Authorization and Authentication
Bluetooth supports several security modes: Security Mode 1 (nonsecure), Security Mode 2 (service-level enforced security), and Security Mode 3 (link-level enforced security).
In Security Mode 1, all protection systems are disabled. Neither authentication nor encryption is supported, and the Bluetooth device operates in the broadcasting mode, also called the promiscuous mode. This allows hackers to build sniffers based on the available components .
When a Bluetooth device operates in Security Mode 2, the authentication process starts immediately after establishing a connection. Authentication is carried out by the security manager according to the Logical Link Control and Adaptation Protocol (L2CAP). The security manager operates at the data-link layer and interacts with higher-layer protocols. This allows the user to selectively restrict access to the Bluetooth device (for instance, everyone can view data but cannot modify it).
In Security Mode 3, authentication takes place before establishing the connection. It takes place at the data-link layer; therefore, all unauthorized devices will be discarded when the connection is established. Security Mode 3 supports dynamic encryption of traffic without participation of the higher-layer protocols, which ensures the maximum level of security and comfort . However, even in this case the protection level is relatively low, and the device can be easily hacked.
The foundation of Bluetooth security is key generation (Fig. 29.6). Keys are generated on the basis of PINs. This code is a number from 1 to 16 bytes in length, assigned by the device owner and stored in nonvolatile memory. Most mobile devices use a 32-bit PIN, which is set to 0 by default. Some devices refuse to operate with the PIN set to 0, forcing users to change it to something like 1234. However, cracking such trivial PINs is not interesting.
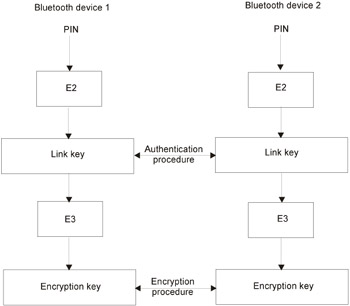
Figure 29.6: Generation of the private keys on the basis of the PIN
A PIN is used by the system to generate a 128-bit link key computed according to the E2 algorithm. The link key, in its turn , is used for generating a 128-bit encryption key computed according to the E3 algorithm. The link key is used for authentication, and the encryption key is for traffic encryption.
Authentication is carried out according to the classical challenge-response method, which is as ancient as the computing world itself. The user logon in UNIX and the one in Windows NT are built on the basis of the same principles (Fig. 29.7). The sequence of operations is as follows :
-
The initiator of the connection (claimant) sends its unique 48-bit hardware address ( BD_ADDR ) to the device that is expected to respond (verifier). In a certain sense, this hardware address is similar to the MAC address, which is hard-encoded into the network adapter.
-
The verifier generates a random 128-bit challenge, designated as AU_RAND , and passes it to the claimant.
-
The verifiers uses the BD_ADDR , link key, and challenge to generate a secret encrypted sequence ( SRES ). The claimant carries out the same operations.
-
The claimant passes the resulting SRES to the verifier.
-
The verifier compares the SRES that it has computed with the response obtained from the claimant. If these values match, then the verifier establishes the connection.
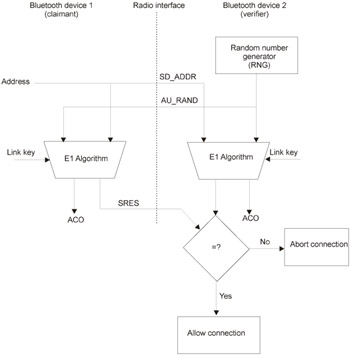
Figure 29.7: The authentication process
Thus, the PIN is not transmitted as plaintext; therefore, a hacker cannot eavesdrop on it. However, it is still possible to guess it. It is even possible to eavesdrop on BD_ADDR, AU_RAND , and SRES , after which the intruder would be able to choose a link key that would produce an identical SRES , provided that the BD_ADDR and AU_RAND values are given. On Pentium 4, cracking a four-character PIN takes seconds.
Interesting Links Related to Encryption Algorithms
-
"Wireless Network Security." An excellent manual on wireless network security, containing detailed description of authentication and encryption protocols: http://csrc.nist.gov/ publications /nistpubs/800-48/NIST_SP_800-48.pdf .
-
" Bluetooth Security ." A good article describing encryption and authentication protocols: http://www.niksula.cs.hutfi/~jiitv/bluesec.html .
-
"Bluetooth Security: Protocol, Attacks and Applications." A PowerPoint presentation, containing an overview of the key features of the cryptographic algorithms used by Blue-tooth for encryption and authentication: http://www.item.ntnu.no/fag/ttm4705/kollokvie_presentasjoner_2004/bluetooth_security.ppt .
EAN: 2147483647
Pages: 164