ACS Reports
| ACS can provide numerous reports such as accounting reports, administrative reports, and system reports, among others. Some of these reports that ACS maintains might contain information from multiple sources and for multiple reasons. For example, ACS might log a failed password authentication attempt to the Failed Attempts log, and in the same log, you might find a failed attempt caused by an unknown AAA client attempting to communicate with ACS. This is where the third-party reporting programs, such as aaa-reports by Extraxi, SQL, or Microsoft Access can provide enhanced functionality by allowing you to pick the logs apart and see only what you want to see. Accounting ReportsACS also maintains TACACS+, RADIUS, and Voice over IP (VoIP) accounting reports, which contain records of successful authentications during selected time periods. In addition to logging successful authentications, these logs contain information such as time/date, username, type of connection, amount of time logged in, and bytes transferred. Accounting logs contain information about the use of remote access services by users. By default, these report logs are available in CSV format. With the exception of the Passed Authentications log, you can also configure ACS to export the data for these logs to an ODBC-compliant relational database. TACACS+ AccountingThe TACACS+ accounting report logs contain user sessions' stop and start times, AAA client messages with username, caller line identification information, and session duration. The TACACS+ accounting report is seen in Figure 12-10. Figure 12-10. TACACS+ Accounting Report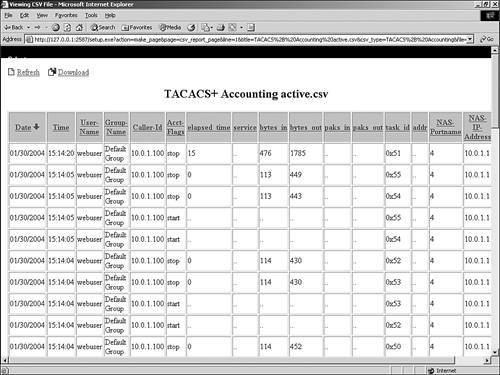 RADIUS AccountingRADIUS accounting files contain the following information: user sessions' stop and start times, AAA client messages with username, caller line identification information, and session duration. The RADIUS accounting report is seen in Figure 12-11. Figure 12-11. RADIUS Accounting Report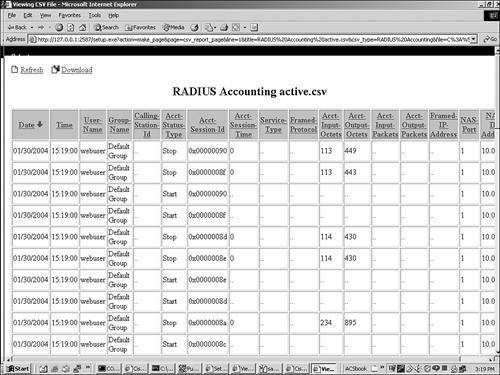 You can also configure ACS to include accounting for VoIP in this RADIUS accounting report log or in a separate VoIP accounting log. This is seen in the next section, "VoIP Accounting." VoIP AccountingAnother type of accounting report that ACS provides is for VoIP. This accounting information can be found in the RADIUS accounting report log or optionally in a separate VoIP accounting report log. You might want to send VoIP accounting to both report logs. These reports can be configured in the System Configuration page under the Logging link. VoIP accounting reports contain the following information:
As previously mentioned, you can configure ACS to include accounting for VoIP in this separate VoIP accounting log, in the RADIUS accounting log, or in both places. Failed Attempts ReportThe Failed Attempts report provides you with information related to authentication attempts that were not successful. From this report, you can gather information such as the username attempting to authenticate as well as the IP address that they made the attempt from. You also receive information to guide you in the direction you should look if authentication is not successful. An example of this would be a failed authentication attempt to an external database. In this situation, you receive a message