2-2 area area-id authentication message-digest
| < Free Open Study > |
2-2 area area-id authentication message-digestNOTE This command requires the following additional commands: For a physical interface: ip ospf message-digest-key key-id md5 password (see Section 19-9) For a virtual link if authentication is used in Area 0: area transit-area virtual-link router-id message-digest-key key-id md5 password (see Section 2-20) Syntax Description:
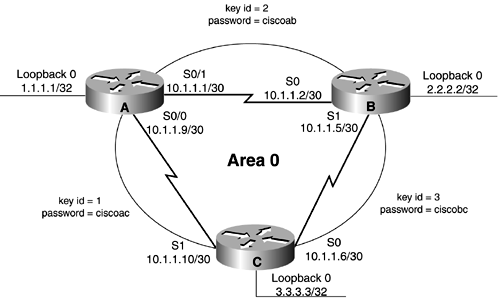
Purpose: To enable MD5 password authentication in an OSPF area. OSPF MD5 authentication requires the use of the router configuration command to enable authentication in an area and the interface or virtual link command for key and password configuration. Since this router configuration command enables authentication in an area, every interface in the area must be configured with an authentication key and password if using Cisco IOS Software Release 11.X or earlier. In Cisco IOS Software Release 12.X, the authentication used on an interface can be different from the authentication enabled for an area. When using Cisco IOS Software Release 12.X, the authentication method used on different interfaces in the same area does not need to be the same. Authentication can be turned off on selected interfaces using the command ip ospf authentication null (see Section 19-1). The key and password do not need to be the same on every interface, but both ends of a common link need to use the same key and password. Authentication is enabled by area (Cisco IOS Software Release 11.X and earlier) so it is possible to employ authentication in one area without using authentication in other areas. The password is encrypted, so it is extremely difficult for someone to intercept OSPF protocol packets and compromise the password. Initial Cisco IOS Software Release: 11.0 Configuration Example 1: MD5 Password AuthenticationFor the network in Figure 2-2, initially configure OSPF without authentication in Area 0. Figure 2-2. Network Used to Demonstrate OSPF MD5 Authentication Configuration and Troubleshooting Router A interface Loopback0 ip address 1.1.1.1 255.255.255.255 ! interface Serial0/0 ip address 10.1.1.9 255.255.255.252 ! interface Serial0/1 ip address 10.1.1.1 255.255.255.252 clock rate 64000 ! router ospf 1 network 10.1.1.0 0.0.0.15 area 0 _______________________________________________________________________ Router B interface Loopback0 ip address 2.2.2.2 255.255.255.255 ! interface Serial0 ip address 10.1.1.2 255.255.255.252 ! interface Serial1 ip address 10.1.1.5 255.255.255.252 clock rate 64000 ! router ospf 1 network 10.1.1.0 0.0.0.15 area 0 _______________________________________________________________________ Router C interface Loopback0 ip address 3.3.3.3 255.255.255.255 ! interface Serial0 ip address 10.1.1.6 255.255.255.252 ! interface Serial1 ip address 10.1.1.10 255.255.255.252 clock rate 64000 ! router ospf 1 network 10.1.1.0 0.0.0.15 area 0 Verify the OSPF configuration on Routers A, B, and C by displaying the state of each router's OSPF neighbors. rtrA# show ip ospf neighbor Neighbor ID Pri State Dead Time Address Interface 3.3.3.3 1 FULL/ - 00:00:38 10.1.1.10 Serial0/0 2.2.2.2 1 FULL/ - 00:00:37 10.1.1.2 Serial0/1 _______________________________________________________________________ rtrB# show ip ospf neighbor Neighbor ID Pri State Dead Time Address Interface 1.1.1.1 1 FULL/ - 00:00:35 10.1.1.1 Serial0 3.3.3.3 1 FULL/ - 00:00:30 10.1.1.6 Serial1 _______________________________________________________________________ rtrC# show ip ospf neighbor Neighbor ID Pri State Dead Time Address Interface 2.2.2.2 1 FULL/ - 00:00:30 10.1.1.5 Serial0 1.1.1.1 1 FULL/ - 00:00:37 10.1.1.9 Serial1 Verify that OSPF is not using authentication. rtrA# show ip ospf Routing Process "ospf 1" with ID 1.1.1.1 Supports only single TOS(TOS0) routes SPF schedule delay 5 secs, Hold time between two SPFs 10 secs Minimum LSA interval 5 secs. Minimum LSA arrival 1 secs Number of external LSA 0. Checksum Sum 0x0 Number of DCbitless external LSA 0 Number of DoNotAge external LSA 0 Number of areas in this router is 1. 