Detection Software
The detection software presented in this section is fully detailed in Appendix A, “Freeware.” The detail provided here is specific to rootkit detection. For more information about these applications, and the rest of the software mentioned in this book, refer to Appendix A.
Strider GhostBuster
This detector employs the following:
-
File list comparisons
-
Registry key comparisons
-
Process list comparisons
-
INT 2E comparisons
GhostBuster is a pretty good rootkit detector. More important, it is a Microsoft Rootkit Detector. Expect this software to expand rapidly as Microsoft’s best minds add their combined knowledge to the task of rootkit detection. Once the software is widely distributed, the combination of rapid detector development and regularly scheduled updates will make GhostBuster the standard for rootkit detection. If you’re developing a new rootkit intended for distribution to the general public, you will soon need to test it against GhostBuster before considering any form of large-scale deployment.
Strider GhostBuster is currently a research project and not available to the general public.
RootkitRevealer
The web address for this product is www.sysinternals.com/utilities/rootkitrevealer.html.
This detector employs the following:
-
File list comparisons
-
Registry key comparisons
-
Alternate data stream detection
RootkitRevealer does a good job of detecting older rootkits, but looking for hidden files, hidden registry entries, and alternate data streams won’t help if rootkits aren’t using these techniques. This, combined with the recent acquisition of Sysinternals by Microsoft, puts RootkitRevealer on the short list for planned obsolescence. Rootkit Revealer is shown in Figure 13-2.
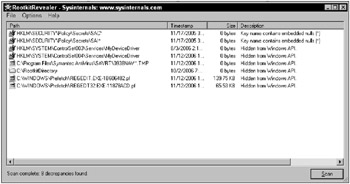
Figure 13-2
Figure 13-2 shows Rootkit Revealer after scanning a machine running the rootkit developed in Chapter 9 of this book. The scan begins with two false positives. False positives are false indications of a rootkit. In this case, special access registry keys are flagged as possible indications of a rootkit, though they can only be viewed from the local system account. These false positives are followed by clear indications that our rootkit is hiding a registry key. Unfortunately, the clear indication is followed by a false positive caused by anti-virus software, which blurs the authenticity of the otherwise clear indication. Then, another clear indication of our rootkit is presented by showing our hidden directory. This is followed by more false positives, caused by using the registry editor during the security scan.
F-Secure Blacklight
The web address for this product is www.f-secure.com/blacklight.
This detector employs the following:
-
File list comparisons
-
Directory list comparisons
-
Process list comparisons
BlackLight has the advantage of being very user friendly. After downloading, the user can perform a full scan with the press of a single button. Hidden files, hidden directories, and hidden processes are revealed without the need to scan from a known good environment. BlackLight will not detect all forms of process hiding, and newer rootkits might not employ file or directory hiding techniques, so don’t expect to find any of the newer rootkits with this detector. F-Secure BlackLight is shown in Figure 13-3.
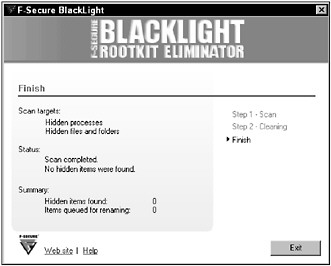
Figure 13-3
Figure 13-3 shows F-Secure BlackLight after scanning a machine running the rootkit developed in Chapter 9 of this book. The scan completed without finding any indication of a rootkit. This is more a reflection of the test environment than the tested software, as our hidden directory has no files in it and the HideMe application was not running, so no processes were being hidden at the time of the scan. Nonetheless, it does help to show how easily some rootkit detectors can be thwarted by simple obfuscation in lieu of intricate hiding techniques.
RootKit Hook Analyzer
The web address for this product is www.resplendence.com/hookanalyzer.
This detector employs the following:
-
System call table comparisons
Rootkit Hook Analyzer is an easy-to-use rootkit detector that validates kernel system call table entries. A rootkit that uses kernel hooking would need to hook ZwFileOpen (for ntoskrnl.exe) and ZwQuerySystemInformation (for SystemModuleInformation) to misdirect Rootkit Hook Analyzer. Because these hooks are a prerequisite to advanced kernel hooking rootkits, Rootkit Hook Analyzer might not provide enough coverage to detect rootkits specifically designed to hide kernel hooking.
Rootkit Hook Analyzer is also a great tool for testing the implementation of a kernel hooking rootkit. If a kernel hooking rootkit cannot be detected by Rootkit Hook Analyzer, there is a high probability that the rootkit will remain undetected for a long time. Figure 13-4 shows a Rootkit Hook Analyzer.
