Lesson 1: Securing Public Web Servers
Lesson 1: Securing Public Web Servers
Windows 2000 Server includes IIS and a management console that allows you to control the IIS settings, including its security options. This lesson covers the basics of security for Windows 2000 Web servers.
After this lesson, you will be able to
-
Understand IIS and its security features
-
Configure basic IIS security settings
-
Restrict connections by IP address or domain name
Estimated lesson time: 10 minutes
Understanding Internet Information Services
Microsoft Internet Information Services (IIS) is a full-featured Web server that you use to publish Internet or intranet Web pages. IIS 5.0 is included with Windows 2000 Server. A single installation of IIS can manage multiple Web sites. IIS supports a variety of security features, including user authentication and SSL encryption.
IIS security does not replace other security features it enhances them. Make sure you use the security features specific to IIS in addition to the other security features of Windows 2000, such as IP filtering and NTFS file system security.
IIS serves Web documents using HTTP and the secure HTTPS version. In addition, it supports FTP, SMTP, and NNTP.
When IIS is installed on a server, it includes an online copy of the IIS documentation. You can access this documentation with the URL http://localhost/iisHelp on the IIS computer.
Implementing IIS Security
Security for IIS Web sites can be managed separately for the following:
-
Globally for all Web sites and directories on the server
-
Per Web site
-
Per virtual directory
To manage security at these different levels, right-click the server, the Web site, or the virtual directory that you want to configure, click Properties, and then click the Directory Security tab in the Properties dialog box. All three levels present the same set of security options.
IIS Web servers provide Web sites in three primary security contexts:
-
Intranets are private Web sites that operate inside private networks.
-
Extranets are Web sites that connect a specific group of users from multiple organizations.
-
Internet Web sites provide Web pages to anonymous users from the public.
Each security context has dramatically different security requirements, and IIS is designed to handle all of them. However, not all security features are appropriate for every security context. For example, authenticated access is not designed for public use because you can't create a user account for every member of the public.
Establishing Security Settings
The security settings in IIS are designed primarily to protect IIS services in intranets and extranets. You must use a strong security proxy such as Microsoft Internet Security and Acceleration (ISA) Server to protect public Web servers, and your security restrictions for public servers should be implemented on the proxy server rather than on the IIS server. You also must use NTFS permissions to restrict access to critical files on public Web servers.
For each Web site, the security settings in IIS allow you to choose one of the following types of authentication:
-
Anonymous access for the Internet or when authentication is not necessary
-
Basic authentication for extranets that serve clients other than Windows computers when you can't use digest authentication or certificate mapping
-
Integrated Windows authentication for intranets where users will be using Microsoft Windows computers with Internet Explorer
-
Digest authentication for extranets where you can't deploy certificates to all users and all browsers support digest authentication
-
Certificate mapping for extranet use when you can deploy certificates to all users
Managing Directory Security Properties
To access most of the security properties for a Web site, select a Web site in the Internet Information Services management console, choose Properties from the Action menu, and click the Directory Security tab in the Properties dialog box that appears. You'll find these security options on the Directory Security tab:
-
Allow anonymous access and control authentication methods
-
Restrict access based on domain name or IP address
-
Manage Web server and client certificate settings
The properties for a folder or virtual directory also include a Directory Security tab. For purposes of security, you can think of a virtual directory as a "Web site within a Web site" it's a collection of Web content that has its own security settings. Virtual directories also allow you to store Web site files anywhere you want and make them appear to be within the directory structure of your Web site. You can use virtual directories to enable security features for a section of a site if the main portion of the site allows anonymous access.
Using IP Address and Domain Name Restrictions
To prevent access to a Web site from specific computers or to make a private Web site available only to specific machines, you can grant or deny access in IIS to a Web site based on the IP address or domain name of the user.
Restricting access by domain name requires a reverse Domain Name System (DNS) lookup for each page access. This can slow down the server and is not recommended in most cases.
To manage these settings, click the Edit button within the IP Address And Domain Name Restriction area of the Directory Security tab in the Properties dialog box. You can choose to either grant or deny access to the server by default and then add a list of exceptions to this rule. For each exception, you can specify a single IP address, a range of addresses, or a domain name.
