Hard Disk Duplication
| | ||
| | ||
| | ||
Creating a forensic image of a hard disk is one of the most common forensic techniques used. Images are created as part of investigations for analysis but may be created for other reasons as well:
-
Creating hard disk images to fulfill a legal discovery request.
-
Imaging the machines of high risk (or all) employees when they leave the company.
-
Duplicating an organization's standard or gold-disk build for comparison purposes.
-
Transferring damaged or degradable media to an archival-quality format (for example, DVD-R/CD-R).
| Tip | There are questions regarding the lifespan of DVD-R and CD-R media. Some media created in the 1980s and 1990s had manufacturing defects leading to early degradation, but the optical media is generally expected to last several decades. For best results, use archival-grade optical write-once media such as that available from Mitsui and Delkin. |
When a hard disk is imaged , the values of all of the bits in every sector are copied from the suspect's drive to another type of media or an image file. The drive itself can be later recreated exactly by copying the forensic image to another drive of a similar geometry and size (or a larger size in most cases) or analyzed as an image.
| Note | Technically, all of the relevant bits are copied. Drive-specific information such as preambles and CRC data are not generally copied. Likewise, bad sectors on the drive may not be copied (if marked bad by the drive hardware). Since these are not user accessible, there is no inherent data loss by not duplicating them. |
While forensic duplication does require all bits be copied in an unaltered fashion, the storage of those bits once copied does not need to be in a bit-by-bit file. Courts have permitted the use of lossless compression to save space. This can be a major factor in imaging times if a disk is mostly empty. They have also allowed reversible encryption to protect the image from prying eyes. Depending on the imaging software used, additional meta-information may be stored with the drive image as well. This information can include hash values, drive geometry information, examiner information, and duplication time/date stamps.
Duplication can be performed locally or remotely, with advantages and disadvantages to each method. Local duplication is faster than remote duplication and provides greater flexibility in acquisition hardware and techniques. There are two methods of local duplication: in-situ duplication (where the drives to be duplicated are kept in their respective machines) and direct duplication (where the drives are removed and directly duplicated using the appropriate hardware). (See the sidebar "Write Blocking.")
| |
When performing a forensic duplication, the data being acquired should not be altered in any way. While intentional alteration can be avoided procedurally, accidental alteration is more difficult to achieve. Many programs can inadvertently alter the contents of a disk; Windows itself writes a signature to a drive the first time it is recognized by the system.
To avoid both intentional and accidental alteration when performing a forensic duplication, write blocking software or hardware is used. Both write blocking software and hardware protect the evidence drive from alteration during the duplication process. Software write blockers attempt to catch the system calls generated by any instructions that attempt to write to the disk. Hardware write blockers monitor and block and write commands sent to the disk itself.
Software write blockers, such as PDBlock, allow a user to connect drives directly to the interfaces available on their forensic workstation. This can include FireWire, USB, SCSI, ATA, and SATA-based drives, depending on what adapters are present. For more obscure connection types (for example, some of the older SCSI standards or proprietary RAID-devices), there may not be any hardware blockers available, leaving software blocking as the only alternative. Some software blockers have had problems in the past with older operating system calls that bypass the standard Windows APIs for drive access. When using a software write blocker, make sure it has been court - tested and covers write calls based on both INT 13 and its extensions.
Hardware-based solutions are specific to an interface or set of interfaces. One side of the write blocker is connected to the forensic workstation (generally through a FireWire or USB 2.0 connection), and the other to the drive to be imaged. The Ultrablock and FireFly lines of write blockers from Digital Intelligence support the common SATA, IDE, and SCSI standards for connecting a range of hard disks. Hardware solutions generally allow for the highest speed imaging, as they use the native interface of the drive itself.
A final option for write blocking is to use all-in-one cloning devices. Originally developed for making multiple copies from a single master drive for rapid deployments, hardware-based cloning devices such as the SF-5000 have been adapted for forensic duplication, are ultra -portable and do not require a PC to operate . For high-volume duplications, these devices are must-haves when going on-site.
