9.3 Challenges and Recent Developments of Terminal Mobility
9.3 Challenges and Recent Developments of Terminal Mobility
At present, we experience the early stages of the emerging mobile Internet and the road has not yet been mapped out. The work that has been proposed from different research groups has largely addressed the fundamental issues of user mobility and many areas still remain relatively untouched. As can be expected, the industry lags behind the research community and there is no universal consensus on standards for mobility management.
To date, the predominant picture is to use Mobile IP for global addressing and specific link layer technologies for certain access technologies, e.g., GPRS Tunneling Protocol (GTP) in UMTS networks. However, because the rollout of mobile data networks has just begun, there is little experience with the difficulties and properties of mobile computing. Therefore, over the next few years as the mobile experience grows, many new issues will be revealed and problems that only have been touched by researchers to date will be thoroughly investigated.
9.3.1 Mobile IP Enhancements
Although Mobile IP is a simple and scalable solution for IP mobility, it suffers from performance and security problems and has a number of drawbacks, especially when serving users with high mobility and quality of service (QoS) expectations. Currently, there are many enhancements being proposed to Mobile IP, and these proposals are summarized in the following sections.
9.3.1.1 Route Optimization
Because all packets destined to a mobile host have to be routed through its HA, the chosen path can be significantly longer than the direct route. In a QoS supported mobile network, a longer path and the ensuing delay will produce a higher probability of call dropping and service refusal. To rectify this problem, the extension of route optimization in Mobile IP [19] provides a means for corresponding hosts to cache the actual location of a mobile host so that their packets can be tunneled to the mobile host directly.
The IPv6 base specification incorporates this idea. In addition, it replaces the tunneling mechanism with loose source routing that incurs less delivery overheads. [20] Thus, Mobile IPv6 overcomes the previously mentioned shortcoming of Mobile IPv4.
Another approach to this problem is to introduce the concept of a location server. Through the location server, the mobile host can update its current location and the CH can then query the server for the current location of a mobile user before transmitting a packet. Because the CH knows the actual location of an MH, both triangle routing and tunneling can be avoided. The associated call setup and signaling protocols can be implemented by either changing the Mobile IP protocol (e.g., MIP-LR [21]), setting up user agents at the application layer (e.g., the SIP with mobility support [22] and session layer mobility management [23]), or modifying the upper layer protocol (e.g., the MSOCKS [24] and the end-to-end approach to host mobility [25]).
It is worth noting that in order to enable optimal routing, all the above proposals have to introduce mobility awareness in the corresponding hosts. In particular, it requires either modifications to the IP protocol stack (binding cache followed by tunneling or loose source routing), or the addition of a location server and associated signaling protocols. Unfortunately, a global deployment of these enhancements will not be available in the near future.
9.3.1.2 Frequent Handover and Fast Location Updates
Mobile IP does not mandate fast handover and location updates, and hence there are several problems when serving highly mobile users. Each time a mobile host moves from one subnet to another, it needs to register its new location with the HA. Thus, if the visited network is some distance away from the home network, the signaling delay for reregistrations can become large and, consequently, many packets could be misrouted.
In addition, Mobile IP does not require a mobile host to inform its previous FA when it moves. Therefore, the previous FA is not able to reroute packets to the current FA. The extension of routing optimization in Mobile IP [26] allows the misrouted packets to be tunneled from the old to the new foreign agent. However, a drawback is that the mobility agents need to deal with many associated security issues.
Another disadvantage is that when intersubnet handovers occur, the mobile host obtains a new COA and thus packets destined to the mobile host will be encapsulated with a different tunnel header. Even if we assume that network resources can be dynamically reallocated across a QoS-capable Internet backbone during handovers, such rerouting and resource allocation processes may take a long time when the HA and the FA are far apart (see Figure 9.4(a)).
Lately, in addition the work on Mobile IPv6, there have been attempts in the Internet community to resolve these problems by introducing the concept of micro mobility. This concept is a promising approach to efficiently manage high user mobility within a single administrative domain (see Figure 9.4(b)). In micro-mobility schemes, (1) location updates within a domain are handled locally, thus avoiding frequent reregistrations across the Internet to the HA; and (2) by using a specific packet delivery scheme within the region, it prevents the costly reestablishment of end-to-end routing between the HA and the FA. This regional framework is normally coordinated by a domain gateway, which serves as the interchange entity for mobility management within a domain (micro-mobility) and mobility management across different domains (macro-mobility).