similar to the following: External DB user invalid or bad password. In cases such as this, you might need to reset the user password in the external database or verify that the password entered is correct. Another example is seen in Figure 12-12. As you can see, authentication has failed for user admin. The reason authentication has failed is noted in the Authen-Failure-Code field. In this case, the CS in the report stands for CiscoSecure, so the password the user is entering is being matched to the ACS internal database and is invalid. Figure 12-12. Failed Authentications Report with Invalid CS Password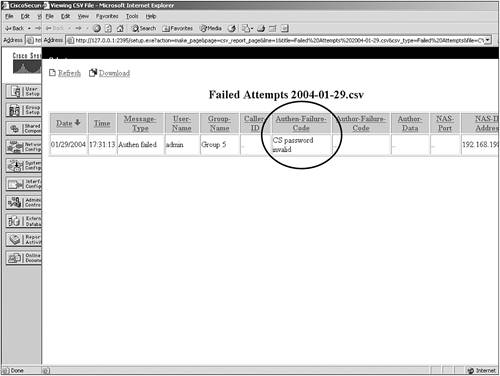 In the Failed Authentications report, you not only see failed authentications by users, but also remember that ACS authenticated the AAA clients that it communicates with using a shared secret key. In Figure 12-13, you see an example that is very common. In the example, the Authen-Failure-Code field tells us that there is a key mismatch. Note here that no user is listed in the User-Name field. This is because the key mismatch is between the AAA client192.168.198.128 and ACS. This caused the authentication between ACS and the AAA client to fail. Figure 12-13. Failed Authentications Report with Key Mismatch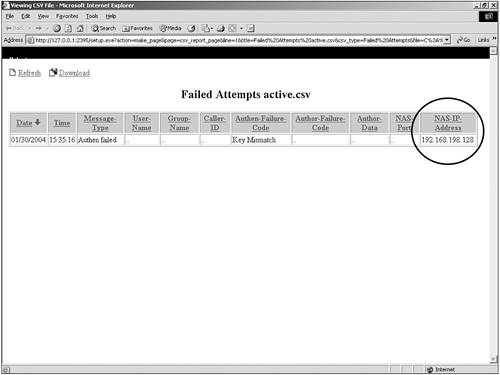 Passed Authentications ReportPassed Authentications gives you information about successful authentications. This report includes the following information:
An example of the Passed Authentications report is seen in Figure 12-14. Figure 12-14. Passed Authentications Report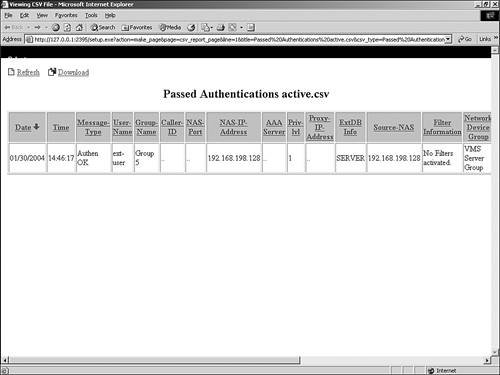 Administrative ReportsThree different administrative reports exist in ACS: TACACS+ Administration, Logged-in Users, and Disabled Accounts. Of the three reports, TACACS+ Administration is not dynamic. It records information as it happens and can be downloaded in CSV format. The other two reports are dynamic. TACACS+ Administration ReportThe administrative report contains information about all the TACACS+ commands requested during the period of time covered in the report. This report is used most often when you are using ACS to control access to network devices or when using command authorization sets. To use the TACACS+ Administration log, you must configure TACACS+ AAA clients to perform command accounting with ACS. The command authorization configuration is covered in Chapter 10, "Configuring Shared Profile Components." An example of the TACACS+ Administration Report is seen in Figure 12-15. Figure 12-15. TACACS+ Administration Report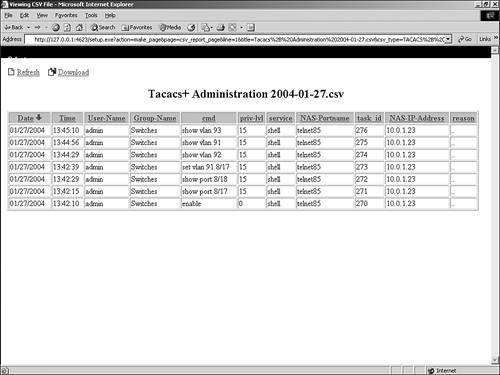 Logged-In Users and Disabled Accounts ReportsThe last two administrative reports are dynamic in nature, meaning that they populate based on the current status of ACS. The dynamic administrative reports have the following traits:
System ReportsSystem reports are report logs that record events directly related to ACS and actions it has taken. Examples of these reports are as follows:
