IDS Sensors Using Common Cisco Devices
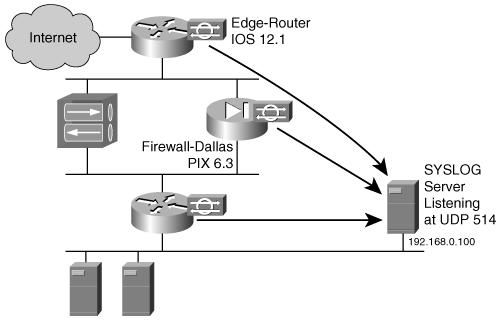
| Cisco IOS routers and PIX Firewalls are the most fundamental elements of a typical network. Both of these devices feature built-in IDS sensors that are easy to deploy. The embedded sensors eliminate the need for port mirroring or wire taps to capture the traffic, thus empowering Netadmins to deploy basic IDS sensors without additional hardware purchases. The inline IDS capabilities of both IOS routers and PIX Firewalls allow these devices to directly drop suspicious traffic, thus preventing an attack. However, despite the advantages offered by both the IOS- and the PIX Firewall based IDSs, they merely complement the overall security strategy. The IOS- and PIX-based IDSs should not be considered as an option for replacing dedicated IDS devices. Figure 9-6 shows the logical layout of a sample network with IOS- and PIX-based IDS sensors. The intrusion alerts from all the sensors are consolidated to a central syslog server to enable ease of management. Figure 9-6. IOS- and PIX-Based Sensors Router IDSsRouter-based embedded IDS sensor functionality was first introduced with Cisco IOS Release 12.0(5)T. The sensor supported 59 basic signatures for detecting the most common network attacks. However, the IDS feature has been renamed the Intrusion Prevention System (IPS) in Cisco IOS Release 12.3(8)T and higher. The IPS feature supports in excess of 740 signatures and is available with the following IOS software feature sets:
The IDS/IPS features in the IOS allow the router to monitor the traffic, send an alert, or reset the connection when suspicious patterns are detected. Deploying an IOS-based IDS involves the following steps:
Configuring an IOS-Based IDS SensorBefore configuring the sensor on the router, you should first enable syslog messaging with timestamps. Then configure the IDS parameters and enable the IDS on the interfaces. Table 9-4 summarizes the steps for configuring an IOS-based IDS sensor.
Tip Beginning with the 831, 1710, 2600XM, 3700, and 7300 Series routers, you can also configure IOS-based IDSs or IPSs using the Cisco Router and Security Device Manager (SDM) GUI, without a detailed knowledge of IOS commands. SDM also allows you to add, remove, or edit signatures for the IOS IPS feature. SDM is the web browser based GUI for configuring Cisco routers and is discussed in Chapter 8, "Router and Switch Security." Example 9-5 shows a sample configuration of an IOS-based IDS sensor. The sensor is configured to drop all the packets that match the attack signatures. All the IDS alerts are sent to the syslog server 192.168.0.100. The highlighted text in the example provides more details regarding the relevant configuration. Example 9-5. IOS Configuration IDS Sensor! enable logging before IDS setup logging on logging 192.168.0.100 ! IOS IDS messages are sent at warning level logging trap warnings service timestamps log datetime msec ! default action for attack signature is set to drop the packets ip audit attack action drop ip audit notify log ip audit po max-events 100 ip audit smtp spam 200 ! Signature 2004 is globally disabled ip audit signature 2004 disable ip audit name IDS1 info action alarm ip audit name IDS1 attack action