12.2 Helper Applications and Plug-ins
| only for RuBoard - do not distribute or recompile |
12.2 Helper Applications and Plug-ins
With all of these documented examples (and more) of the damage that downloaded programs can do, why do people continue to download and run programs? One reason is that the web sites that people visit frequently require the downloads. Many web sites are authored with so-called "rich media" animations, interactive graphics, broadcast audio, streaming video clips that can only be viewed by using a particular program called a helper application or a plug-in. Although these programs are widely used, they are not without their risks.
12.2.1 The History of Helpers
The original web browsers could only display a limited number of media types, such as HTML, ASCII text, GIFs, and XBM files. When a web server attempted to download files with an unrecognized MIME type, the web browsers would save the file to the computer's hard disk and launch a registered helper application to process the downloaded data.
Helper applications proved to be a simple and clean way to extend the functionality of web browsers. When you click on a link to hear a song using RealAudio, for instance, your web browser downloads a small file and then gives this file to the RealAudio player. The file contains a pointer to another URL on the Internet from which the RealAudio player should actually download the song. Without this level of indirection, it would be necessary to either have the web browser download the entire song before playing it (as was common practice before the introduction of RealAudio), or else it would have been necessary to modify the web browser itself to make the RealAudio program work.
But helper applications have an important limitation: if a helper application wants to display information on the computer's screen, it has to display that information in its own window and not in the browser's window. Helper applications also can't ordinarily modify the way that a browser operates.
Plug-ins were introduced with Netscape Navigator as a simple way of overcoming the limitations of helper applications. A plug-in allows a third party to extend the functionality of a browser. One of the simplest uses for plug-ins is to replace helper applications used by web browsers. Instead of requiring that data be specially downloaded, saved in a file, and processed by a helper application, the data can be left in the browser's memory pool and processed directly by the plug-in. But plug-ins are not limited to the display of information. In the fall of 1996, Microsoft released a plug-in that replaced Netscape's Java virtual machine with its own. Network Associates distributes a plug-in that adds PGP email encryption to Netscape Communicator's email package. Macromedia's Flash and Shockwave technologies are implemented with plug-ins. Adobe has a plug-in that makes it possible to view Acrobat files directly in web browsers.
12.2.2 Getting the Plug-In
Traditionally, plug-ins have been manually downloaded by the web user. The plug-ins are then installed when the user runs a special installer or "setup" utility. The plug-in installer puts a copy of the plug-in into a special directory and registers the plug-in directly with the web browser. When new instances of the web browser are started, the program scans its list of registered plug-ins and the file types that each plug-in supports. If the browser downloads a file with a registered file type, the plug-in is automatically loaded into the browser's memory and started.
If the required plug-in is not present, Netscape can give the user the option of automatically downloading and installing the plug-in. In Navigator 2.0, the window that allowed people to install the plug-in had a button labeled "Plug-in Info." Clicking this button caused Navigator to switch to a web page describing the plug-ins currently available and linking to another web page containing Netscape's Plug-in Security warning:
Plug-in Security Implications
When running network applications such as Netscape Navigator, it is important to understand the security implications of actions you request the application to perform. If you choose to download a plug-in, you should know that:
* Plug-ins have full access to all the data on your machine.
* Plug-ins are written and supplied by third parties.
To protect your machine and its documents, you should make certain you trust both the third party and the site providing the plug-in.
If you download from a site with poor security, a plug-in from even a trusted company could potentially be replaced by an alternative plug-in containing a virus or other unwanted behavior.
...Copyright 1996 Netscape Communications Corporation
Unfortunately, most users didn't have the necessary tools or training to act upon Netscape's message. Confronted with this message, most users simply clicked past the warning page and downloaded the plug-in. Few realized that a plug-in can do far more damage than simply crashing their computer.
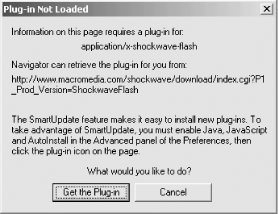
Later versions of Netscape did away with the plug-in security warning and just displayed a window with a button labeled "Get the Plug-in" (see Figure 12-2).
Figure 12-2. The Plug-in Not Loaded page for Netscape Navigator 6.0 suggests that the user enable Java, JavaScript, and AutoInstall, but it does not warn the user about the potential security risks of doing so or of downloading the plug-in itself.