9.3.1.2.1 Micro Mobility
So far, only Mobile IP has been considered as the solution for macro-mobility management. On the other hand, many types of regional network architectures have been proposed for micro-mobility management. The proposals can be divided into four categories:
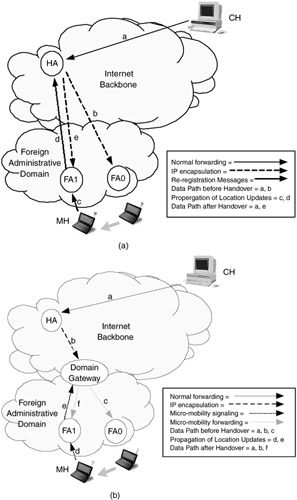
Figure 9.4: An illustration of the necessity of micro-mobility management in IP networking— (a) signaling and rerouting without the support of micro mobility; (b) signaling and rerouting with the support of micro mobility.
-
Cascade tunneling: This has been proposed as a solution to location registration latencies resulting from large distances between mobile hosts and servers. The solution is to perform registrations locally in the visited domain through a hierarchy of foreign agents with tunneling between them as described in Gustafsson and coworkers. [27] This approach reduces the number of signaling messages to the home network and shortens the signaling latency when moving from one foreign agent to another. However, the scheme requires the introduction of new registration messages for local mobility. Furthermore, a special gateway entity (gateway foreign agent) is required to handle and transform these regional registrations, and also to dynamically manage regional tunnels for the mobile host in both the forward and reverse directions. As a result, changes to both HA, FA, and MH are necessary. The changes ensure that the HA will always see the gateway foreign agent as the current location of a mobile host, regardless of which FA is serving the mobile host in the visited domain. The cascade tunneling approach also can be found in other proposals such as Regional Aware Foreign Agent [28] and Transparent Hierarchical Mobility Agents. [29] Instead of modifying those well-defined mobility agents of Mobile IP, these proposals introduce several new entities in their frameworks for handling the regional tunnel management.
-
Dynamic per-host routing: In a limited geographical area, i.e., between different subnets within the same management domain, the concept of dynamic per-host routing can be deployed as an alternative to regular IP routing. Problems associated with scalability and compatibility can be minimized because of the limited scope and single ownership of the management domain. With this scheme, IP addresses have no location significance inside the domain, and therefore neither tunneling nor address conversion is necessary during packet delivery. For example, HAWAII [30] uses path refresh messages to establish and update host-specific forwarding entries in routers between a gateway entity called the domain root router and the base station. In HAWAII, the role of a base station is twofold. First, it emulates an FA for replying to Mobile IP registration messages, thus making HAWAII entities transparent to mobile hosts that use Mobile IP. Second, it converts Mobile IP registration updates into HAWAII refresh messages, which in turn either revives or creates new forwarding entries in the routers, depending on whether a subnet handover has taken place. A similar approach is used in Cellular IP, [31] which also requires special routers that can set up, refresh, or modify host-specific forwarding entries using control packets. Besides control packets, routers utilize user data packets to refresh forwarding entries. To cater to large-scale deployment, special paging packets and paging caches are integrated in such a way that the gateway router can efficiently locate any idle mobile hosts.
-
Overlay routing: Regional overlay routing applies an overlay model where IP packets are either segmented or encapsulated into another packet format for local delivery. Because the data forwarding mechanism is no longer IP-based, address conversions need to be done at the gateway entity and the base stations, and all mobility support issues have to be resolved by the overlay network. One example of this approach is IP over Mobile ATM, [32] where IP packets are segmented into ATM cells and delivered by virtual connections between the gateway and a base station across a mobility-enabled ATM network. When the MH roams from one base station to another, its ongoing virtual connections need to be rerouted to its latest location. Another example of overlay routing that can be considered is multiprotocol label switching (MPLS) for Mobile IP, [33] where IP packets are encapsulated with a label that directs the forwarding path to a base station. In fact, this is very similar to the cascade tunneling scheme mentioned earlier, except that the regional IP tunnel is now replaced by a label-switched path across the MPLS domain.
