Lesson 8: Configuring Routing and Remote Access Security
Remote access enables clients to connect to your network from a remote location through various hardware devices including network interface cards and modems. Once clients obtain a remote access connection, they can use network resources such as files in the same way as they would use a client computer directly connected to your LAN. In this lesson, you learn how to configure security for remote access on your network.
After this lesson, you will be able to
- Create a remote access policy
- Configure remote access security
- Configure encryption protocols
- Configure authentication protocols
- Configure and troubleshoot network protocol security
Estimated lesson time: 60 minutes
Overview of Remote Access
Routing and Remote Access is the service that lets remote users connect to your local network by telephone. Remote access provides an opportunity for intruders to access your network; therefore, Windows 2000 provides multiple security features to permit authorized access while limiting opportunities for mischief. When a client dials a remote access server on your network, the client is granted access to the network if the following are true:
- The request matches one of the remote access policies defined for the server.
- The user's account is enabled for remote access.
- Client/server authentication succeeds.
After the client has been identified and authorized, access to the network can be limited to specific servers, subnets, and protocol types, depending on the remote access profile of the client. Otherwise, all services typically available to a user connected to a LAN (including file and print sharing, Web server access, and messaging) are enabled by means of the remote access connection.
Configuring Protocols for Security
Consider that someone can intercept a user name and password while a user is attempting to log on to the Routing and Remote Access server using techniques similar to a wiretap. To prevent this, Routing and Remote Access can use a secure user authentication method, which includes the following:
- Challenge Handshake Authentication Protocol (CHAP). CHAP is designed to address the concern of passing passwords in plaintext. CHAP is the most common dial-up authentication protocol used. Because the algorithm for calculating CHAP responses is well known, it is very important that passwords be carefully chosen and that they are sufficiently long. CHAP passwords that are common words or names are vulnerable to dictionary attacks if they can be discovered by comparing responses to the CHAP challenge with every entry in a dictionary. Passwords that are not sufficiently long can be discovered by persistence by comparing the CHAP response to sequential trials until a match to the user's response is found.
- Microsoft Challenge Handshake Authentication Protocol (MS-CHAP). MS-CHAP is a variant of CHAP that does not require a plaintext version of the password on the authenticating server. MS-CHAP passwords are stored more securely at the server but have the same vulnerabilities to dictionary and brute force attacks as CHAP. In MS-CHAP the challenge response is calculated with a Message Digest 4 (MD4)-hashed version of the password and the network access server (NAS) challenge. This enables authentication over the Internet to a Windows 2000 domain controller (or a Windows NT 4.0 domain controller on which the update has not been installed).
- Password Authentication Protocol (PAP). PAP passes a password as a string from the user's computer to the NAS device. When the NAS forwards the password, it is encrypted using the RADIUS shared secret as an encryption key. PAP is the most flexible protocol because passing a plaintext password to the authentication server enables that server to compare the password with nearly any storage format. For example, UNIX passwords are stored as one-way encrypted strings that cannot be decrypted. PAP passwords can be compared to these strings by reproducing the encryption method. Because it uses a plaintext version of the password, PAP has a number of security vulnerabilities. Although the RADIUS protocol encrypts the password, it is transmitted as plaintext across the dial-up connection.
- Shiva Password Authentication Protocol (SPAP). SPAP is a reversible encryption mechanism employed by Shiva remote access servers. A Windows 2000 remote access client can use SPAP to authenticate itself to a Shiva remote access server. A remote access client running Windows 32-bit operating systems can use SPAP to authenticate itself to a Windows 2000 remote access server. SPAP is more secure than PAP but less secure than CHAP or MS-CHAP. SPAP offers no protection against remote server impersonation.
Like PAP, SPAP is a simple exchange of messages. First, the remote access client sends an SPAP Authenticate-Request message to the remote access server containing the remote access client's user name and encrypted password. Next, the remote access server decrypts the password, checks the user name and password, and sends back either an SPAP Authenticate-Ack message when the user's credentials are correct, or an SPAP Authenticate-Nak message with a reason why the user's credentials were not correct.
- Extensible Authentication Protocol (EAP). EAP is an extension to PPP that allows for arbitrary authentication mechanisms to be employed for the validation of a PPP connection. With PPP authentication protocols such as MS-CHAP and SPAP, a specific authentication mechanism is chosen during the link establishment phase. Then, during the connection authentication phase, the negotiated authentication protocol is used to validate the connection. The authentication protocol itself is a fixed series of messages sent in a specific order. Architecturally, EAP is designed to allow authentication plug-in modules at both the client and server ends of a connection. By installing an EAP-type library file on both the remote access client and the remote access server, a new EAP type can be supported. This presents vendors with the opportunity to supply a new authentication scheme at any time. EAP provides the highest flexibility in authentication uniqueness and variations.

Practice: Using Security Protocols for a Virtual Private Network Connection
For a VPN to be secure, you need to use an appropriate security protocol. In this practice, you will configure a VPN to use the CHAP Authentication method.
Exercise 1: Enabling your Virtual Private Network (VPN) Server to use the CHAP Authentication Method
- Click Start, point to Programs, point to Administrative Tools, and then click Routing And Remote Access.
- Right-click the server name for which you want to enable authentication protocols, and then click Properties.
The Server Properties dialog box appears.
- In the Security tab, click Authentication Methods.
The Authentication Methods dialog box appears.