1 normal 0 stub 0 nssa Area BACKBONE(0) Number of interfaces in this area is 2 Area has no authentication SPF algorithm executed 6 times Area ranges are Number of LSA 3. Checksum Sum 0x25F8D Number of DCbitless LSA 0 Number of indication LSA 0 Number of DoNotAge LSA 0 Modify the configurations on Routers A, B, and C by adding MD5 password authentication to area 0. For this example, use the passwords ciscoab, ciscobc, and ciscoac to demonstrate that multiple passwords can be used in an area. Router A interface Loopback0 ip address 1.1.1.1 255.255.255.255 ! interface Serial0/0 ip address 10.1.1.9 255.255.255.252 ip ospf message-digest-key 1 md5 ciscoac ! interface Serial0/1 ip address 10.1.1.1 255.255.255.252 ip ospf message-digest-key 2 ciscoab clock rate 64000 ! router ospf 1 area 0 authentication message-digest network 10.1.1.0 0.0.0.15 area 0 _______________________________________________________________________ Router B interface Loopback0 ip address 2.2.2.2 255.255.255.255 ! interface Serial0 ip address 10.1.1.2 255.255.255.252 ip ospf message-digest-key 2 md5 ciscoab ! interface Serial1 ip address 10.1.1.5 255.255.255.252 ip ospf message-digest-key 3 md5 ciscobc clock rate 64000 ! router ospf 1 area 0 authentication message-digest network 10.1.1.0 0.0.0.15 area 0 _______________________________________________________________________ Router C interface Loopback0 ip address 3.3.3.3 255.255.255.255 ! interface Serial0 ip address 10.1.1.6 255.255.255.252 ip ospf message-digest-key 3 ciscobc ! interface Serial1 ip address 10.1.1.10 255.255.255.252 ip ospf message-digest-key 1 md5 ciscoac clock rate 64000 ! router ospf 1 area 0 authentication message-digest network 10.1.1.0 0.0.0.15 area 0 VerificationVerify that the OSPF neighbor relationships are still active. rtrA# show ip ospf neighbor Neighbor ID Pri State Dead Time Address Interface 3.3.3.3 1 FULL/ - 00:00:31 10.1.1.10 Serial0/0 2.2.2.2 1 FULL/ - 00:00:30 10.1.1.2 Serial0/1 _______________________________________________________________________ rtrB# show ip ospf neighbor Neighbor ID Pri State Dead Time Address Interface 1.1.1.1 1 FULL/ - 00:00:38 10.1.1.1 Serial0 3.3.3.3 1 FULL/ - 00:00:33 10.1.1.6 Serial1 _______________________________________________________________________ rtrC# show ip ospf neighbor Neighbor ID Pri State Dead Time Address Interface 2.2.2.2 1 FULL/ - 00:00:33 10.1.1.5 Serial0 1.1.1.1 1 FULL/ - 00:00:30 10.1.1.9 Serial1 Verify that MD5 authentication is enabled for Area 0. rtrA# show ip ospf Routing Process "ospf 1" with ID 1.1.1.1 Supports only single TOS(TOS0) routes SPF schedule delay 5 secs, Hold time between two SPFs 10 secs Minimum LSA interval 5 secs. Minimum LSA arrival 1 secs Number of external LSA 0. Checksum Sum 0x0 Number of DCbitless external LSA 0 Number of DoNotAge external LSA 0 Number of areas in this router is 1. 1 normal 0 stub 0 nssa Area BACKBONE(0) Number of interfaces in this area is 2 Area has message digest authentication SPF algorithm executed 2 times Area ranges are Number of LSA 3. Checksum Sum 0x14A19 Number of DCbitless LSA 0 Number of indication LSA 0 Number of DoNotAge LSA 0 The password used can be seen by anyone looking at your configuration. For added security, the password in the configuration can be encrypted using the global configuration command service password-encryption, as shown in the following configuration. Router A service password-encryption Listing the configuration will show that the password has been encrypted. rtrA# show running-config Building configuration... Current configuration: ! version 12.0 service timestamps debug uptime service timestamps log uptime service password-encryption ! hostname rtrA ! ip subnet-zero ! interface Loopback0 ip address 1.1.1.1 255.255.255.255 no ip directed-broadcast ! interface Serial0/0 ip address 10.1.1.9 255.255.255.252 no ip directed-broadcast ip ospf message-digest-key 1 md5 7 02050D4808090E22 no ip mroute-cache ! interface Serial0/1 ip address 10.1.1.1 255.255.255.252 no ip directed-broadcast ip ospf message-digest-key 2 md5 7 045802150C2E4D4C clockrate 64000 Configuration Example 2: Changing Keys and PasswordsFor additional security, you may choose to periodically change the key and password. With clear-text authentication, changing passwords will cause a loss of OSPF connectivity from the time you change the password on one interface until you change the password at the other end of the link. With MD5 authentication, you can configure a new key and password on a link while leaving the old key and password in place. The old key and password will continue to be used until the new key and password are configured on the other end of the link. Modify the key and password on the link between Routers A and B. Add a new key and password on Router A in order to observe the behavior when the new key and password have only been configured on one end of the link. Router A interface Serial0/1 ip address 10.1.1.1 255.255.255.252 no ip directed-broadcast ip ospf message-digest-key 2 md5 ciscoab ip ospf message-digest-key 