Implementing Smart Card Authentication in the PKI
|
EXAM 70-293 OBJECTIVE 6, 6.2.3
If security is a primary concern for your organization, you might want to consider the use of smart cards for both local and remote authentication. This adds a second level of security to the authentication process. Whereas traditional authentication via password requires only “something you know” (the password), smart card authentication also requires “something you have” (the card).
Along with biometric devices such as fingerprint readers and retinal scanners, smart cards represent a more secure way for users to gain access to the network. Smart cards are not as secure as most biometric devices, but they are more widely implemented and have a longer history of use (more than 11 years). In fact, there are many companies that issue smart cards and smart card readers along with Windows Server 2003-compliant drivers and software. Primarily because of several competing standards, smart card adoption has been slow, but their popularity continues to grow. They might not replace the standard log-on password anytime soon, smart card technology is full of potential.
What Are Smart Cards?
Most smart cards today look and feel like a credit card. The difference is that smart cards have either integrated circuit technology (with gold-colored metallic contact points on the surface of the card) or magnetic technology (located inside the card). Smart cards use these technologies to house an embedded microprocessor that is capable of storing everything from encryption keys to medical information (at least in theory). At present, smart cards are generally used for authentication, and sometimes for encrypted e-mail.
In the case of authentication, the user inserts a smart card into a smart card reader and enters his or her personal identification number, or PIN, similar to the process of using an ATM bank card. The reader can then forward the secure information contained in the card, eliminating the need for the user to type in a name and password (the actual process of authentication is described in more detail below). It is a more secure method of authentication because theft of a smart card does not compromise security—without the PIN, the card is useless, and without the card, knowledge of the PIN is useless.
| Test Day Tip | For the exam, be aware that when smart card authentication is used, you cannot promote a server to a domain controller and you cannot join a computer to a domain. To accomplish these administrative tasks, a normal password logon is required from a user with appropriate permissions. |
How Smart Card Authentication Works
After setting up an enrollment station (described below), any user with the enrollment agent certificate can issue smart cards to users. Enrollment is the process by which a CA grants a certificate to the card. The card itself generates a public/private key pair, and the certificate is used to protect the public key during transport. After enrollment, the user can insert the card at any workstation on the network, including terminal services clients and remote access clients, as long as a smart card reader is present.
If possible, clients logging on to a Windows Server 2003 network will be authenticated with the Kerberos protocol. In traditional authentication, a username and password typed in via the keyboard are used to encrypt communication between the client and the Key Distribution Center (KDC). With smart cards, however, the private key stored in the card digitally automatically signs the timestamp that is sent to the KDC, eliminating the need for a password. In addition to the encrypted timestamp, the card’s certificate (including of course the card’s public key) is sent as well. When the KDC receives the package, known as a ticket-granting ticket (TGT) request, it verifies the public key and then uses the public key to verify the digital signature on the request. If everything checks out, the server authenticates the client by returning a ticket that is also encrypted with the card’s public key. Finally, the ticket is decrypted at the client’s workstation by the private key stored in the smart card.
| Exam Warning | The CA that issues the smart card certificates must reside in the same network forest as the users. Users from a different forest will use local domain controllers to authenticate, and these domain controllers will not be able to validate the certificates they receive. |
Deploying Smart Card Logon
Even though smart cards have been around for some time, many different standards still exist. This can complicate the deployment of a smart card solution, especially if Windows Server 2003 does not natively support the hardware you’ve chosen. In that case, several extra steps are required. Windows Server 2003, out of the box, contains drivers for two companies that manufacture smart cards and readers – Schlumberger and Gemplus. For any other vendor’s equipment, you’ll need to install drivers and the CSP that the vendor uses.
The first step in deployment is to prepare the appropriate certificate templates. These templates include the following:
-
Enrollment agent
-
Smart card logon
-
Smart card user certificates
The templates are not enabled by default and require some configuration. The second step is to issue the enrollment agent certificate. Finally, the smart cards need to be enrolled at the enrollment station. We’ll guide you through the step-by-step deployment process later in this chapter.
Smart Card Readers
Most smart card readers in today’s market attach to the computer’s USB or serial port. USB equipment is strongly recommended if your clients have USB ports. Readers are available in external or internal models, and many cost less than fifty dollars at retail. Readers that are built into a keyboard are also gaining in popularity. Make certain that the readers you choose will read the kind of smart card you plan on issuing.
