Reviewing and Setting Rights
Another item in the Administrative Tools folder, Local Security Policy, lets you specify password and lockout policies for all users on a computer and assign rights to users and groups. You must be logged on as a member of the Administrators group to use Local Security Policy.
To get to Local Security Policy, open the Start menu and choose Settings, Control Panel, Administrative Tools, Local Security Policy. This opens a Microsoft Management Console window with Security Settings at its root, as shown in Figure 27-5.
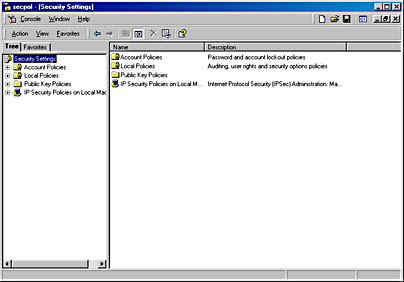
Figure 27-5. Choosing Local Security Policy opens the Security Settings tool in Microsoft Management Console.
Setting Password and Lockout Policies
Under Account Policies, you can set a variety of parameters that control password and lockout behavior for all local accounts. As shown in Figure 27-6, the right pane lists each of the policies for the item selected in the left pane. The second column in the right pane shows the local setting for each policy, which you can set by double-clicking a policy name. The third column, titled Effective Setting, shows the actual policy setting in force. This might be different from the local setting because a domain-level policy (set by an administrator on the domain controller) takes precedence over a local policy setting.
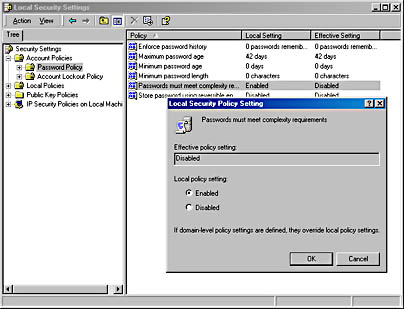
Figure 27-6. Double-clicking a policy opens a Local Security Policy Setting dialog box that explains the policy and lets you set the local policy.
Password policies place restrictions on the types of passwords users can provide, and how often they can (or must) change them. Account lockout policies govern the behavior of Windows 2000 in the event that a user types the wrong password. Table 27-1 explains the most commonly used settings under Account Policies.
Table 27-1. Commonly Used Account Policies
| Policy | Description |
|---|---|
| Password Policy | |
| Enforce password history | When a password expires, many users avoid the hassle of remembering a new password by submitting a previous password. Alternating between two passwords, thereby reusing the same passwords, compromises security. Specifying a number greater than 0 causes Windows 2000 to remember that number of previous passwords and forces users to pick a different password than any of the remembered ones. |
| Maximum password age | Specifying a number greater than 0 (the maximum is 999) dictates how long a password remains valid before it expires. (To override this setting for certain user accounts, open the account's properties dialog box in Local Users And Groups and select the Password Never Expires check box.) Selecting 0 means passwords never expire. |
| Minimum password age | Specifying a number greater than 0 (the maximum is 999) lets a system administrator set the amount of time a password must be used before the user is allowed to change it. Selecting 0 means users can change passwords as often as they like. |
| Minimum password length | Specifying a number greater than 0 (the maximum is 14) forces passwords to be longer than a certain number of characters. (Requiring longer passwords enhances security, because longer passwords are harder to guess.) Specifying 0 permits users to have no password at all. Note: Changes to the minimum password length setting do not apply to current passwords. |
| Account Lockout Policy | |
| Account lockout duration | Specifying a number greater than 0 (the maximum is 99,999 minutes) specifies how long the user is to be locked out. If you specify 0, the user is locked out forever—or until an administrator unlocks the user, whichever comes first. |
| Account lockout threshold | Specifying a number greater than 0 (the maximum is 999) prevents a user from logging on after he or she enters a specified number of incorrect passwords within a specified time interval. |
| Reset account lockout counter after | This is where you set the time interval during which a specified number of incorrect password entries locks out the user. After this period elapses (from the time of the first incorrect password), the counter resets to 0 and starts counting again. |
TIP
If you use password history, you should also set a minimum password age. Otherwise, users can defeat the password history feature by simply creating a sequence of passwords at random.
If you are an administrator, you can unlock a locked-out user by double-clicking the user's name in Local Users And Groups and clearing the Account Is Locked Out check box.
Assigning Rights to Users and Groups
To assign or change the rights for a user or group:
- In Local Security Policy, expand Local Policies and select User Rights Assignment.
- Double-click the policy you want to view or modify.
- To add a user or group to the list, click Add.
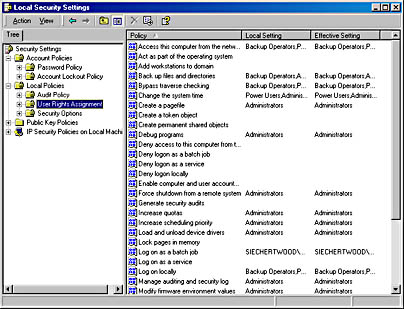
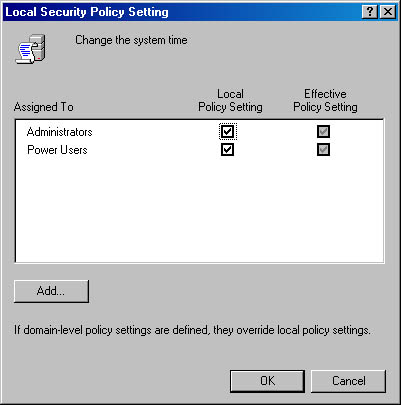
The Effective Policy Setting check boxes show the actual policy setting in use. If your computer is part of a domain, domain-level settings override local settings. Unless you are a domain administrator, you can't change the domain-level settings, so the Effective Policy Setting boxes are unavailable.
The Select Users Or Groups dialog box appears. This dialog box functions like the one shown in Figure 27-3 except that it shows users as well as groups.
Table 27-2 lists the default rights assigned to the built-in user groups.
Table 27-2. Default Rights of Built-In User Groups
| Group | Default Rights |
|---|---|
| Administrators | |
| Backup Operators | |
| Everyone | |
| Guest (account) | |
| Power Users | |
| Users | |
| (no one) |
EAN: 2147483647
Pages: 317