9.3.1.3 Tunneling across QoS Domains
Even though tunneling has been adopted as the standard mechanism for redirecting packets in Mobile IP, there are certain constraints if it is used in conjunction with the currently developed QoS frameworks. For example, when the protocol that has been adopted by the IETF Resource Reservation Protocol (RSVP) is applied to Mobile IP it is assumed that RESV messages follow the inverse path of PATH messages. However, this is not the case for the base specification of Mobile IP which results in triangle routing.
Another incompatibility comes from the IP-in-IP encapsulation. The insertion of a tunnel header offsets the packet payload, which prevents the fields in the transport and higher layers from being accessed normally. When RSVP signaling messages enter a tunnel, they are encapsulated with a tunnel header that carries an IP-in-IP encapsulation rather than a router-alert option. Consequently, RSVP-capable routers cannot recognize the packets, and resources are not reserved accordingly.
Moreover, even if the required resources could be reserved, the intermediate RSVP routers will not be able to access port numbers correctly in order to distinguish data packets belonging to different flows. Therefore, it will not be possible to honor the per-flow state resource reservations.
To resolve these problems, an RSVP tunneling algorithm has been proposed in Terzis et al. [34] This scheme passes end-to-end RSVP messages transparently (i.e., without reservations) between tunnel endpoints and instead the tunnel ingress and egress nodes are responsible for generating additional RSVP signaling to reserve resources between them. When data packets arrive at the tunnel ingress node, they are wrapped with extra IP and UDP headers such that intermediate routers can apply a standard RSVP filter specification to map a packet to the appropriate reservation. Because the source and destination IP address and the destination UDP port number (being assigned as a constant value of 363) are identical for every flow inside the tunnel, a unique source UDP port number is used to differentiate packets from various flows within the tunnel. However, this approach results in further complicating both the signaling and encapsulation at the tunnel endpoints. Moreover, it considerably increases the overhead of transferring small packet payloads such as voice data.
RSVP is proposed to be used with and tightly connected to the Integrated Services (IntServ) architecture, and it is considered as the signaling protocol to be used with Differentiated Services (DiffServ) as well. [35] The same shortcomings when combining QoS and tunneling will apply to both the IntServ and DiffServ environments. In the case of a DiffServ infrastructure without RSVP signaling, tunneling poses fewer problems because the DiffServ code point (DSCP) can be copied forwards and backwards between the tunnel header and the original IP header when encapsulation and decapsulation take place. However, in certain networking scenarios when path- or source-dependent services are desirable, multiple field (MF) classification has to be invoked at the ingress and egress DiffServ routers. [36] Similar to RSVP-compliant routers without modifications, these DiffServ edge routers will not be able to access the higher layer information in the packet payload due to the extra location offset created by the tunnel header, thus MF classification cannot be performed properly.
9.3.1.4 Link Layer Assisted Handover Detection
The base specification of Mobile IP was designed to be independent of the underlying link layer technology. However, because of its passive approach to handover detection, the registration process when moving from one FA to another can be long enough to cause problems, especially for real-time communications and reliable data transfers using TCP. [37], [38]
Recently in the IETF, there have been at least two proposals that couple link layer functionality with Mobile IP in an attempt to minimize service disruption experienced by a mobile host when moving between foreign agents. In the Fast Handoffs draft, [39] the movement of an MH is anticipated from the link layer information, and simultaneous bindings are used to send multiple copies of packets to different potential foreign agents. In the FA Assisted Handoff draft, [40] the FA takes a proactive approach to manage handover events. When an FA is aware of a handover occurring at the link layer of its current cell, it sets up a mobile host's visitor entry and issues the handover messages on behalf of the mobile host to the next FA. As a result, packets can be forwarded from the current FA to the next FA prior to receiving a formal registration request at the network layer. Unfortunately, these handover proposals assume that the identity of the new FA is known to the MH. If there are multiple foreign agents appearing at the link layer, these proposals do not provide a solution to choose the one the mobile host will select.
