6.4 Addressing Mechanisms
6.4 Addressing Mechanisms
In this section we will discuss some of the popular mechanisms for addressing networks: classful addressing, subnetting, variable-length subnetting, supernetting and classless interdomain routing (CIDR), private addressing and network address translation (NAT), and dynamic addressing. Although these mechanisms all basically share the same theme (manipulating address space), we will treat them separately to highlight their differences.
Although the concept of classful addressing is a bit outdated, we will discuss it here to give some background on newer mechanisms and to provide insight on the addressing process.
6.4.1 Classful Addressing
Classful addressing is applying predetermined mask lengths to addresses to support a range of network sizes. The result is a set of classes of addresses (A, B, C, D, and E), each of which supports a different maximum network size. A class identifier at the beginning (first octet) of the address determines its class. A Class A address is indicated when the first bit of the first octet is 0 (network addresses 1 through 127), a Class B address is when the first bit is 1 and the second bit is 0 (network addresses 128 through 191), and a Class C address is when the first bit is 1, the second bit is 1, and the third bit is 0 (network addresses 192 through 223). The structures of classes A, B, and C are shown in Figure 6.6. Classes D and E are not shown here; they are used only for special purposes (Class D is used for multicast) or are reserved.

Figure 6.6: Classful addressing uses traditional class boundaries to form Class A, B, or C addresses.
Classful addresses default to a natural mask, which coincides with the class boundary and reflects that class's network and host space allocations. The natural mask is different for each class. For Class A addresses, the natural mask is 255.0.0.0, indicating that the bits in the first octet represent the network for that class. Since the first bit of the first octet is used to indicate a Class A address and neither all 0s nor all 1s can be used as network addresses (they represent broadcasts), there can be 27 - 2, or 126, possible networks. The device (host) portion of the mask is the remaining three octets, so there can be up to 224 2 or more than 16 million possible device addresses per network for Class A networks. So, Class A provides for a few very large networks.
The natural mask for Class B addresses is 255.255.0.0, so the first two octets represent the network for that class. Since the first two bits are used to identify the class, there can be 214 - 2, or 16,382, possible networks. The device portion of the mask is the remaining two octets, so there can be up to 216 - 2, or 65,534, possible device addresses per network. So, Class B provides for tens of thousands of (still quite large) networks. At one time this seemed like a lot of networks, but not anymore.
The natural mask for Class C addresses is 255.255.255.0, so the first three octets represent the network for that class. Since the first three bits are used to identify the class, there can be 221 - 2, or slightly more than 2 million, possible networks. The device portion of the mask is the remaining octet, so there can be up to 28 - 2, or 254, possible device addresses per network. So, Class C provides for millions of small networks.
There are two additional classes of address space (Classes D and E) that are used or reserved for special purposes. Class D is used for multicast addresses, and Class E is reserved. Class D address spaces are calculated the same way as the other classes, so Class D is indicated when the first, second, and third bits of the first octet are 1 and the fourth bit is 0 (network addresses 224 through 239).
Classful addressing was the first step to add hierarchy to addressing. Although the three classes can address from very small to very large networks, there are some fundamental problems with this scheme. First, Class A and B networks can address large numbers of devices. As it turns out, networks do not scale well to the size of a Class A or B, so further hierarchy is needed. Furthermore, as Class A and B address space ran out, the use of Class C address space had an impact on routing in the Internet. Clearly, something more than classful addressing was needed.
Example 6.2: Determining Class and Natural Mask
For the network address from Example 6.1, 136.178.10.1, determine its class and natural mask. Recall from Example 6.1, the binary representation of 136.178.10.1:
![]()
Looking at the first three bits (from left to right) of the first octet, we see that they are 100. Since the first bit must be 0 for a Class A address, 136.178.10.1 is not Class A. The first two bits are 10, which are consistent with Class B; therefore, 136.178.10.1 is a Class B address. The natural mask for this address is the natural mask for Class B, 255.255.0.0.
There are limitations in allocating addresses based on Class A, B, and C boundaries. First, since there are relatively few Class A and B addresses, they have already been allocated. This leaves new networks with only Class C address space. Thus, a network may require many Class C addresses. Second, these class boundaries are not an efficient use of network addresses. Many networks require more addresses than a single Class C can provide yet are not large enough to justify a Class A or B, even if such network addresses were available. There are networks that have Class A or B addresses but can use only a small fraction of the total address space. What was needed was a more flexible method to match address space to the requirements of each network. This was accomplished by expanding the network mask to create subnets and variable-length subnets, as described next.
