URI Filtering Protocol
A Uniform Resource Identifier most commonly defines how to access resources on the Internet. URI Filtering Protocol is used to enable passing data between VPN-1/FW-1 and a third-party server for URI classification.
The most common example of UFP is to pass HTTP Uniform Resource Locators (URLs) to a server running Websense, SurfControl, or a similar product, to check that the requested URL is allowed by your organization s acceptable Internet usage policy. Since the term URI (described in RFC 1630) and URL (RFC 1738) essentially deal with the same thing ( especially when discussing HTTP), it is common to see the terms interchanged. Which term you use (URL or URI) is more a matter of preference than being technically correct, as there seems to even be disagreement between the industry standards organizations as to which is correct in which circumstances.
| |
Load Balancing Chained Servers
CVP chaining enables you to tie servers with different functions together to apply multiple levels of control to a single data stream. For example, you may chain an antivirus and content filtering server together to inspect and clean files downloaded by your users. Load sharing enables you to spread the work to be done across multiple servers for efficiency and redundancy, but what happens if you want to do both?
You cannot apply load balancing to chained servers since load balancing must be done between two or more servers with similar functions, and a chain contains multiple servers all doing different functions. You can, however, chain multiple load balanced servers, enabling you to achieve a similar effect.
Consider that you have two antivirus servers and two content filtering servers that you want to load balance and chain. To do this, you first must create two URI groups that use load sharing, one for the antivirus servers, and one for the content filters. Then all you need to do is create a third URI group that chains the first two groups together. This provides load sharing between similar servers and enables you to chain the servers together.
| |
Defining Objects
Creating a UFP server object is almost identical to creating a CVP object. Both objects require that you define a workstation object with at least a name and IP address for the server and that you use that workstation in the OPSEC application object. Figure 7.7 shows the General tab of the UFP server object, which enables you to define the application you are using. You can choose from the predefined list, which includes vendors such as WebSense, Symantec, SurfControl, Secure Computing, and 8e6_Technologies, or you can use the User Defined option to customize your UFP server object. A complete list of UFP applications from OPSEC-certified vendors is available atwww.opsec.com/solutions/sec_content_security.html.
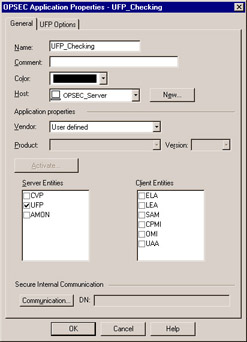
Figure 7.7: UFP Server Object ”General Tab
The difference in setting up a CVP server compared to a UFP server starts when you select UFP (as seen in Figure 7.7) in the Server Entities section of the OPSEC Application Properties window, which makes the UFP Options tab (Figure 7.8) available.
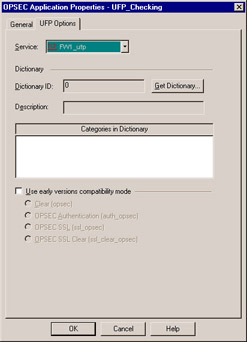
Figure 7.8: UFP Server Object ”UFP Options Tab
The Service drop-down menu defines which port the UFP service will be listening on; for most UFP applications, this is set to FW1_ufp (TCP port 18182). The backward compatibility options for UFP servers are the same as for the CVP server you looked at earlier, enabling you to configure options that, in previous versions of VPN-1/FireWall-1, were set in the now nonexistent fwopsec.conf file.
The Dictionary section of the UFP tab will show the category list from the UFP server. In order for the UFP server to function with VPN-1/FW-1, the servers Dictionary ID and category list are required. The dictionary is basically a list of categories and the dictionary ID is the version of the list. This is useful if you are using a dictionary that is updated often. Once you ve set up the server object on the General tab and set the service to match your UFP server, you can click the Get Dictionary button to retrieve the category list and ID number from the UFP server. The category list is displayed to help you verify that the connection to the UFP server is established and to show you which categories are available on that server. Note, however, that the categories in this window cannot be manipulated here. To select which categories you would like to filter incoming URLs against, you must create a URI resource that uses UFP.
