Methods of Attack
The three most widely implemented types of attack on Bluetooth networks are Blu-etracking, Bluesnarfing, and Bluebugging. All of these attacks are based on vulnerabilities of the Bluetooth protocol stack (Fig. 29.8).
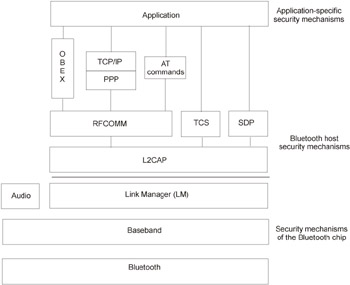
Figure 29.8: The Bluetooth protocol stack
Bluetracking attacks are based on the device address, BD_ADDR , being passed into the network as plaintext, because of which it can be easily sniffed and decoded. The hacker can determine the device manufacturer, its model, and its origin. A group of hackers, distributed over an entire city and armed with random antennae, can easily track the movements of the victim.
The series of much-talked-of Bluesnarfing attacks is still covered with a veil of mystery. Before the eyes of a wonder -stricken community, hackers steal notes, contacts, address books, archives of SMS messages, and other private information. How do they manage this? Hackers smile but do not rush to explain. Bluetooth developers confirm the possibility of attack ( http://www.bluetooth.com/help/security.asp ); however, they do not make technical details freely available to the user community. On many mobile devices, the Object Exchange (OBEX) service works in a nonsecure mode, without requiring any authentication. For example, this is typical for cellular phones from Sony Ericsson (in particular, models T68, T68i, R520m, T610, and Z1010), Nokia (6310, 6310i, 8910, and 8910i), and Motorola (V80, V5xx, V6xx, and E398). As relates to Siemens, all models always operate in secure mode.
Attacks of the Bluebugging type (also called Blue Bug) are a kind of Blue-snarfing attack; however, instead of exchanging objects, AT commands are sent using the same OBEX protocol. AT commands are normal communications commands known to anyone who actively works with modems. Using these commands, it is possible to send SMS messages, make phone calls at the expense of the victim, and even surf the Internet using the WAP or GPRS protocols. No authentication is needed to carry out all these actions. Bluebugging is serious, so owners of the previously-listed unreliable cellular telephones operating in the nonsecure mode are strongly advised to always make sure that Bluetooth is off.
Even secure telephones such as those by Siemens can be cracked by a brute-force attack. As was already pointed out, a 4-byte (32-bit) PIN can be cracked in seconds. Even if the manufacturers increase the length of PIN to 16 bytes, this won't prevent hackers from attacking Bluetooth-enabled devices. However, it would create considerable problems to users. Such a PIN would be hard to memorize, and this means that users would tend to use meaningful "dictionary" numbers , which would simplify brute-force attacks on PINs.
In total, there are more than 20 types of attacks, and it would be too tiresome to list them all here. If you are interested in this topic, you can read the " Wireless Network Security " book and other similar documents.
Interesting Links Related to Bluetooth Security
-
"Preliminary Study: Bluetooth Security." An overview of the main attacks at Bluetooth: http://student.vub.ac.be/~sijansse/2e%20lic/BT/Voorstudie/PreliminaryStudy.pdf .
-
"Wireless Security." Descriptions of the main Bluetooth vulnerabilities confirmed by its developers: http://www.bluetooth.com/help/security.asp .
-
"Hardware Hacking." A chapter of an excellent manual for hardware hackers: http://www.grandideastudio.com/files/books/hpyn2e_chapterl4.pdf .
EAN: 2147483647
Pages: 164