| In this section of the chapter, I will cover a wide range of example Trojans and worms. I will spend more time on the first Trojan, Back Orifice, because it is representative of the largest Trojan threats. 6.7.1 Back Orifice Back Orifice 2000, or BO2K, as it is known, was released in July 1999 under the public GPL GNU license. It is free for anyone to use or modify. It is very configurable, with point and click GUI configuration screens. The Back Orifice Trojan, like most RATs, has two parts : a server and a client. The server portion is preconfigured by the hacker and then somehow placed on the victim's machine. When the server program is executed, it automatically installs itself, hides its presence, and opens a new port number on the host machine. Often, if the right plug-in is included, it will email the hacker with the IP address of the new host victim. The client program is used by hackers to locate and manipulate server programs. The client and server programs must match many configuration parameters in order to find each other. A client using the common port number of 31337 over TCP with XOR encryption will not work with a server using the UDP protocol or CAST-256 encryption. As shown in Figure 6-2, Back Orifice has a user -friendly GUI to help configure the server executable that will be placed on the victim's PC. Figure 6-2. Back Orifice's server configuration GUI 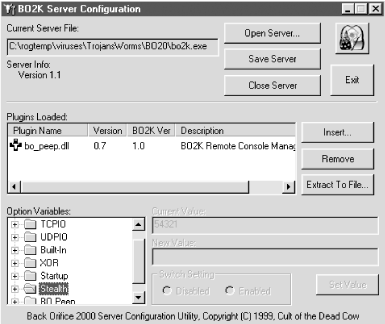 Using the Back Orifice 2000 Server Configuration Utility , a hacker can configure a whole host of server options including whether to use TCP or UDP, what port number to use, the encryption type, the stealth (which works better on Windows 9x machines than on Windows NT) password, and the use of plug-ins. Back Orifice has an impressive array of features including keystroke logging, HTTP file browsing, registry editing, audio and video capture, password dumping, TCP/IP port redirection, message sending, remote reboot, remote lockup , packet encryption, and file compression. It comes with its own software developer's kit (SDK) to allow its functionality to be extended by plug-ins. Once running, the server portion of the program runs on the host machine waiting for a client to connect. The server can simply open a particular predefined port number by starting its service (daemon process) or if installed with the Butt Trumpet plug-in, it will send an email to the client originator as a predetermined email address. In these cases, the hackers usually choose a portal email system (e.g., Yahoo, Hotmail, etc.) where it is easy to be anonymous. Thus, the hacker can start a new email account, escape detection, and close it if needed. If Back Orifice is running on a system, it can use its stealth abilities to hide from prying eyes. The server program will not appear on the task list, or if it does, it can appear as any legitimate executable name . Early versions of the Trojan allowed the filename to appear blank, and thus, the whole filename would be .EXE . By default, after the server program is installed on the host machine, it deletes the original Trojan file. Although Back Orifice network packets have a unique signature that can be monitored , BO2K has the ability to modify its data packet headers so they are not conspicuous. The only consistent, reliable way to detect Back Orifice is to use NETSTAT -A , and look for new ports that should not be opened on a particular machine. It also can't hurt to have a scanner or firewall that can detect BO scans . In Example 6-5, NETSTAT -A reveals Back Orifice running on port 31337. The client is using port 1216 on the remote machine. The server connects to the client and can begin to send commands to control the server. The Back Orifice client offers an array of features and commands that can be sent to the server portion of the program. Pick a command or feature and select the Send Command button to control the server located on the host machine. In Figure 6-3, I sent a text message to the server program. Example 6-5. Netstat -Example with Back Orifice running on port 31337 and a client using port 1216 on the remote machine Active Connections Proto Local Address Foreign Address State TCP roger:5679 ROGER:0 LISTENING TCP roger:137 