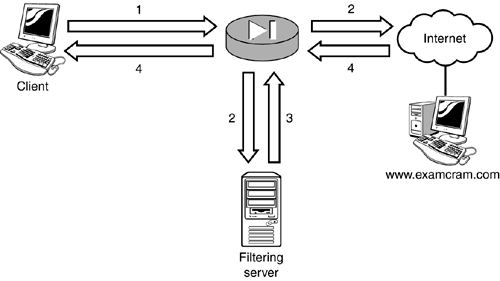
Web Traffic Filtering
| Although the firewall's main purpose is to protect inside users from outside threats, the PIX firewall can also help control which Web sites internal users can access. The PIX firewall can be linked to a URL filtering server such as WebSense or N2H2, which provide Internet monitoring and URL Web site blocking if necessary. Figure 8.4 displays the basic Web filter process, which includes these steps:
Figure 8.4. URL filtering process. Configuring WebSense and N2H2The PIX firewall can be configured to use WebSense or N2H2 URL filtering servers for HTTP traffic. The basic steps are the same for each vendor's configuration on the PIX firewall. They are as follows :
The url-server CommandThe first step is to identify the URL server you want to use. You use two different commands, based on which vendors you are actually using. However, their basic structures are the same: Identify the interface, identify the host, and set the timeout durations. The command syntax is as follows: pixfirewall(config)# [no] url-server [<(if_name)>] [vendor websense] host <local_ip> [timeout <seconds>] [protocol TCPUDP [version 14]] pixfirewall(config)#[no] url-server [<(if_name)>] vendor n2h2 host <local_ip> [port <number>] [timeout <seconds>] [protocol TCPUDP] The filter url CommandAfter the servers have been configured, you need to specify which traffic will be forwarded to them. The filter URL command is used to identify which local users' Web traffic will be forwarded to the URL servers. The following displays the syntax needed: pixfirewall(config)# [no] filter url <port>[-<port>]except <lcl_ip> <mask> <frgn_ip> <mask> [allow] The filter url command allows you to be granular enough to select specific inside ( lcl_ip ) to outside ( frgn_ip ) ranges to filter. The except option enables you to exclude certain IP addresses from the filter. The allow option defines what the PIX firewall will do when WebSense or N2H2 servers are offline. If allow is stated, Web traffic is allowed to pass through the firewall. Conversely, if allow is not stated, all Web traffic is blocked. The url-cache CommandWeb filtering does come at a cost to performance. The delays introduced by querying an external URL filtering server can be an issue. By using the url-cache command, the PIX can cache a request locally on the firewall and reuse this cache the next time a user goes to the same destination. This decreases the impact of delays and increases the users' throughput. However, you do lose some tracking information about users' Web activity that would have been recorded on the URL server. The command syntax for the url-cache command is shown here: pixfirewall(config)# [no] url-cache <dstsrc_dst> size <Kbytes> A URL Filtering ExampleThe following sequence of commands configures a WebSense filter as the filtering server. It then specifies that all traffic is to be forwarded to the WebSense filter, except traffic initiated by 192.168.1.11: pixfirewall(config)# url-server (inside) vendor websense host 192.168.1.101 timeout 5 protocol TCP version 4 pixfirewall(config)# filter url http 0 0 0 0 pixfirewall(config)# filter url except 192.168.1.11 255.255.255.255 0 0 allow pixfirewall(config)# url-cache dst 128 Monitoring URL FilteringSeveral commands allow you to view your configuration and monitor your URL filtering traffic. Table 8.4 lists several of these. Table 8.4. URL Filtering Commands
|
EAN: 2147483647
Pages: 218
- Legal, Regulations, Compliance, and Investigations
- Initiation of the System Authorization Process
- Appendix D The Information System Security Engineering Professional (ISSEP) Certification
- Appendix E The Information System Security Management Professional (ISSMP) Certification
- Appendix F Security Control Catalog