As an added benefit of write blockers, they can be employed to perform an analysis of a drive without first duplicating its contents. While not the standard technique for analyzing drive information, if a quick analysis is required, the suspect drive can be connected and searched before duplication occurs. This technique is useful when attempting to identify drives requiring additional analysis during a triage operation.
| |
Remote duplication is slower but can be done without the suspect being aware that duplication is occurring. Similarly, remote duplication can be performed when local duplication is not possible because of limited physical access to the suspect machine for whatever reason. Remote duplication always occurs in-situ.
In-Situ Duplication
In-situ duplication is generally slower than direct duplication but provides other advantages. If complex hardware is present (for example, hardware RAID controllers and obscure SCSI cards), the native computer's existing configuration can be used in the duplication. Secondly, there is less risk of damage to the drive itself as it does not need to be removed. Finally, duplication on live systems can be done without powering down for critical systems where downtime is not an option.
There are five primary methods for in-situ duplication:
-
Serial cable. A null-modem serial cable (used in the past for programs such as LapLink) can be connected between the analysis computer and the suspect computer to perform the duplication. A serial cable is generally the slowest method for connection, and duplication of terabyte- sized drives can take many days depending on the port speed settings, but this may be the only method available on older laptops with proprietary drive hardware (and no parallel or Ethernet ports they do still exist). Fortunately these laptops tend to have very small hard drives.
-
Parallel cable. Faster than a serial cable, a parallel cable delivers multiple bits of data simultaneously (in parallel). Products like EnCase rely on parallel port connections as a back method of communicating. While still slow, a parallel port connection can be used when an Ethernet connection is unavailable, or drivers for the Ethernet card in the suspect's machine are difficult to acquire.
-
Ethernet. Ranging from moderately fast to very fast, Ethernet connections constitute the ideal method for machine-to-machine duplications. Ethernet cards are readily available in most current laptops and desktops at 10 and 100 Mb/s, with 1 Gb/s cards become even more common, and Ethernet drivers (for DOS, which most boot disks use) for the most common chipsets are readily available online. When performing an Ethernet-based duplication, a crossover cable is used to directly connect the machines. The use of a hub or switch will not only slow down the duplication, but will introduce another layer of complexity that is unnecessary.
-
Wireless. Wireless Ethernet cards are now readily available, though the speeds are generally lower and encryption needs to be used to protect forensic integrity. They are not generally used for forensic purposes, however. Many of the DOS mode drivers that are frequently needed for duplication are non-existent for these chipsets, although bootable Linux drivers generally are.
-
USB. A fairly recent trend since the introduction of cheap USB 2.0 hard disks, DOS USB drivers are now part of many forensic boot disks and CD's. These drivers enable the examiner to connect a larger USB hard drive to the suspect's machine and perform the duplication directly to that location. The availability of cheap USB hard disks and speed improvements in USB 2.0 has made this one of the preferred choices for local acquisition.
| Note | The times shown in Figure 9-1 are estimated based on the theoretical maximum speeds of each technology commonly in use and do not reflect compression. |
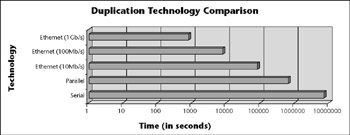
Figure 9-1: Duplication timeframes for 100GB of data
In-situ duplications require the use of a boot disk or bootable CD. These media allow the examiner to boot to a memory-only (does not write to the hard disk) version of an operating system which permits duplication. The operating system used is generally DOS or Linux.
The default Windows XP startup disks do not read NTFS partitions and likewise do not have access to CD-ROMs. To remedy this, create a Windows 98SE OEM boot disk and install the NTFS read-only drivers available at http://www.sysinternals.com/ntw2k/freeware/ntfsdos.shtml.
| Note | Images can be created from either the OS itself or from extractable images available at http://www.bootdisk.com. Technically, one does not need any file system drivers to do a raw drive duplication, but the NTFS driver is read-only and enables the analyst to do a quick check for specific files or their contents on the suspect system as needed. |
This floppy can now be used for booting on the suspect's machine. The primary consideration during acquisition is not altering the data on the suspect device. As such, extra caution is needed in booting to ensure the floppy or CD boots first. To boot for the purposes of a duplication:
-
Disconnect the data cable and power cable from the back of any hard disk drives in the suspect's machine.