ROGER:0 LISTENING TCP roger:138 ROGER:0 LISTENING TCP roger:nbsession ROGER:0 LISTENING TCP roger:31337 ROGERLAP:1216 ESTABLISHED UDP roger:nbname *:* UDP roger:nbdatagram *:* Figure 6-3. The Back Orifice client 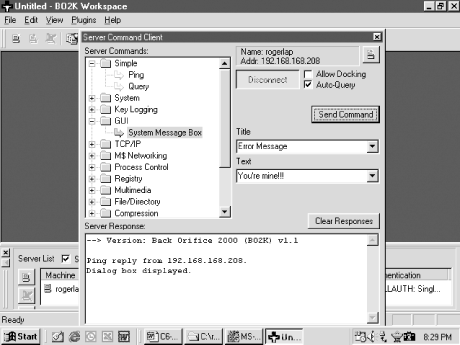 Most of the time the server process is invisible to the user, although the slightest syntax or process error on behalf of the client will cause a noticeable runtime error on the server. Back Orifice's developers didn't put in enough error-checking code in their server program. Still, most of these errors don't kill the server program (some do), and most victims don't know that the error on their screen has anything to do with a Trojan. If a machine is compromised by a RAT, the remote hacker can do anything the local user's security allows. Although most RATs are operated by teenagers without serious harmful intent, malevolent deeds can easily be accomplished. Many within the security industry believe corporate spying is occurring on a grand scale. A business competitor could read a company's financial statements, future strategies, cost breakdowns, and intended sales prices, and record the audio and video feeds of important conversations. A report in a 1996 edition of Government Information Technology Issues magazine revealed that the FBI is investigating at least 250 major hacking crimes at any one time. In order for the FBI to be involved the crime must be of a significant dollar amount and cross state lines. The same report said over $800 million of extortion money has been paid to hackers in the last few years , while 83 percent of hacker- related cases go unreported. This 1996 report was released before the release of easy-to-use RATs. Statistics today would easily quadruple those amounts. Increasingly, protecting the privacy of our home machines is important. Figure 6-4 shows one of the most serious types of threats from a RAT. A Back Orifice server is running on a host computer. In this example, the user is connecting to his online bank to check his bank balance. The client portion of Back Orifice was used to send a fake message to prompt the user for their Visa account information. Figure 6-4. Remote access Trojans can easily compromise security 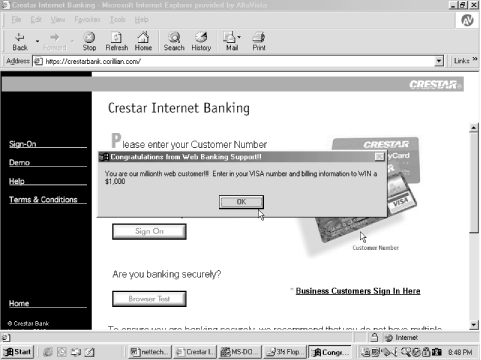 Even if a user didn't fall for this trick, the remote hacker is watching the customer put in his account and PIN number. The hackers could then view financial transactions, transfer money, and withdraw cash (at the ATM). Everywhere the user goes, the hacker can go. In the world of malicious mobile code, backdoor Trojans and RATs rank high on the list of realistic threats. 6.7.2 PICTURE.EXE Trojan In late December/early January 1999, an email Trojan was spammed to several newsgroups with an attachment called PICTURE.EXE or MANAGER.EXE . If run, it copied itself to the Windows directory as a file called NOTE.EXE . It then added a RUN line to WIN.INI . When loaded, it searched all the local hard drives for JavaScript and HTML files, and saved the list of found files to $2321.DAT . Next , it would look into the user's WINDOWS\TEMPORARY INTERNET FILES subdirectory and write the list of URL's found to a file called $4135.DAT . It also looked for and recorded any AOL login names and passwords. Next, it sent files to two separate email addresses, abreb@hotmail.com and chinafax@263.net . Both accounts are easy to setup and not linked to any particular user or computer. Later versions of this Trojan broadcasted its presence to known hacker sites and awaited predefined commands from client computers. 6.7.3 Win32.Ska-Happy99 In early January 1999, an email began arriving with an attachment called HAPPY99.EXE . When executed it displayed fireworks on the screen with a message, "Happy New Year 1999." The Trojan copies WSOCK32.DLL to WSOCK32.SKA , and modifies the original to contain the Trojan. WSOCK32.DLL is the main Windows file for communicating with the Internet. The modified copy now allows the worm to insert itself into the Internet communication's process. Files SKA.EXE and SKA.DLL are created in the System directory and the registry is modified to run SKA.EXE on startup. Every email or newsgroup posting sent by the user will generate a second copy (without any message text) containing the Trojan, to the same recipients. This second email is barely noticeable and the invaded user's outbox will not show signs of the Trojan. A file called LISTE.SKA is maintained in the System folder to keep track of what recipients have already received the Trojan. 