Stateful IPsec VPN High-Availability Alternatives
| Site-to-Site IPsec HA can be designed to reconverge quicker upon failover when a stateful design alternative is used. Recall that in stateless IPsec failover, there is a reconvergence delay directly attributable to rebuilding IPsec SAs with the redundant router upon failover. Stateful IPsec HA builds the appropriate entries in the redundant VPN gateway's SADB in advance and employs a mechanism to accurately maintain state parity between the active and standby VPN gateways, thereby effectively precluding the need for IPsec to renegotiate Phase 1 and Phase 2 SAs upon failover. We will now explore the additional components required for an IPsec VPN design with stateful local High Availability. Solution Overview for Stateful IPsec High AvailabilityThe solution for stateful HA requires all of the same physical components as a stateless solution, but it allows for additional redundancy at both ends of the IPsec VPN tunnel. In the previous stateless HA examples, our design discussion only involved the termination of the IPsec VPN tunnel at a redundant point (the HSRP virtual IP address), while the origination of the VPN tunnel was sourced from a nonredundant point (the physical interface on 2651XM-VPNA, 2651XMVPNB, and 2651XM-VPNC). In our discussion of stateful IPsec HA designs, we will discuss a design in which the IPsec VPN tunnels are both sourced from and terminated on statefully redundant HSRP virtual interfaces. The stateful design in Figure 6-5 illustrates this behavior. Notice that in Figure 6-3 and Figure 6-4, only the concentrating end of the VPN design (domain D) incorporated redundant termination of the IPsec tunnels from domains A, B, and C on an HSRP virtual interface, while in Figure 6-5, a stateless IPsec HA design has been incorporated at all domains to allow for redundant origination and termination of the IPsec VPN tunnel at domains A, B, and C. Figure 6-5. Stateful IPsec High Availability Topology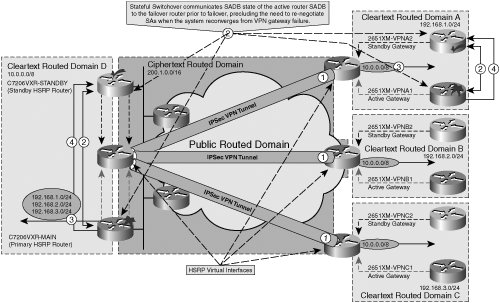 The following list briefly describes the stateful failover of the IPsec VPN tunnel illustrated in Figure 6-5:
In this section, we will discuss in greater detail the step-by-step failover of an IPsec VPN tunnel in a stateful HA design, but first, we will look at some of the key components of a stateful IPsec HA design that differ from a stateless IPsec redundancy designs. HSRP and RRIThe stateful HA designs discussed in this chapter all use HSRP and RRI in the same way that the stateless designs do. Therefore, the reconvergence delay attributable to reconvergence of HSRP and re-injection of RRI routes is similar between stateful and stateless designs. Additionally, HSRP timers and RRI configurations should be similar between stateful and stateless designs. The key ingredient of a stateful design, which is also the key differentiator between stateful and stateless local IPsec HA alternatives, is the communication of state between the active and standby IPsec gateways configured for tunnel termination on the HSRP interface. This communication requires a function called Stateful Switchover (SSO), which we will now explore. Stateful Switchover (SSO) and IPsec High AvailabilitySSO is the primary differentiator between stateful and stateless HA designs outlined in this chapter. Unlike stateless IPsec HA designs in which there is no sharing and synchronization of IPsec state between the redundantly configured IPsec gateways, there is a synchronization and mutual update of state information between redundant gateways in a stateful design. The mechanism used to communicate, synchronize, and maintain the state between two or more redundant IPsec gateways is SSO. As we will see, this dramatically streamlines the failover reconvergence process and reduces IPsec tunnel failover delay by eliminating the need for eradication of old SAs and regeneration of new ones. This is because the SAs in a stateful design are already configured by SSO and are therefore available on the redundant peer prior to failover. Note IKE keepalives are not supported with SSO in a stateful IPsec HA environment. Dead Peer Detection (DPD), however, is supported in stateful IPsec HA deployments. By default, SSO uses the standards-based Stream Control Transmission Protocol (SCTP), defined in RFC 2970, to transport IPsec state information between redundant IPsec gateways. SCTP is similar to TCP in that it is connection-oriented and reliable, but it also has notable differences. One such underlying difference is that SCTP provides message ordering and reliability, whereas TCP provides these services for the actual bytes of the message. Because of this, SCTP is well suited for the reliable, sequenced exchange of state messages used to provide IPsec HA between two redundant IPsec gateways. As with HSRP and RRI, there are timers within SSO that can be tuned. Ideally, those timers should be set so that the state of each gateway is most accurately reflected in its redundant peers, rather than simply to aid in the speed of reconvergence among failover. Remember, SSO exists so that the state