Configuring Smart Client and Server Precursors
| If clients will be allowing smart updates from an external Internet site, those clients will need to be configured correctly to support downloading executable .NET assemblies. This section describes a manual process for configuring those clients. (Because manually configuring a large number of clients may not be practicableand customers may not want to bother themselves we will talk about automating the security policy information in the Creating a Microsoft Installer File to Manage Security Policies section later in this chapter. As an overview, here are the summarized precursors for client workstations to support smart updates. Clients will need:
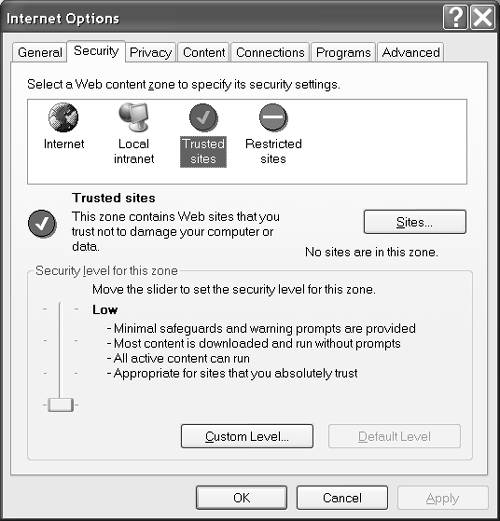
Let's take a moment to look at the implications of each of these precursors and review the steps necessary to support smart updates on the client. Connecting to the InternetConnecting to the Internet sounds simple, but there are some specific implications relative to smart client updates. The first fact you should know is that .NET assemblies tend to be quite small because a lot of the functionality exists in the framework. This means quite complex applications will have relatively small, binary assemblies. The benefit is that even relatively slow dial-up connections should be able to download new clients. On the other hand, if the client workstation is not connected, a direct Assembly.LoadFrom method will fail even if the assembly has already been cached. You will get a FileNotFoundException on the client because either the file can't be found on the server or the file on the client cannot be compared to the file on the serverboth because there is no Internet connection. To work in offline mode you will need to devise some strategy that uses a fail-over scheme if the online assembly can't be found. Installing the .NET FrameworkIt has been amazing to hear about the resistance some people and companies have to installing the .NET Framework. PCs that run something as small as a Java applet have Java on them. PCs that run applications written in Delphi have some Borland runtimes on them. Visual Basic 6 applications drag along the VB runtime, and every Windows user has tons of disk space taken up in API DLLs and probably Microsoft Office DLLs too. Runtimes , frameworks, and APIs exist to factor out commonality so you are not paying storage costs for the same code over and over. Microsoft's .NET Framework is not significantly different in size than Java's Java Runtime Environment (JRE) or Borland's Visual Control Library. The 20 cents it costs for the 20MB in storage space for the .NET Framework isn't worth mentioning. The benefits you will get from this world-class framework are priceless. You can download and install the framework from the Microsoft software or obtain a redistributable copy from your Visual Studio .NET distribution disks. I suspect that your next Windows upgrade will include the .NET Framework for obvious reasons, including the likelihood that many Microsoft applications will have been ported to .NET. Adding to the Trusted Sites ListHaving an Internet connection and the .NET Framework are obvious enough. However, if you want customers to be able to download your smart clients, including the application launcher, from the Internet, customers will need to make some adjustments to their browsers. I run my computer footloose because I would rather restore an image on the very rare occasion I might download something nasty than have restrictions on what I can do while surfing. To ensure your customers can download executables, like your application launcher's assembly, have customers add your Web site to the workstation's list of trusted sites. Clearly customers will have to trust your company and want your product to be motivated to add your company to their trusted sites list. To adjust the browser security, follow these steps.
