Auditing
Auditing gives you a way to track potential security problems, helps to ensure user accountability, and provides evidence in the event of a security breach. To audit effectively, you need to establish an audit policy. This requires you to determine which categories of events, which objects, and which accesses you want to audit.
Establish a Strategy
Your policy should be based on a strategy. For instance, you might decide that you are interested in a record of who accessed the system or specific data on the system, or that you are interested in detecting unauthorized attempts to tamper with the operating system.
Common Events to Be Audited
The most common types of events to be audited are the following:
-
Users logging on to and logging off the system
-
Management of user accounts and groups
-
Accesses of objects, such as files and folders
Implementing Auditing Policy
When you implement auditing policy, keep the following points in mind:
-
Develop your audit strategy. Decide which behaviors you want to audit.
-
Select the audit categories that correspond to your auditing strategy, and no more.
-
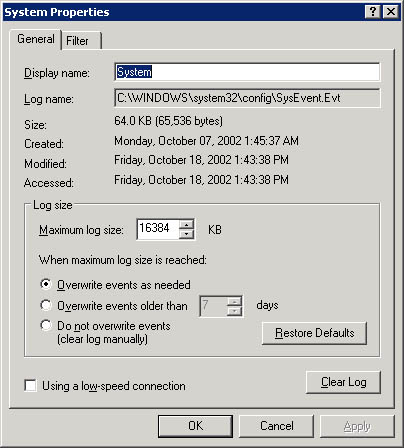
Select an appropriate size and retention policy for the security log. You can view the security log and set the log size and retention policy with Event Viewer, as shown in Figure 5-2.
-
If you have decided to audit directory service access or object access, determine which objects must be monitored as part of your strategy. Also determine the minimum number of accesses you need to audit to fulfill the goals of your strategy. You shouldn't audit any more objects or accesses than necessary because a too-broad audit selection could cause audit logs to fill very rapidly on a busy machine.
-
Deploy your policy. You can do this with the Local Security Policy tool on a stand-alone machine or with Group Policy on a domain.
-
Review your security logs regularly. There's no point in auditing if you're never going to look at your logs. An event log collection system can help make this a manageable task.
-
Fine-tune your policy as necessary. This might include adding or removing objects or accesses to your audit policy, or enabling or disabling audit categories. After reviewing your logs, you might find that you have collected more or less information than you want.
Figure 5-2. Administrators can easily configure the event log's size and retention policy.
| |
| Top |
EAN: 2147483647
Pages: 153