Designing DNS Service Placement
| Active Directory cannot function without DNS (Domain Name Services). For this reason, it's important to have a sound DNS service before you implement Active Directory. This should include DNS servers that are located as close as possible to the domain controllers and client computers they serve. Because DNS zones must be replicated when changes occur, you must balance the need for timely replication of the DNS zones with the need for quick name resolution for clients and servers. Windows Server 2003 provides many features that can be used to create this balance. Those features include the following:
In the previous chapter, we discussed these features and their relation to the logical infrastructure. We now examine how each feature relates to the physical infrastructure of a Windows Server 2003 network. Active Directory Integrated ZonesActive Directory integrated zones were first implemented with Windows 2000 Server. These zones provide significant benefits to a network's physical infrastructure over and above those of standard DNS zones. Because they must be located on domain controllers, they are (by default) as close to the domain controller as they can get! In addition, Active Directory integrated zones conserve bandwidth for clients and servers by attaching their zone transfer process to the normal replication of Active Directory. For these reasons, Active Directory integrated zones should be used whenever possible. It isn't always possible to use Active Directory integrated zones because the server that hosts the integrated zone must be a domain controller as well as a DNS server. Some organizations have smaller remote offices that do not contain a domain controller. In this case, a different type of zone is required.
In addition, Active Directory integrated zones should be used only by administrators who understand the risks associated with their use. All Active Directory integrated zones are primary zones. This means they can be read from and written to as well. These zones can be secured, and administrators should take great care to make sure they are secure to prevent spoofing of IP addresses. Spoofing occurs when a hacker can collect enough information about your network to fool the system into thinking that he belongs in it. This significant security risk should be avoided. Spoofing can be prevented using Active Directory integrated zones with secure dynamic updates. Stub ZonesStub zones are new to Windows 2003 DNS servers. Prior to the use of stub zones, all DNS servers in a domain always replicated all the records for each zone to the replica servers for that zone. Stub zones improve DNS efficiency for networks that are at the edge of the topology. These zones replicate only the information about the other DNS servers inside the topology. The assumption is that they will have to use these servers to gain information about the domain. In other words, they are not the name resolution severs for our domain as much as they are the name resolution servers to help other domains discover our domain. Stub zone database files improve DNS efficiency because they do not replicate all the records for a zone. In fact, they contain and manage only the following types of records:
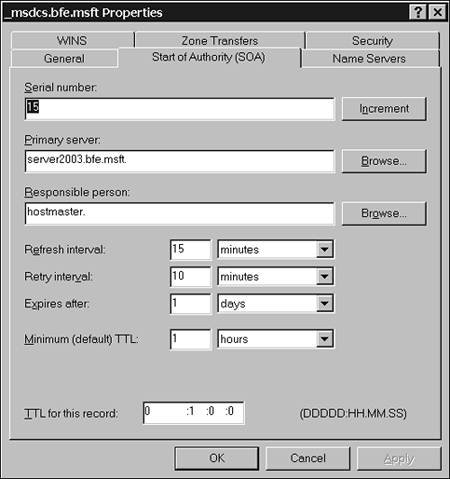
We now examine each of these records and their purpose in a stub zone database. Start of Authority Resource RecordThe start of authority (SOA) resource record is an essential element in any DNS database. It is said to be the first record of the database and it establishes the fact that this database is a DNS database. The SOA record usually contains instructions to the database as to its role (primary or secondary) and how it maintains contact with the other DNS servers that host the replica database files. The SOA sets the schedule for how often a secondary server contacts the primary servers for database updates. SOA records on secondary servers respond to settings in the SOA record on primary servers. Figure 6.1 illustrates the settings that SOA records can communicate. Figure 6.1. Start of authority records control communication between primary and secondary servers.
Named Server RecordsNamed server (NS) records identify a particular server as hosting a zone. Servers can host multiple zones and one server can be a primary for one zone and a secondary for another. Named server records allow servers and clients to locate a server by its fully qualified domain name (FQDN). Glue Host RecordsGlue host (A) records are used for locating the authoritative DNS servers for a delegated zone. In effect, they glue zones together by providing an efficient path for other DNS servers to follow when resolving a name. Incremental Zone TransferPrior to the release of Windows 2000 Server, DNS databases shared "all or nothing at all." In other words, the whole database had to be replicated when replication occurred. For example, suppose a server had 2,000 records on it and you added another 2 records to the database. The entire database had to be copied (replicated) to each of the replica servers. This is referred to as AXFR (all zone transfer). The ultimate disadvantage of this type of replication was a lack of accuracy because the administrators did not want to replicate the servers as often as it was in this case. Windows Server 2003, as well as Windows 2000 Server, provides for incremental zone transfer (IXFR). With IXFR, only the records that have changed since the last zone transfer are transferred. So, if you have 2,000 records and add 2 more, only the additional 2 records have to be replicated. This is accomplished using an additional table, which contains each record and the status of its last update. The information in the table is referred to as the up-to-datedness vector. The ultimate benefit of this type of zone transfer is greater accuracy because administrators are more willing to let servers replicate more often. Caching-Only DNS ServersThe key word in caching-only DNS is only. All DNS servers keep a cache in addition to any DNS zones that they host. The cache includes records that have been recently resolved. You can set the cache to control how long the resolved queries remain cached. The cache is always checked before databases are checked. However, a caching-only DNS server does not host a DNS database. It can resolve a query on its own only if the query happens to be in its cache. In other words, it can resolve a query on its own only if it has resolved it before. You might be asking how it resolved the query in the first place. Well, a caching-only DNS server is set with forwarders that allow it to ask another server to resolve the query and tell the caching-only DNS server. It then caches that information for the next time. The main benefit of caching-only DNS servers is that they do not host a DNS zone and therefore do not need zone transfer at all. All zone transfers rob from the available bandwidth of the network; therefore, this type of zone is useful when you have a small office that is connected to the home office with a relatively slow link (low bandwidth). Caching-only DNS servers will, of course, have to use the link until they learn the addresses that are most used, but the use of the link for name resolution will decrease when the most used names are in the cache. Because there is no zone transfer at all, there is no zone transfer bandwidth use issue.
Conditional ForwardingConditional forwarding is new to Windows Server 2003. A forwarder is a designated DNS server that forwards queries to resolve external domain names for another DNS server. Forwarders can be used to reduce the amount of name resolution traffic across a WAN (Wide Area Network). Prior to Windows Server 2003, servers that were set with forwarders would forward all queries they could not resolve to all forwarders based on their position in a list. This was less than efficient because some servers that were set as forwarders did not have the best logical route to resolve the query. Conditional forwarding allows all queries for a particular namespace to be forwarded to a particular server's IP address. This server should be logically close to the namespace listed. For example, a conditional forwarder could be used to forward all queries ending with examcram2.com to a specific IP address of a DNS server or to multiple IP addresses of DNS servers that can resolve the query. In the same way, conditional forwarders can also be used to manage name resolution between different namespaces in a network. Figure 6.2 illustrates the settings for conditional forwarding. Figure 6.2. We can set DNS servers for conditional forwarding.
|
EAN: 2147483647
Pages: 152