Risk-Assessment Terminology
In the previous chapter, the basic elements of risk in an IT infrastructure were identified as assets, threats, and vulnerabilities. Assets typically are items of quantitative or qualitative value to an organization. This can include computers, network equipment, hardware, software, applications, and data assets. One of the most important reasons for conducting a risk assessment on an IT infrastructure and its assets is to assist the organization in adequately managing risk. Risk assessments are a critical component of an overall risk-management strategy for an IT infrastructure and its assets. Developing a risk-management strategy helps organizations manage and mitigate risk to threats and vulnerabilities that are uncovered and identified during the risk and vulnerability assessment. Thus, a risk assessment is a major component of an organization's overall risk-management strategy. Because IT infrastructures grow and evolve, risk management for an organization must include periodic risk assessments. As more and more IT systems, applications, and data assets are implemented, mitigating risk for these production IT assets becomes increasingly important.
Risk-assessment and risk-management terminology include the following terms and definitions:
- Acceptable risk A term used to describe the minimum acceptable risk that an organization is willing to take.
- Countermeasure or safeguards Controls, processes, procedures, or security systems that help to mitigate potential risk.
- Exposure When an asset is vulnerable to damage or losses from a threat.
- Exposure factor A value calculated by determining the percentage of loss to a specific asset because of a specific threat.
- Residual risk The risk that remains after security controls and security countermeasures have been implemented.
- Risk management The process of reducing risk to IT assets by identifying and eliminating threats through the deployment of security controls and security countermeasures.
- Risk analysis The process of identifying the severity of potential risks, identifying vulnerabilities, and assigning a priority to each. This may be done in preparation for the implementation of security countermeasures designed to mitigate high-priority risks.
Risk-Management and Risk-Assessment Requirements
As defined previously, risk management is a process for reducing risk to IT infrastructures and IT assets by identifying and eliminating threats through the deployment of security controls and security countermeasures. Risk management is an ongoing and everyday responsibility for an IT infrastructure and its assets. Because risk assessments are usually done after the fact and on an existing IT infrastructure and its production systems, applications, and data, many organizations attempt to address risk management early in the development life cycle, prior to IT systems, applications, and data being implemented in production. This is the best way to mitigate risk in production IT systems, applications, and data, given the many software vulnerabilities that exist. One approach to risk management is to incorporate it into the system design and system architecture phases of development. By mitigating the bugs and flaws in firmware, operating systems, and applications, exposure to risk from software vulnerabilities can be minimized. Mitigating bugs in software requires incorporating security controls in the software development life cycle (SDLC) as described in the previous chapter.
Ongoing risk management includes conducting periodic risk and vulnerability assessments on an organization's IT infrastructure and assets. Risk and vulnerability assessments can be approached in different ways, depending on the environment and the IT infrastructure. Risk-assessment approaches are best looked at by understanding the landscape first. This landscape is depicted in the sevenareas of information security responsibility described in the previous chapter in Figure 3.4. These seven areas require proper security controls and security countermeasures within each area to mitigate risk from threats and vulnerabilities to the overall IT infrastructure. By conducting a periodic risk assessment, the IT organization will know exactly how vulnerable the IT infrastructure and its assets are, and proper remediation can be planned.
Each of the seven areas of information security responsibility has its own risk-mitigation issues that must be analyzed uniquely as well as collectively from an organizational perspective. When identifying and locating an organization's assets, the entire IT infrastructure must be examined, including the end users and IT support staff. By conducting a risk assessment, an organization will be able to align its minimum acceptable level of risk for the IT infrastructure and its mission-critical IT assets with proper risk-mitigation techniques, security controls, and security countermeasures.
Defense-in-Depth Approach for Risk Assessments
Another way of looking at the IT infrastructure and its risk mitigation is to examine the security of an IT infrastructure in a layered fashion. This layered approach to risk mitigation is referred to as defense-in-depth. Defense-in-depth is the practice of layering, like an onion, the defenses and security countermeasures into zones, thus distributing the responsibility and accountability for information security over the seven areas of information security responsibility. This multilayered approach to information security provides layers of additional security controls and security countermeasures to slow down as well as mitigate the risk of an internal or external attack. A layered IT security infrastructure plan allows for compartmentalized safeguards and security countermeasures. The overall aggregate security level would be a combination of the defense-in-depth layers, provided they were implemented properly. The security controls and security countermeasures that are implemented throughout the IT infrastructure should be designed so that a failure in one safeguard is covered by anotherhence, the layered approach to security. This defense-in-depth approach truly combines the capabilities of people, operations, and security technologies to establish multiple layers of protection, eliminate single lines of defense, and enhance the overall security of the IT infrastructure and its assets.
