An Introduction to Wireless Architecture
An Introduction to Wireless Architecture
The basic components of a wireless architecture remain the same throughout different systems. Each implementation and technology, of course, sees variations and different options, but by way of introduction, they resemble one another. The architecture we use to represent a generic framework depicts wireless devices retrieving information from a server on the wired Internet by way of its own communication across a wireless network (see Figure 1.1). Other implementations and purposes for wireless communication are discussed throughout the book.
Figure 1.1. A generic system architecture
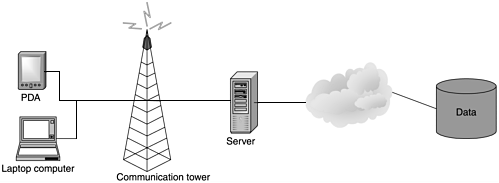
The first component on our diagram is the device. Devices in a wireless system can be cell phones, Personal Digital Assistants (PDAs), laptops with wireless network cards, or any device that communicates without wires. These devices operate over wireless networks and communicate with towers called bearers. These bearers have popped up alongside highways across the world. Unlike the telephone or radio towers of old, bearers are not connected by aboveground wires visible from the road. Bearers are in charge of passing information sent wirelessly to a wired network. They receive data and transmit it to a component that forwards it via wires to the wired Internet. This component is sometimes a wireless gateway and other times another specialized server designed to be the pivot point between wireless and wired communication. A gateway performs translations among protocols, sessions, encryption, and all else necessary to prepare wireless data for transmission over the wired Internet to its destination.
In our architecture diagram, we will examine one typical scenario the wireless device requesting information from a Web page on a Web server. The gateway, in this situation, translates the request into one that is readable by the Internet and sends it to the appropriate server. The server processes the request and returns the information to the gateway via the wired Internet. At this point, the wireless gateway performs the necessary transformations again and transmits the data to a bearer, which, in turn, forwards it to the device. The device renders the information on its display screen, and an iteration of this communication cycle is complete. Wireless technologies are generally the final link between an existing wired network, its resources, and new-generation wireless devices.
EAN: 2147483647
Pages: 73
- Using SQL Data Definition Language (DDL) to Create Data Tables and Other Database Objects
- Understanding SQL Transactions and Transaction Logs
- Using Keys and Constraints to Maintain Database Integrity
- Working with SQL JOIN Statements and Other Multiple-table Queries
- Writing Advanced Queries and Subqueries