Designing an Optimized IAS Solution
Optimize your IAS design by planning how to scale your IAS servers, whether or not to add IAS servers, where to place your IAS servers, and other steps as illustrated in Figure 7.9.
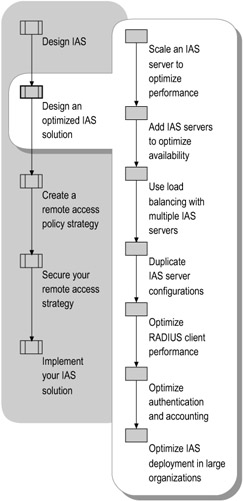
Figure 7.9: Designing an Optimized IAS Solution
IAS RADIUS clients and servers require minimal management and administration. However, over time, changes in the number of access clients, changes in WAN technology, and other factors can reduce the performance of IAS.
You can optimize IAS performance by positioning your IAS servers strategically. Use the following guidelines when deciding where to position your IAS servers:
-
Locate IAS servers in the same domain with the server that provides remote user account authentication.
-
Locate IAS on a domain controller and store the user account database in Active Directory.
In addition, the following factors can negatively impact IAS performance:
-
The current load of the domain controller.
-
The resolution of user principal names, resulting in an additional remote procedure call (RPC) query against the computer that contains the global catalog.
-
EAP-based authentication methods, involving multiple challenge-response exchanges.
-
The type of hardware in use.
-
Network latency between:
-
The IAS server and the domain controller.
-
The IAS server and the computer that contains the global catalog.
-
The IAS server and the access server.
-
You can optimize the performance of an IAS solution by scaling IAS to meet increasing demands in your organization and by including more than one RADIUS client and server in your network design.
Scale an IAS Server to Optimize Performance
IAS servers can accommodate a large volume of accounts and authentications per second. For this reason, they perform well in large organizations. A single IAS server can often meet the dial-up and VPN connection needs for an entire network. However, if you have more complex network access needs, you might need to scale even a single IAS server. For example, certificate-based authentication can generate a large volume of authentication traffic that is transmitted every time a client logs onto the network. If you use certificate-based authentication, you must scale IAS to meet all of your Internet authentication needs.
For more information about scaling IAS, see "Deploying IAS as a RADIUS proxy" in Help and Support Center for Windows Server 2003.
Add IAS Servers to Optimize Availability
It is important to prevent an IAS server from becoming a single point of failure.
To prevent an IAS server from becoming a single point of failure, deploy IAS servers either in pairs (a primary and a backup IAS server) to provide fault tolerance, or in multiples, to balance the load of a large volume of authentication and accounting requests. Add at least two additional IAS servers per forest.
The level of availability that you need to provide depends on the following:
-
How likely it is that a network link will fail
-
How important it is to provide uninterrupted authentication to your clients at all times
Balance your need for availability against your need to minimize the costs of the hardware investment. Keep in mind that you can add IAS to existing domain controllers.
When you deploy more than one IAS server, make sure to design your IAS servers to use RADIUS proxies for load balancing and synchronization of the server configurations.
Use Load Balancing with Multiple IAS Servers
If you add multiple IAS servers for performance reasons, you must load balance the servers. You can load balance and provide failover at each access server by configuring the access server to send queries to multiple RADIUS servers in a specified order of importance. You can also load balance by using IAS as a RADIUS proxy server that forwards connection requests to IAS servers in groups called remote RADIUS server groups. These configurations are useful for the following:
-
Organizations that use EAP-TLS for authentication, which increases the load on RADIUS proxies and servers. For example, ISPs and corporations that want to provide wireless or authenticating switch access often use EAP-TLS.
-
Organizations that need to sustain continuous service availability.
-
ISPs that outsource VPN access for other organizations. The outsourced VPN services can generate a large volume of authentication traffic.
You can use RADIUS proxies to balance the load of a large volume of authentication traffic. Without RADIUS proxies, each network access server balances its RADIUS requests across multiple RADIUS servers and detects unavailable RADIUS servers.
When RADIUS proxies are in place, the load of authentication, authorization, and accounting traffic is distributed across all of the IAS servers in the organization. Additionally, there is a consistent scheme for failure detection and RADIUS server failover.
