HTTP Inspection Engine
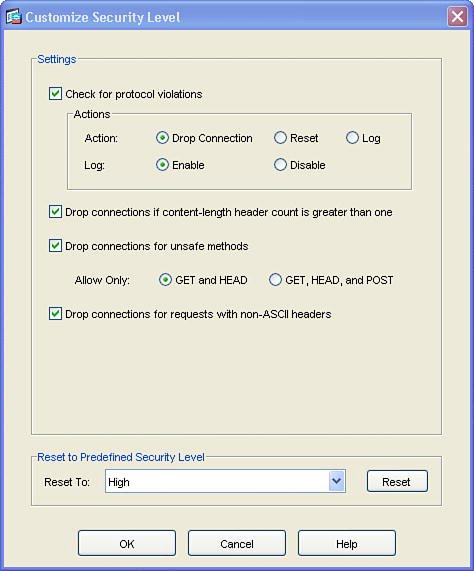
| HTTP or web traffic is one of the most popular types of traffic on networks today. ASA includes the ability to inspect HTTP traffic flows to detect possible network attacks. You can initiate the process to configure the inspection of an HTTP traffic flow under the Service Policy Rules section. This process to initiate the creation of a traffic flow for HTTP inspection is similar to the process to define a traffic flow with Service Policy Rules for IPS inspection as described in the "Intrusion Prevention Service" section earlier in this chapter. The configuration to inspect a certain HTTP traffic flow results in a class-map and policymap statement, similar to the CLI output for the IPS Service Policy Rule configuration. The HTTP inspection engine allows the ASA to mitigate potential network attacks that are tunneled over TCP port 80, the HTTP port. The HTTP inspection engine also verifies that the network traffic is RFC-compliant and not a series of malformed or handcrafted packets designed to potentially launch a network attack. URL length is also inspected to help detect any handcrafted large URLs that can be designed to create a network attack. ASDM features an easy-to-use wizard to walk you through the Service Policy Rule definition process. You can configure HTTP inspection globally for all traffic through the ASA, or you can configure protocol inspection for a single interface. In the Add Service Policy Rule Wizard, as shown in Figure 3-14, you can configure a rule to be global, which applies to all interfaces on the ASA. Figure 3-14. Global Rule to Inspect HTTP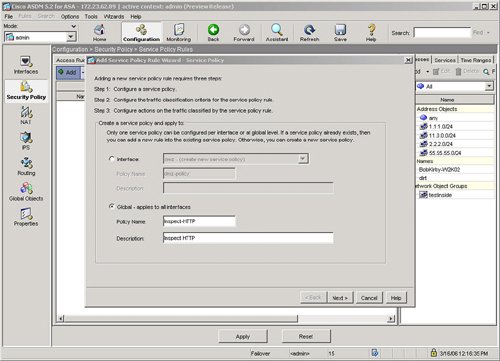 The next step is specification of what traffic or ports will be inspected. Figure 3-15 displays an example of how to select the inspection of TCP packets, and Figure 3-16 configures the HTTP/web service to inspect HTTP/WWW, or TCP port 80. Figure 3-15. Inspect TCP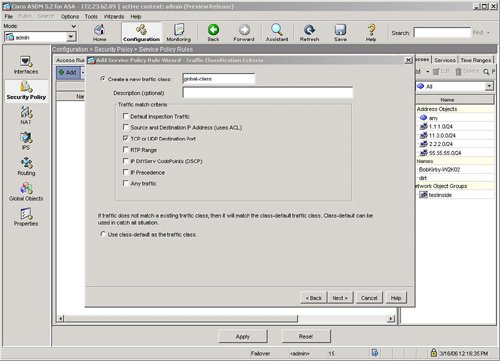 Figure 3-16. Inspect HTTP/Web Service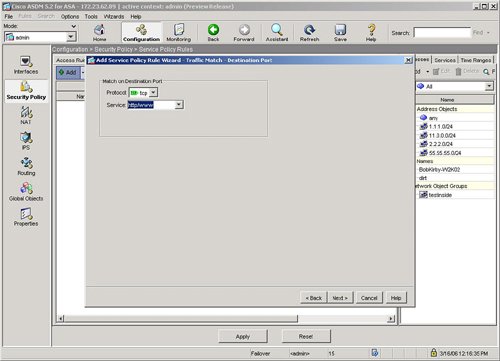 The next step in the wizard enables you to configure protocol inspection. HTTP inspection can be selected for inspection, as shown in Figure 3-17. Figure 3-17. Select HTTP for Protocol Inspection Several DDoS attacks send only part of the TCP handshake to initiate but never complete a TCP connection. This DDoS attack can result in a large TCP connection table that can consume resources that would otherwise go to servicing legitimate network traffic. The ASA supports the ability to configure a threshold for the maximum number of embryonic, or