Plug-ins for Internet Explorer are Windows dynamic linked libraries (DLLs) that are specially registered in the Windows registry. They are usually installed by small executable files that are downloaded using Internet Explorer. Thus, when you attempt to install an Internet Explorer plug-in, Internet Explorer displays the standard window that is displayed whenever an executable program is downloaded.
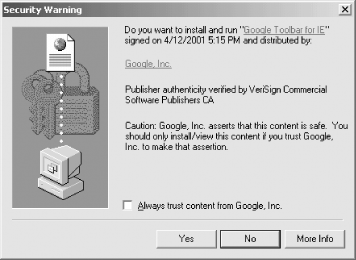
For example, Figure 12-3 shows the panel that IE displays when the Google Toolbar for Internet Explorer is downloaded. This executable is digitally signed using Microsoft's Authenticode technology (see Section 12.3 later in this chapter), so Internet Explorer can display the program's given name as well as the distinguished name on the certificate of the public key that is used to verify the signature. Microsoft's warning makes a lot more sense than Netscape's.
Figure 12-3. Internet Explorer displays this panel when the Google Toolbar for IE is downloaded
12.2.3 Evaluating Plug-In Security
Given the original warning from Netscape and the current warning from Microsoft, what is the proper procedure for evaluating a plug-in to determine if it is safe or not?
Fortunately, most plug-ins aren't hostile applications that will scan your hard drive and delete your files. Most well known plug-ins such as the plug-in for Adobe Acrobat or Macromedia's Flash are well behaved programs that do what they advertise and little more. Google, for instance, has two versions of its plug-in: one version that maintains your privacy, and another version that sends the URL of every web page you visit to Google's server so that it can display the "PageRank" of any web page you visit. The difference is clearly disclosed to users.
Security-conscious individuals should simply avoid downloading plug-ins that are not widely used on the Internet. Otherwise, you might end up like the victims in the Sexygirls.com case. But you also need to be sure that the copy of the Adobe Acrobat or Flash plug-in that you are downloading is actually being downloaded from the official Adobe or Macromedia site. Otherwise, you might think that you are downloading the Flash plug-in, but actually be downloading david.exe from Sexygirls!
Even after you have made the decision to download a well known plug-in, you need to be sure that you are actually downloading the plug-in that you think you are downloading! You also may wish to verify that no vulnerabilities have been discovered with the plug-in itself. There have been cases of vulnerabilities being found in widely used plug-ins that would allow an attacker to use the plug-ins to compromise the security of the plug-in's users.
There are many ways your computer might be damaged by a plug-in. For example:
-
The plug-in might be a truly malicious program, ready to damage your computer when you make the mistake of downloading it and running it. It might seek out credit card numbers, make your computer dial expensive phone numbers, or encrypt your hard disk and demand a ransom.
-
The plug-in might be a legitimate plug-in, but a copy might have been modified in some way to exhibit new dangerous behaviors. For example, the plug-in might change your default security settings, or disable your browser's ability to validate digital signatures.
-
There might not be a malicious byte of code in your plug-in's executable, but there might be a bug that can be misused by someone else against your best interests.
-
The plug-in might implement a general-purpose programming language that can subsequently be misused by an attacker.
Once you have downloaded and run a plug-in, there's really no way to protect your computer against these attacks. (Some vendors have developed what they claim are "sandboxes" for mobile code, but experience with these programs is not consistent.)
It is nearly impossible to determine if a plug-in has hidden security problems. That's because plug-ins are provided precompiled and without source code. Unless you work for the company that creates the plug-in, it is usually not possible to inspect the actual plug-in's source code. Instead, you must trust the company that makes the plug-in and hope the people there have your best interests at heart. As the Sexygirls.com case shows, that's not always a valid assumption.
What's worse, there is no safety in numbers: simply because a plug-in works well for others, that doesn't mean that the plug-in will work safely for you. It is fairly trivial to create a program that behaves one way for most computer users but another way for a particular target. Such a program could also be programmed to cover its tracks. If you are the victim of a targeted plug-in attack and you do notice a problem, you might be more likely to ascribe it to a passing bug or strange interaction because no one else will ever report it.
| only for RuBoard - do not distribute or recompile |
EAN: 2147483647
Pages: 194