-
Boot the machine and enter BIOS. This can generally be accomplished by pressing F1, F2, or Del during the initial boot process.
-
Change the BIOS settings to boot first from either the floppy of the CD drive. If possible, disable booting from the hard disk as an option.
-
Reboot the system with the floppy/CD inserted. Confirm the system boots properly.
-
Power off the system and reattach the relevant hard disk cables.
-
Power on the system with the bootable floppy/CD in the drive.
-
Load any necessary drivers to perform the duplication and connect the relevant serial/parallel/Ethernet/USB devices.
-
Begin the duplication.
Because of the size limitations of the floppy disk, a forensic CD used in conjunction with the floppy is extremely useful. A copy of dd.exe and large driver files can be burned to a CD in advance, then accessed or loaded as necessary. Although primarily a Linux distribution, the Helix environment contains several of these files for forensic use. Additionally, both SafeBack and EnCase provide bootable floppy and CD images to enable the imaging of drives with their respective tools. A menu-driven Ethernet/TCP/IP boot disk image created by Teledata from and contains the common Ethernet chipset drivers (both PCI and CardBus) as well as the ability to configure a card with a static or dynamic IP address.
To perform an image using the Ethernet connection, the analyst first needs to boot the suspect's computer using a network boot disk as noted previously. Then do the following:
-
Connect a crossover cable between the suspect machine and the analysis machine.
-
Configure the suspect machine with a static IP address of 192.168.1.1 and a Netmask of 255.255.255.0.
-
Boot the analysis machine and configure it with an IP address of 192.168.1.2 and a Netmask of 255.255.255.0.
-
Start a netcat listener on the evidence machine and pipe the output of that listener to dd:
nc -l -p 23 dd of=c:\evidence.img
-
Use dd to image the drive and send the results to netcat on the evidence machine (http://www.chadsteel.com on port 23 in the example) by typing the following on the suspect machine:
dd if=\.\PhysicalDrive0 bs=512 conv=noerror nc www.chadsteel.com 23
If a partition needs to be imaged and not the entire drive, the drive letter (for example, c: ) can be substituted for PhysicalDrive0.
| Tip | If multiple partitions are present, PhysicalDrive# can be used with # being the number of the drive to image the entire physical drive. For imaging nonhard disks, using the drive letter will image the whole device assuming one partition is present. |
If the drive image files are too large, they can be split using the skip feature of dd. This allows the drive to be broken into manageable chunks to enable easier transmission, compression, and archiving to smaller media. To create 660MB-sized image files (to fit a standard CD), the following commands can be used:
dd-gnu if=\.\PhysicalDrive0 count=660000 of=c:\evidence1.img dd-gnu if=\.\PhysicalDrive0 count=660000 skip=660000 of= c:\evidence2.img dd-gnu if=\.\PhysicalDrive0 count=660000 skip=1320000 of= c:\evidence3.img . . .
An additional feature that can be used with the GNU gzip program is compression. Compressing an image will allow it to be transmitted faster and use less bandwidth.
| Warning | For most scenarios compressing is faster. However, if the drive is filled (70 percent or more) with MPEG-2 movies or MP3s (or any other precompressed file formats), it will actually be slower. Similarly, a drive that has been overwritten with random characters will also be slower. |
To perform compression, the image is piped to gzip using the -c option (to send the results to standard output) before piping to netcat. On the listening side, the results are then decompressed before outputting to a file. To enable compression using gzip, on the listening computer type:
nc -l -p 23 gzip -d -c dd of=c:\evidence.img
And on the suspect's computer, type:
dd if=\.\PhysicalDrive0 bs=512 conv=noerror gzip -c nc www.chadsteel.com 23
Enabling compression will generally halve the transfer times on a typical machine.