drop ! interface Ethernet0/0 ip address 192.168.0.10 255.255.255.0 ip audit IDS1 in ! interface Serial0/0 ip address 172.16.0.10 255.255.255.0 ip audit IDS1 in !end Verifying the ConfigurationYou can verify the Cisco IOS Firewall IDS configuration using the show ip audit configuration command, as shown in Example 9-6. Example 9-6. Output of the show ip audit configuration Command Router-Dallas#show ip audit configuration Event notification through syslog is enabled Event notification through Net Director is disabled Default action(s) for info signatures is alarm Default action(s) for attack signatures is drop Default threshold of recipients for spam signature is 200 Signature 2004 disable PostOffice:HostID:0 OrgID:0 Msg dropped:0 :Curr Event Buf Size:0 Configured:100 Post Office is not enabled - No connections are active Audit Rule Configuration Audit name IDS1 info actions alarm attack actions drop Router-Dallas# Monitoring the NetworkThe IDS sensor monitors the traffic flowing through it, and the alerts are sent to the syslog server. Example 9-7 shows the messages received by syslog server. Note the signature numbers denoted by the highlighted text. Example 9-7. Syslog MessagesDec 09 15:31:24 192.168.0.6 47: Dec 9 15:31:24.410: %IDS-4-ICMP_FRAGMENT_SIG: Sig:2150:Fragmented ICMP Traffic - from 192.168.0.140 to 192.168.0.6 Dec 09 15:31:37 192.168.0.6 49: Dec 9 15:31:37.097: %IDS-4-TCP_FIN_ONLY_SIG: Sig:3042:TCP - FIN bit with no ACK bit in flags - from 192.168.0.140 to 192.168.0.6 Dec 09 15:32:19 192.168.0.6 51: Dec 9 15:32:18.742: %IDS-4-TCP_FIN_ONLY_SIG: Sig:3042:TCP - FIN bit with no ACK bit in flags - from 192.168.0.140 to 192.168.0.6 Dec 09 15:33:39 192.168.0.6 53: Dec 9 15:33:38.951: %IDS-4-TCP_NO_FLAGS_SIG: Sig:3040:TCP - No bits set in flags - from 192.168.0.140 to 192.168.0.6 You can also monitor the network through the router CLI using the show ip audit statistics command, as shown in Example 9-8. The highlighted sections indicate a high number of attacks matching signatures 2150, 3040, and 3042. The information regarding these signatures matches that shown in the previous example. Example 9-8. Output of the show ip audit statistics CommandRouter-Dallas#show ip audit statistics Signature audit statistics [process switch:fast switch] signature 2000 packets audited: [5:5] signature 2150 packets audited: [341:481] signature 3040 packets audited: [3320:3332] signature 3041 packets audited: [0:10] signature 3042 packets audited: [13280:17972] Interfaces configured for audit 2 Session creations since subsystem startup or last reset 0 Current session counts (estab/half-open/terminating) [0:0:0] Maxever session counts (estab/half-open/terminating) [0:0:0] Last session created never Last statistic reset never Post Office is not enabled - No connections are active Router# PIX IDSsPIX-based IDS sensors are supported by PIX OS version 5.2 and higher. The sensors support 59 signatures to detect most common attacks. Deploying a PIX-based IDS involves the following steps:
Configuring a PIX-Based IDS SensorSimilar to the IOS-based IDS, the syslog with timestamps should be enabled on the PIX Firewall before configuring the IDS sensor. The steps involved in configuring a PIX-based IDS sensor are summarized in Table 9-5.
