Getting Started
|
Once you have your business plan in place and have decided to become an independent InfoSec consultant, your plan should provide you with a step-by-step approach to getting started. [1] Let's break down the InfoSec consulting business into sections (see Figure 17.1):
-
Engagement setup
-
Engagement process
-
Assessment services
-
Advisory services
-
Security implementation
-
Augmentation
-
Legal issues
-
International aspects
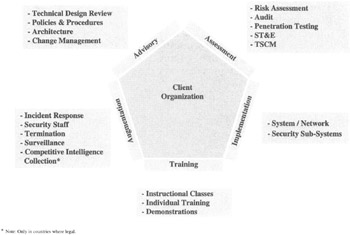
Figure 17.1: An example of InfoSec consulting components.[2]
Engagement Setup
To begin, you need an "entry into the business" strategy. You must have established and continue to refine your information network (trusted contacts within your business arena who can tell you what is going on where, etc.). You must also use other sources to find your potential customers—or clients, as some like to call them. Such other sources include referrals, marketing through brochures, pamphlets, lectures, books, articles, and your business Web site. It also includes "cold calling" of potential customers and explaining to them what services you offer.
Once you have made contact with a potential client, you must clearly and precisely communicate your services; you must "find their pain" and explain how you can help solve their problems. Try to make this a question-and-answer session where a dialogue takes place. You should also use the opportunity to explain your experience by citing examples of your past services to clients, without providing specific names, of course.
Assuming the meeting went well and they ask you for a proposal, you should provide one in the most expeditious manner possible and be sure that you understand: Each client requires a different approach depending on the size of the client—small, medium, or large organization—as the scale, tactics, and strategy will vary with each. In the proposal you should be precise, include a project schedule with logistics requirements, roles, and responsibilities (for both you and your client), and address liability issues. Other matters to consider are:
-
Understand who you are dealing with and be sure to get to the right level of authority to make decisions that affect your work;
-
Identify their needs as specifically as possible;
-
Understand their budget (size and cycle);
-
Get the "big picture";
-
Be sure you have a clear understanding of their expectations and your deliverables, before leaving the potential client;
-
Determine any time factors that they want to consider; and
-
If needed, exchange encryption keys so correspondence can be done in private.
As part of your engagement setup, you should have a specific written proposal prepared, as well as one in the standard format you have developed. Both should be on your notebook computer so that they can be modified immediately to fit the situation. If you believe your specific written proposal is just right for your potential client, be sure to have several hard copies available to present to the potential client. The proposal, as a minimum, should include:
-
Proposal Structure
-
Work to Be Performed
-
Project Schedule
-
Timing and Fees
-
Roles and Responsibilities
-
Assumptions and Caveats
-
Legal Issues
Engagement Process
Once you begin, remember to document everything to include:
-
Time and dates;
-
Whom you spoke to;
-
What was said;
-
Any action items resulting from the conversations;
-
Task you completed and their time and date;
-
Notable events that occurred; and
-
All other matters that can be used to support your activities, position, time spent, and the like.
More than one consultant has found that they performed work based on conversations with a client's employee, and then found that the client balked in making payments for that work, since they considered it unauthorized—the person had no authority to direct a consultant to perform that function. It is imperative that you and the client both have a clear understanding of what is agreed to, when it will be accomplished, proof that it was accomplished, and the fees relative to completing the work. Notes help when discussing the work performed, and especially in dealing with the billing process. An excellent technique to use during the engagement management process is to monitor the progress of the engagement on a daily basis. Constantly communicate with the client the progress (or lack of it) and delineate why there are delays. If there are delays due to a fault on the part of the client, inform the client of the impact to the engagement and give choices such as:
-
Ask for additional funding,
-
Abbreviate certain tasks, or
-
Eliminate certain tasks.
This technique helps avoid unpleasant surprises and misunderstandings. It's a "we" mentality. You approach your counterpart project manager and say "Joe, we've got a problem. The project is behind because of this, this, and this. How do you think we can fix this?" If the project is screwed up, Joe has just as much to lose politically as you do monetarily. If there is a debate as to why things aren't going well, the events are fresh in everyone's minds and it's easy to sort out and correct or compensate. A common mistake is to wait until near the end of the engagement when things are way behind schedule and inform the client, thinking that somehow everything might work out. This will end up in a best-case scenario as souring the client relationship and worst-case, in court arguing over who did what when.
If there are delays due to your own performance or lack of planning, work extra hours and accept the loss. Do whatever you have to do to meet the objectives of the proposal, and don't complain about it. Make careful notes as to why you miscalculated or undermanaged the engagement, and use that knowledge when writing your next proposal.
Assessment Services
You may want to break your services into various groups. One group may be "assessment services." This should have been decided as part of your business plan. These services include such things as penetration testing and security tests and evaluations of software, systems, and it may include supporting documentation analyses. Also included may be technical security countermeasures (TSCM), audits, and risk assessments.
Advisory Services
Advisory services, also previously considered as part of your business plan, include the following:
-
Technical design review;
-
Policies, procedures, and guidelines;
-
Security change management;
-
Systems and network security; and
-
Security architecture.
Security Implementation
The services to be considered, based on your expertise, of course, include ensuring that products to be installed on systems don't make the systems and networks more vulnerable and any security software meets the needs of the business and operates as advertised. Again, be sure to document everything.
Augmentation
Augmentation services may include such things as termination surveillance and assisting in client investigations of employees, such as computer forensic services. You may also be requested to respond to incidents. If so, this should be addressed in your contract, and also the billing for such responses—which often seem to happen after midnight.
Legal Issues
Legal issues may arise as to your authority in conducting or assisting in high-technology crime investigations; as well as issues related to your contract. It is imperative, to avoid legal problems later, that all matters be clearly and concisely stated in the contract. The worst thing you would want is conflicts in contract interpretations, delayed payments, or refusal to pay what you billed the client, not to mention the problem of your reputation, which will follow you (good and bad) from client to client.
Above all, never begin an engagement without a signed contract. Make certain that the person signing it has the legal right to do so for the organization (usually an officer or director).
International Aspects
More and more InfoSec consultants are working all over the world and with foreign clients. In dealing with such clients, it is important to:
-
Avoid slang, colloquial terms;
-
Learn as much of the foreign language and culture as possible;
-
Make positive comments on the food and architecture;
-
Use local hand gestures and volume of speech;
-
Understand the foreign governments where you will be working;
-
Understand the latest terrorist threats in the region;
-
Explain InfoSec terms in local context;
-
Don't complain about their country or culture or brag about yours; and
-
Avoid political discussions or, if you are dragged into a conversation, remain neutral.
[1]Some of the information provided in this chapter was provided by Steve Lutz, President, WaySecure, a very successful international security consultant and InfoSec specialist for decades.
[2]Figure 17.1 is courtesy of Steve Lutz, President, WaySecure.
|
EAN: 2147483647
Pages: 204