Duplicating an image to a local USB drive is much simpler. Duplication can be performed as follows :
dd if=\.\PhysicalDrive0 of=\.\f:\evidence.img bs=512 conv=noerror
where f: is the drive letter of the USB-attached device.
| Note | All of these examples assume gzip, dd, and nc are in the current path. Include them in the path or explicitly type the directory names where they are located on the particular forensic CD/floppy. |
All of the in-situ commands shown previously can be used on a live system as well, though it is not recommended unless other options have been exhausted. If remote duplication of a live system is needed, it is recommended that a specialty tool such as EnCase Enterprise be used.
| Tip | Social engineering can be used to facilitate an installation of the EnCase Enterprise Servlet or other forensic tools. We once used a "must install this patch immediately" technique to successfully deploy the servlet to a large number of internal machines through a simple email message. |
| |
EnCase Enterprise, Guidance Software's flagship product, provides comprehensive, court-tested remote acquisition and analysis capabilities. The EnCase tool has an integrated acquisition environment based on servlets, small applications that can be placed on the machine to be duplicated. These are tied together with a central authentication and authorization machine called SAFE, which provides the necessary controls on forensic duplication within an organization. The following figure shows the overall model.
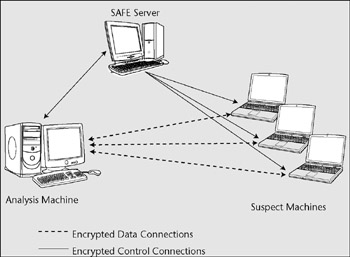
EnCase Enterprise Deployment Model
When a duplication or analysis of a remote machine is required, the EnCase servlet is installed on the machine to be duplicated. The servlet supports multiple operating systems, and can be installed locally or remotely with administrative rights. Remote installation can be done with SMS or by copying the servlet to the suspect machine and then running it using a remote execution tool such as psexec. The servlet can be installed as memory-only (no copy is made to disk) or as an executable running as service. The service is user-configurable for naming purposes, and can be well-hidden from suspect observation. A listener is opened on port 4445 for instruction connections from the SAFE, and remains present until uninstalled or stopped .
When a duplication is needed, the examiner logs into the analysis machine and connects to the SAFE to be authenticated and authorized to perform the duplication. When the analyst confirms that the user can perform the duplication, he makes a data connection to the remote system to retrieve the meta-contents of the file system (the FAT of the MFT). The contents are cached on the analysis machine for identification of specific files to copy or meta-analysis on the files present.
The duplication can be at a file, partition (logical), or physical level. For a full duplication, the servlet compresses the data on the suspect's machine and then sends it over an AES-encrypted channel to the analysis machine for inclusion as an image file (using a proprietary EnCase image file format). With version 5 of EnCase Enterprise, the connection can be stopped and restarted as necessary with a delta kept at the servlet level of any changes since the last connection very helpful with laptops, as they disconnect frequently. The image gathered can be automatically hashed when downloaded, allowing for an integrated integrity verification.
Although expensive, the EnCase Enterprise tool does provide a more seamless and streamlined approach to forensic duplication than single, standalone tools. For organizations with multiple sites globally or cost-prohibitive travel requirements for investigations, it can pay for itself in a very short time.
| |
Direct Duplication
Direct duplication is faster than in-situ duplication, as it uses the native drive technology of the disk being imaged. Direct duplication is preferred when there are a large number of drives that need to be imaged, when the drives need to be shipped or carried to a lab for imaging, or when readily available drive formats (for example, SATA or ATA) are being analyzed. Because direct duplication does not require the use of boot disks or CDs, there is no need for a working CD or floppy drive on the target machine. Similarly, as long as the drives are intact, having the ability to use a hardware write blocker increases the integrity of a direct duplication.
A second occasion when direct duplication is warranted is the acquisition of removal media. Devices such as floppy disks, CD-ROMs, DVDs, Digital Cameras, USB Flash Drives, and other removable devices can all be imaged the same way as a hard disk. By imaging these media, they can be analyzed en masse (imaging searching one hundred floppy disk images stored on a fast hard disk versus searching one hundred floppy disks individually) regardless of the original media type.
To duplicate a hard disk directly, the following are the basic steps:
-
Unplug the suspect's machine, following the guidelines for powering down noted previously.
-
Remove any hard drives in the machine.
-
Check any removable media drives and remove any contents.
-
Connect the write blocker to the analysis machine.
-
Connect the disk drive to the write blocker.
-
Power on the analysis machine.
-
After booting is complete, power on the write blocker.