developing, connections that are allowed at one time by the appliance. Maximum connection parameters can provide protection against DDoS attacks on the ASA. The Maximum TCP and User Datagram Protocol (UDP) Connections field allows the ASA to configure a threshold of how many connections are active through the appliance at one time. The Maximum Embryonic Connections field controls the size of the internal state table for TCP connections. The Randomize Sequence Number feature allows the ASA to create random, nonpredictable sequence numbers for TCP connections. The ability to randomize sequence numbers creates an additional layer of abstraction and protection against network attackers who endeavor to predict sequence numbers and masquerade as legitimate network connections. The Randomize Sequence Number feature is on by default. As mentioned in the previous chapters, the DDoS Guard is typically deployed upstream close to the protected zone or servers. The ASA and DDoS Guard can provide a layered defense against DoS and DDoS attacks. Max Embryonic Connections and Randomize Sequence Number protection on the ASA can be the first line of defense, and the DDoS Guard can be second line of defense against the network attack. A TCP Map is used to configure the customized inspection and protection for TCP connections. A TCP Map can be configured as part of the HTTP inspection to provide TCP and HTTP protection for web traffic. A TCP Map can also be configured separately and independent of HTTP inspection. TCP MapCisco ASA features the ability to tailor how TCP connections should be policed and normalized. TCP maps dictate how TCP sessions should be managed for a specific traffic flow. You can configure TCP maps as part of application protocol inspection, as evidenced by the ability to create a TCP map while defining protocol inspection for HTTP. To create a new TCP map that can be used as part of HTTP protocol inspection, select the connection settings and the Use TCP Map option under TCP Normalization as shown in Figure 3-18. You can use TCP maps to police the behavior of a connection to reduce vulnerabilities and to minimize the chance of a network attack through the specified TCP connection. Figure 3-18. Use TCP Map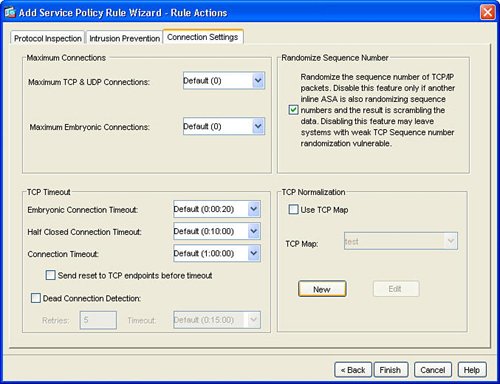 TCP normalization is the process of inspecting TCP flows for traffic that may not be normal and could possibly be used to implement a network attack. TCP maps determine what part of the TCP flow will be inspected to identify fields in TCP packets that may not be normal or standard. Figure 3-19 displays an example of TCP Map configuration