) but are difficult to guess. In addition, replacing letters in the words with numbers or symbols helps by adding another layer of difficulty when trying to crack the password. Ensure that none of the following are used in a password:
-
Names
-
Important dates
-
Phone numbers
-
Words (in any language) which could be found in a dictionary
-
Simple words such as "password" or "computer"
By following these recommendations, users will be able to create strong passwords that are difficult to crack and impossible to guess.
Something You Have
The something you have authentication type relies on some form of authentication that the access control subject physically has. This could be anything from a driver's license that authenticates someone as a valid driver of vehicles, to an ATM card used to authenticate them to their bank. Several other examples of this type of authentication are:
-
Smart cards
-
Proximity cards
-
Identification tokens
-
Keys
-
Identification badges
-
Passports
-
Transponders
An access control subject would have to physically have all of these forms of identification available to be authenticated. If the access control subject does not have a physical form of identification, they are not authenticated.
The security offered by this type of authentication is also repudable, similar to the something you know type of authentication. However, it offers a few advantages. First of all, no one can guess or crack a physical form of identification. Secondly, since there is nothing to memorize, there is nothing for the user to write down.
The disadvantage of this type of authentication is that the physical form of identification can be stolen. Since it is repudable, no one can prove that the person using it is actually the person who is authorized to do so. Also, some physical forms of authentication can be copied or cloned, which can result in more than one person having a copy. Most secure physical forms of identification have controls in place which make them difficult to copy or clone, but with enough perseverance, it can be done.
Something You Are
The something you are authentication type is relatively new. Although it has been around for several years, it is only now that it is becoming affordable enough to be commonly implemented. This authentication type is known as biometrics and is based on the science of identifying people based on their physical characteristics.
The science of biometrics is based on the concept that, while many people share common traits, there are certain traits that are unique to almost every individual. It is by detecting and measuring these traits that biometric authentication works. Some of the measurable traits commonly used for authentication are:
-
Fingerprints
-
Signatures
-
Eye characteristics
-
Facial characteristics
-
Voiceprints
-
DNA
All of these traits are detectable, measurable, and generally unique to every individual. A biometric system is designed to scan for one or more of these traits and compare the measure of the trait being scanned against a database of pre-scanned measurements. By doing so, the biometric system is able to authenticate the access control subject if they are in the database of allowed subjects.
This system has many advantages over the other authentication types. No one can guess or crack a password, if there is not a password to guess or crack. There is nothing that can be stolen or copied aside from actual body parts of the person being scanned. It is very difficult to duplicate any of the measured characteristics being used by the biometric system.
Biometric authentication has some serious disadvantages as well. The cost of biometrics is on the decline, but it is still the most expensive authentication type used today. The hardware and software necessary to provide accurate authentication is expensive and difficult to maintain. In addition, as biometric authentication is still relatively new to the field of information security, there are many learning curve problems to overcome with both the manufacturers and the administrators. An excellent example of this is the identification and response to false positives and false negatives. These are situations in which either the biometric scanner authenticates someone that should not have been or does not authenticate someone who should have been, respectively. Most IT administrators want to have a zero percent false positive rate and the users want to have a zero percent false negative rate. With most biometric hardware and software this is an impossible goal, so a middle ground must be met, which can be very difficult to do.
One of the greatest disadvantages of biometric authentication is privacy. Most people do not want to have private information such as their DNA sitting in a computer database just so they can gain access to something. In addition, with the facial characteristics recognition aspect of biometric authentication, there comes into play the possibility of you're a person's every movement or action being tracked remotely by camera. Many people consider this a paranoid point of view, but it is a valid privacy concern that many individuals have. These concerns must be addressed within any authentication type that is implemented. A good authentication type is completely useless if the end users refuse to make use of it.
The Dawn of Biometrics
We are working in a very exciting time in the realm of information security. Biometric technology has been around for many years, but only now is it becoming reliable and affordable enough to be implemented as a common authentication method. Every few months a new device comes on the market that uses this technology to improve security. With this advanced technology in hand, administrator's can do a great deal to increase system security while making obtaining access easier for users.
The day is coming where a user will simply sit down at their desk and be identified by their smell and behavior through biometric devices. If the companies creating these devices can alleviate the privacy concerns that many people have about biometrics, there is no end to the uses of biometric technology.
Authentication Type Combinations
There are three basic types of authentication: "something you have," "something you know," and "something you are". In addition, these three types of authentication can be combined to provide even greater security. These combinations are called factors of authentication. A two-factor authentication method would make use of two of the three types of authentication. Three-factor authentication uses all three types of authentication and is considered the strongest form of authentication.
Some examples of authentication type combinations are: requiring that a PIN be entered in combination with a six-digit code displayed on an authentication token, or requiring a password, smart card, and fingerprint scan in order to enter a secure area. These combinations provide more security than any of the three authentication types can provide by themselves. By using these combinations, administrators can increase the security of an access control system and lower the risk caused by the disadvantages of the individual access control types.
