Usage Models
Usage Models
The architecture we just described is generic; myriad usage models would fit in to this architecture. The following usage models focus on the first part of the communication cycle, the device to the network or devices to other devices, but the models also serve as important illustrators of the capabilities in wireless devices.
Internet Bridge
The Internet bridge architecture best fits a usage model wherein a wireless network serves as a bridge between the wireless device and the wired Internet. In this model, the mobile device is used to wirelessly connect to a wired system (refer to Figure 1.1).
Conference
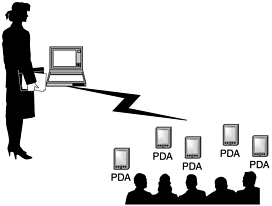
Users at a conference often want to share information. In a keynote session, for example, a presenter may want to share her slides with the audience members who come up afterwards to pose questions (see Figure 1.2). If the audience members and presenter have wireless devices, they can exchange documents and business cards immediately.
Figure 1.2. The conference usage model
Multipurpose Phone
A cell phone is used in place of a landline at home, connected to a fixed line. When its owner is on the go, the phone is used as a mobile device for initiating and receiving calls. When the same phone is close to another, similar phone, they can participate in two-way communication and avoid a phone service charge, provided that they obtain service from the same provider.
Synchronizer
Mobile devices can automatically synchronize among one another to provide an easy way to stay organized. A user's desktop, PDA, wireless-enabled laptop, and cell phone can be synchronized as soon as information is entered into any of them. A laptop can be automatically updated when information is received in a cell phone, just as a PDA can propagate its new business card contact information to the other devices.
Now we will examine in more detail the important components of a wireless architecture: devices and technologies. The security implications of each will be discussed still further throughout the text, as well as how to avoid the risks associated with each component.
EAN: 2147483647
Pages: 73