options. Figure 3-19. TCP Map Options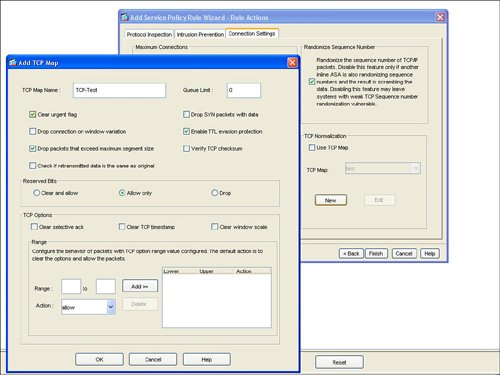 HTTP MapFigure 3-20 displays an example of selecting protocol inspection for HTTP and the location to configure or select a customized HTTP map. An HTTP map is used to define the parameters of the inspection for HTTP. Multiple HTTP maps are allowed in order to have different HTTP normalization and enforcement rules for different traffic flows on different interfaces. Figure 3-20. Configure HTTP Map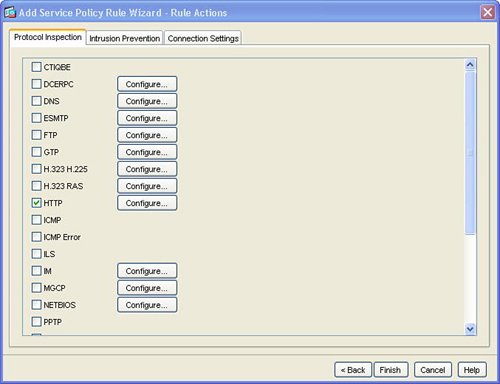 An HTTP map can be configured to allow customized or specific processing for an HTTP protocol violation. Figure 3-21 displays an example of how to select an HTTP Map and the location of how to initiate the customization process for an HTTP map. Figure 3-21. Select HTTP Map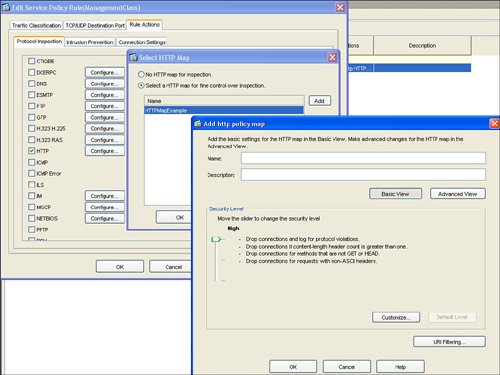 An HTTP connection can be allowed, reset, or dropped, depending on conformance to the RFC standard. A syslog can also be generated for an HTTP connection that triggers the defined condition. ASDM can reset any HTTP connection that does not conform to the HTTP protocol. This stance to reset an HTTP connection in an HTTP Map enables the ASA to be self-defending by automatically resetting the nonconforming or suspect HTTP connection that could be used for a potential network attack. Figure 3-22 displays an example of the customizable options under the basic view of an HTTP Map and the basic protocol violation parameters in an HTTP map. Figure 3-22. HTTP Map Protocol Violation Customization The advanced view of an HTTP Map allows additional customization features, including the ability to restrict certain content or application types in an HTTP connection. For example, Figure 3-23 displays an example of how an HTTP Map can be customized to prevent or block MP3 download through an HTTP connection. Figure 3-23. HTTP Content Type Inspection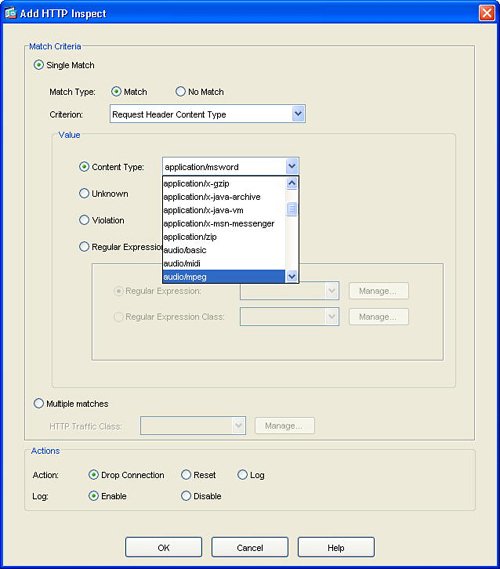 Figure 3-24 provides an example of a configured service policy rule to inspect TCP and HTTP traffic and references the corresponding TCP and HTTP maps. Figure 3-24. Service Policy Rule for TCP and HTTP Protocol Inspection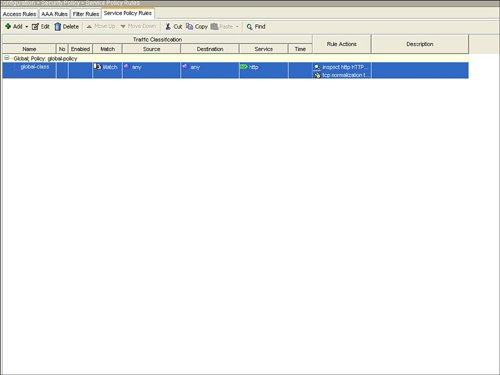 |
EAN: 2147483647
Pages: 112
- Chapter III Two Models of Online Patronage: Why Do Consumers Shop on the Internet?
- Chapter VI Web Site Quality and Usability in E-Commerce
- Chapter VII Objective and Perceived Complexity and Their Impacts on Internet Communication
- Chapter XI User Satisfaction with Web Portals: An Empirical Study
- Chapter XVI Turning Web Surfers into Loyal Customers: Cognitive Lock-In Through Interface Design and Web Site Usability