These reports are discussed in further detail. ACS Backup and RestoreThe ACS Backup and Restore lists ACS backup and restore activity that ACS has taken. This report is not configurable in the interface. The information that gets populated in this log is placed there automatically when a backup occurs, whether it is a scheduled or manual backup. The report is also populated when a restore occurs. In Figure 12-18, you can see that a backup and a restore has taken place. You can also see the location of the dump file used for backup. Figure 12-18. Backup and Restore Report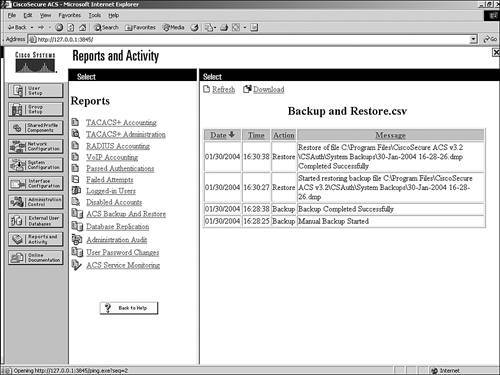 RDBMS SynchronizationThe RDBMS Synchronization report lists RDBMS Synchronization activity. This report cannot be configured. Database ReplicationThe Database Replication report lists database replication activity. This report also cannot be configured. In Figure 12-19, you can see an example of a replication that was unsuccessful. It is a good idea to check this report from time to time so that you can verify that replication is being performed successfully. Figure 12-19. Database Replication Report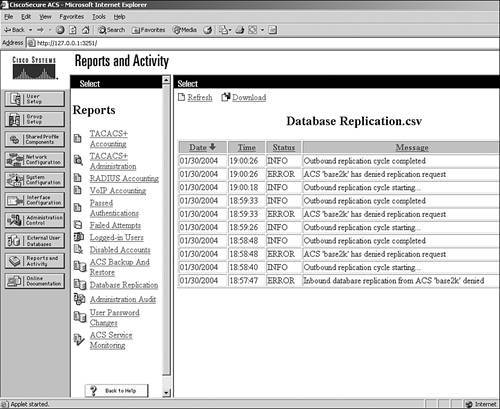 Administration AuditThe Administration Audit report lists actions taken by each system administrator, such as adding users, editing groups, configuring an AAA client, or viewing reports. You can see an example of the Administrative Audit report in Figure 12-20. Figure 12-20. Administrative Audit Report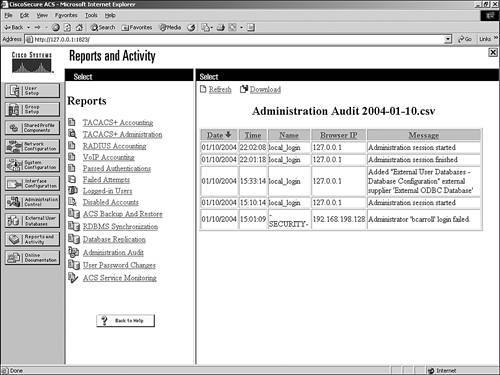 The Administrative Audit report can be modified. You can configure the administration audit report by following these steps:
To manage which Administrative Audit CSV files ACS keeps, do the following:
User Password ChangesThe User Password Changes report lists user password changes initiated by users, regardless of which password change mechanism was used to change the password. This log contains records of password changes accomplished by the CiscoSecure authentication agent, by the user changeable password HTML interface, or by Telnet session on a network device using TACACS+. It does not list password changes made by an administrator in the ACS HTML interface. You can configure this log. If you want ACS to generate a new User Password Changes log file at a regular interval, perform these steps:
If you want to manage which User Password Changes log files ACS keeps, follow these steps:
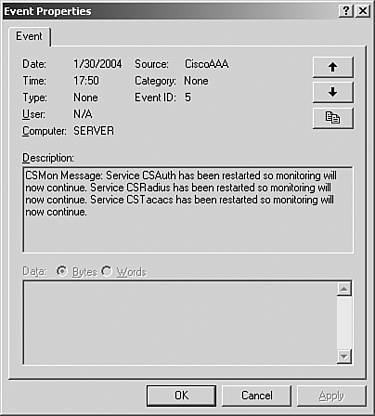
This completes the management of ACS User Password Changes log files. These log files can now be viewed in the Reports and Activity section of the ACS HTML interface. ACS Service MonitoringThe ACS Service Monitoring report is designed to report when the ACS services start and stop. This report is actually built by the CSMon process. When CSMon watches the ACS process and sees the services change, you get a message in this log. You can see an example of this report in Figure 12-21. Figure 12-21. ACS Service Monitoring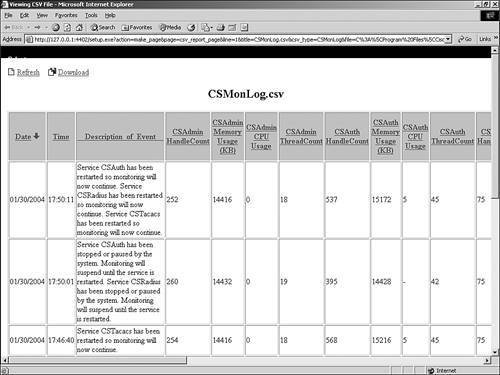 You can also configure this report to log to the Windows Event Log, which is discussed in the next section. To configure ACS service monitoring logs, perform the following tasks:
To instruct ACS to test the login process, follow these steps:
Now your ACS sends you an e-mail as well as logs events to the Windows Event log. To view the Windows Event log, you use the event viewer. Follow these steps to access the viewer in Windows 2000:
You can now view the service log messages in the Windows Event Viewer. Figure 12-22 shows what this would look like. Figure 12-22. ACS Service Monitoring in Windows Event Viewer
|
EAN: 2147483647
Pages: 173