Duplicate IAS Server Configurations
When you deploy more than one IAS server to provide the same authentication, authorization, and accounting service to RADIUS clients and proxies, you must copy the configuration of one IAS server computer to the other IAS servers. To duplicate the configuration of one IAS server to multiple IAS servers, use the IAS snap-in. This duplication method is useful when the number of configuration changes is small or if you are duplicating the configuration to only a few IAS servers. You can use the snap-in to manage both local and remote IAS servers. If you make a configuration change to one IAS server, you must make the same configuration change to all of the IAS servers that provide the same service.
To duplicate one IAS server configuration when there are a large number of configuration changes or a larger number of IAS servers, you can copy the configuration of one IAS server to another IAS server in the following way:
-
Make configuration changes on the primary IAS server.
-
On the primary IAS server, use the netsh aaaa dump command to export the configuration of one IAS server to a Netsh script file. The dump command displays the configuration of the IAS database file (Ias.mdb) as a Netsh command script that you can use to duplicate the configuration of the server on which the command is executed. The Netsh command script contains the configuration of the IAS server, including the registry keys and database file (Ias.mdb), in a compressed text format as a large data block. This large data block is used by the set config command within the script to import the configuration of a saved data block into an existing IAS database on the same or another computer, which you can perform by using the netsh exec command. To save the Netsh command script to a file, type: netsh aaaa show config > Path\File.txt
-
On the target computers, use the netsh exec command to import the primary IAS server configuration to the other IAS servers.
By using these two Netsh commands, you can automate the process in a simple batch file or script for multiple IAS servers.
Use this method to manage RADIUS and remote access policy configurations in a large enterprise network.
The netsh aaaa commands also provide a way to export and import individual aspects of the IAS server configuration rather than the entire configuration. For example, you can export and import only the remote access policies, or you can export and import only the RADIUS clients configured on a server.
For more information, see "Netsh" and "Netsh commands for AAAA" in Help and Support Center for Windows Server 2003.
Optimize RADIUS Client Performance
Because RADIUS clients, such as VPN servers and dial-up access servers, manage access client connections, their performance directly affects access client performance. Providing highly available RADIUS clients ensures that access clients can reliably connect to the network and can always be authenticated by IAS.
You can optimize performance for access clients that are using all types of connections by doing any of the following:
-
Upgrading the hardware of existing RADIUS clients. Choose this option if your hardware is outdated, and it is cost effective to upgrade it.
-
Replacing existing RADIUS clients with higher-performance servers. Choose this option if you cannot upgrade the hardware of your existing resources.
-
Adding RADIUS clients. Choose this option if your hardware is up-to-date, but you require more fault tolerance. Be sure to register redundant RADIUS clients with the IAS servers to ensure proper authentication and accounting.
You can optimize the performance of RADIUS clients that support dial-up connections by assigning remote access clients different primary and backup telephone numbers. This ensures that the remote access clients connect to different RADIUS clients. Choose this option if you require additional load balancing.
Optimize Authentication and Accounting
RADIUS servers provide authentication and accounting for RADIUS clients, and interact with the authentication servers. As a result, RADIUS server performance and availability impacts authentication and accounting performance.
To optimize authentication in your network, ensure that all redundant IAS servers use the same user account database, thereby ensuring that the user accounts are available for authentication. Also, specify that RADIUS clients use the redundant IAS servers to ensure proper authentication and accounting.
In larger organizations with complex forest or domain topologies, use IAS as a RADIUS proxy to forward authentication requests to remote RADIUS server groups. You can also designate remote RADIUS server groups to process only accounting requests, freeing the servers performing authentication from handling accounting traffic.
To optimize authentication and accounting performance in your IAS design, take the following actions:
-
Run IAS on the same computer as the domain controller. This speeds IAS access to the Active Directory user accounts database when IAS is performing user authentication and authorization.
-
Run IAS on the same computer that contains the global catalog. If it is not possible to run IAS on the same computer as the domain controller or the computer that contains the global catalog, verify that you have an efficient domain and site topology, and place the IAS server on the same subnet as a domain controller or global catalog server.