9.3.1.5 Discussion of Mobile IP Enhancements
Future IP mobility frameworks need to consider the QoS constraints of active connections more closely when handling the usual requests of handover and rerouting. Several optimizations can be done to improve the overall mobility performance:
-
The handover latency could be improved significantly by tightly coupling the IP layer with the link layer to give "hints" of potential handovers.
-
It is beneficial to forward packets directly between the corresponding and mobile hosts, as it enables the resultant path to be optimized for quality of service. However, it is unclear if and when all corresponding hosts would become mobility aware to provide this service.
-
It would be advantageous to assign a gateway entity near the mobile host to handle micro-mobility. Techniques such as cascade tunneling, dynamic per-host routing, and overlay routing can be realized with such a gateway. However, it is still debatable as to which approach is the most appropriate. The most obvious consideration is that if tunneling is used to redirect packets in the future wireless Internet environment, its integration into the IntServ and DiffServ framework demands more attention and new solutions.
9.3.2 Higher-Layer Mobility Management
One of the visions of future mobile communication is that of a multiaccess environment in which terminals will be attached to several different overlaid access networks simultaneously. In a multiaccess scenario, it is possible to select network interfaces for separate connections. It is likely that users will have access to several different networked devices. If this becomes a reality, it is likely that future services will emerge where it is possible to hand over sessions between different terminals.
These functions and others are, at the very best, cumbersome to solve in the network layer and therefore some proposals have been made that enable these functions by performing IP mobility management in layers above the network layer.
The MSOCKS proposal [41] places the mobility management function in the transport layer. This proposal is optimized for local mobility management within a single access network. The mobility management is carried out through splicing different socket endpoints together in the kernel of an intermediate node. The binding between different sockets is updated as clients move around and make address updates.
Another proposal, Session Layer Mobility Management (SLM) [42] places mobility management in a layer above the transport layer. This proposal lifts transport protocol dependency by maintaining states outside of sockets. This way, the data delivery can be totally separated from IP addresses and even socket endpoints. This in turn enables easy integration of intermediate nodes such as PEPs and handover between different devices. SLM uses a location server for both users and terminals; this way, it is possible to resolve user identifiers to terminals and to follow these terminals as they move and change addresses.
A final proposal [43] advocates changes to the TCP stack on end hosts to include mobility support. As is the case with MSOCKS, this proposal is transport-protocol-specific, but the mobility management is carried out end-to-end without requiring any intermediate node.
All these proposals require significant changes to end systems. However, it can be argued that software updates are necessary in any case, and that this is an ongoing process. If IPv6 is to be implemented or if RSIP is to be used, end hosts have to be updated. Similarly, if QoS support will be offered in access networks, end hosts will have to be upgraded with this support.
9.3.3 Enhancements to Support Conversational Multimedia
Traditional circuit switched telephony networks were designed and optimized to support voice services. Contrary to this, the packet-switched data network paradigm introduces a network that is able to support a variety of services and is optimized for maximum utilization. QoS management is an important building block to support classes of services with strict requirements in terms of parameters such as bandwidth, delay, and jitter from the network. In a fixed networking environment, resource reservations will suffice because the network behavior is predictable, but a wireless link will always suffer from varying conditions due to factors such as noise, handover latency, and overcrowded cells. However, interactive and especially conversational media require predictable network behavior even when the host is mobile.
The measures taken to alleviate these problems in mobile networks can be divided into two orthogonal classes, proactive and reactive. Proactive measures try to predict the needs of applications and make advance measures on their behalf. Network resource reservation is one of the measures in this category, but at handover QoS management has to be extended with additional functions to guarantee a smooth transition to the new cell.
9.3.3.1 Advance Resource Reservation
It is generally difficult to promise a specified level of QoS to mobile uses in mobile environments, because there may not be enough resources in the part of the network into which the mobile user is moving. Moreover, during handovers the ongoing traffic is likely to be disrupted, which can violate some of the previously agreed upon QoS parameters such as packet delay, jitter, and loss.