These layers of protection extend to specific, critical defensive zones commonly found in defense-in-depth risk mitigation approaches:
- Data defenses Security controls and security countermeasures that protect an organization's data assets, such as encryption technology of data within a database.
- Application defenses Security controls and security countermeasuresthat protect an organization's systems and applications, such as deploying firewalls and IP-based Virtual Private Network (VPN) technology to minimize authorized traffic to specific source IP addresses and authentication capabilities.
- Operating system defenses Security controls with automated software patch management deployments that harden server and workstation operating systems with all security software patches.
- Network infrastructure defenses Perimeter defenses with audit and monitoring at all ingress/egress points in a network infrastructure.
Figure 4.1 shows the defense-in-depth or layered approach to information security controls and security countermeasures.
Figure 4.1. Defense-in-depth approach to information security.
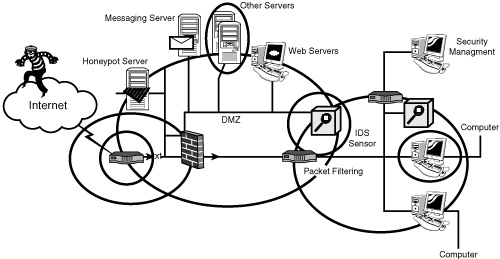
The defense-in-depth approach to risk mitigation can best be supported by conducting periodic risk assessments within each layer of the defense-in-depth information security implementation. Conducting a risk assessment on an IT infrastructure that incorporates defense-in-depth strategies allows the IT security professional to focus the assessment on each layer or area within the overall IT infrastructure. Risk assessments are a critical function for the proper implementation and deployment of a defense-in-depth strategy because an organization may knowingly be able to implement security controls and security countermeasures only in specific locations within the IT infrastructure. Conducting a risk assessment will assist the IT organization in addressing the gaps and voids that are uncovered during the assessment, and proper risk-mitigation techniques can be deployed strategically throughout the defense-in-depth layered infrastructure.
Risk Analysis Approach for Risk Assessments
After an IT infrastructure's systems, applications, data, and assets are identified, inventoried, and prioritized by the organization, conducting a risk analysis on those IT assets is required. The process of determining the objective and subjective value of IT assets, the identification of specific threats to them, and the loss or impact to the organization if a threat to the IT asset is realized is part of the risk analysis. This loss or impact to the organization is calculated using either a quantitative or qualitative risk-assessment approach. The results will be a report to management identifying the elements of greatest risk to an IT infrastructure and its assets. This will allow management to make sound business decisions pertaining to the deployment of security controls and security countermeasures to achieve the confidentiality, integrity, and availability goals of the organization.
The following list summarizes the risk-analysis life cycle, which is part of the overall process for conducting a risk assessment on an IT infrastructure and its assets:
- Asset identification An accurate and detailed inventory of IT assets, hardware, software, systems, applications, data, disk storage, and miscellaneous equipment.
- Asset valuation After assets are identified, placing an asset value in dollars or assigning an asset weighted factor value allow an organization's IT assets to be prioritized from highest importance to lowest.
- Threat identification Although there are a multitude of threats to an IT asset, this step in the process requires identifying all possible threats or vulnerabilities for each IT asset identified in the asset inventory. This threat identification or valuation step allows the organization to assess the impact of a threat being realized.
- Impact or financial loss calculation The final step in the risk analysis exercise is to assess the potential impact of a threat to an IT asset and the IT infrastructure and organization and calculate the potential for financial loss.
Asset Valuation Approach for Risk Assessments
Risk analysis requires the identification of an IT infrastructure's assets, including data assets and their valuation. Asset valuation is an important task to conduct as part of an organization's ongoing risk management strategy. Asset valuation is important for the following reasons:
- Helps prioritize IT asset recovery An organization's IT asset valuation provides useful information about an organization's most critical systems, resources, applications, and data, thus providing valuable information for prioritizing investments for security controls and security countermeasures.
- Assists in the justification for security controls and countermeasures Many organizations need to justify the investment needed for proper security controls and security countermeasures. A proper asset valuation will assist an organization's management team in making business decisions regarding deployment of security controls and security countermeasures.
- Assists in assessing how much insurance to purchase for the IT infrastructure and its assets After an asset valuation is completed, an organization will be able to accurately assess its business insurance requirements.