of the IPsec SADB is already built on the redundant peer before failover. As such, there should be no failover delay attributable to SSO if the state of each VPN gateway's SADB is correctly synchronized. Example 6-11 shows SSO output on C7206VXR-MAIN in Figure 6-5. The key difference between stateful (Example 6-11) and stateless (Example 6-5) configurations is the configuration of SSO to communicate the SADB state between active and redundant IPsec VPN gateways prior to a convergence event taking place. Configuration lines 4 and 5 instruct SSO to use the standby group with the name "chap6-vpnha" for redundancy. This indirectly binds SSO to the redundant crypto process. (Note from previous examples that the crypto process is also bound to this HSRP group as well.) As discussed previously, SSO uses stream control transport protocol (SCTP) to relay SADB state information from active to standby IPsec VPN gateways. The configuration in lines 717 of Example 6-11 instructs the SCTP to use the physical interface on Fa0/0 of C7206VXR-MAIN as the local IP, the physical interface on Fa0/0 of C7206VXR-STANDBY as the remote IP, and port 6666 as the Layer 4 source and destination ports. Example 6-11. SSO Configuration on C7206VXR-MAIN (Figure 6-5)
Stateful High Availability Failover ProcessThe following sections describe the stateful High Availability failover process:
Step 1: Initial IPsec VPN Tunnel EstablishmentAs with a stateless IPsec HA design, an IPsec VPN tunnel must first be built. Stateful IPsec HA offers a key design differentiator in this step: Whereas stateless IPsec HA allows the network designer to terminate the IPsec tunnel on an HSRP Virtual Interface, a stateful design allows the designer to both terminate and source the IPsec tunnel from HSRP virtual interfaces, thereby offering redundancy at both the origination and termination points of the IPsec VPN (a stateless design only offers redundancy at the termination points). This key point of differentiation is enabled with stateful IPsec HA using SSO. Step 2: SADB Synchronization with SSOAs we have discussed several times, in order for a design to be stateful, the IPsec SADB must be synchronized between active and failover IPsec VPN gateways. When IPsec Phase 1 and Phase 2 SAs are populated in the active router's SADB, they are then shared with the redundant router pre-failover using SCTP (the transport protocol for SSO messages). As we will see in later steps and in the stateless HA design summary, sharing of the SADB state using SSO eliminates failover delay attributable to IPsec reconvergence. Caution Although SCTP eliminates certain vulnerabilities inherent to the nature of TCP, SADB information passed using SCTP in an SSO-enabled design is sent in cleartext, not ciphertext. Therefore, administrators should be advised not to allow SCTP messages to cross an untrusted domain, such as a Layer 2 domain spanned across multiple untrusted switched domains. Step 3: Pre-HSRP Failover RRI ExecutionRRI propagates routing information in a stateful IPsec HA deployment in the same way that it does in a stateless IPsec HA deployment. There should be no additional decrease in system reconvergence attributable to RRI injection when selecting a stateful IPsec HA design alternative over a stateless one. Be aware, however, that as with a stateless IPsec HA option, injecting routes via RRI in a failover scenario will require RP reconvergence behind the IPsec VPN, contributing to the overall system reconvergence delay. Step 4: Active Router FailureTo trigger failover between redundant peers, an active router must first fail. Although this step is similar to what occurs in a stateless failover design, note that one key difference is that this failover can occur on either side of the VPN tunnel because there is redundancy built into the source of the IPsec VPN tunnel in this design. Step 5: HSRP ReconvergenceAs with a stateless design, HSRP must reconverge. The HSRP timers should be tuned for rapid failover in this stateful design in the same manner that they are tuned in a stateless design. It is important to note, however, that unlike a stateless design, HSRP reconvergence is the only process that contributes to the delay of the overall IPsec VPN tunnel. Step 6: IPsec ReconvergenceThe key difference between stateless and stateful IPsec HA solutions is that there is no reconvergence of IPsec in the overall reconvergence of the system. This is because the redundant router has already been informed of the IPsec SA state that it should use by its active counterpart prior to failover. For this reason, there is no failover delay attributable to Phase 1 and 2 IPsec negotiation in a stateful IPsec HA design. Step 7: Post-HSRP RRI ExecutionOnce the standby IPsec VPN gateway assumes the crypto forwarding responsibilities for traffic through the IPsec VPN tunnel, it must update the local routing table with itself as the VPN gateway for routes on the opposite side of the IPsec VPN tunnel. This is done through RRI in the same manner outlined in our discussion of stateless IPsec HA. |
EAN: 2147483647
Pages: 113