To date, there have essentially been two methods proposed to make QoS support more mobility aware. The first method focuses on the preallocation of network resources in locations where the mobile host is likely to visit. Preallocation can improve the continuity of a connection after a move, and reduce packet losses and latency of resource allocation. However, preallocation requests can fail under severe network congestion because there are simply no resources available for reservation. Moreover, even after preallocation, signal fluctuations of the wireless link can contribute to the failure of QoS guarantees. Under such conditions, it becomes necessary to take an alternative approach.
The second approach emphasizes the adaptivity of end systems, where their application, middleware or proxy, reacts to the changes of network resources caused by wireless channel fading and user mobility. This functionality can be achieved by means of session customization at various places. In the Internet environment, adaptive end systems have to rely on mechanisms that probe the network in order to avoid congestion. Unfortunately, this action is likely to cause traffic interruptions before congestion can be avoided on a long-term basis.
From this discussion, we believe that the first method (i.e., advance reservation) is a proactive approach to deliver some level of QoS guarantees (at least statistically) to the mobile users, whereas the second method (i.e., end system adaptivity) is a reactive approach to cope with changes of QoS and, as such, they are complementary.
9.3.3.1.1 Current Approaches of Advance Reservation
Advance reservation needs to deal with two nontrivial problems, namely, how to configure resources in advance, and where to preallocate resources for mobile devices.
How to Configure Resources in Advance when Mobile: Advance reservation was originally considered in Wireless ATM research. [44], [45], [46], [47] Because of the recent interest in providing mobile QoS in an IP environment, the research community has addressed this issue using a combination of Mobile IP and IntServ models. Based on the topology used for reserved data paths, these proposals can be classified into three categories as shown in Figure 9.5.
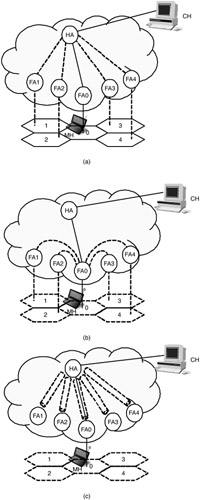
Figure 9.5: Various schemes for resource preallocation— (a) preconfigured anchor rerouting; (b) preconfigured path extensions; (c) preconfigured tunneling tree.
-
Preconfigured anchor rerouting: The MRSVP protocol [48] is an example of preconfigured anchor routing. In MRSVP, an MH specifies and dynamically maintains a set of locations (known as the MSPEC), from which it wants to make advance reservations to its HA (i.e., the anchor point). Special routing entities, called RSVP proxy agents, are provided at the locations specified in the MSPEC to make reservations on behalf of the mobile host. To allow for better link utilization, reservations made by these proxy agents allow resources to be temporarily borrowed by lower priority services. The reservations are either classified as active or passive, depending on whether the reserved resources are strictly used for a data flow or if they can be temporarily borrowed by other services. Of all proxy agents associated with an MSPEC, only the one currently serving the mobile host is allowed to make active reservations. The others will remain capable of making passive reservations until the mobile host moves into their wireless region. Similar mechanisms also can be found in other proposals such as RSVP-A [49] and Mobile Extensions to RSVP. [50]
-
Preconfigured path extensions: An example of preconfigured path extensions is Advanced Reservation Signaling. [51] This scheme uses a concept of passive reservations similar to MRSVP. However, instead of making multiple reservation paths connecting the HA with other foreign agents, the advance reservation signaling simply extends the existing RSVP data path from the current position of a mobile host to all its adjacent base stations.
-
Preconfigured tunneling tree: The proposal in Terzis and coworkers [52] is an example of preconfigured tunneling tree schemes. It does not rely on the notion of passive reservations. Instead, it requires RSVP-capable tunnels [53] to be established between the HA and other foreign agents. Unlike ordinary IP encapsulations, these RSVP tunnels are preprovisioned with certain levels of resources while accommodating multiple end-to-end RSVP sessions. When the resources consumed by mobile hosts visiting an FA exceed the reserved amount, the FA can request an incremental block of resources to be added to the RSVP tunnel.
Where to Preallocate Network Resources for Mobile Devices: It is difficult to determine where to preallocate resources, because of the difficulties of predicting user movements. Despite this, many resource preallocation algorithms have been proposed in the literature as an attempt to safeguard the QoS agreements for mobile services. The algorithms can be classified into three main categories.