6.4.2 Subnetting
The next step in adding hierarchy to addressing is to allow a classful network address to be segmented into smaller sections. Subnetting (RFC 950) accomplishes this. Subnetting is using part of the device (host) address space to create another level of hierarchy. Changing the address mask increases the number of bits allocated to the network, creating the subnet. The resultant mask now includes a subnet mask, and the network segments that are created are termed subnets.
What is essentially being done in subnetting is that by changing the address mask to increase the number of bits allocated to the network, and thereby decreasing the number of bits allocated to devices, subnetting takes address space away from devices and gives it to the network.
Subnetting can be done on Class A, B, or C networks, although it is rare to subnet a Class C network (since there are only 254 addresses for devices anyway). The result of subnetting is a set of equal-sized subnets, where the length of the subnet mask determines the number of subnets and the size of each subnet. An example of this for Class B networks is shown in Figure 6.7.
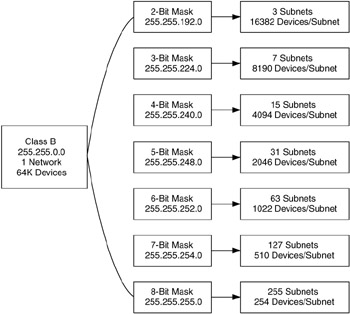
Figure 6.7: Masks and sizes for subnetting a Class B network.
Subnetting is done to add hierarchy to a network. A network in which all devices are addressed with the same network address can have problems scaling to a large number of devices. The term large is relative; although some networks can have problems with a few dozen devices, others can scale to hundreds of devices without problems. The problems are usually related to traffic loads and behavior at the link and physical layers. The behaviors of users, applications, and devices will be reflected in the traffic flows on the network, and the characteristics of these flows (including their sources and sinks) will have an impact on the scalability of the network. How network devices are configured at the link layer will affect how they communicate at that layer. Problems at the link layer, such as jabbering devices or broadcast/multicast storms, will affect scalability of the network. Subnetting helps reduce the problem by segmenting the network into subnets connected by routers. Routers terminate the link and physical layers, thus stopping problems in one subnet from affecting other subnets.
Subnet masks (and therefore subnets) are recognized only within that network. When routes to that network are advertised, the natural mask is used. This is desirable because subnetting is used to provide hierarchy within that network, so there is no need to reveal that hierarchy outside of the network.
Example 6.3: Creating Subnets
Subnet 129.99.0.0 into seven subnets. 129.99.0.0 is a Class B (how do we know this?) address with a natural mask of 255.255.0.0. To create subnets, we increase the mask into the third octet by enough bits to get seven subnets. From the previous figure (see Figure 6.7), we see that three bits will give us seven subnets, using an extended mask (subnet mask) of 255.255.224.0, as shown here.
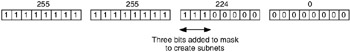
Each subnet is shown here in binary and dotted-decimal forms.
| Subnet 1: | 10000001 | 01100011 | 00100000 | 00000000 | | 129.99.32.0 | 255.255.224.0 |
| Subnet 2: | 10000001 | 01100011 | 01000000 | 00000000 | | 129.99.64.0 | 255.255.224.0 |
| Subnet 3: | 10000001 | 01100011 | 01100000 | 00000000 | | 129.99.96.0 | 255.255.224.0 |
| Subnet 4: | 10000001 | 01100011 | 10000000 | 00000000 | | 129.99.128.0 | 255.255.224.0 |
| Subnet 5: | 10000001 | 01100011 | 10100000 | 00000000 | | 129.99.160.0 | 255.255.224.0 |
| Subnet 6: | 10000001 | 01100011 | 11000000 | 00000000 | | 129.99.192.0 | 255.255.224.0 |
| Subnet 7: | 10000001 | 01100011 | 11100000 | 00000000 | | 129.99.224.0 | 255.255.224.0 |
6.4.3 Variable-Length Subnetting
Subnetting segments a network into a number of equal-sized subnets, which is often inefficient. If a goal of subnetting is to create subnets that are scaled to the sizes of groups (workgroups) in the organization so that a subnet can be allocated to each group, then it is desirable to have subnets of different sizes. Variable-length subnetting is subnetting in which multiple variable-length subnet masks are used, creating subnets of different sizes.