Enterprise Authentication
When working with authentication within a large enterprise environment, every small detail of the authentication system grows to enormous proportions due to the number of users involved. For example, implementing a new password expiration policy can cause thousands of passwords to be invalidated at once, generating huge call volumes to internal help desks and lost productivity from the users. These types of things must always be kept in mind when dealing with security within large enterprises.
Due to the number of servers, host systems, and other computer systems that a user within a large enterprise must interface with, authentication within the enterprise becomes even more difficult to manage. If a user were required to use a different password or authentication type for every system they access, it would be impossible to remember them all and would inevitably lead to security breaches as the user tries to find ways around the system. The following sections go over a few technologies that have been created to help combat this problem
Single Sign-On
One solution for these security problems is known as Single Sign-On (SSO). With SSO, the user authenticates once, and the fact that they have been authenticated is passed on to each system that they attempt to access. Their initial authentication can take place using any authentication type or combination of types, while the authentication to subsequent systems can occur using an entirely different authentication type. Several vendors have come out with various forms of SSO technology to aid with authentication within large enterprises. Some of these SSO products are:
-
CA-Unicenter
-
IntelliSoft SnareWorks
-
Kerberos
-
SESAME
-
KryptoKnight
-
NetSP
-
Memco Proxima
-
Tivoli Global Sign-On
-
X.509
| Note | Each of these products offers their own advantages and disadvantages. It is beyond the scope of this book to compare them, as the SSCP exam is not vendor-specific. The SSCP exam expects you to understand the concept behind how they work as well as understanding the advantages and disadvantages of the technology itself. In addition, the SSCP exam requires that you understand some of the standards of SSO such as Kerberos and X.509. |
SSO technology also offers some advantages to the enterprise security administrator. When a new employee is hired, all of the accounts for the user on all of the systems can be created at the same time. This substantially decreases the amount of time necessary to create user accounts. In addition, when an employee is dismissed, all of their access to systems can be disabled quickly and simultaneously. This increases the security of the enterprise by helping to eliminate the security risk caused by vengeful ex-employees. Finally, when a user forgets their password or loses their token their password or authentication information can be easily and quickly updated in a single location. This also cuts down on the amount of time necessary to administer user accounts.
The primary disadvantage of SSO technology is that it is very difficult to implement properly and to integrate with all existing systems that may have their own authentication methods. Many host systems have their own proprietary authentication system, and each of these systems requires some work to integrate properly with SSO products. It cost more, and some enterprises choose not to spend the money regardless of the hours saved on user administration. Typically, SSO has a very high return on investment and pays for itself in a very short period of time. Due to the initial setup costs and the amount of time required to implement it properly, however, it is often considered too expensive and difficult to implement.
| Test Day Tip | Remember that SSO is primarily for the convenience of the user. This will help you to put SSO into perspective with the actual required portions of access control. |
Kerberos
Kerberos (currently Kerberos v5) is the preferred network authentication protocol used in many medium and large environments to authenticate users and services requesting access to resources. Kerberos is a network protocol designed to centralize authentication information for the user or service requesting the resource. This allows authentication of the access control subject by the host of the access control object, through the use of secure and encrypted keys and tickets (authentication tokens) from the authenticating Key Distribution Center (KDC). It allows for cross-platform authentication, and will be available in upcoming implementations of various network operating systems (NOSs). Kerberos is very useful in the distributed computing environments currently used, because it centralizes the processing of credentials for authentication. Kerberos utilizes time stamping of its tickets, to help ensure they are not compromised by other entities, and an overall structure of control that is called a realm. Some platforms use the defined terminology, while others such as Windows 2000 use their domain structure to implement the Kerberos concepts.
Kerberos is described in RFC 1510, available on the Web at www.cis.ohio-state.edu/cgi-bin/rfc/rfc1510.html. Developed and owned by the Massachusetts Institute of Technology, information about the most current and previous releases of Kerberos is available on the Web at http://web.mit.edu/kerberos/www.
Figure 2.7 shows the default components of a Kerberos v5 realm.
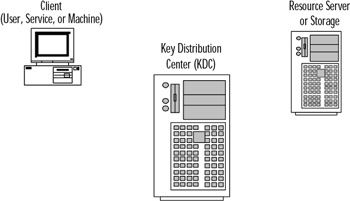
Figure 2.7: Kerberos Required Components
As can be seen in Figure 2.7, there is an authentication server requirement (the KDC). In a Kerberos realm, whether in a UNIX- or Windows-based operating system, the authentication process is the same. For this purpose, imagine that a client needs to access a resource on the resource server. Figure 2.8 follows the path for authentication during logon, and Figure 2.9 follows the resource access path.