-
Utilize dd (or another duplication utility) to image the drive.
| Tip | It is possible to remove CD/DVDs even when the machine is powered off. Place a paperclip in the small hole under the drive to eject the media. |
Duplicating locally allows for a larger number of possibilities for the storage of the duplicated information. The location to which the initial duplication occurs may or may not become the long-term storage location (for example, multiple disks may be duplicated to a hard disk as a short- term step, burned en masse to a DVD-R for archiving and data integrity, and finally copied back to another hard disk for fast analysis). The primary options for duplication are magnetic tape, hard disks, optical disks, and multi-tiered storage devices.
Magnetic Tape
Magnetic tape is the cheapest per-gigabyte option for the storing of duplicate information. Inexpensive tape media are readily available in a range of sizes and can store images of the largest single drives available on a single tape. Additionally, most magnetic tape cartridges support write protection after the initial writing, making them suitable for evidentiary image storage. Due to the small physical dimensions of tape cartridges, they also qualify as having the greatest storage density per cubic foot (important for large organizations which store hundreds of terabytes or petabytes of data).
Magnetic tape hardware is generally slower than a hard disk for duplicating but fast enough to be viable for the initial storage (although the serial nature of tape-based systems makes them unsuitable media for direct analysis). Like all magnetic media, tapes tend to degrade over time and need to be kept at the manufacturer-specified temperature and humidity to maintain their integrity for an extended period of time. The past ten years have also seen more significant technology changes in the tape backup space that are not backwards compatible than other media types, requiring spares of tape backup units be kept for as long as the evidence tapes themselves are kept.
Despite its limitations, magnetic tape remains an excellent choice for both short-and long-term evidentiary storage of data.
Hard Disks
The fastest mechanism for duplicating a hard disk is to duplicate it to another hard disk. Hard disks are one of the few media that allow direct analysis of the data using a write blocker as well as storage, although in practice they are rarely used as long-term storage options.
Hard disks have a good history of backwards compatibility within the ATA technology chain. An SATA controller can still read an original ATA-1 drive with the proper adapter, but hard disks suffer from the same degradation that affects all magnetic media. The cost per gigabyte of a hard disk is relatively high, and the physical dimensions of hard disks make them less than ideal for high-volume storage.
Hard disks are the best choice when a fast initial duplication is required or a quick analysis is needed and a write blocker is available.
| Tip | Hard disks used for duplication should be prepared in advance by wiping the disk with a series of zeros and then formatting for the appropriate partition type. NTFS is recommended due to the file size limitations present in FAT drives. Images can grow larger than the 4GB allowed for a single file on a FAT partition. Never assume that an out-of-the-box hard disk is wiped clean for forensic use. Some manufacturers have been known to provide refurbished platters on new disks, and others write-test data to drives as part of their QA procedures. |
Optical Disks
Optical disk media, specifically CD and DVD-Rs, are excellent for both portability and evidential integrity. The price per gigabyte on optical media is generally better than that of hard disks, and the longevity of archival quality optical disks purporting to be greater than that of any magnetic media. The inherent write-once capability of the media itself offers built-in protection against intentional or accidental alteration, and optical drives have been made backwards compatible with the first CD-ROMs.
| Note | Although there are rewritable optical media available, they are not suitable for forensic use. Their longevity is less, the inherent advantage of having write-once capability is not present, and their cost per gigabyte is significantly higher. |
The speed of optical disks is increasing rapidly but is not as fast as a hard disk for direct duplication. Additionally, the capacity of optical media is fairly small by current standards, although the new high-density DVD standards improve that dramatically, and the need to span multiple disks is a negative.
Optical media are an excellent choice for long-term archiving of evidence, as well as the forensic duplication of smaller-capacity media (for example, flash disks, floppies, or other optical disks).
Multi-tiered Storage
A typical forensic duplication and analysis lab will have multiple storage options available. Here is a typical setup for a complete forensic lab:
-
Multi-terabyte RAID array. For analysis of multiple disk images at once and short-term storage of working copies for all active cases, a large disk array can be used. This can be a standards RAID array, or a more advanced NAS or SAN solution such as those available from EMC or NetApps.
-
Ultrium tape backup unit (integrated). To backup the overall array, an Ultrium tape unit can be used with weekly full and daily incremental backups. The tapes are not the copies of record, but backups of the working analysis copies.