-
Neighborhood-based allocation: These schemes preallocate network resources between an anchor node and a set of base stations surrounding the MH. The number of base stations involved in the preallocation process depends on how far ahead in time the network is willing to support a mobile service. For example, Virtual Connection Tree [54] configures resources in advance between a root switch and each base station in the management domain upon the admission of a call. This implies that the network is willing to support this mobile host as long as it stays within the domain, but the network also may have low utilization of resources. In contrast, Advanced Reservation Signaling [55] reserves resources only between a, MH's current location and all adjacent cells. Thus the network guarantees continuity of services after the next handover, but its further commitments are subject to successful reservations at the new neighboring cells.
-
History-based allocation: Through modeling and simulation, many proposals have shown that the user mobility history can be helpful in predicting the future movements of a mobile host. Depending on the service commitment to mobile users, these proposals preallocate resources at various levels in advance along the predicted path. For instance, in order to obtain mobility-independent service guarantees, MRSVP and other similar protocols attempt to make resource reservations at each location a mobile host may visit during the lifetime of a session. The Shadow Cluster concept, [56] on the other hand, estimates an MH's future location in the short term rather than the long term. Based on the probabilities of previous visits and the current trajectory of a mobile host, network resources are reserved near its present location and along its direction of travel. A less-ambiguous scheme can be found in the Profile-Based Next-Cell Prediction, [57] where resources are reserved only at the most-likely visiting cell, and further QoS commitments depend on the reservation process after the next handover. It is noticeable that the further ahead a scheme tries to predict the movement, the more likely it is to support the lifetime of a session. However, this is achieved at the expense of overall network utilization because of poor prediction accuracy.
-
Coarse-grained allocation: This scheme does not reserve resources on a per-user or per-cell basis, but works on a logical model called the Virtual Bottleneck Cell, [58] which treats a cluster of base stations as an aggregate virtual system. We believe that by controling the parameters and functions of a virtual bottleneck cell, the QoS agreements at each base station inside the cluster can be satisfied, even in environments with heterogeneous demands among base stations. However, it is not obvious how to decide the boundary of a virtual bottleneck cell, so that it is large enough for users to stay for a sufficient duration but small enough to accurately reflect the characteristics of underlying base stations. Moreover, because of its design philosophy, it is difficult to integrate this aggregated admission control with flow-specific mobility protocols such as MRSVP or Advanced Reservation Signaling.
9.3.3.1.2 Discussion of Advance Reservation Issues
Advance reservation should make a compromise between the continuity of QoS support and the risk of overreserving resources in the mobile network. The coarsegrained allocation appears to be a scalable solution to this problem, but the feasibility of aggregated functions and the scope of a virtual bottleneck cell both require further investigations. The neighborhood-based allocation is the simplest scheme to implement. However, resources are likely to be oversubscribed because mobile users are seldom moving randomly in real life. By applying user mobility patterns, the history-based allocation scheme reserves resources in selective surrounding cells, and thereby attempts to minimize the probability of overreserving resources in the mobile network. This view has been supported by simulation results from various studies, [59], [60], [61] but its usefulness in real life cannot be fully verified unless the actual user mobility in wireless networks is better understood. [62]
9.3.3.2 Reactive Enhancements to Support Multimedia Delivery
The second class of measures that can be taken to increase QoS in a mobile environment is reactive measures. These are measures that react when the network characteristics fail to meet the requirements of the application. If the proactive measures work properly, there is no need for reactive measures because the application requirements would be met and therefore the two classes of measures are orthogonal.
The most commonly proposed reactive measure is to make the applications elastic through adaptation. For example, the adaptive multirate (AMR) codec in UMTS networks measures the available data rate due to packet loss and sets the encoding parameters accordingly. In this way, the voice quality can be degraded but still be continuous when the signal quality goes down. The proactive alternative, to rely only on resource reservation, means that resources will have to be overreserved in order to maintain a quality buffer for the codec or the voice output will be intermittent when the network fails to meet the codec demands.