Creating a URI Resource to Use UFP
Unlike a CVP server, which can be used with SMTP, TCP, FTP, and URI, a UFP server can only be used with URI resources. A URI is made up of two basic parts : a scheme or protocol, and a path . The scheme is the first portion of the URI, located to the left of the colon . Common schemes are HTTP, FTP, Trivial File Transfer Protocol (TFTP), Lightweight Data Access Protocol (LDAP), and so on, and can be thought of as a protocol identifier. The remainder of the URI specifies the path to the resource, and often has scheme-dependant syntax. Part of the path may contain a method, such as GET, POST, or PUT, which the UFP server may use to make filtering decisions.
Although the UFP server actually scans the URL and makes a control decision, it s the URI resource that tells VPN-1/FW-1 where and how to send the URI to be scanned. Figure 7.9 shows the URI Resource Properties window that is used to create the resource that will enable you to validate URLs through the UFP server created above.
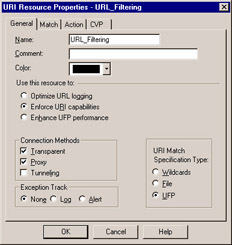
Figure 7.9: URI Resource Properties “General Tab
Aside from the generic object identifiers, there are some interesting URI resource options to select from. The first is the Use this resource to radio button set, which affects how the URI resource functions. If you select the first option, Optimize URL logging , all of the remaining options will gray out, and the object will only be used to log HTTP URLs into the VPN-1/FW-1 log. This option will not require the use of a security server to proxy the connection.
In order to use this resource as a conduit to an UFP server, you must select the Enforce URI capabilities or Enhance UFP performance option. The former utilizes the security server and provides extended options for filtering traffic, while the latter allows the firewall to retrieve the URL deep in the INSPECT engine (without the use of a security server), and to query the UFP server with the URL. Unfortunately, if you select the Enhance UFP performance option, UFP caching, CVP, certain HTTP header verifications, and authentication will not be available. For the rest of this section, we will use the Enforce URI capabilities option.
The Connection Methods section defines which modes VPN-1/FW-1 will use to examine traffic. If Tunneling mode is selected, you will not have access to the CVP tab and will not be able to use any URI filtering or UFP servers, since tunneling only allows the security server to inspect the port and IP address information, not the URI that you re interested in. Transparent mode is used when users browser configurations do not contain proxy server information. In this configuration, the firewall must be the network gateway that handles Internet traffic. As your users request resources from the Internet, the firewall will send the URIs to the UFP server to be checked as part of the security policy. In Proxy mode, the firewall must be specified in each user s browser as a proxy server. This configuration is very useful if you want to direct Internet service requests (such as FTP and HTTP) to a firewall that is not the default gateway for your network, as the security server will provide proxy services to Internet requests . Using the Proxy option also enables you to manually load balance your Internet traffic by directing users traffic to different firewalls, or to separate traffic based on type (for example FTP to one firewall, HTTP to another) if required.
The URI Match Specification Type section specifies how you want to inspect the URIs matched by this object. We ll be examining the File and Wildcards options later in the chapter, but for now we re only interested in the UFP option. Once you select the UFP option, then the Match tab, as seen in Figure 7.10, will provide you with additional UFP options needed to enable the UFP server.
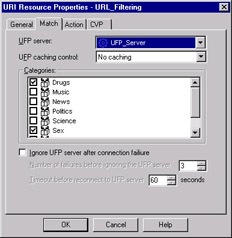
Figure 7.10: UFP Options for URI Resources
The Match tab enables you to select which UFP server to use, as well as to set operating parameters to control the interaction between the firewall security server and the filtering application. The UFP caching control field allows you to increase the performance of the URI resource by reducing the number of URLs sent to the UFP server. There are four caching options.
-
No Caching With caching disabled, the UFP server is used to check each URI. Typically, turning off the cache has a negative impact on performance, as every request must be checked by the UFP Server. However, this option is useful if your UFP server configuration changes frequently and you want to ensure that each request is filtered using the newest options. However, when using the Enhance UFP performance option, the overhead of a security server is removed, providing better performance than even a security server, which caches UFP requests.
-
UFP Server This option allows the UFP server to control the caching. The UFP server may choose to check each URL or it may maintain its own cache to speed up the checks.
-
VPN-1 & FireWall-1 (one request) The VPN-1/FW-1 security server controls UFP caching. Unique URIs will be sent to the UFP server only once before being added to the cache. This option provides the greatest performance by significantly reducing the number of URIs sent to the UFP server.
-
VPN-1 & FireWall-1 (two requests) URIs previously checked by the UFP server will be sent a second time before being added to the cache. Reduced performance is traded for the added security of checking each URL twice.
