14.1 Properties of the Internet Protocol The Internet Protocol was developed with the idea of maintaining communication between two systems even when some transmission sections fail. For this reason, the Internet Protocol was developed on the basis of the principle of datagram switching, to transport IP data units, rather than on that of circuit-switching, like conventional telephone network. The following sections describe the protocol mechanisms of the Internet Protocol. Section 14.2 will then explain how IP is implemented in the Linux kernel. Figure 14-1 shows how the Internet is structured. Rather than being one single network, the Internet is composed of many smaller local area networks, which are connected by routers. This is the reason why it is often called the network of networks or global network. Each network connected to the Internet can be different both in size and in technology. Within one network (e.g., the network of a university), it is often meaningful to build several subnetworks. These often independent networks and subnetworks are connected by routers and point-to-point lines. Figure 14-1. The structure of the global Internet. 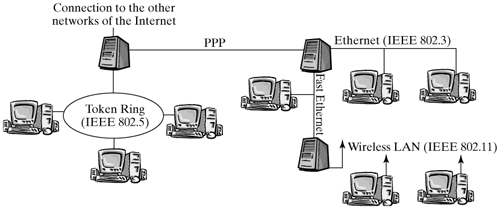
The interconnection of single local area networks offers a way to send data from an arbitrary computer to any other computer within the internetwork. Before it sends a packet, an Internet computer checks for whether the destination computer is in the same local area network. If this is not the case, then the data packet is forwarded to the next router. If both the sender and the receiver are in the same local area network, then the packet is delivered to the receiver directly over the physical medium. In either case, the IP layer uses the service of the data-link layer to physically transport the packet (horizontal communication see Section 3.2). Let's assume that, in the first case, the packet has not yet arrived in the destination computer. The router checks the destination address in the IP packet header and the information in the routing table to determine how the packet should be forwarded. Next, the packet travels from one router to the next until it eventually arrives in the destination computer. Chapter 16 discusses routing in IP networks. 14.1.2 The IP Packet Header Figure 14-2 shows the format of an IP packet. The fields of the IP packet header have the properties described below. Figure 14-2. Packet-header format of the Internet Protocol. 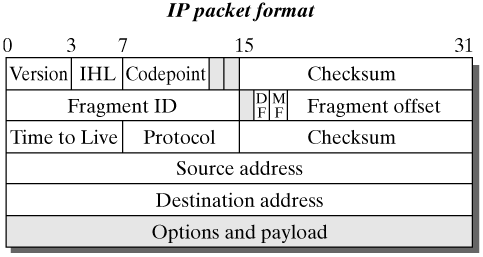
Version: This field contains the version number of the Internet Protocol used. Including the version number provides a way to use several versions of the Internet Protocol. Currently, only versions v4 and v6 are defined. In general, the two versions are not specified in the Version field; they are identified by their protocol identifiers on the MAC layer (0x800 for IPv4, 0x86DD for IPv6 see include/linux/if_ether.h) IHL (Internet Header Length): This field contains the length of the packet header, because it can be longer than 20 bytes, if options are used. The length is stated in multiples of 32 bits. The smallest valid value is 5 (no options), and the highest value is 15 (corresponds to a header length of 60 bytes). Codepoint: This field was originally called Type of Service. Its purpose was changed to Differentiated Services Codepoint in RFC 2474. This field shows the forwarding behavior used [NBBB98]. Total length: This value includes the entire length of the IP packet. Its 16-bit length makes the maximum size of an IP datagram 65,535 bytes. RFC 791 specifies that each IP-enabled computer should be capable of processing data packets with a size of 576 bytes. In general, however, it is possible to process packets with a bigger length. Otherwise, a packet has to be fragmented. (See Section 14.2.3.) Fragment ID: The destination computer can use this identifier, together with the sender address, to reassemble fragments of IP datagrams to reconstruct the original datagrams. All fragments of an IP datagram have the same fragment ID, which is set by the sender. Flags: An IP packet can include two flags (the third flag is currently not used): Don't Fragment (DF) and More Fragments (MF). MF is used for a fragmented packet. The DF bit means that a datagram must not be fragmented, even