Threat Modeling Principles
Threat modeling should not be a one time only process. It should be an iterative process that starts during the early phases of the design of your application and continues throughout the application life cycle. There are two reasons for this. First, it is impossible to identify all of the possible threats in a single pass. Second, because applications are rarely static and need to be enhanced and adapted to suit changing business requirements, the threat modeling process should be repeated as your application evolves.
The Process
Figure 3.1 shows the threat modeling process that you can perform using a six-stage process.
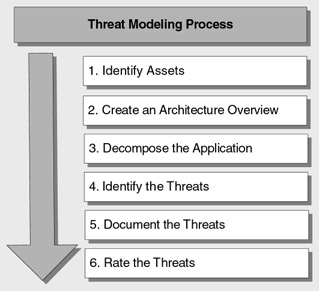
Figure 3.1: An overview of the threat modeling process
| Note | The following process outline can be used for applications that are currently in development and for existing applications. |
-
Identify assets .
Identify the valuable assets that your systems must protect.
-
Create an architecture overview .
Use simple diagrams and tables to document the architecture of your application, including subsystems, trust boundaries, and data flow.
-
Decompose the application .
Decompose the architecture of your application, including the underlying network and host infrastructure design, to create a security profile for the application. The aim of the security profile is to uncover vulnerabilities in the design, implementation, or deployment configuration of your application.
-
Identify the threats .
Keeping the goals of an attacker in mind, and with knowledge of the architecture and potential vulnerabilities of your application, identify the threats that could affect the application.
-
Document the threats .
Document each threat using a common threat template that defines a core set of attributes to capture for each threat.
-
Rate the threats .
Rate the threats to prioritize and address the most significant threats first. These threats present the biggest risk. The rating process weighs the probability of the threat against damage that could result should an attack occur. It might turn out that certain threats do not warrant any action when you compare the risk posed by the threat with the resulting mitigation costs.
The Output
The output from the threat modeling process is a document for the various members of your project team. It allows them to clearly understand the threats that need to be addressed and how to address them. Threat models consist of a definition of the architecture of your application and a list of threats for your application scenario, as Figure 3.2 shows.
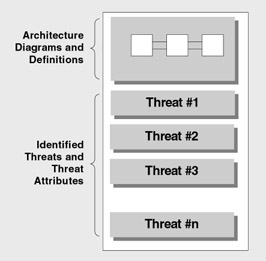
Figure 3.2: Components of the threat model
EAN: 2147483647
Pages: 613
- Executing Corporate Strategy with Lean Six Sigma
- Success Story #3 Fort Wayne, Indiana From 0 to 60 in nothing flat
- Success Story #4 Stanford Hospital and Clinics At the forefront of the quality revolution
- Raising the Stakes in Service Process Improvement
- Designing World-Class Services (Design for Lean Six Sigma)