- Provides financial valuations for the organization to conduct ROI and cost-benefit analyses Without an IT asset valuation, it is difficult to conduct a Return On Investment (ROI) or cost-benefit analysis pertaining to the investment in security controls and security countermeasures.
There are two methods for conducting an asset valuation. Deciding which one to use is important because it also represents the foundation for which risk-assessment approach an organization will use. Asset valuation for an IT infrastructure and its assets can be approached either qualitatively or quantitatively.
- A qualitative valuation is a subjective determination of an IT asset's value to the organization. This is usually accomplished by creating a valuation model or system that prioritized the criticality or importance of an IT asset to the organization. The qualitative value of an IT asset will include consideration of how critical the IT asset is to the organization, its intellectual property value, or its market value.
- A quantitative valuation identifies actual market value for an organization's IT assets. The quantitative value of an asset will include the monetary expenditures required for purchasing and maintenance of the IT asset itself. This may also include such costs as licensing or development and deployments costs, user training, documentation, and upgrades.
At this stage in the risk analysis, identifying all the possible threats to the IT assets can be completed next. It is important that at this stage, all threats are considered and listed. Threats may be categorized in many ways. The best categorization is one that readily fits the needs of the organization. Within these categories will be more specific threats. Information may be available from users, auditors, system administrators with trust relationships, and information sites such as www.cert.org. After the threats have been identified, they must be ranked in order of the magnitude of the impact if they are realized, as well as the likelihood. Because there are so many threats in the IT environment, this ranking may be facilitated by associating the threats that are relevant to vulnerabilities in your particular IT assets. Known vulnerabilities in your software are examples of this.
Introduction to Assessing Network Vulnerabilities
- Introduction to Assessing Network Vulnerabilities
- What Security Is and Isnt
- Process for Assessing Risk
- Four Ways in Which You Can Respond to Risk
- Network Vulnerability Assessment
Foundations and Principles of Security
- Foundations and Principles of Security
- Basic Security Principles
- Security Requires Information Classification
- The Policy Framework
- The Role Authentication, Authorization, and Accountability Play in a Secure Organization
- Encryption
- Security and the Employee (Social Engineering)
Why Risk Assessment
- Why Risk Assessment
- Risk Terminology
- Laws, Mandates, and Regulations
- Risk Assessment Best Practices
- Understanding the IT Security Process
- The Goals and Objectives of a Risk Assessment
Risk-Assessment Methodologies
- Risk-Assessment Methodologies
- Risk-Assessment Terminology
- Quantitative and Qualitative Risk-Assessment Approaches
- Best Practices for Quantitative and Qualitative Risk Assessment
- Choosing the Best Risk-Assessment Approach
- Common Risk-Assessment Methodologies and Templates
Scoping the Project
- Scoping the Project
- Defining the Scope of the Assessment
- Reviewing Critical Systems and Information
- Compiling the Needed Documentation
- Making Sure You Are Ready to Begin
Understanding the Attacker
- Understanding the Attacker
- Who Are the Attackers?
- What Do Attackers Do?
- Reducing the Risk of an Attack
- How to Respond to an Attack
Performing the Assessment
- Performing the Assessment
- Introducing the Assessment Process
- Level I Assessments
- Level II Assessments
- Level III Assessments
Tools Used for Assessments and Evaluations
- Tools Used for Assessments and Evaluations
- A Brief History of Security Tools
- Putting Together a Toolkit
- Determining What Tools to Use
Preparing the Final Report
- Preparing the Final Report
- Preparing for Analysis
- Ranking Your Findings
- Building the Final Report
- Contents of a Good Report
- Determining the Next Step
- Audit and Compliance
Post-Assessment Activities
- Post-Assessment Activities
- IT Security Architecture and Framework
- Roles, Responsibilities, and Accountabilities
- Security Incident Response Team (SIRT)
- Vulnerability Management
- Training IT Staff and End Users
Appendix A. Security Assessment Resources
Appendix B. Security Assessment Forms
- Information Request Form
- Document Tracking Form
- Critical Systems and Information Forms
- Level II Assessment Forms
Appendix C. Security Assessment Sample Report
- Appendix C. Security Assessment Sample Report
- Notice
- Executive Summary
- Statement of Work
- Analysis
- Recommendations
- Conclusions
Appendix D. Dealing with Consultants and Outside Vendors
- Appendix D. Dealing with Consultants and Outside Vendors
- Procurement Terminology
- Typical RFP Procurement Steps
- Procurement Best Practices
Appendix E. SIRT Team Report Format Template
EAN: 2147483647
Pages: 138