Restricting access to Web sites using IIS is not as secure as restricting access using Windows IP filtering in the TCP/IP configuration properties, ISA Server, or a dedicated firewall. Before using IIS to restrict access to a site, ensure that you want to restrict only Web protocols. In most cases, you are better off restricting all TCP/IP protocols using IP filtering or your firewall.
Keeping IIS Secure
Hackers target IIS because it is the most public of all services provided by Windows 2000. For this reason, more bug exploit attacks are perpetrated against IIS than any other service. Servers that run IIS should not be considered secure, regardless of the IIS security settings described here.
Make all of your security decisions for Web servers with the understanding that all public Web servers are subjected to an extraordinary amount of hacking activity. Data you can't afford to lose should never be stored on public Web servers. Never activate IIS on servers that don't require it to function unless those servers are protected from the Internet by a strong firewall.
Carefully consider the security ramifications of hosting multiple Web sites on a single Web server. Do not put secure Web sites on public Web servers and rely on Web authentication for security, because hackers who gain access to the public server will have access to the secure site on the same public Web server. Hosting multiple Web sites on a single server is a convenience feature, not a security feature. Keep Internet sites on public Web servers and intranet sites on private servers. Use certificate mapping (see Lesson 3) for extranet servers.
Maintaining IIS security is an ongoing process. When using IIS as a public Web server:
-
Use the most secure authentication, and use SSL certificates for critical transactions. Secure authentication is described in Lesson 2 of this chapter; SSL certificates are described in Lesson 3.
-
Turn off non-Web services such as FTP and SMTP that you are not currently using. (Select the service from the Internet Information Services management console and, from the Action menu, choose Stop to stop a service, or Delete to remove it entirely.)
-
Keep IIS updated with the latest security patches, and implement a policy to ensure regular updates. See Chapter 14, "Software Maintenance," for information about automatic update services.

In this practice, you configure basic security properties for IIS. To complete this practice, you need a Windows 2000 Server computer with IIS installed. If your server was upgraded from an earlier version of Windows, you might need to install IIS using Add/Remove Programs in Control Panel.
Exercise 1: Configuring IIS Security Options
In this exercise, you configure basic IIS security options, including setting up IP address restrictions for a private Web site.
To configure IP address and domain name restrictions
-
Log on as the administrator.
-
From the Administrative Tools menu, select Internet Services Manager. The Internet Information Services management console appears, as shown in Figure 12.1.
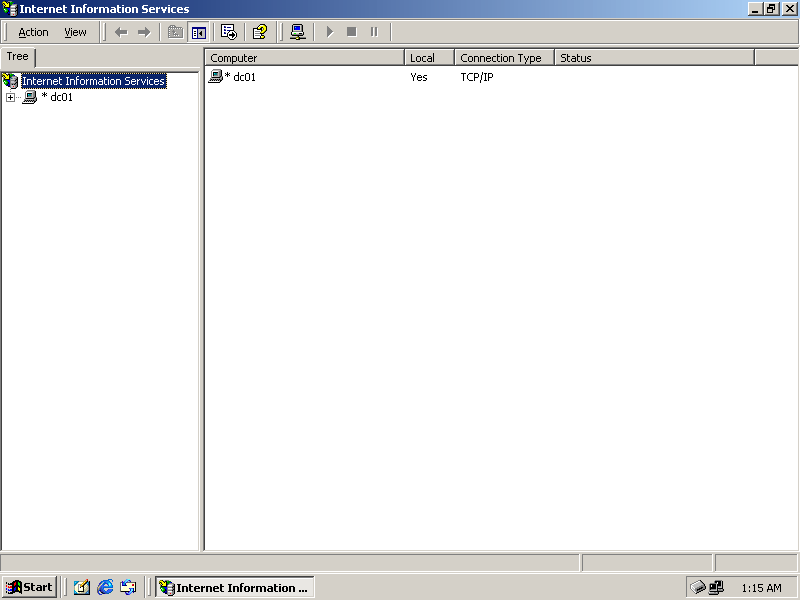
Figure 12-1. The Internet Information Services management console
-
Expand DC01 and select Default Web Site in the console tree.
-
From the Action menu, choose Properties. The Default Web Site Properties dialog box is displayed, as shown in Figure 12.2.