6.7.4 Win32.ExplorerZip ExplorerZip was released in Israel, October 6, 1999, on the heels of the Melissa virus attack. Within four days, it had shut down email at more than 20 major U.S. companies, including Microsoft, Intel, GE, Boeing, and AT&T. It arrives in an email attachment with the following text: "I received your email and I shall send you a reply ASAP. Till then, take a look at the attached zipped docs." It arrives from someone the recipient sent email to recently. The attachment, named ZIPPED_FILES.EXE , has a WinZip icon. Although not really a zipped file, it was realistic enough to fool most people. Users who ran the file received the following error message: "Cannot open file: it does not appear to be a valid archive. If this file is part of a ZIP format backup set, insert last disk of the backup set and try again. Please press F1 for help." It may have appeared as if the unzipping failed, but the worm now invaded the user's system. The worm copies itself to the user's Windows System directory as EXPLORER.EXE or to the Windows directory as SETUP.EXE and loads itself from the WIN.INI file (Windows 9x) or the registry (NT). When activated, it will search for files on drives C to Z with the following extensions, .C, .CPP, .H, .ASM, .DOC, .XLS, and .PPT , and replace them with 0 byte files. This effectively makes the files deleted and unrecoverable. It then sends itself via email using Outlook, Outlook Express, or Exchange mail to recipients found in unread messages in the inbox. It monitors all incoming messages and replies to the sender with a copy of itself. It inserts a tab character at the end of each subject line to recognize which messages it has already replied too. The worm is visible on the task list as Zipped_ files or Explore or _setup. Unlike Melissa, ExplorerZip was very malicious. This is unusual for any widespread code, because very malicious programs get noticed and cleaned quickly. But the worm's email ability allowed it to spread more quickly than it could be cleaned. The worm was released in a second version a few days later, compressed by the NeoLite program, and most scanners (even the ones recently updated to reflect the first worm) did not detect the new variant. 6.7.5 Win32.PrettyPark First discovered in June 1999, PrettyPark is a typical worm arriving as an email attachment called Pretty Park.EXE . The executable, written in Delphi and compressed with WWPack32 , can arrive with an icon of Kyle, the SouthPark  cartoon character, as shown in Figure 6-5. cartoon character, as shown in Figure 6-5. Figure 6-5. PrettyPark worm icon  When the worm is executed for the first time, it copies itself as a file called FILES32.VXD (it's not a true VXD file) to the Windows System directory and modifies the registry to run as a hidden application each time any other application is started. This is a common mechanism for many Trojans and worms today. They accomplish this feat by modifying the registry, specifically the HKCR\exefile\shell\open\command or HKLM\Software\CLASSES\exefile\shell\open\command keys. Typically, either of these keys are blank or they will contain the default value of "%1" %*. The worm changes the value to files32.vxd"%1" %*, which has the effect of running the worm each time any EXE program is executed. If a worm modifies a system in this way, you must remove the Trojan code in the registry keys prior deleting the Trojan files, or else you will not be able to run most applications, including REGEDIT.EXE to fix the problem. This worm also has a unique way of reacting to runtime errors. Most worms and Trojans tell the code to skip past the error and continue executing. PrettyPark attempts to launch either the SSPIPES.SCR (3D Pipes) or Canalisation3D.SCR screensavers, to hide any resulting error message. After installing an IRC client and a related IRC script file, the worm then contacts a predetermined set of IRC servers over