The Ignore UFP server after connection failure option controls how the security server will react if the UFP server is not available to service requests. Leaving this option unchecked can have a severe impact on performance if your UFP server fails, since the security server will attempt to send each URI to the failed server and will not allow traffic to pass until the server responds with an accept message. If this option is not enabled and your UFP server fails, then you most likely will experience a Denial of Service (DoS) condition, since even acceptable sites cannot be checked. The telltale sign of this condition will be messages in your logs that read, Unknown error while trying to connect to UFP, and users calling your help desk complaining of a lack of access. Enabling the Ignore UFP server after connection failure option enables you to specify the Number of failures before ignoring the UFP server option, which controls how many attempts are made before considering a UFP server offline. The Timeout before reconnect to UFP server value instructs VPN-1/FW-1 on how long to wait before considering the connection to the UFP server lost.
| Warning | The Ignore UFP server after connection failure option is not to be used lightly. By checking this box, if the UFP server fails, all access would still function without the added security the UFP server provides. This could be a circumvention of your overall security policy. Make sure to check what value the company ( specifically the Human Resources and Legal departments) places on Web access and the inspection capabilities UFP provides. Because Internet access impacts the ability of users to do work, it must be balanced against any relevant legal ramifications , which means this decision typically needs to made at an executive level by someone with the authority to decide if lost productivity takes a higher priority than content security. |
Finally, the CVP tab enables you to hand data off to a third-party server for validation. In addition to the antivirus example we looked at earlier, CVP servers like Symantec s Igear Web content scanner can provide you with fine- tuned content control for Web applications. Note that the CVP tab is not available if the Tunneling or Enhance UFP performance options are selected. The Action tab in the URI Resource Properties window is discussed later in this chapter.
Using the Resource in a Rule
Using a UFP server to validate URIs as part of your security policy is similar to using a CVP server in a resource rule. To follow the example used earlier, the UFP server can be used to scan URL requests to Internet sites. In doing so, the final step is to add the URI resource, which uses the UFP server object, as the resource in a new (or existing) rule. As with the CVP rule we created earlier, the only difference between a rule that uses a resource and a normal security policy rule is what is defined in the service column. Instead of selecting the Add option for the service, use the Add with Resource option to select the URI resource that contains the UFP server configuration you need. Figure 7.11 shows the final rule in the security policy being used to reject unacceptable data requests. Notice that the Service column shows both the scheme being used (HTTP) and the name of the URI resource (URL_Filtering).
As with CVP resources, it is necessary to remember that a match is made on the packet, not the session. For example, with UFP, you will typically create a drop or reject rule to match on the categories you want to disallow. As you can see in Figure 7.11, you must have another rule that will accept the traffic that you want to allow, or else it will be dropped on the cleanup or Drop All rule. This second rule is necessary because the resource rule only deals with dropping traffic, not with allowing it. You could, of course, use a UFP resource in the rule base to allow traffic based on category rather than drop it to get around this second rule requirement. The only problem with this approach is that the allowed list is often longer that the drop list, and is therefore is harder to maintain. The difference between drop and reject in these two cases is that drop will silently drop the packets, whereas reject will quickly tell the user that his connection is not allowed by returning an error or redirecting the user to another Website if defined in the Action tab. Reject is typically a more useful configuration because it will allow you (and your helpdesk) to distinguish between network connectivity problems and disallowed Websites.
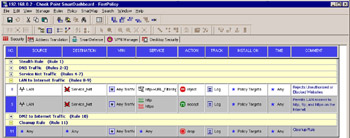
Figure 7.11: Security Policy Rule Using UFP Server in URI Resource
UFP Group
A UFP group is similar to a CVP group except that it does not support chaining. The configuration of a UFP group is similar to the other generic group configuration screens, in that you enter a name, comment, and select the appropriate color and then simply move UFP servers from the Not in group section to the In group section.
Your choices for load balancing between servers in a UFP group are either Random or Round Robin . Using Up and Down buttons will enable you to change the order in which servers are used in the round robin configuration, but since the server being used will change with each incoming session, changing the order will only slightly affect how the object performs . The final option, Load sharing suspend timeout , enables you to configure the time to ignore a failed server before attempting to reestablish communication with it. You can set this time to anywhere from 0 (ignore the failure, attempt to use server normally) to 10,000 minutes.