-
Ultrium tape backup unit (portable ). For high-capacity, on-site evidentiary copies, a portable Ultrium unit can be used. The unit should be the largest capacity currently available, and be compatible with the integrated server unit mentioned previously.
-
DVD-R drives. The fastest available (and highest capacity for high-density DVDs) drives should be installed on all analysis machines. Additionally, a portable drive (USB 2.0 and FireWire combo if available) should be purchased. The DVD-R media are used to create and restore the archival, best evidence copies of the disk images as well as perform backups of specific pieces of evidence (for example, log files) and other case information.
-
USB 2.0 hard disks. Several USB 2.0 hard disks cans be used for quick evidence gathering or as temporary analysis devices. The capacity should be the largest available.
With all acquisition, evidentiary integrity must be maintained and confirmed throughout the duplication process. An MD5 hash of the data can be used to provide this confirmation. To prove alteration has not occurred, an MD5 sum should be taken immediately following every step in the duplication (for example, copying from a local system to DVD-R) and the results compared to the original MD5 hash and recorded as part of the documentation of the duplication.
| |
Our security team was briefed on an investigation in a secured area that required our expertise. A confidential informant made allegations of fraud, bribery, and embezzlement on the part of a corporate management team. He provided sufficient direct evidence to prove the wrongdoing, but the extent of the corruption was unclear.
Because the investigation spanned an entire management team, we had a minimal amount of time onsite to conduct interviews and collect evidence only 24 hours for 20 individuals. With the whole group as potential suspects , local support was not an option, and because of the critical nature of the business, we were not permitted to bring the electronic evidence offsite for forensic duplication and analysis.
After our legal department ran a quick contract, the investigation team began preparing for an early morning flight. As a result of the late request, we did not have the ability to pull in additional support or equipment. To make things tougher, half of our duplication laptops were out on other remote investigations. Facing a shortage of duplication equipment (one portable tape backup unit and two duplication laptops with a myriad of interfaces), we were illequipped to image and bring back 20 laptops and several local servers.
Relying on our scavenging abilities , we visited our internal desktop support team and commandeered their imaging equipment, which they used for cloning laptops to deploy to the sales force. Another team member was sent to the local CompUSA before closing to purchase 20 of the largest capacity hard disks available. We ended up with a myriad of brands and sizes from what was actually in stock. The remainder of the evening was spent wiping the disks for use and putting a game plan in place. We would focus on interviewing and acquiring while on-site and perform all of the electronic analysis offline. A second trip would be scheduled as necessary if further individuals were implicated as a result of the analysis activities.
When we hit the ground, we split into two teams . The management team was called into a conference room and interviewed one by one regarding the allegations. At the same time, we used the cloning hardware to image their laptop drives directly to similarly sized SATA drives, as well as the drives of four Windows 2000 file servers. Due to its size (15TB total storage space), the mail server was not fully imaged. The mail files of the suspects were copied directly to the tape backup unit for analysis at a later point.
We ultimately identified five other suspects after the interviews. We acquired their machines via the tape backup unit as we had already run out of hard disks. All of the disks and tapes were then packed in anti-static bags and then put into evidence bags and boxed for drop-shipping to the analysis lab.
At the lab, the individual drives were re-imaged and acquired using EnCase Enterprise. The acquired image files were burned to DVD-R for permanent storage, and the individual case files copied to our EMC unit for simultaneous analysis. The mail files were likewise copied to individual DVD-Rs, and copies placed on the analysis array.
Our analysis validated the allegations. A careful reconstruction of several e-mail chains confirmed the bribery allegations, and a series of deleted Excel spreadsheets were recovered from the free space on the drive. They belonged to the vice president of sales and showed two sets of monthly sales figures: one under a worksheet called Reported and a second under a worksheet called Actual . This was as close to a smoking gun as we could possibly hope for.
The analysis was able to link six of the suspects to wrongdoing. They were immediately dismissed by the company and replaced with a new team. Although the managing partner was not directly implicated, she was likewise replaced because of the magnitude of the corruption that had occurred on her watch.
| |
| | ||
| | ||
| | ||
EAN: 2147483647
Pages: 71