Active Sniffing or ARP Spoofing
When sending a packet to the specified IP address, it is necessary to deliver it to a specific network host. However, to which host is it necessary to deliver the packet? After all, the network adapter operates only with MAC addresses and has no information about IP ones. Consequently, it is necessary to have the table that would map each MAC address to the corresponding IP address. The task of building such a table is delegated to the operating system. The operating system achieves this goal using ARP. If the physical address of the recipient is not known, then a broadcast request is formulated approximately as follows : "Host with the given IP address, please report your MAC." Having received the response, the host inserts it into its local ARP table. For reliability, the local ARP table is periodically updated (actually, the ARP table represents a normal cache). Depending on the type of operating system and its configuration, the update interval can vary from 30 seconds to 20 minutes.
No authorization is required for updating the ARP table. Furthermore, most operating systems readily interpret ARP responses even if they were not preceded by appropriate ARP requests (SunOS is one of the few systems that will not be deceived in such a way; therefore, a fictitious ARP packet must be sent only after the appropriate ARP request but before the arrival of the actual response).
To capture an IP belonging to someone else, it is enough to send a fictitious ARP request that might be either directed or broadcast (for sending and receiving ARP packets, it is necessary to have access to raw sockets or the special API of the operating system; more details can be found by analyzing an arp utility). Assume that the attacker wants to grab the traffic between hosts A and B. In this case, the attacker sends a fictitious ARP response to host A. This fictitious ARP response contains the IP address of host B and the attacker's MAC address. To host B, it sends an ARP response containing the IP address of host A and the attacker's MAC address. Both hosts update their ARP tables, and all packets that they send are delivered to the intruder's host, which either blocks them or delivers them to the recipient (possibly, in a slightly modified form, in which case it operates like a proxy). If the intruder sends a fictitious ARP packet to the router, then the intruder will also be able to capture the packets that arrive from outside the given network segment. An attack of this type is known as a Man-in-the-Middle (MiM) attack (Fig. 27.4).
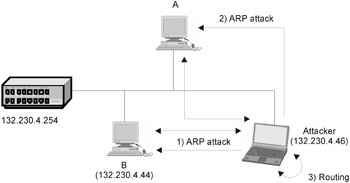
Figure 27.4: Attack of the MiM type, even in networks with an intellectual hub
As a variant, it is possible to send a fictitious ARP response with a nonexistent MAC address, in which case the connection between A and B will be lost. However, this connection will be automatically restored, because the ARP table is dynamically updated; to avoid this, the attacker must send a powerful storm of fictitious packets to the target computer (Fig. 27.5).
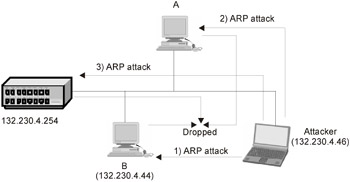
Figure 27.5: Terminating a connection between hosts
By the way, if the router doesn't route the arriving packets in time, it automatically switches to the broadcast mode and begins to operate as a normal hub. Thus, the attacker can overload the router (or wait until the peak network load is reached) and then sniff the traffic in passive mode.
Detecting Active Sniffing
The active nature of the ARP attack discloses the intruder, and network analyzers such as arpwatch easily detect network sniffing (Fig. 27.6). They grab all packets that travel across the network (in other words, operate like sniffers), retrieve ARP responses, and store them in the database, remembering, which IP address maps to which MAC address. When discrepancies are detected , an email message is sent to the administrator. However, at the moment this message arrives to the destination address, the intruder can escape with all the traffic grabbed already. Furthermore, in networks with DHCP servers (the ones responsible for automatic assignment of IP addresses), arpwatch operates with a large number of false positives. This happens because different IP addresses are assigned to the same MAC address.
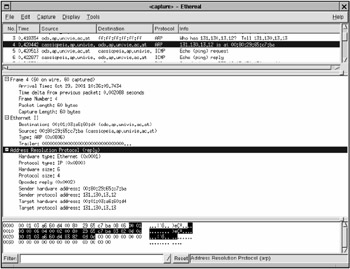
Figure 27.6: Capturing a fictitious ARP request
Some operating systems can detect on their own the capture of their IP addresses by a foreign host; however, this is possible only if the intruder has used broadcast sending. This is a rare event, because intruders are not fools. In addition, for some unknown reason, the operating system doesn't send an ARP response, recapturing the stolen IP. On the contrary, the operating system usually is limited to a warning message, which ordinary users are unlikely to understand.
A static ARP table formed manually appears more attractive. However, lots of operating systems still continue to receive fictitious ARP responses, obediently allowing intruders to do whatever they want. It is difficult to persuade them not to behave this way, especially for users that are not gurus.
EAN: 2147483647
Pages: 164