Tip You can also configure a PIX-based IDS using the PIX Device Manager (PDM) GUI, without a detailed knowledge of PIX commands. PDM can also create graphs to monitor IDS statistics. Example 9-9 shows the sample configuration of a PIX-based IDS sensor. The sensor is configured to drop all the packets that match the attack signatures. All the IDS alerts are sent to the syslog server 192.168.0.100. For the sake of clarity, the example includes highlighted comments that explain the relevant details about the configuration. Example 9-9. PIX IDS Configurationlogging on logging timestamp ! PIX IDS messages are sent at warning level logging trap warnings logging host inside 192.168.0.100 ! ip audit name IDS1 attack action alarm drop reset ip audit name IDS2 info action alarm !Unlike IOS IDS info and attack signatures are applied !to the same interface using different names ip audit interface inside IDS2 ip audit interface inside IDS1 ! ip audit interface outside IDS2 ip audit interface outside IDS1 ! ip audit info action alarm ip audit attack action drop reset ! ip audit signature 1000 disable ip audit signature 2002 disable !end Verifying Sensor ConfigurationTo verify the sensor configuration, use the show running command in privileged mode. Monitoring the NetworkThe sensor monitors the traffic flowing through the PIX Firewall, and the intrusion alerts are sent to the syslog server. Example 9-10 shows the messages collected by the syslog server. Note how the output contains the details of the attack signatures. Example 9-10. Syslog MessagesDec 09 16:16:44 192.168.0.20 Dec 09 2004 16:16:45: %PIX-4-400023: IDS:2150 ICMP fragment from 192.168.0.140 to 192.168.0.20 on interface inside Dec 09 16:16:44 192.168.0.20 Dec 09 2004 16:16:45: %PIX-4-400025: IDS:2154 ICMP ping of death from 192.168.0.140 to 192.168.0.20 on interface inside Dec 09 16:16:44 192.168.0.20 Dec 09 2004 16:16:45: %PIX-4-400025: IDS:2154 ICMP ping of death from 192.168.0.140 to 192.168.0.20 on interface inside Dec 09 16:16:51 192.168.0.20 Dec 09 2004 16:16:51: %PIX-4-400026: IDS:3040 TCP NULL flags from 192.168.0.140 to 192.168.0.20 on interface inside Dec 09 16:16:55 192.168.0.20 Dec 09 2004 16:16:56: %PIX-4-400014: IDS:2004 ICMP echo request from 192.168.0.140 to 192.168.0.20 on interface inside The IDS statistics can also be viewed at the PIX CLI in privileged mode using the show ip audit count command. As highlighted in Example 9-11, the PIX has detected attacks matching the 2001, 2150, 2154, and 3040 signatures. These signature details match the output shown in the previous example. Example 9-11. Output of the show ip audit count CommandFirewall-Dallas# show ip audit count Signature inside Global 1000 I Bad IP Options List 0 0 1001 I Record Packet Route 0 0 1002 I Timestamp 0 0 1003 I Provide s,c,h,tcc 0 0 1004 I Loose Source Route 0 0 1005 I SATNET ID 0 0 1006 I Strict Source Route 0 0 1100 A IP Fragment Attack 0 0 1102 A Impossible IP Packet 0 0 1103 A IP Teardrop 0 0 2000 I ICMP Echo Reply 0 0 2001 I ICMP Unreachable 193482 193482 2002 I ICMP Source Quench 0 0 2003 I ICMP Redirect 0 0 2004 I ICMP Echo Request 10 10 2005 I ICMP Time Exceed 0 0 2006 I ICMP Parameter Problem 0 0 2007 I ICMP Time Request 0 0 2008 I ICMP Time Reply 0 0 2009 I ICMP Info Request 0 0 2010 I ICMP Info Reply 0 0 2011 I ICMP Address Mask Request 0 0 2012 I ICMP Address Mask Reply 0 0 2150 A Fragmented ICMP 306 306 2151 A Large ICMP 0 0 2154 A Ping of Death 1992 1992 3040 A TCP No Flags 3321 3321 3041 A TCP SYN & FIN Flags Only 0 0 3042 A TCP FIN Flag Only 0 0 3153 A FTP Improper Address 0 0 3154 A FTP Improper Port 0 0 4050 A Bomb 0 0 4051 A Snork 0 0 4052 A Chargen 0 0 6050 I DNS Host Info 0 0 6051 I DNS Zone Xfer 0 0 6052 I DNS Zone Xfer High Port 0 0 6053 I DNS All Records 0 0 6100 I RPC Port Registration 0 0 6101 I RPC Port Unregistration 0 0 6102 I RPC Dump 0 0 6103 A Proxied RPC 0 0 6150 I ypserv Portmap Request 0 0 6151 I ypbind Portmap Request 0 0 6152 I yppasswdd Portmap Request 0 0 6153 I ypupdated Portmap Request 0 0 6154 I ypxfrd Portmap Request 0 0 6155 I mountd Portmap Request 0 0 6175 I rexd Portmap Request 0 0 6180 I rexd Attempt 0 0 6190 A statd Buffer Overflow 0 0 Firewall-Dallas# |
EAN: 2147483647
Pages: 106