if this means that the packet cannot be transported any further. The MF bit shows whether more fragments follow this IP packet (i.e., the MF flag is set in all fragments of a datagram, except for the last fragment). Fragment Offset: This field specifies where in relation to the beginning of the entire datagram the present fragment has to be ordered. This information is required to reassemble the original packet from the individual fragments in the destination computer. Since this field has a size of 13 bits, a maximum number of 8192 fragments can be created from one IP datagram. All fragments, except the last fragment, have to be a multiple of 8 bytes. This is the elementary fragment unit. Time To Live (TTL): This is a counter used to limit the lifetime of IP packets. This field originally stated the maximum lifetime in seconds, but is used today to specify the maximum number of intermediate systems (routers). Each router on the path has to decrement this counter by at least one. If a longer buffering time is necessary, then the counter should be decremented by more. If the field has the value 0, then the packet has to be rejected, to keep a packet from wandering in the network forever. Protocol: This field includes the number of the transport protocol to which the packet should be forwarded. Numbering of protocols was defined in [RePo94] (e.g., TCP (6), UDP (17), IDMP(1), IGMP (2)). Checksum: This field includes the checksum over the fields of the IP packet header. The payload in the IP datagram is not checked, for efficiency reasons. In general, this check occurs within the transport protocol. The checksum has to be recomputed in each network node visited, because the IP header changes in each hop, in the TTL field. For this reason, it is important to use efficient checksums. A sender computers the 1's-complement sum of all 16-bit quantities in the header, excluding the checksum field itself, and then stores the 1's complement of the sum in the CHECKSUM field. A receiver computes the same 16-bit sum of values in the header, including the checksum field. If the checksum is correct, then the result is zero. Sender and destination addresses: These fields include the 32-bit Internet addresses of the sender and the receiver. Section 15.1.5 describes the address classes of the Internet Protocol. Option and padding fields: To keep the headers of datagrams small, IP defines a set of options that can be present, if needed. The header length is specified in 32-bit multiples; if options do not end on a 32-bit boundary, then PADDING that contains zero-bits is added to make the header a multiple of 32 bits. Section 14.3 describes all IP options.
14.1.3 Lifetime of an IP Data Packet Faulty functions in the network can cause packets to circulate in the network rather than arriving at their destination address. These data packets consume valuable resources in the network, so they have to be destroyed by control mechanisms at some point in time. The following method is used to destroy such packets: The TTL (Time To Live) field of the IP data header takes the number of routers (hops). This field is actually intended to specify the lifetime of a packet in seconds, but it is currently used to count the hops through the routers on the path. Each router reduces this value by 1, and the packet is rejected when the value 0 is reached. This prevents a packet that cannot be delivered from circulating forever. In addition, you can set a specific TTL value in the sender to limit the reach of a packet. 14.1.4 Addressing in the Internet Three different addresses are used to reach a communication partner or an application in the Internet. These addresses identify a unique communication endpoint within the Internet and are often called sockets: The IP address specifies a unique computer in the Internet. Each computer in an IP network has to have a unique Internet address. Section 14.1.5 explains the structure of this address format and the set of different classes. The transport protocol ID specifies the transport protocol instance used (i.e., TCP, UDP, ICMP, etc.). The Internet Protocol uses this identifier to know which transport protocol is used. The port number identifies a unique and specific application within the TCP and UDP transport protocols (multiplexing).