the Internet to notify the originator of the latest compromised system. If the distributor of the worm is monitoring the same IRC channel, they can then request system information from the compromised system (e.g., computer name, registered owner, system root path , dialup networking logon names and passwords, and the victim's email address). Every 30 minutes it attempts another IRC communication and sends itself to everyone within the Outlook address book. 6.7.6 JS.KAK.Worm Released on at the end of 1999, JS.KAK is a JavaScript email worm that is spreading quite rapidly in the wild. It arrives as either as an attachment or as an email signature. The first versions only infected Outlook Express email messages and did so by inserting itself as a signature. The signature feature of email systems automatically append predefined text or graphics to any email sent by the user. JS.KAK takes advantage of this and copies its code to the signature of any email sent ( newer variants arrive as email attachments). The infected email with the bogus signature arrives in the next victim's Outlook inbox. Then when the email is opened (or even previewed in Outlook Express), it automatically compromises the system without the user having to open an attachment. It does this by exploiting a little-known Internet Explorer hole (Scriptlet.Typelib, covered in Chapter 11). The BubbleBoy worm, discovered on November 15, 1999, was the first to spread this way, but it isn't as common. JS.KAK copies its code to a file called KAK.HTA and places it in the Windows Startup directory, where it is automatically executed by Internet Explorer upon reboot. Different versions copy to C:\Windows , C:\Windows\System , C:\Windows\Menu , or C:\Windows\Start Menu\Programs\StartUp . It modifies the registry to place itself as a signature in Outlook Express (HKEY_Current_User/Identities/<identity>/Software/Microsoft/Outlook/Express/5.0/signatures). All future sent email will carry a copy of the worm. The registry is also modified so the HTA is automatically run upon boot up. The original worm originated in France and contains the code to correctly place itself in the Startup directory in the French-language version of Windows. Some versions of JS.KAK modify the AUTOEXEC.BAT to run the HTA on startup. JS.KAK can also write a short HTML file, KAK.HTM , which will run and install the Trojan if executed. With three to four different startup methods , this worm can be particularly difficult to prevent from reappearing. The worm contains a slightly malicious payload. On the first day of any month at 5:00 P.M., JS.KAK displays the following message, "Kagou-Anti-KroSoft says not today!" and it attempts to shut down Windows. Unsaved data can be lost. Users who do not disable the mechanisms the virus uses to spread (covered at the end of this chapter) can recompromise themselves by viewing an infected email message in their Sent box. The preview mode of Outlook Express is enough to launch the virus. 6.7.7 Bat.Chode.Worm On March 31, 2000, the FBI's U.S. National Infrastructure Protection Center issued a press release (http://www.nipc.gov/warnings/advisories/2000/00-038.htm) warning the public against a new worm family. The worm contains a mixture of the DOS batch file language, Visual Basic Script, .PIF files, and occasionally, an executable. Most of the replicating code is programmed in the DOS batch file language. The feature that is most troubling for the feds is that the Trojans will use modems to repeatedly dial 911. It does this with a simple command, ECHO AECHO ATDT 911 , redirected toward a COM port, which is sufficient code to make a modem dial a number. Enough metropolitan cities were hit with the bug (e.g., Houston, Texas) that the FBI felt the Trojan was a threat to our nation's 911 infrastructure. Potentially, if enough worms activated at once, it could have caused a denial of service incident with the 911 emergency number and prevented sick or injured persons from recieving prompt medical care. The worm stores itself and a log file of its activities in a subdirectory called C:\Program Files\CHODE . It also uses an interesting methodology to spread. Chode cycles through a list of well-known ISPs (e.g., ATT