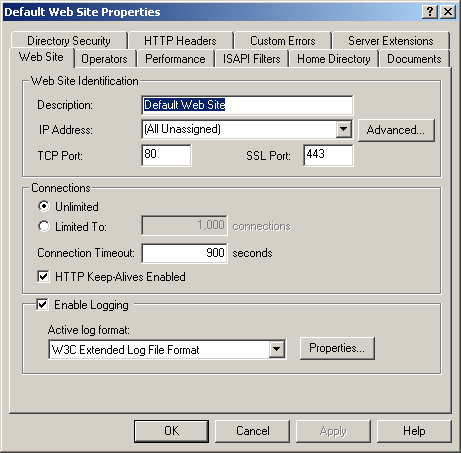
Figure 12-2. Default Web Site Properties
-
Select the Directory Security tab. The Directory Security properties are displayed, as shown in Figure 12.3.
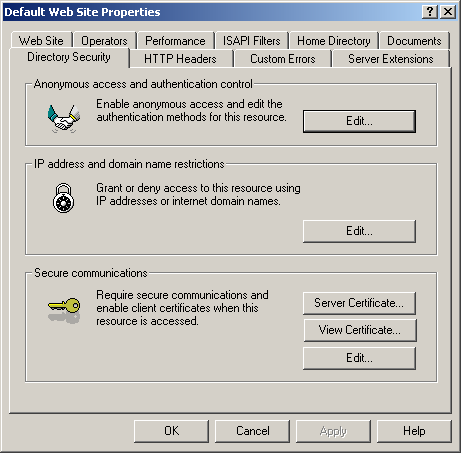
Figure 12-3. Web site directory security properties
-
In the IP Address And Domain Name Restrictions area, click Edit. The IP Address And Domain Name Restrictions dialog box is displayed, as shown in Figure 12.4.
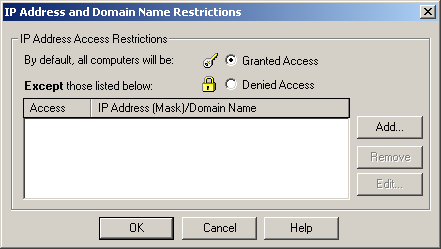
Figure 12-4. IP Address And Domain Name Restrictions dialog box
-
Select the Denied Access option.
-
Click Add to add an IP address range. The Grant Access On dialog box is displayed, as shown in Figure 12.5.
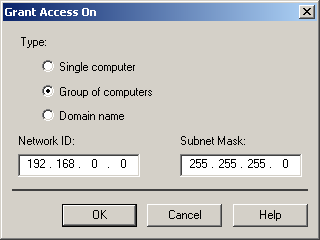
Figure 12-5. Granting access to an IP address range
-
Select the Group Of Computers option.
-
Type 192.168.0.0 in the Network ID box, and 255.255.255.0 in the Subnet Mask box.
-
Click OK. The range you entered is now included in the list in the IP Address And Domain Name Restrictions dialog box.
-
Click OK, and then click OK in the Properties dialog box.
The Web server is now limited to access from computers in the 192.168.0 address range.

The following questions are intended to reinforce key information in this lesson. If you are unable to answer a question, review the lesson and try the question again. Answers to the questions can be found in the appendix.
-
What component provides Web services in Windows 2000 Server?
-
What type of authentication is normally used for public Internet Web sites?
-
Which tab in the Properties dialog box for a Web site includes most security options?
-
What additional mechanisms should you use to enhance security besides IIS service-specific security options?
-
Which services can IIS provide along with HTTP?
Lesson Summary
-
Internet Information Services (IIS) is included with Windows 2000 Server and provides Web services as well as basic support for FTP and other network services. IIS can support any number of Web sites using the HTTP and HTTPS (secure HTTP) protocols.
-
You manage IIS using the settings in the Internet Information Services management console, available from the Administrative Tools menu. This console lists Web sites and other services and allows you to manage their properties.
-
The Directory Security property page for a Web site provides options with which you can manage most of the security aspects of IIS. This includes authentication methods, IP address and domain name restrictions, and certificate options.
-
The IP address and domain restrictions settings provide simple IP-based security for IIS. You can configure these settings to either grant or deny access by default, and you can add as exceptions to the default rule one or more IP addresses, address ranges, or domain names.
EAN: 2147483647
Pages: 82