4 md5 cisconew clockrate 64000 Verify that the OSPF neighbor relationship between Routers A and B is still active. rtrA# show ip ospf neighbor Neighbor ID Pri State Dead Time Address Interface 3.3.3.3 1 FULL/ - 00:00:34 10.1.1.10 Serial0/0 2.2.2.2 1 FULL/ - 00:00:35 10.1.1.2 Serial0/1 You can determine if Router A is using both keys when communicating with Router B by viewing the interface properties or by enabling OSPF debugging. rtrA# show ip ospf interface s0/1 Serial0/1 is up, line protocol is up Internet Address 10.1.1.1/30, Area 0 Process ID 1, Router ID 1.1.1.1, Network Type POINT_TO_POINT, Cost: 64 Transmit Delay is 1 sec, State POINT_TO_POINT, Timer intervals configured, Hello 10, Dead 40, Wait 40, Retransmit 5 Hello due in 00:00:08 Neighbor Count is 1, Adjacent neighbor count is 1 Adjacent with neighbor 2.2.2.2 Suppress hello for 0 neighbor(s) Message digest authentication enabled Youngest key id is 4 Rollover in progress, 1 neighbor(s) using the old key(s): key id 2 rtrA# debug ip ospf events OSPF events debugging is on rtrA# 01:30:25: OSPF: Rcv hello from 3.3.3.3 area 0 from Serial0/0 10.1.1.10 01:30:25: OSPF: End of hello processing 01:30:26: OSPF: Rcv hello from 2.2.2.2 area 0 from Serial0/1 10.1.1.2 01:30:26: OSPF: End of hello processing 01:30:30: OSPF: Send with youngest Key 1 01:30:30: OSPF: Send with key 2 01:30:30: OSPF: Send with key 4 Notice that both keys are being used for authentication. Configure the new key and password on Router B while leaving the old key and password in place. Router B interface Serial0 ip address 10.1.1.2 255.255.255.252 no ip directed-broadcast ip ospf message-digest-key 2 md5 ciscoab ip ospf message-digest-key 4 md5 cisconew Routers A and B will now use the youngest key (the last key configured). rtrA# show ip ospf interface s0/1 Serial0/1 is up, line protocol is up Internet Address 10.1.1.1/30, Area 0 Process ID 1, Router ID 1.1.1.1, Network Type POINT_TO_POINT, Cost: 64 Transmit Delay is 1 sec, State POINT_TO_POINT, Timer intervals configured, Hello 10, Dead 40, Wait 40, Retransmit 5 Hello due in 00:00:02 Neighbor Count is 1, Adjacent neighbor count is 1 Adjacent with neighbor 2.2.2.2 Suppress hello for 0 neighbor(s) Message digest authentication enabled Youngest key id is 4 The old key and password can now be removed from routers A and B using the no form of the interface command. Troubleshooting
Router B interface Serial0 ip address 10.1.1.2 255.255.255.252 no ip ospf message-digest-key 2 md5 ciscoab ip ospf message-digest-key 5 md5 ciscoab List the OSPF neighbors for Router A. rtrA# show ip ospf neighbor Neighbor ID Pri State Dead Time Address Interface 3.3.3.3 1 FULL/ - 00:00:31 10.1.1.10 Serial0/0 Router A has lost Router C as a neighbor. Enable debugging on Router A to see if you can determine the problem. rtrA# debug ip ospf events OSPF events debugging is on rtrA# 00:09:34: OSPF: Rcv pkt from 10.1.1.2, Serial0/1 : Mismatch Authentication Key - No message digest key 5 on interface Be careful when configuring passwords. A space is a valid character, so if you use the password cisco<space> then there will be a password mismatch, but you won't be able to tell by looking at the configuration, especially if the password is encrypted in the configuration. On Router A, remove the OSPF router configuration command area 0 authentication message-digest. Restore the proper key on Serial0 on Router B. Router A interface Serial0/0 ip address 10.1.1.9 255.255.255.252 ip ospf authentication-key cisco ! router ospf 1 no area 0 authentication message-digest _______________________________________________________________________ Router B interface Serial0 ip address 10.1.1.2 255.255.255.252 no ip ospf message-digest-key 5 md5 ciscoab ip ospf message-digest-key 2 md5 ciscoab Router A should drop both OSPF neighbors. rtrA# show ip ospf neighbor Neighbor ID Pri State Dead Time Address Interface 3.3.3.3 1 INIT/ - 00:00:38 10.1.1.10 Serial0/0 2.2.2.2 1 INIT/ - 00:00:39 10.1.1.2 Serial0/1 Now debug the OSPF traffic on Router B or C to determine the problem. rtrB# debug ip ospf events OSPF events debugging is on rtrB# 21:43:04: OSPF: Rcv hello from 3.3.3.3 area 0 from Serial1 10.1.1.6 21:43:04: OSPF: End of hello processing 21:43:05: OSPF: Send with youngest Key 4 21:43:05: OSPF: Send with youngest Key 3 21:43:08: OSPF: Rcv pkt from 10.1.1.1, Serial0 : Mismatch Authentication type. I nput packet specified type 0, we use type 2 Routers B and C are using type 2 authentication (MD5) and Router A is using type 0 authentication (none). |
| < Free Open Study > |
EAN: 2147483647
Pages: 236