Configuring Content Security and Control Security
| The partnership between Cisco Systems and Trend Micro has enabled the creation of the Content Security and Control Security Module for the ASA product line. This Content Security and Control Security Service Module (CSC-SSM) implements many of the advanced virus, phishing, spam, and spyware control functions on the ASA platform. The functions that are implemented on the CSC-SSM Module include the following:
The base CSC-SSM license contains support for the antivirus, antispyware, and fileblocking features. An additional plus license is required to enable the antiphishing, antispam, URL filtering/blocking, and content filtering features. You can implement these base and plus functions on the following network protocol types that are supported by the CSC-SSM module:
The CSC-SSM module can be managed with ASDM. The CSC-SSM module management through ASDM uses the IP address, username, and password for the CSC-SSM module. Figure 3-25 displays the Trend Micro Content Security icon in ASDM and the initial logon to the Content Security SSM. In addition to ASDM management, the CSC-SSM modules can also be centrally managed by Trend Micro's Trend Micro Control Manager (TMCM) centralized management product. Figure 3-25. Content Security Icon and CSC-SSM Logon in ASDM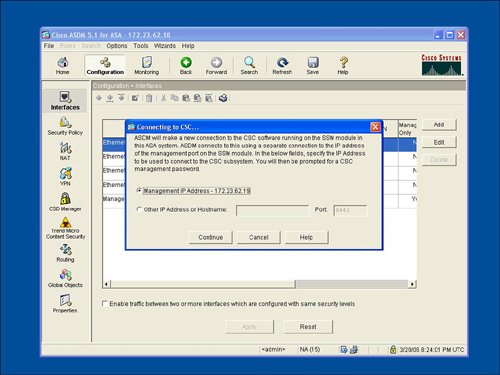 The main Content Security tab on the ASDM homepage features a near real-time update of the security threats that have been detected by the Content Security module. These security threats are divided into the following categories:
Figure 3-26 displays the graphs in ASDM for virus detection. Similar threat graphs are also available for spyware detection, spam detection, and URL filtering/blocking protection. The threat graphs can be accessed from the Monitoring area in ASDM by selecting the Threat option under the Trend Micro Content Security icon. Figure 3-26. Threat Graphs The CSC-SSM configuration process to send network traffic from the ASA chassis to the CSC-SSM is similar to that of other features in ASA, including the IPS-SSM module. CSCSSM, like IPS-SSM, uses the service policy rules described earlier in the "Intrusion Prevention Service" and "Protocol Inspection" sections of this chapter to specify what network traffic should be sent from the ASA chassis to the CSC-SSM module. The user can initiate configuration of the CSC-SSM module by selecting Configuration from the top of the ASDM GUI and then selecting the Trend Micro Content Security option from the left side of the ASDM GUI. Selecting the Configuration option for Trend Micro Content Security will result in the display of the items that can be configured on the CSC-SSM module including Content Security and Control Services Module (CSC-SSM) setup, web (URL filtering/blocking), mail (scanning, content filtering, antispam), file transfers (scanning, blocking), and updates. Content Security and Control Services Module (CSC-SSM) SetupCSC Setup options include the following:
The CSC-SSM Setup Wizard walks the user through each of the CSC-SSM setup steps. Figure 3-27 displays CSC Setup options in the GUI and the launch point for the Setup Wizard screen of the CSC-SSM Setup Wizard. Figure 3-27. CSC-SSM Setup Wizard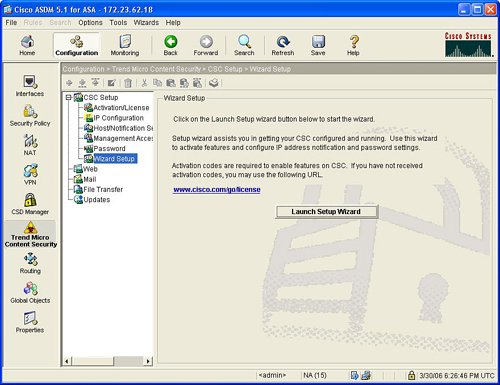 WebThe CSC-SSM module features the following web or HTTP functions:
The configuration of these web features requires ASDM to launch the integrated Trend Micro InterScan for Cisco CSC-SSM management. Trend Micro InterScan requires an additional password to be entered to log on. Figure 3-28 displays the web options in ASDM for CSC-SSM, and Figure 3-29 provides the resulting logon screen to Trend Micro InterScan. Figure 3-30 displays the Summary page in Trend Micro InterScan, which can be displayed after logon to Trend Micro InterScan from ASDM. Figure 3-28. Trend Micro Content Security Options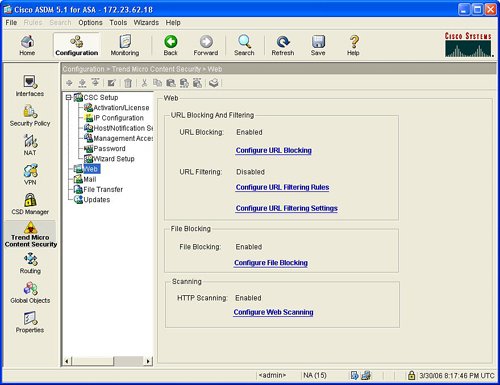 Figure 3-29. Log on to Trend Micro InterScan for Cisco CSC-SSM Figure 3-30. Trend Micro InterScan Summary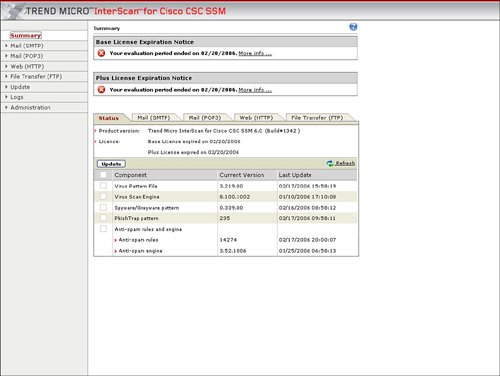 URL BlockingURL Blocking allows a specific URL to be blocked, thus preventing a user from accessing a specific website or webpage. ASDM, through the launch of the integrated Trend Micro InterScan Device Manager, allows the URL blocking feature to be configured including blocking on wildcards and the ability to always allow a specific list of URLs. Figure 3-31 displays the location to select web URL blocking configuration and the resulting configuration options that are displayed in Trend Micro InterScan. Figure 3-31. URL Blocking in Trend Micro InterScan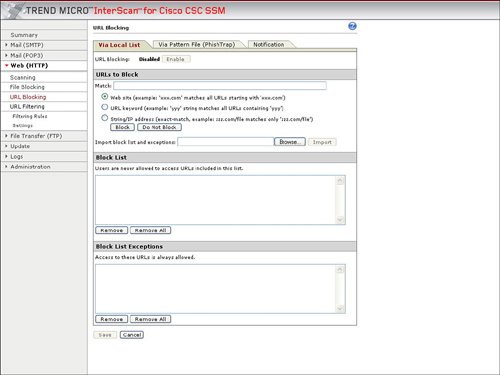 Phishing is a type of malware with which an e-mail is sent to an unsuspecting user with a link to a fake website. These phishing e-mails can attempt to trick the user to log on to what appears to be a valid banking or e-commerce site. However, what the user is really logging on to is a fake website, and the attacker's purpose is the gathering of the user's account information. Trend Micro collects and maintains a list of these phishing or fake websites. The CSC-SSM module can block the HTTP connection and protect the user from accessing one of these known phishing websites. Trend Micro also collects a list of known websites that harbor spyware. Network attackers often plant spyware on more vulnerable websites and attempt to download spyware to unsuspecting users that frequent these websites. The CSC-SSM module also features the ability to block URL access to prevent users from accessing one of these known websites that are rife with spyware. Figure 3-32 provides an example of how antiphishing and antispyware can be enabled for URL inspection through the ASA CSC-SSM. Figure 3-32 also displays how you can identify a specific phishing site and update Trend Micro's phishing sites list. Figure 3-32. Antiphishing and Antispyware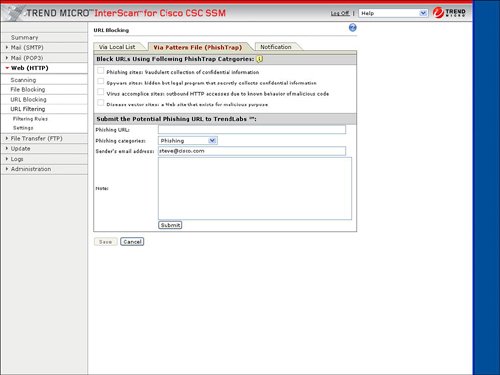 URL FilteringCSC-SSM supports the use of predefined types of websites that can be filtered, including entertainment, gambling, job search, and so on. The websites within these categories are updated and maintained through Trend Micro. These categories of websites can also be filtered based upon the time of day to permit certain sites