This practice allows for a better mapping of subnets to workgroups. For example, the following organization has a number of workgroups of varying sizes.
| Workgroup | Groups | Size/Group (Devices) |
|---|---|---|
| Engineering | 3 | 400 (1200 total) |
| Marketing | 1 | 1950 |
| Administration | 1 | 200 |
| Sales | 15 | 35–90 (1350 total) |
| Research and development (R&D) | 1 | 150 |
| Support | 22 | 10–40 (880 total) |
| Total | 43 | 5730 |
This organization has a Class B address (136.178.0.0, mask 255.255.0.0) and would like to give one subnet to each group. If we were to just use the natural mask, this network would support 65,534 devices, which is far more than needed. However, it is likely that the network would have problems scaling to that size. We cannot implement subnets of equal size, given the requirement of one subnet per group. To support the largest group (Marketing, with 1950 devices), we would need a 5-bit or smaller subnet mask. But this would give a maximum of 31 possible subnets (with a 5-bit mask). To have enough subnets, we would need a 6-bit or larger subnet mask, but then the size of the subnet would not be large enough for Marketing. By using variable-length subnetting, we can tailor the subnets to the sizes of the groups and how many subnets we need.
For this example we choose to use a combination of 4-bit and 8-bit subnet masks. With a 4-bit mask (255.255.240.0), we would have 15 subnets, each with a maximum of 4096 devices. This would be sufficient for Engineering and Marketing. The 8-bit subnet mask (255.255.255.0) provides subnets that can have a maximum of 254 devices each, sufficient for each of the groups is Sales, R&D, and Support.
The subnet allocations are as follows: The 4-bit mask (255.255.240.0) is used to allocate the following 15 subnets:
| 136.178.16.0 | 136.178.96.0 | 136.178.176.0 |
| 136.178.32.0 | 136.178.112.0 | 136.178.192.0 |
| 136.178.48.0 | 136.178.128.0 | 136.178.208.0 |
| 136.178.64.0 | 136.178.144.0 | 136.178.224.0 |
| 136.178.80.0 | 136.178.160.0 | 136.178.240.0 |
Not all of these subnets would be used at this time. We would allocate three subnets to Marketing (136.178.16.0, 136.178.32.0, and 136.178.48.0), one subnet to Marketing (136.178.64.0), and we probably should allocate one to Administration (136.178.80.0), as it would be close to the maximum number of devices for an 8-bit subnet.
For the 8-bit mask, we would take one of the 4-bit subnets and apply the 8-bit mask to it. We could take the next 4-bit subnet available (136.178.96.0) and apply an 8-bit mask (255.255.255.0), yielding the following 8-bit subnets:
| 136.178.97.0 | 136.178.102.0 | 136.178.107.0 |
| 136.178.98.0 | 136.178.103.0 | 136.178.108.0 |
| 136.178.99.0 | 136.178.104.0 | 136.178.109.0 |
| 136.178.100.0 | 136.178.105.0 | 136.178.110.0 |
| 136.178.101.0 | 136.178.106.0 | 136.178.111.0 |
These are all the 8-bit subnets between 136.178.96.0 and 136.178.112.0. Each of these subnets can support up to 254 devices. We would allocate 15 of these subnets (136.178.97.0 through 136.178.110.0) to Sales and the last one (136.178.111.0) to R&D. At this point we need to create more 8-bit subnets (22 subnets for Support), so we would repeat this procedure for the next two available 4-bit subnets (136.178.112.0 and 136.178.128.0). For 136.178.112.0:
| 136.178.113.0 | 136.178.118.0 | 136.178.123.0 |
| 136.178.114.0 | 136.178.119.0 | 136.178.124.0 |
| 136.178.115.0 | 136.178.120.0 | 136.178.125.0 |
| 136.178.116.0 | 136.178.121.0 | 136.178.126.0 |
| 136.178.117.0 | 136.178.122.0 | 136.178.127.0 |
and for 136.178.128.0:
| 136.178.129.0 | 136.178.134.0 | 136.178.139.0 |
| 136.178.130.0 | 136.178.129.0 | 136.178.140.0 |
| 136.178.131.0 | 136.178.136.0 | 136.178.141.0 |
| 136.178.132.0 | 136.178.137.0 | 136.178.142.0 |
| 136.178.133.0 | 136.178.138.0 | 136.178.143.0 |
The 22 subnets for Support would be (136.178.113.0 through 136.178.127.0, and 136.178.129.0 through 136.178.129.0). The remaining 4-bit and 8-bit subnets would be available for future growth.