Worldnet, PSInet, Earthlink, and Mindspring) looking for a valid Internet connection. It looks for and maps to an accessible Windows C drive share. It then looks to see if it has already compromised the new share, and if not, proceeds to copy itself to the new host. Chode uses two stealth techniques, which is surprising for a malicious batch file program. First, it hides its activities by using a freeware utility called ASHIELD . This free executable is included with the Trojan and is called when necessary. Chode also installs ASHIELD.PIF and NETSTAT.PIF in the Startup directory, and the .PIF files help to hide the worm further when it is started. A Visual Basic Script file, WINSOCK.VBS , is also installed in the Startup directory. It contains the payload routine of the virus and on the 19 th of any month, it will delete files in C:\ , C:\windows , C:\windows\system , and C:\windows\command , and then it will display a vulgar message. 6.7.8 Win32.Qaz Discovered on July 18, 2000, the high-level network Trojan, worm, and virus, Qaz, has the distinction of having been successfully used to invade Microsoft Corporation. It was discovered that Qaz's backdoor Trojan component had possibly been used for weeks by a hacker, or hackers, to poke around on Microsoft's corporate network near the end of 2000. Because Microsoft released several varying and inconsistent public statements about how long the Trojan had been on their network and what it had been used for, the public learned that even supposedly sophisticated, secure networks were easily exploited. Even though later contradicted, Microsoft said that new versions of their software had been stolen by the hackers. There were even unconfirmed rumors that hackers had placed a secret back door in Microsoft's beta software that would make future released versions universally vulnerable. Although the rumor was probably without merit, it demonstrated the power of unmanaged malicious mobile code to cause damage to a company's goodwill. First discovered in China, Qaz usually arrives in an email attachment, although it has no coding of its own to spread that way. Once executed, it acts as a companion virus, searching for and replacing NOTEPAD.EXE with itself on all found network drives. When the virus code in NOTEPAD.EXE is run, it will also launch a stored original copy of NOTEPAD (now stored in NOTE.COM ) to escape detection. It adds itself to one of the Run keys in the registry as start IE "notepad qazwsx.hsq." Once a computer is infected, it emails the virus author the IP address of the compromised computer and installs a Winsock backdoor that listens on TCP/IP 7597. As demonstrated in the Microsoft attack, Qaz is in the wild and working. 6.7.9 Life Stages Worm The Life Stages worm arrives in infected emails with randomly selected subjects and texts . A file called LIFE_STAGES.TXT.SHS is attached, but because of the Windows default hiding ability it will appear as LIFE_STAGES.TXT to most users. Because it looks innocent enough, most users open it. The .SHS file is a Windows scrap file pointing to a Trojan executable. While displaying a simple message to the user using Notepad, the Trojan begins to modify the system. Several copies of the worm and a few VBS scripts are created. Life Stages copies itself to the user's desktop and into the Recycle Bin. Worm files called MSINFO16.TLB , SCANREG.VBS , and VBASET.VLB are copied to the Windows System directory, and the worm will place itself in the Startup folder and startup areas of the registry. It then copies REGEDIT.EXE (in most cases it does not touch the NT version, REGEDT32.EXE ) into the Recycle Bin as RECYCLED.VXD and redirects .REG associated files to the worm program. It attempts to look for IRC programs on each local drive, and if any clients are found, it will send itself out to all open IRC channels. It then uses Outlook to send out copies of itself to 100 random names in the user's address book. In most instances, all this worm activity slows down the compromised machine considerably. Although it has no intentionally destructive payload beyond its replication mechanisms, it can quickly overwhelm a company's email system, and its myriad changes to each PC can make cleanup difficult. |