during leisure time but not during standard work hours. ScanningScanning enables the CSC-SSM module to scan HTTP traffic, including that for web mail, and to detect and remove certain viruses or spyware that could be used to implement a network attack. CSC-SSM also features the ability to clean an infected file or to delete the infected file before it is transported to the user over the scanned HTTP or web connection. File BlockingFile blocking enables certain file types or file extensions to be blocked so they are not transported over an HTTP or web download connection. File types that can be blocked include MP3, JPG, EXE, java, and Microsoft Office applications. CSC-SSM can provide protection for the POP3 and SMTP mail protocols. The CSC-SSM module supports the following mail security functions for incoming and outgoing POP3 and SMTP network traffic:
ScanningScanning allows incoming and outgoing e-mail to be scanned for viruses, spyware, and other malware. Infected attachments can be either cleaned or deleted before they are delivered to the user. Figure 3-33 displays an example of configuring virus and other malware scanning for incoming SMTP mail. Figure 3-33. Scanning Configuration for Incoming SMTP Mail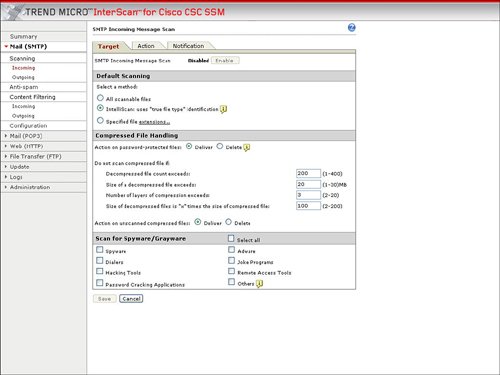 AntispamThe Mail configuration option in Trend Micro InterScan for CSC-SSM also contains the ability to protect e-mail users from spam. Spam messages can contain a potential network threat, in addition to being a nuisance. The antispam capability in ASA CSC-SSM can both reduce the exposure to spam-based network attacks and increase productivity by reducing spam to users of a network. The antispam capability enables the administrator to define spam threshold buckets of high, medium, or low. The easy-to-use configuration of Antispam through the integration of ASDM and Trend Micro InterScan also enables the administrator to permit specific e-mail sources or block specific e-mail sources/spammers. Figure 3-34 displays the Antispam configuration options of ASA CSC-SSM. Figure 3-34. Antispam Configuration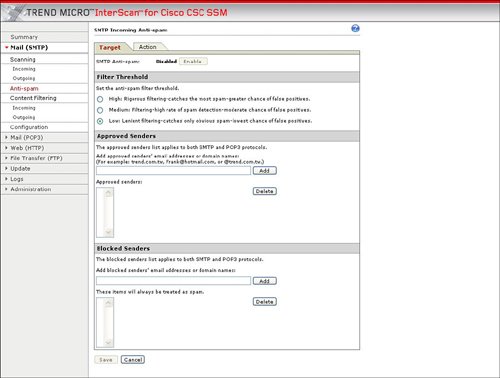 Content FilteringThe CSC-SSM module can filter mail based upon the type of content in the e-mail. For example, mail that exceeds a certain size can be filtered. Mail with a certain filename on an attachment or an attachment of a certain file type, like MP3, JPG, or EXE, can also be filtered or removed from an e-mail before delivery to the user. Figure 3-35 displays an example of the content filtering options. Figure 3-35. Content Filtering Configuration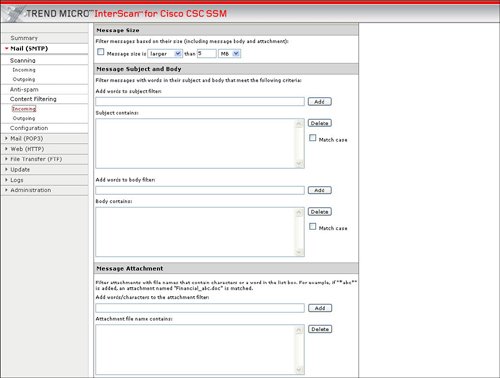 File TransferCSC-SSM provides protection for file transfers using FTP. CSC-SSM allows both the scanning of FTP network traffic for viruses and other malware and the blocking of file transfers based upon file types. File types that can be blocked include MP3, JPG, EXE, Java, and Microsoft Office file extensions. The file transfer, or FTP, scanning, and blocking configuration options are very similar to the web scanning and file blocking features described in the "web" section for CSC-SSM in this chapter. |
EAN: 2147483647
Pages: 112