-
Reduce the number of user accounts in each domain by redesigning your domain topology.
-
Add IAS proxy servers to load balance authentication and accounting between servers in remote RADIUS server groups.
-
Upgrade the hardware resources of the existing IAS servers.
-
Replace existing IAS servers with higher performance servers.
-
Reduce the level of detail recorded in IAS accounting. IAS accounting can record user authentication requests, accounting requests, and periodic data. Make sure you are logging only the amount of information you need to troubleshoot network access.
-
If you configure IAS accounting for SQL Server logging, install SQL Server Desktop Engine (MSDE 2000) on the IAS server, and log to MSDE 2000 instead of directly to SQL Server 2000 running on another computer. This configuration assists in preventing logging failure due to network hardware failure or heavy network traffic. Use a custom application, service, or component to periodically publish the accounting logs from the MSDE 2000 database on each IAS server to the master SQL Server 2000 database.
-
For wireless deployments, use PEAP-EAP-MS-CHAPv2 with fast reconnect. PEAP uses cached TLS keys during re-authentication with access points configured as RADIUS clients of a single IAS server. Cached authentication is critical for wireless deployments because wireless clients authenticate each time they move to and associate with a new access point. In addition to improving performance, PEAP fast reconnect significantly reduces the latency of authentication and the public key operation overhead on both the client and the RADIUS server.
-
Use the MaxConcurrentApi registry entry (HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Netlogon\ Parameters) to increase the number of multiplexed connections to the domain controller.
| Caution | Do not edit the registry unless you have no alternative. The registry editor bypasses standard safeguards, allowing settings that can damage your system, or even require you to reinstall Windows. If you must edit the registry, back it up first and see the Registry Reference on the Windows Server 2003 Deployment Kit companion CD or at http://www.microsoft.com/reskit. |
For more information, see "Remote access logging" in Help and Support Center for Windows Server 2003.
Optimize IAS Deployment in Large Organizations
You can optimize IAS performance in large organizations by doing the following:
-
If you are using remote access policies to restrict access for all but certain groups, create a universal group for all of the users to whom you want to allow access, and create a remote access policy that grants access for that universal group. If you have a large number of users on your network, create global groups within the universal group, and add the users to the global groups.
-
Use IAS as a proxy server and configure connection request policies to distribute authentication requests to remote RADIUS server groups based on the realm name portion of the user name. In this manner you can load balance traffic based on domain membership, and authentication requests are sent to a remote RADIUS server group that resides in the same domain where the user account is located.
-
Install IAS as a dedicated RADIUS server. If you choose not to run the IAS server on a domain controller with a global catalog, you can run it on a computer that has other services running on it, as long as the services are not resource-intensive.
In very large environments (such as an ISP with millions of remote access users and extremely heavy load conditions) that must process a large number of both authentication requests and accounting packets per second, you can optimize IAS performance by doing the following:
-
Using a faster domain controller to yield better throughput. The number of authentications per second depends on the hardware used for the domain controller.
-
Using separate IAS servers for authentication and accounting. IAS proxy servers can send all accounting requests to a specific remote RADIUS server group, while sending authentication requests to other groups. For more information, see "Configure accounting" in Help and Support Center for Windows Server 2003.
-
Running the IAS server on a domain controller with a global catalog. Choose this option if you have a high-latency connection between your IAS server and your domain controller, or between your IAS server and your global catalog, but you do not have problems with your IAS performance.
-
Increasing the number of concurrent authentication calls in progress at one time by using the MaxConcurrentApi registry entry. Keep in mind that if you assign too high a value to this registry entry, your IAS server can place an excessive load on your domain controller. Values from 2 to 5 provide the best performance.
For more information about the MaxConcurrentApi registry entry, see the Registry Reference on the Windows Server 2003 Deployment Kit companion CD or at http://www.microsoft.com/reskit.
| Caution | Do not edit the registry unless you have no alternative. The registry editor bypasses standard safeguards, allowing settings that can damage your system, or even require you to reinstall Windows. If you must edit the registry, back it up first and see the Registry Referenceon the Windows Server 2003 Deployment Kit companion CD or at http://www.microsoft.com/reskit. |
EAN: N/A
Pages: 146