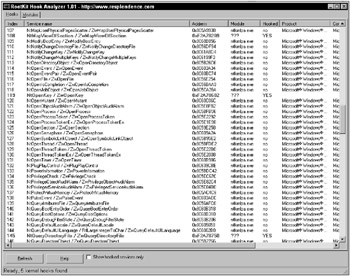
Figure 13-4
The figure shows Rootkit Hook Analyzer after scanning a machine running the rootkit developed in Chapter 9 of this book. The scan clearly shows each of the kernel system call table hooks implemented by our rootkit. Unfortunately, the detector cannot distinguish the source of the hooks, leaving the operator without the information required to validate and correct the problem. If the operator knows a little about Windows system internals, ZwEnumerateKey, ZwOpenKey, and ZwQueryKey hooks will indicate a rootkit, but if the operator knows a little more, then he or she may realize that these are also the hooks used to virtualize the registry in some host-based intrusion prevention software systems. Without any indication which software implemented the hook, it would be difficult to proceed.
IceSword
IceSword is available from the Wiley rootkit website.
This detector employs the following:
-
File list comparisons
-
Registry entry comparisons
-
Process list comparisons
-
System call table comparisons
IceSword is a rootkit detector for experts. It can also detect spyware, anti-virus software, browser toolbars, and other software unrelated to rootkits. Learning how to use IceSword, and how to recognize the difference between expected and abnormal test results, will take some time, but if you’re willing to make the investment, IceSword can be a very useful tool. Unfortunately, as a personal rootkit detector, IceSword is severely limited by its complexity. Figure 13-5 shows an IceSword Hidden Directory detection. Figure 13-6 shows an IceSword Kernel Hook detection. Figure 13-7 shows an IceSword Kernel Module list. Figure 13-8 shows an IceSword Hidden Registry Key detection. Figure 13-9 shows an IceSword Communication Port detection.
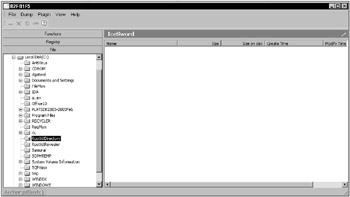
Figure 13-5
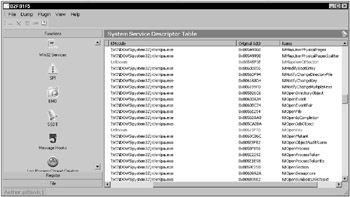
Figure 13-6
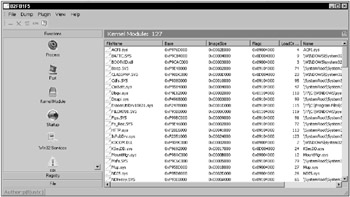
Figure 13-7
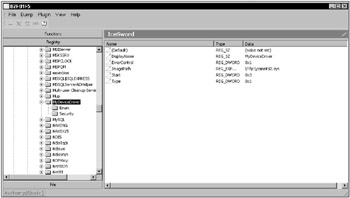
Figure 13-8
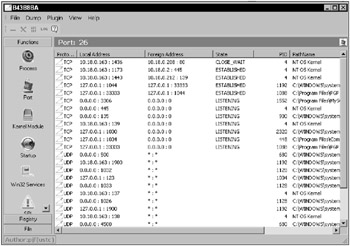
Figure 13-9
Like Rootkit Hook Analyzer, kernel hooks are clearly displayed but contain no indication of how they were installed. The hidden directory and hidden registry key would normally provide the cause of the kernel hooks. Unfortunately, IceSword does not highlight or otherwise call attention to these as anomalies. Without some indication that the directory and registry key are hidden from conventional software, IceSword requires the user to somehow know that the displayed directory and registry key do not appear in conventional listings. In addition, the TDI communication port and the device driver entry are successfully hidden from IceSword. Combined, the conflicting data does not present a clear indication to the average user.
Sophos Anti-Rootkit
The web address for this product is www.sophos.com/products/free-tools/sophos-anti-rootkit.html.
This detector employs the following:
-
File list comparisons
-
Registry entry comparisons
-
Process list comparisons
Like BlackLight, Sophos is very user friendly. After downloading, the user can perform a full scan with the press of a single button. Hidden files, hidden registry entries, and hidden processes are revealed without the need to scan from a known good environment. Also like BlackLight, Sophos will not detect all forms of process hiding, so don’t expect to find any of the newer rootkits with this detector. Figure 13-10 shows a Sophos Anti-Rootkit window.
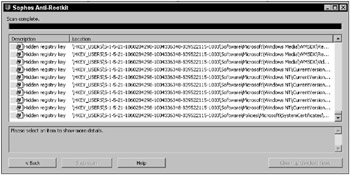
Figure 13-10
This figure shows Sophos Anti-Rootkit after scanning a machine running the rootkit developed in Chapter 9 of this book. The scan contained 4,003 suspect registry keys. Under these circumstances, it really doesn’t matter if our hidden registry key was in the list. Detected or not, our hidden registry key is completely hidden in the sea of false positives presented by Sophos version 1.1.
EAN: 2147483647
Pages: 229