- In the Authentication Methods dialog box, select Encrypted Authentication, as illustrated in Figure 12.20, and then click OK.

Figure 12.20 Using the CHAP authentication method
- Click OK to close the Server Properties dialog box.
Creating Remote Access Policies
Routing and Remote Access and IAS both use remote access policies to determine whether to accept or reject connection attempts. In both cases, the remote access policies are stored locally. Policy is now dictated on a per-call basis.
With remote access policies, you can grant or deny authorization by time of day or day of the week, by the Windows 2000 group to which the remote access user belongs, by the type of connection being requested (dial-up networking or VPN connection), and so forth.
Local versus Centralized Policy Management
Because remote access policies are stored locally on either a remote access server or an IAS server, in order to centrally manage a single set of remote access policies for multiple remote access or VPN servers, you must do the following:
- Install the Windows 2000 IAS as a RADIUS server on a computer.
- Configure IAS with RADIUS clients that correspond to each of the Windows 2000 remote access or VPN servers.
- On the IAS server, create the central set of policies that all Windows 2000 remote access servers are using.
- Configure each of the Windows 2000 remote access servers as a RADIUS client to the IAS server.
After you configure a Windows 2000 remote access server as a RADIUS client to an IAS server, the local remote access policies stored on the remote access server are no longer used. Centralized management of remote access policies is also used when you have remote access servers that are running Windows NT 4.0 with the Routing and Remote Access Service (RRAS). You can configure the server that is running Windows NT 4.0 with RRAS as a RADIUS client to an IAS server. You cannot configure a remote access server that is running Windows NT 4.0 without RRAS to take advantage of centralized remote access policies.
Using Encryption Protocols
You can use data encryption to protect the data that is sent between the remote access client and the remote access server. Data encryption is important for financial institutions, law-enforcement and government agencies, and corporations that require secure data transfer. For installations where data confidentiality is required, the network administrator can set the remote access server to require encrypted communications. Users who connect to that server must encrypt their data, or the connection attempt is denied.
For VPN connections, you protect your data by encrypting it between the ends of the VPN. You should always use data encryption for VPN connections when private data is sent across a public network such as the Internet, where there is always a risk of unauthorized interception.
For dial-up networking connections, you can protect your data by encrypting it on the communications link between the remote access client and the remote access server. You should use data encryption when there is a risk of unauthorized interception of transmissions on the communications link between the remote access client and the remote access server. There are two forms of encryption available for demand-dial connections: Microsoft Point-to-Point Encryption (MPPE) and IP Security (IPSec).
- MPPE. All PPP connections, including Point-to-Point Tunneling Protocol (PPTP) but not including Layer 2 Tunneling Protocol (L2TP), can use MPPE. MPPE uses the Rivest-Shamir-Adleman (RSA) Cipher 4 (RC4) stream cipher and is only used when either the EAP-Transport Layer Security (TLS) or MS-CHAP (version 1 or version 2) authentication methods are used. MPPE can use 40-bit, 56-bit, or 128-bit encryption keys. The 40-bit key is designed for backwards compatibility and international use. The 56-bit key is designed for international use and adheres to United States encryption export laws. The 128-bit key is designed for North American use. By default, the highest key strength supported by the calling router and answering router is negotiated during the connection establishment process. If the answering router requires a higher key strength than is supported by the calling router, the connection attempt is rejected.
NOTE
For dial-up networking connections, Windows 2000 uses MPPE. - IPSec. For demand-dial connections using L2TP over IPSec, encryption is determined by the establishment of the IPSec security association (SA). The available encryption algorithms include Data Encryption Standard (DES) with a 56-bit key, and triple DES (3DES), which uses three 56-bit keys and is designed for high-security environments. The initial encryption keys are derived from the IPSec authentication process.
For VPN connections, Windows 2000 uses MPPE with the PPTP, and IPSec encryption with the L2TP.
Follow these steps to configure encryption for a dial-up connection:
- Click Start, point to Programs, point to Administrative Tools, and then click Routing And Remote Access.
- Under the server name, click Remote Access Policies.
- In the details pane, right-click the remote access policy you want to configure, and then click Properties.
- Click Edit Profile.
- In the Encryption tab, illustrated in Figure 12.21, specify settings as needed, and then click OK.
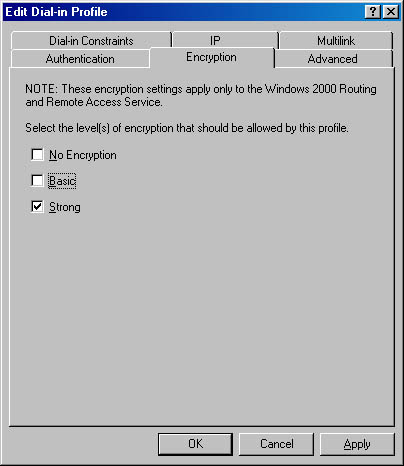
Figure 12.21 Setting the level of encryption
- Click OK to close the Policy Properties dialog box.
Lesson Summary
Remote access enables clients to connect to your network from a remote location using various hardware devices, including network interface cards and modems. Once a client obtains a remote access connection, he or she can use network resources, such as files, just as when the client computer is directly connected to the LAN. In Windows 2000 you create remote access policies and then configure them for security. You can set the level of encryption and dial-up permissions for remote access.
EAN: N/A
Pages: 244