6.4.4 Supernetting
As mentioned earlier, there are not many Class A and B networks (on the order of tens of thousands). As these network were allocated, it became necessary to allocate several Class C network addresses in place of a single Class A or B. Recall that there are millions of Class C networks that can be allocated.
What happens when Class C addresses are used in lieu of Class A or B addresses? Consider, for example, addressing strategy for a company with 10,000 devices. A single Class B could support up to 65,534 devices, which would be plenty for this company, but a Class B is not available, so Class C addresses are used instead. A single Class C can support up to 254 devices, so 40 Class C networks are needed (40 networks 254 addresses/network 10,160 total addresses).
When 40 Class C networks are allocated to this company (e.g., 192.92.240.0 through 192.92.279.0), routes to each network will have to be advertised to the Internet. Thus, instead of an advertisement for a single Class B network for this company, we now have advertisements for 40 Class C networks. Each route advertisement would be added to the routers in the Internet, using memory and processing resources. As you may imagine, the number of routes would grow exponentially, as would the memory and processing requirements in the routers. In fact, this was a problem in the Internet in the 1990s. There were predictions that the Internet would collapse in 1995, yet this did not happen. Through the ingenuity of Internet engineers at that time, a mechanism was found to alleviate this problem. The answer is supernetting.
Supernetting is aggregating network addresses by changing the address mask to decrease the number of bits recognized as the network. By decreasing the number of bits recognized as the network, we are in effect ignoring part of the network address, which results in aggregating network addresses.
Let's see how this works. We will consider a block of 16 contiguous Class C addresses (you will shortly see why 16 was chosen, and why it is contiguous), 192.92.240.0 through 192.92.255.0, with their natural mask 255.255.255.0:
| 192.92.240.0 | 192.92.248.0 |
| 192.92.241.0 | 192.92.249.0 |
| 192.92.242.0 | 192.92.250.0 |
| 192.92.243.0 | 192.92.251.0 |
| 192.92.244.0 | 192.92.252.0 |
| 192.92.245.0 | 192.92.253.0 |
| 192.92.246.0 | 192.92.254.0 |
| 192.92.247.0 | 192.92.255.0 |
You will notice that the first, second, and last octets of this group of addresses do not change. They are 192, 92, and 0, respectively. The third octet does change for each address. If we look at the binary representation of this octet for these addresses, we get Figure 6.8:
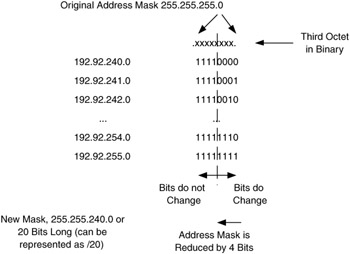
Figure 6.8: Modifying the address mask for supernetting.
Notice that the first four bits in this octet do not change, only the last four bits do. Also notice that the last four bits are represented in their full range of values, from (binary) 0000 to 1111. Therefore, if we choose to ignore the last four bits in this octet, we get a single address that represents the full range of 16 addresses. That address is 192.92.240.0 (the first address of the group), and its mask is 255.255.240.0 (the natural mask minus the last four bits). This mask is termed the supernet mask.
How does that work? Let's first look at 192.92.240.0 with its natural mask, 255.255.255.0. These addresses are shown in Figure 6.9 as decimal and binary representations.

Figure 6.9: IP address shown with natural mask.
When the natural mask is applied to the address, we get a single Class C network with 254 device addresses. If we look at this network with the new supernet mask, we get Figure 6.10:
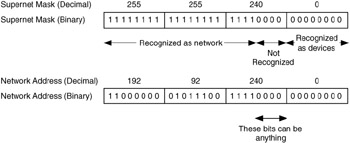
Figure 6.10: IP address shown with supernet mask.
The difference here is that, with the new supernet mask, the last four bits of the third octet are not recognized as part of the network, so they can be anything (0000 to 1111). As a result, we get a set of 16 addresses, ranging from 192.92.240.0 (where the last four bits of the third octet are 0000) to 192.92.255.0 (where the last four bits of the third octet are 1111). Thus, the single advertisement of 192.92.240.0 with supernet mask 255.255.240.0 is the equivalent of 16 advertisements for addresses 192.92.240.0 through 192.92.255.0.
