7.2 Bluetooth Basics
| < Day Day Up > |
| Bluetooth Special Interest Group (SIG), a consortium of telecommunications, electronics, and computer manufacturers, develops Bluetooth. The founding members were Ericsson, Nokia, IBM, Intel, and Toshiba. The first version of the Bluetooth specification was formally adopted by the SIG in 1999. The first revisions of the Bluetooth specification had a mixed reception , because implementations were dogged by interoperability problems. The 1.1 release, published in 2001, eliminated the gray areas from the 1.0b specification and, as a result, improved device interoperability. Over two years since the 1.1 release, Bluetooth is well on its way to becoming a ubiquitous technology in portable devices. At the time of writing, the current approved revision of the Bluetooth specification is Version 1.2, released in November 2003. The Bluetooth specification itself covers the many levels involved in getting a signal between two applications, from the radio through link control to application-level protocols. Figure 7-1 shows just some of the various strata specified by Bluetooth, which we encounter in this chapter. Further details, including the specifications themselves , can be obtained from http://www.bluetooth.org. Figure 7-1. Some layers of the Bluetooth specification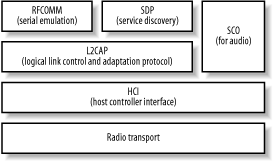 Bluetooth hardware typically takes the form of one or two microchips, which are embedded in devices. Computers are increasingly shipping with integrated Bluetooth adapters, but the prevailing way of adding Bluetooth support is by adding an external adapter, typically via the USB or PC card ports. Before a device can sport the Bluetooth logo and use the Bluetooth trademarks, it must be put through a series of tests known as qualification . Qualification involves tests for all parts of the Bluetooth specification, from radio testing to protocol conformance. 7.2.1 What You Can Do with BluetoothAs Bluetooth is intended to replace cable, it can be used for more or less the same purposes as a cable, within the bandwidth constraints of the technology. All the following usage scenarios are supported within Linux and are discussed in this chapter:
7.2.2 ConceptsThe following sections describe essential Bluetooth concepts that you need to be aware of. These include the Bluetooth address, which uniquely identifies a Bluetooth adapter; the protocols and profiles that define the communication techniques and device capabilities; bonding, discoverability, and device classes, which Bluetooth devices use to find each other and communicate their abilities ; and piconets, scatternets, masters, and slaves, which describe the topology of Bluetooth networks and the relationships of one device to another. 7.2.2.1 Bluetooth addressEach Bluetooth interface has a Bluetooth address , also known as its BDADDR . These addresses look very much like Ethernet interface MAC addresses, and follow the same address allotments that the ANSI/IEEE 802 standard, administered by the IEEE, has laid down. The first three octets of the Bluetooth address denote the organizationally unique identifier (OUI). For instance, the address 00:80:98:23:15:6E has an OUI of 008098, which is registered to the TDK Corporation.
In addition, Bluetooth adapters have a programmable name used to present to the user in interactions. Example 7-2 shows both the Bluetooth addresses and the names that are discovered in a device scan. 7.2.2.2 ProtocolsThe Bluetooth specification defines some protocols of its own and also reuses some existing standards. A protocol is an agreement about the way data is exchanged. It is on top of these protocols that all applications of Bluetooth are built. An in-depth knowledge of the protocols is not necessary to deploy Bluetooth, but passing familiarity with them helps in troubleshooting situations. Confusingly, some of the protocols have very similar names to the profiles in which they are used and are listed next . (Additionally, some protocols are layered on top of lower-level protocols. This happens elsewhere in computing ”for example, when a computer connects to the Internet via a modem, it uses the RS232 protocol to communicate serial port data, the PPP protocol on top of that to facilitate a network connection, and TCP/IP on top of that to carry the data.)
7.2.2.3 ProfilesA profile is the name given to the implementation of one more protocols to provide a particular application service. Bluetooth devices advertise profiles. Many of the profiles build on each other ”for instance, the OBEX profile builds on the serial port profile. Commonly implemented profiles include:
7.2.2.4 BondingBonding, also called pairing , is the process by which trust is established between two Bluetooth devices. The user is required to input matching codes, called personal identification numbers (PINs), into the two devices. In some situations, one of the devices may have the PIN pre-set ”for example, some headsets come with a PIN of 0000. PINs are typically a sequence of digits; they provide little security, and they are intended only for the initial pairing. Given a successful match of PIN, the devices negotiate a link key , a much more cryptographically secure code, which is used thereafter as an access control mechanism between the two devices. 7.2.2.5 DiscoverabilityA Bluetooth device is discoverable if it can be found by another device's inquiry. During discovery, the inquiring device broadcasts a specially coded message. As remote devices receive the message, they send a return message indicating their presence. In most circumstances, you must make a device discoverable in order to initiate bonding.
7.2.2.6 Device classesBluetooth devices fulfill many functions, so there should be a way that a device can quickly indicate its primary function. As we have already mentioned, the SDP exists to provide a complete description of running services. However, Bluetooth provides an additional way for a device to describe itself: the device class . Although the SDP provides the description of the running services, the device class provides the purpose of them. The device class code is a 24-bit number that incorporates three subcodes: the major device type, the minor device type, and additional service codes, which broadly indicate the services available. Table 7-1 shows the meaning of the useful major device types (other types are reserved or undefined), and Table 7-2 shows the useful service class bits. The meaning of the minor device type bits (bits 7-0) depends on the major device type. You can find a full explanation of these values on the Bluetooth Special Interest Group web site at http://www.bluetoothsig.org/assigned-numbers/baseband.htm. Table 7-1. Major device types as expressed in the device class
Table 7-2. Service classes as expressed in the device class
7.2.2.7 Piconets and scatternets, and masters and slavesA piconet is a network of Bluetooth devices created by a master connecting to one or more slaves. The master is the device that initiates the connection. Figure 7-2 shows the topology of a piconet. A master may be connected to as many as seven slaves simultaneously . Figure 7-2. Topology of a piconet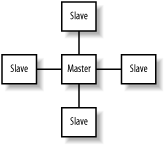 Various applications such as LAN access points require the master/slave relationship to be the same as the server/client relationship. For this reason, a client device, which serves as a master, initiates a connection to the access point; once connected, a role-switch occurs, and the client device now becomes a slave. For most applications of Bluetooth on Linux, you do not need to be aware of these distinctions, but the knowledge of their existence may be useful in debugging scenarios. Some Bluetooth hardware has restricted role-switching ability. Sometimes, a slave in one piconet is connected to a master of another piconet. The linking together of multiple piconets in this way is called a scatternet . |
| < Day Day Up > |
EAN: 2147483647
Pages: 100