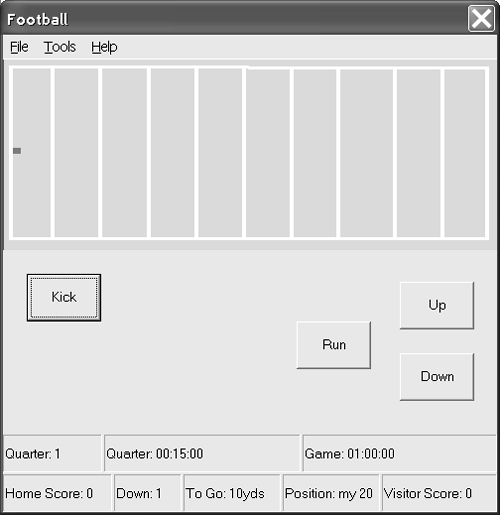
Fun applications to experiment with are the Wahoo! game, available for download at http://www.sellsbrothers.com/Wahoo/Wahoo.exe, and the Football game (Figure 10.4), available at http://www.softconcepts.com/Football/Football.exe. (The latter is based on the popular Mattel football game from the 1970s. Apparently the game is making a comeback along with all the other retro 1970s memorabilia, and I got one for Christmas. I thought it would be fun to write a version for my PC, thus improving my chances of beating the sharper mind and reflexes of my wife, Lori.) Figure 10.4. A snapshot of the Football game in prototype form, as an example of a smart client Windows Forms application.
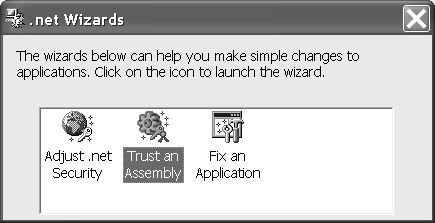
Adjusting Security Policy for Application AssembliesChapter 18 covers the management of security policies in more depth. For now we need a convenient and reliable way to manually allow clients to run our smart client assemblies downloaded from the Internet. The easiest way to do this is to run the Microsoft .NET Framework wizard, Trust an Assembly. To indicate that an individual assembly downloaded from the Internet can be trusted and allowed to run, follow these steps.
At this point you can point your browser to http://www.softconcepts.com/Football/Football.exe and the executable will download and start running automatically. (You should see the latest update of the game, similar to the game shown in Figure 10.4.) You may want to experiment with varying degrees of trust for each assembly you want to download and execute from any specific provider. As an application implementer you want your customers to give you as much trust as possible; while as an application consumer you want to yield only as little trust as is necessary. Unfortunately there are few blanket rules for security, especially when it comes to the World Wide Web. As mentioned, we will talk more about security in Chapter 18.
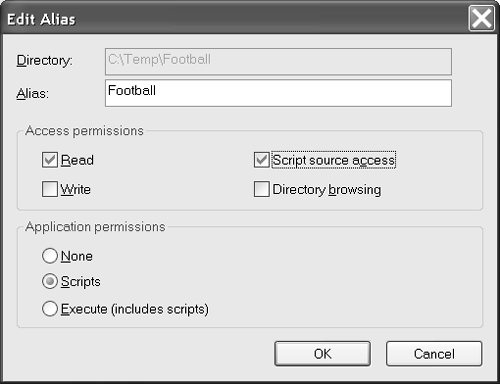
Configuring Server Precursors for Smart Client AssembliesWhen you are configuring a Web site, you want to limit permissions to only those absolutely needed by your legitimate customers. There are enough people in the world trying to hack Web sites for fun and profit, and you and I don't need to encourage them. To permit customers to download your smart client assemblies from an intranet or the Internet, set access permissions to Read and application permissions to Scripts, as shown in Figure 10.6. Figure 10.6. Set access permissions to Read and application permissions to Scripts for shared Web directories that contain smart client assemblies. You can create any executable assembly and set Web sharing by right-clicking on the folder containing the executable, selecting the Sharing and Security context menu item, and navigating to the Web Sharing tab. The Web Sharing tab can be used to create a virtual directory and set permissions for that virtual directory. This shortcut yields the same results as establishing a virtual directory from the management console for IIS. Figure 10.7 shows the virtual Football directory in the management console on my laptop. Figure 10.7. You can create a shared Web directory in Windows Explorer or the management console for IIS. |
EAN: 2147483647
Pages: 215