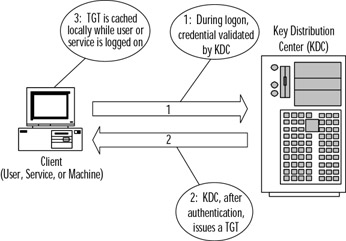
Figure 2.8: Authentication Path for Logon Access in a Kerberos Realm
As seen in Figure 2.8, two events are occurring as credentials are presented (password, smart card, biometrics) to the KDC for authentication. First, the authentication credential is presented to the KDC. Second, the KDC issues a Ticket Granting Ticket (TGT) that is associated with the access token while user's are actively logged in and authenticated. This TGT expires when the user (or service) disconnects or logs off the network. This TGT is cached locally for use during the active session.
Figure 2.9 shows the process for access control object access in a Kerberos realm. It starts by presenting the previously granted TGT to the authenticating KDC. The authenticating KDC returns a session ticket to the entity requesting access to the access control object. This session ticket is then presented to the remote resource server. The remote resource server, after accepting the session ticket, allows the session to be established to the object.
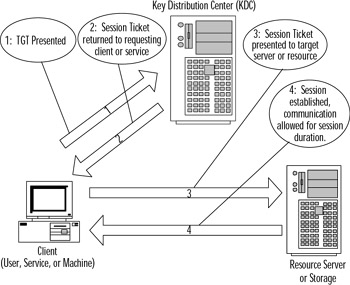
Figure 2.9: Resource Access in Kerberos Realms
Kerberos uses a time stamp and it is important to understand where and when the time stamp is used. Previously mentioned was the concept of non-repudiation, which is one reason for the use of time stamps. In the case of Kerberos, the time stamp is also used to limit the possibility of replay or spoofing of credentials. Replay is the capture of information, modification of the captured information, and retransmission of the modified information to the entity waiting to receive the communication. If unchecked, this allows for impersonation of credentials when seeking access. Spoofing is the substitution of addressing or authentication information to try to attain access to a resource based on information acceptable to the receiving host, but not truly owned by the sender. The initial time stamp refers to any communication between the entity requesting authentication and the KDC. Normally, this initial time period will not be allowed to exceed five minutes. If clocks are not synchronized between the systems, the credentials (tickets) will not be granted if the time differential exceeds the established limits. Session tickets from the KDC to a resource must be presented within this time period or they will be discarded. The session established between the resource server and the requesting entity is also time-stamped, but generally lasts as long as the entities logon credential is valid. This can be affected by system policies like logon hour restrictions, which are defined in the original access token. TGT tickets are not part of the default five-minute period. Rather, they are cached locally on the machine, and are valid for the duration of the logged-on session.
X.509
X.509 is a de facto standard based on an ITU Telecommunication Standardization Sector (ITU-T) recommendation for authentication using public keys (covered in great detail within Chapter 6). It bases its authentication on digitally signed public key certificates issued by a certificate authority (CA). This form of authentication is most commonly used for Secure Sockets Layer (SSL) transactions over Hypertext Transfer Protocol (HTTP), but also has many other uses. For example, it can be used as for SSO purposes because it allows for an access control subject to be authenticated a single time for multiple connections and also allows for non-repudiation.
Remote Access Authentication
Providing for reliable authentication that is easily administered for remote users is another challenge within large enterprises. Most large enterprises have user's who perform work or need access to corporate data while away from the main office. To properly enforce security policies with these remote users, some form of remote access is implemented by the enterprise. Implementing a good access control system for this type of environment is challenging, but there are several authentication options available to fulfill this need.
The first and most obvious solution is to use the default authentication method of the software being used for remote access. This could be a proprietary system or it could be based on some other standard authentication method. Typically, this works great for small remote access systems, but when dealing with large enterprises a more full-featured authentication method is usually needed. Two examples of enterprise remote access control systems are Terminal Access Controller Access Control System (TACACS) and Remote Authentication Dial-In User Service (RADIUS).
| Test Day Tip | The key point to remote access is that it involves the use of a public communications medium. Remember this when you are debating on whether or not these transmissions should be encrypted. |
TACACS
An older and less often used remote access authentication system is TACACS. TACACS is an authentication protocol that allows one or more remote access servers to forward identification information to a remote TACACS authentication server for authentication and authorization. It allows for a centralized access control approach that keeps all access control changes isolated to a single place. This helps a great deal when considering the amount of administration necessary to perform access control in a decentralized environment where every server has its own user list and access control system.
When the TACACS server receives the identification data, it either returns authorization information or denies access to the user. This information is passed back to the remote access server in cleartext and the remote access server responds appropriately. This causes a security problem as authentication information is going across the network in a non-encrypted form. A later version of TACACS called TACACS+ allows for encryption of this data and has now supplanted TACACS.
RADIUS
Another common remote access authentication system is RADIUS. This is a protocol used for providing authentication for one or more remote access servers. RADIUS is similar to TACACS in that it is a centralized approach to access control and helps keep administration to a minimum within large enterprises.
Using RADIUS, a remote access server accepts the authentication credentials from the access control subject and passes them along to the RADIUS server for authentication. The RADIUS server then responds to the remote access server either with authorization information or denying access. A major advantage of RADIUS is that communication between the RADIUS server and the remote access server is encrypted, which helps increase the overall security of access control.
|
|
EAN: 2147483647
Pages: 135