Smart Card Enrollment Station
The enrollment station you choose should be a secure system and must be running Windows 2000 or higher. Of course a smart card reader must be installed and appropriate drivers and CSPs loaded if necessary. Finally, you should install any vendor-supplied utility software.
Using Smart Cards To Log On to Windows
Smart cards can be used for more than secure authentication. In fact, there are two different templates in Windows Server 2003 that are both used for smart card certificates. The first is the smart card log-on certificate, which, as the name implies, is used only for logons. The second is the smart card user certificate, which, in addition to logons, provides secure e-mail services. For the following exercise, you’ll use the more common of the two which is the smart card logon certificate. You will have to have a PKI implemented with at least one CA already running before beginning. You will also need a smart card reader and a smart card to complete this exercise.
Exercise 12.04: Implementing and Using Smart Cards
-
On the system acting as the CA, log on as an administrator and open the Certification Authority console by clicking Start | Programs | Administrative Tools | Certification Authority.
-
Expand the appropriate CA container, right-click Certificate Templates, and choose New | Certificate Template to Issue (see Figure 12.30).
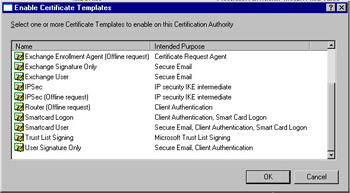
Figure 12.30: Enable Certificate Templates Window -
Select Smartcard Logon and click OK. Repeat step 2 and select Enrollment Agent and then click OK.
-
Right-click Certificate Templates and choose Manage. As shown in Figure 12.31, this displays the Certificate Template snap-in.
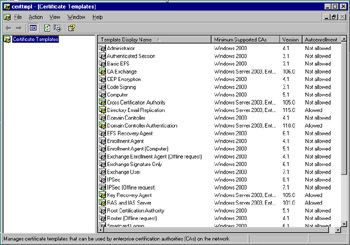
Figure 12.31: Certificate Templates Snap-In -
Right-click the Smartcard Logon template and choose Properties. Click the Security tab.
-
For this exercise, assign the administrator the role of enrollment agent. Add the Administrator by clicking the Add button. After selecting the Administrator, select the Read and Enroll check boxes. Click OK to finish. Close the console.
-
Log on to the enrollment station system as an administrator. Click Start | Run, type certmgr.msc, and then click OK. This launches the Certificates snap-in, as seen in Figure 12.32.
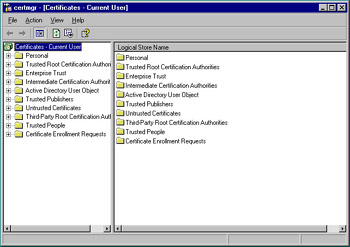
Figure 12.32: Certificates Snap-In -
Expand the Personal container, right-click Certificates, and choose All Tasks | Request New Certificate. Proceed past the Certificate Request Wizard’s opening screen by click Next.
-
Figure 12.33 shows the Certificate Types screen. Choose Enrollment Agent and click Next. On the next screen, do not type anything in for the Certificate Friendly Name and Description fields. These fields are optional, and you will not use friendly names or their descriptions in this exercise. Click Next, and then click Finish. A message appears when the certificate has been issued. Close the console.
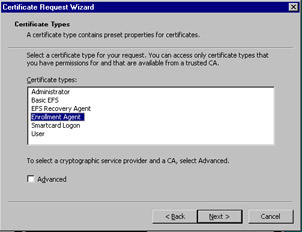
Figure 12.33: Certificate Request Wizard’s Certificate Types Screen -
You will now use a similar certificate-requesting technique to Exercise 12.03, but with more advanced options. Launch Internet Explorer and type http://servername/certsrv in the Address bar, where servername is the server name of the CA you used in step 1.
-
Click Request a certificate and then click Advanced certificate request on the next screen.
-
Figure 12.34 shows the Advanced Certificate Request screen. Click Request a certificate for a smart card on behalf of another user by using the smart card certificate enrollment station.
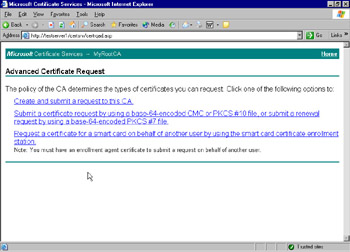
Figure 12.34: Advanced Certificate Request Screen -
Figure 12.35 shows the Smart Card Certificate Enrollment Station screen. Select Smartcard Logon from the Certificate Template drop-down box.