Supernetting reduced the number of advertisements in the Internet and changed the way most people view addressing. If we can change the mask length to aggregate networks, why do we need class boundaries at all? The answer is that we don't. The term classless interdomain routing (CIDR) is used to denote the absence of class boundaries in network routing. The dotted-decimal notation for masks can be replaced by noting the length of the mask in bits. For example, the supernet mask 255.255.240.0 shown previously would be described as a 20-bit mask, and the combination of address and mask would be 192.92.240.0/20. The block of networks that are addressed in this way is termed a CIDR block. According to this convention, a single Class C network would have a mask length of 24 bits (/24), and a single Class B network would have a mask length of 16 bits (/16). When a mask is shown as a length in bits, it is called an address prefix.
By describing networks this way, we are really creating arbitrary hierarchies in the network. By changing the mask length, we can change the degree of aggregation of networks. This is now common practice in the Internet community.
There are some conventions that are followed in supernetting: The number of addresses in a CIDR block are powers of two, and the block of addresses is contiguous—that is, there are no holes in this address space.
The number of addresses in a CIDR block is a power of 2, based on the number of bits that are not recognized by the mask. If we look at 192.92.240.0 with a /24 (the natural mask), we get one network—192.92.240.0. With a /23 mask, we ignore the last bit of the third octet, and we get two networks—192.92.240.0 and 192.92.240.1. As you can see in Figure 6.11, this can continue for /22, /21, and so on. Each time we increase the number of possible networks by a factor of two.
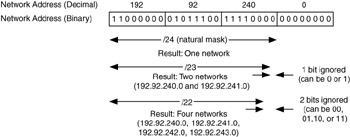
Figure 6.11: Address prefix size determines CIDR block size.
When the address space is not contiguous (i.e., there are one or more network addresses missing from the CIDR block), there is the potential for problems. In our discussion on supernetting, it should be clear that, in the process of changing the mask length, we are ignoring some of the bits in the address. The bits that are ignored can take on any value, and the result is that a range of networks is assumed. If one or more of the networks in that range is not part of the CIDR block (e.g., that network address is being used by somebody else), it will still be advertised as part of the range of addresses in that block.
For example, the advertisement 200.1.128.0/17 is equivalent to a range of 27, or 128, networks, from 200.1.128.0 to 200.1.255.0. If one of these addresses, say, 200.1.200.0/24, was already allocated to another customer, it will still be included in the advertisement 200.1.128.0/17. Does this mean that advertisements cannot have any such "holes" in them? Fortunately, this will still work. As was discussed at the beginning of this chapter, routers will choose the best match for a destination. Given a number of routes (in the router's forwarding table) that would work, the router will choose the one that is the longest match to the destination address of the packet. If the single network 200.1.200.0/24, which is in the CIDR block advertisement 200.1.128.0/17, is owned by somebody else, packets with a destination address of 200.1.200.0/24 would be forwarded to the 200.1.200.0 network, as it is a better (longer) match than 200.1.128.0/17.
6.4.5 Private Addressing and NAT
Private IP addresses are those that cannot be advertised and forwarded by network devices in the public domain. This was originally done to help with address space depletion in the Internet, for if networks that would normally be allocated public address space instead use private address space, those public addresses would remain available.
The Internet Engineering Task Force has defined in RFC 1918 three blocks of private address space:
-
10.0.0.0 through 10.255.255.255 (10/8 prefix)
-
172.16.0.0 through 172.31.255.255 (172.16/12 prefix)
-
192.168.0.0 through 192.168.255.255 (192.168/16 prefix)
There is a side benefit from using private addresses. It turns out that since these addresses are not advertised and forwarded in the Internet, this can provide a degree of security for that network. What is needed in order for this to work, however, is a mechanism to translate addresses from the private address space to the public address space. NAT is such a mechanism. NAT maps IP addresses between public and private spaces.
In translating between public and private address spaces, NAT creates bindings between addresses. These can be one-to-one address bindings (known as static NAT), one-to-many address bindings (known as dynamic NAT), and address and port bindings (known as network address port translation [NAPT]).
Often combinations of static, dynamic and NAPT bindings are used in a network. For example, dynamic NAT is often used for user devices, and static NAT is often used for servers.
EAN: 2147483647
Pages: 161