The following section discusses the first part of the sockets defined above, IP addresses and their structure. The chapters dealing with the transport layer introduce and describe the TCP and UDP protocols, which are the most important transport protocols today. These chapters also explain the meaning of port numbers. 14.1.5 IP Addresses and IP Address Classes Each network device in the Internet or in other IP-based networks has its own unique IP address. Computers connected to several networks concurrently (multihomed hosts) have a separate address for each network connection. These addresses are assigned by the Internet Assigned Numbers Authority (IANA) and their national representatives (e.g., Reseau IP Europe RIPE). Notice that these addresses are not assigned on an individual basis, but in blocks by so-called network classes. If somebody needs an IP address to connect a computer to the Internet, then he or she will obtain a network address and an entire range of addresses. For this reason, each range of network addresses is managed within those addresses themselves. Accordingly, IP addresses are structured in a hierarchy: They are divided into a network part and a computer or host part. Figure 14-3 shows the classes and their different network and host parts. Figure 14-3. Address classes of the Internet Protocol. 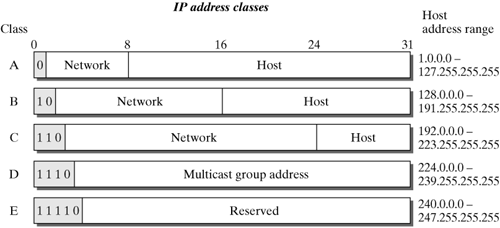
The network part identifies the network to which a station is connected. All computers within a network have the same network part. The computer part identifies a specified computer within a network. If a computer is connected to more than one network, then it has a separate IP address for each network. IP addresses are 32 bits long and are normally written in dotted decimal notation (e.g., 129.13.42.117). As was mentioned earlier, IP addresses are divided into several classes. The prefix of an IP address specifies the address class. The five classes of IP addresses are as follows: Class A: The first bit of the address is zero (i.e., the first byte is smaller than 128). The first byte is the network number, and the last three bytes identify a computer in the network. Accordingly, there are 126 class-A networks, which can manage up to 16 million computers in one network. Class B: A value between 128 and 191 for the first byte (i.e., the first two bits are 10) identifies a class-B address. The first two bytes specify the network, and the last two bytes specify a computer in this network. This results in 16,382 class-B networks with up to 64,534 computers in any one network. Class C: This class uses values between 192 and 223 for the first byte (the first three bits have a value of 110). There are approximately two million class-C networks; the first three bytes are used for the network address and the last for up to 254 computers. Class D: Class-D addresses have a special meaning. They identify a group of computers that can be in different networks, rather than identifying a single computer or network adapter. Class-D addresses are also called multicast addresses. The first byte in a multicast address has a value in the range from 224 to 239; the first four bits are to 1110. When an application sends an IP packet to a class-D address, then the message is broadcast to all members of the addressed group. A special protocol, the Internet Group Management Protocol (IGMP), is used to manage such groups. Chapter 17 discusses IP multicast and IGMP. Class E: this last range of IP addresses, ranging from 240 to 254 in the first byte, is reserved for future use.
As mentioned earlier, IP addresses have to be unique within the Internet. For this reason, all network addresses are assigned by a central organization to ensure that all addresses are unique and visible in the Internet. However, this is not always required. Networks that do not connect to the global Internet do not need an address that is visible in the Internet. Also, it is not necessary that these addresses not be used in another private network. For this reason, address ranges were defined especially for private networks. These ranges are defined in RFC 1918. IP packets with private addresses may not be forwarded in the Internet. This means that private IP addresses can be used in an arbitrary number of nonpublic networks. The following address ranges are reserved for use in private networks: The range from 10.0.0.0 to 10.255.255.254 was reserved in class A for private class-A networks. The range from 172.16.0.0 to 172.31.0.0 was reserved in class B for private class-B networks. This means that 16 class-B network are reserved for private use. Each of these networks can connect up to 65,534 computers. The range from 192.168.0.0 to 192.168.255.0, a total of 256 networks, was reserved in class C for private use. Each of these networks can connect up to 254 computers. In addition, there are other reserved IP addresses with special meanings: The class-A network address 127 represents the loopback network device of a computer. IP packets to an address in the form 127.x.y.z are not output to a network adapter; they are processed locally. In addition to network addresses, computer addresses are also reserved for special use. The values 0 and 255 in computer addresses are reserved in all network classes. An IP address with all bits of the computer part set to zero identifies the network itself. For example, the address 80.0.0.0 refers to the class-A network 80, and the address 128.66.0.0 refers to the class-B network 128.66. An IP address where the computer part consists of 1-bits defines a broadcast address, which can be used to address all computers in a network.
|