Digital Signatures
14.5 Digital Signatures
So far, we've been talking about various kinds of keyed ciphers, using symmetric and asymmetric keys, to allow us to encrypt and decrypt secret messages.
In addition to encrypting and decrypting messages, cryptosystems can be used to sign messages, proving who wrote the message and proving the message hasn't been tampered with. This technique, called digital signing, is important for Internet security certificates, which we discuss in the next section.
14.5.1 Signatures Are Cryptographic Checksums
Digital signatures are special cryptographic checksums attached to a message. They have two benefits:
Signatures prove the author wrote the message. Because only the author has the author's top-secret private key,[8] only the author can compute these checksums. The checksum acts as a personal "signature" from the author.
[8] This assumes the private key has not been stolen. Most private keys expire after a while. There also are "revocation lists" that keep track of stolen or compromised keys.
Signatures prevent message tampering. If a malicious assailant modified the message in-flight, the checksum would no longer match. And because the checksum involves the author's secret, private key, the intruder will not be able to fabricate a correct checksum for the tampered-with message.
Digital signatures often are generated using asymmetric, public-key technology. The author's private key is used as a kind of "thumbprint," because the private key is known only by the owner.
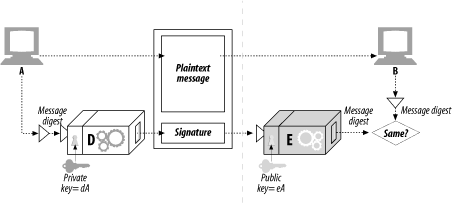
Figure 14-10 shows an example of how node A can send a message to node B and sign it:
Node A distills the variable-length message into a fixed-sized digest.
Node A applies a "signature" function to the digest that uses the user's private key as a parameter. Because only the user knows the private key, a correct signature function shows the signer is the owner. In Figure 14-10, we use the decoder function D as the signature function, because it involves the user's private key.[9]
[9] With the RSA cryptosystem, the decoder function D is used as the signature function, because D already takes the private key as input. Note that the decoder function is just a function, so it can be used on any input. Also, in the RSA cryptosystem, the D and E functions work when applied in either order and cancel each other out. So, E(D(stuff )) = stuff, just as D(E(stuff )) = stuff.
Once the signature is computed, node A appends it to the end of the message and sends both the message and the signature to node B.
On receipt, if node B wants to make sure that node A really wrote the message, and that the message hasn't been tampered with, node B can check the signature. Node B takes the private-key scrambled signature and applies the inverse function using the public key. If the unpacked digest doesn't match node B's own version of the digest, either the message was tampered with in-flight, or the sender did not have node A's private key (and therefore was not node A).
Figure 14-10. Unencrypted digital signature
EAN: 2147483647
Pages: 294