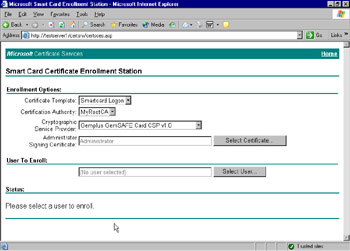
Figure 12.35: Smart Card Certificate Enrollment Station Screen -
Select the CA used in Step 1 from the Certification Authority drop-down box.
-
Select the appropriate CSP from the Cryptographic Service Provider drop-down box.
-
Click the Select User button and choose the user you are enrolling.
-
Place the smart card into the attached reader and click Enroll.
-
The CSP will now enable you to enter a PIN for the card. Enter the PIN and click OK.
-
Distribute the card to the user for testing.
Using Smart Cards for Remote Access VPNs
The use of smart cards for local logons has met with limited, albeit recently growing, success. One reason for the limited acceptance is that local authentication traffic does not usually pass over insecure public networks; therefore, the added cost and administrative effort required for a smart card implementation is not justified. For remote access users, however, authentication communications are vulnerable, and smart cards can provide needed extra security.
To use smart cards to log on to a remote access VPN server, the server must first be configured to enable it. This includes selecting a protocol, as discussed below. It also includes obtaining a machine certificate for the VPN server. When the server is able to accept smart card certificates, the client must be configured to send them. This means attaching a smart card reader and establishing a VPN connection. If you view the Properties of the client’s VPN connection, you will notice a Networking and a Security tab. For smart card use, the type of VPN selected under the Network tab should be the Level 2 Tunneling Protocol, or L2TP. The Security tab, shown in Figure 12.36, is a bit more complex. There are two options, Typical and Advanced.
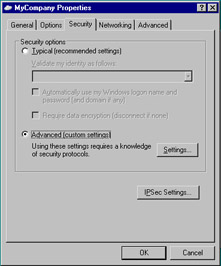
Figure 12.36: Security Tab of the VPN Client’s Properties Sheet
Choose Advanced (custom settings) and click the Settings button. Choose the Use Extensible Authentication Protocol (EAP) option and select Smart Card or other certificate (encryption enabled) from the drop-down box. Click the Properties button, and the Smart Card or Other Certificates dialog box appears as shown in Figure 12.37. Choose the Use my smart card option. Your configuration of the VPN client is now complete.
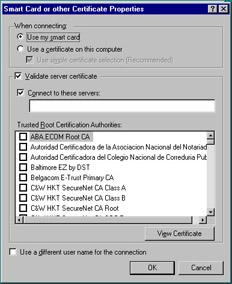
Figure 12.37: Smart Card or Other Certificate Properties Sheet
Enabling the Extensible Authentication Protocol (EAP)
on a Remote Access Server
The steps required to prepare a server that is already running the routing and remote access services (RRAS) to use smart card authentication are fairly straight-forward. First, from the RRAS console, display the properties sheet for the server and proceed to the Security tab. Next, choose Windows Authentication and select Authentication Methods. Choose the Extensible Authentication Protocol (EAP) option and select EAP Methods. Finally, choose the Smart Card or Other Certificate option.
Configuring Remote Access Policies is also relatively simple. You can create a new policy or edit the existing Allow Access If Dial-In Permission Is Enabled policy. After going into the policy’s property sheet, choose to Edit the profile and proceed to the Authentication tab. Select EAP Methods and click Add to choose the Smart Card or Other Certificates option. Clicking Edit brings up the property sheet for the option. To complete the edit, select the RRAS server’s fully qualified domain name (FQDN) in the Certificate Issued To field.
Using Smart Cards To Log On to a Terminal Server
Using smart cards to log on to a terminal server is inherently more secure than using passwords, as we’ve discussed previously. Similar to using a smart card on a local workstation, using a smart card on a terminal client enables the server to verify your identity and give you appropriate access. Also, if you want the information contained in the card to be available for the entire terminal session, perform the following steps:
-
Click Start | Programs or All Programs | Accessories | Communications | Remote Desktop Connection.
-
Click Options and proceed to the Local Resources tab.
-
Under Local Devices, click the Smart Card option and click Connect.
|
EAN: 2147483647
Pages: 173
- Chapter IV How Consumers Think About Interactive Aspects of Web Advertising
- Chapter VI Web Site Quality and Usability in E-Commerce
- Chapter VII Objective and Perceived Complexity and Their Impacts on Internet Communication
- Chapter XIV Product Catalog and Shopping Cart Effective Design
- Chapter XV Customer Trust in Online Commerce