The User Services Assistant (USA) [63] architecture takes this a step further. The architecture introduces a reactive QoS manager through which users can start and register application sessions and subsequently maintain them. USA allows users to make initial resource reservations, but rather than making hard reservations for maximum usage, minimum reservations are made and the decision of when to react to low quality is left to the user. Users indicate dissatisfaction to the manager, which then proposes adaptations to improve the quality of the session. The adaptations can then range from lowering encoding rate or increasing reservations to inserting transcoding functions or protocol translators in the data path.
Thus, USA integrates both proactive and reactive QoS management into the one architecture. Initially, the proactive measure of resource reservations takes place, and subsequently when a user indicates that the QoS level is too low, reactive measures take place. The steps can take place completely independently because the two measures are orthogonal and complementary.
[19]Perkins, C. and Johnson, D., "Route Optimization in Mobile IP," IETF Internet draft, Nov. 2000, work in progress.
[20]Johnson, D. and Perkins, C., "Mobility Support in IPv6," IETF Internet draft, May 2002, work in progress.
[21]Jain, R. et al., Mobile Internet Access and QoS Guarantees Using Mobile IP and RSVP with Location Registers, Proc. IEEE ICC'98, June 1998.
[22]Wedlund, E. and Schulzrinne, H., Mobility Support using SIP, Proc. ACM WoWMo'99, Aug. 1999.
[23]Landfeldt, B. et al., SLM, A Framework for Session Layer Mobility Management, Proc. IEEE ICCCN, Oct. 1999.
[24]Maltz, D. and Bhagwat, P., MSOCKS: An Architecture for Transport Layer Mobility, Proc. IEEE INFOCOM'98, Mar. 1998.
[25]Snoeren, A. and Balakrishnan, H., An End-to-End Approach to Host Mobility, ACM/IEEE Mobicom'00, Aug. 2000.
[26]Perkins, C. and Johnson, D., "Route Optimization in Mobile IP," IETF Internet draft, Nov. 2000, work in progress.
[27]Gustafsson, E., Jonsson, A., and Perkins, C., "Mobile IP Regional Registration," IETF Internet draft, Mar. 2001, work in progress.
[28]Foo, S. and Chua, K.C., Regional Aware Foreign Agent Scheme for Mobile-IP, Proc. MoMuC'99, Nov. 1999.
[29]McCann, P. et al., "Transparent Hierarchical Mobility Agents (THEMA)," IETF Internet draft, Mar. 1999 (outdated).
[30]Ramjee, R. et al., IP-based access network infrastructure for next-generation wireless data networks, IEEE Personal Communications, 7 (4), 2000.
[31]Campbell, A. et al., Design, implementation, and evaluation of Cellular IP, IEEE Personal Communications, Aug. 2000.
[32]Acharya, A. et al., Mobility support for IP over wireless ATM, IEEE Personal Communications, Apr. 1998.
[33]Zhong, R. et al., "Integration of Mobile IP and MPLS," IETF Internet draft, June 2000 (outdated).
[34]Terzis, A. et al., "RSVP operation over IP tunnels," IETF RFC 2746, Jan. 2000.
[35]Bernet, Y. et al., "A Framework for Integrated Services Operation over DiffServ Networks," IETF RFC 2998, Nov. 2000.
[36]Black, D., "Differentiated Services and Tunnels," IETF RFC 2983, Oct. 2000.
[37]Fikouras, N. et al., Performance of TCP and UDP during Mobile IP Handoffs in Single-Agent Subnetworks, Proc. IEEE WCNC'99, Sep. 1999.
[38]Fladenmuller, A. and De Silva, R., The effect of mobile IP handoffs on the performance of TCP, ACM/Baltzer MONET, 4 (2), 1999.
[39]El Malki, K. and Soliman, H., "Fast Handoffs in Mobile IPv4," IETF Internet draft, Sep. 2000, work in progress.
[40]Calhoun, P. et al., "Foreign Agent Assisted Hand-off," IETF Internet draft, Nov. 2000, work in progress.
[41]Maltz, D. and Bhagwat, P., MSOCKS: An Architecture for Transport Layer Mobility, Proc. IEEE INFOCOM'98, Mar. 1998.
[42]Landfeldt, B. et al., SLM, A Framework for Session Layer Mobility Management, Proc. IEEE ICCCN, Oct. 1999.
[43]Snoeren, A. and Balakrishnan, H., An End-to-End Approach to Host Mobility, ACM/IEEE Mobicom'00, Aug. 2000.
[44]Liu, G. and Maguire, G. Jr., A class of mobile motion prediction algorithms for wireless mobile computing and communications, ACM/Baltzer MONET, 1 (2), 1996.
[45]Levine, D., Akyildiz, I., and Naghshineh, M., A resource estimation and call admission algorithm for wireless multimedia networks using the shadow cluster concept, IEEE/ACM Trans. Networking, 5 (1), Feb. 1997.
[46]Oliveira, C., Kim, J., and Suda, T., An Adaptive Bandwidth Reservation Scheme for High-speed Multimedia Wireless Networks, IEEE JSAC, 16 (6), Aug. 1998.
[47]Liu, T., Bahl, P., and Chlamtac, I., Mobility modeling, location tracking, and trajectory prediction in wireless ATM networks, IEEE JAC, 16 (6), Aug. 1998.
[48]Talukdar, A., Badrinath, B., and Acharya, A., MRSVP: A resource reservation protocol for an integrated services network with mobile hosts, to appear in ACM/WINET, May 1999.
[49]Pajares, A. et al., An Approach to Support Mobile QoS in an Integrated Services Packet Network, Proc. IQWiM Workshop, Apr. 1999.
[50]Awduche, D. and Agu, E., Mobile Extensions to RSVP, Proc. IEEE ICCN'97, 1997.
[51]Mahadevan, I. and Sivalingam, K., Architecture and experimental results for quality of service in mobile networks using RSVP and CBQ, ACM/Baltzer Wireless Network, 6 (3), July 2000.
[52]Terzis, A., Srivastava, M., and Zhang, L., A Simple QoS Signaling Protocol for Mobile Hosts in the Integrated Services Internet, Proc. IEEE INFOCOM'99, Mar. 1999.
[53]Terzis, A. et al., "RSVP operation over IP tunnels," IETF RFC 2746, Jan. 2000.
[54]Acampora, A. and Naghshineh, M., An architecture and methodology for mobile-executed handoff in cellular ATM networks" IEEE JACS, 12 (8), Oct. 1994.
[55]Mahadevan, I. and Sivalingam, K., Architecture and experimental results for quality of service in mobile networks using RSVP and CBQ, ACM/Baltzer Wireless Network, 6 (3), July 2000.
[56]Levine, D., Akyildiz, I., and Naghshineh, M., A resource estimation and call admission algorithm for wireless multimedia networks using the shadow cluster concept, IEEE/ACM Trans. Networking, 5 (1), Feb. 1997.
[57]Bharghavan, V. and Mysore, J., Profile Based Next-Cell Prediction in Indoor Wireless LANs, Proc. IEEE SICON'97, Apr. 1997.
[58]Jain, R., Sadeghi, B., and Knightly, E., Toward Coarse-Grained Mobile QoS, Proc. ACM WoWMoM'99, Aug. 1999.
[59]Oliveira, C., Kim, J., and Suda, T., An Adaptive Bandwidth Reservation Scheme for High-speed Multimedia Wireless Networks, IEEE JSAC, 16 (6), Aug. 1998.
[60]Levine, D., Akyildiz, I., and Naghshineh, M., A resource estimation and call admission algorithm for wireless multimedia networks using the shadow cluster concept, IEEE/ACM Trans. Networking, 5 (1), Feb. 1997.
[61]Ramanathan, P., Sivalingam, K., Agrawal, P., and Kishore, S., "Dynamic Resource Allocation Schemes During Handoff for Mobile Multimedia Wireless Networks," IEEE/JSAC, 17(7), July 1999, pp. 1270–1283.
[62]Chan, J. et al., Integrating Mobility Prediction and Resource Pre-allocation into a Home-Proxy Based Wireless Internet Framework, Proc. IEEE ICON 2000, Sep. 2000.
[63]Landfeldt, B., Seneviratne, A., and Diot, C., User Services Assistant: An End-to-End Reactive QoS Architecture, Proc. IWQOS98, Napa, California, 1998.
EAN: 2147483647
Pages: 239