Digital Certificates
14.6 Digital Certificates
In this section, we talk about digital certificates, the "ID cards" of the Internet. Digital certificates (often called "certs," like the breath mints) contain information about a user or firm that has been vouched for by a trusted organization.
We all carry many forms of identification. Some IDs, such as passports and drivers' licenses, are trusted enough to prove one's identity in many situations. For example, a U.S. driver's license is sufficient proof of identity to let you board an airplane to New York for New Year's Eve, and it's sufficient proof of your age to let you drink intoxicating beverages with your friends when you get there.
More trusted forms of identification, such as passports, are signed and stamped by a government on special paper. They are harder to forge , so they inherently carry a higher level of trust. Some corporate badges and smart cards include electronics to help strengthen the identity of the carrier. Some top-secret government organizations even need to match up your fingerprints or retinal capillary patterns with your ID before trusting it!
Other forms of ID, such as business cards, are relatively easy to forge, so people trust this information less. They may be fine for professional interactions but probably are not enough proof of employment when you apply for a home loan.
14.6.1 The Guts of a Certificate
Digital certificates also contain a set of information, all of which is digitally signed by an official "certificate authority." Basic digital certificates commonly contain basic things common to printed IDs, such as:
Subject's name (person, server, organization, etc.)
Expiration date
Certificate issuer (who is vouching for the certificate)
Digital signature from the certificate issuer
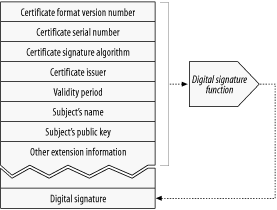
Additionally, digital certificates often contain the public key of the subject, as well as descriptive information about the subject and about the signature algorithm used. Anyone can create a digital certificate, but not everyone can get a well-respected signing authority to vouch for the certificate's information and sign the certificate with its private key. A typical certificate structure is shown in Figure 14-11 .
Figure 14-11. Typical digital signature format
14.6.2 X.509 v3 Certificates
Unfortunately, there is no single, universal standard for digital certificates. There are many, subtly different styles of digital certificates, just as not all printed ID cards contain the same information in the same place. The good news is that most certificates in use today store their information in a standard form, called X.509 v3. X.509 v3 certificates provide a standard way of structuring certificate information into parseable fields. Different kinds of certificates have different field values, but most follow the X.509 v3 structure. The fields of an X.509 certificate are described in Table 14-2 .
Table 14-2. X.509 certificate fields | |
| Field | Description |
| Version | The X.509 certificate version number for this certificate. Usually version 3 today. |
| Serial Number | A unique integer generated by the certification authority. Each certificate from a CA must have a unique serial number. |
| Signature Algorithm ID | The cryptographic algorithm used for the signature. For example, "MD2 digest with RSA encryption". |
| Certificate Issuer | The name for the organization that issued and signed this certificate, in X.500 format. |
| Validity Period | When this certificate is valid, defined by a start date and an end date. |
| Subject's Name | The entity described in the certificate, such as a person or an organization. The subject name is in X.500 format. |
| Subject's Public Key Information | The public key for the certificate's subject, the algorithm used for the public key, and any additional parameters. |
| Issuer Unique ID (optional) | An optional unique identifier for the certificate issuer, to allow the potential reuse of the same issuer name. |
| Subject Unique ID (optional) | An optional unique identifier for the certificate subject, to allow the potential reuse of the same subject name. |
| Extensions | An optional set of extension fields (in version 3 and higher). Each extension field is flagged as critical or noncritical. Critical extensions are important and must be understood by the certificate user. If a certificate user doesn't recognize a critical extension field, it must reject the certificate. Common extension fields in use include: Basic Constraints Subject's relationship to certification authority Certificate Policy The policy under which the certificate is granted Key Usage Restricts how the public key can be used |
| Certification Authority Signature | The certification authority's digital signature of all of the above fields, using the specified signing algorithm. |
There are several flavors of X.509-based certificates, including (among others) web server certificates, client email certificates, software code-signing certificates, and certificate authority certificates.
14.6.3 Using Certificates to Authenticate Servers
When you establish a secure web transaction through HTTPS, modern browsers automatically fetch the digital certificate for the server being connected to. If the server does not have a certificate, the secure connection fails. The server certificate contains many fields, including:
Name and hostname of the web site
Public key of the web site
Name of the signing authority
Signature from the signing authority
When the browser receives the certificate, it checks the signing authority. [10] If it is a public, well-respected signing authority, the browser will already know its public key (browsers ship with certificates of many signing authorities preinstalled ), so it can verify the signature as we discussed in the previous section, Section 14.5 . Figure 14-12 shows how a certificate's integrity is verified using its digital signature.
[10] Browsers and other Internet applications try hard to hide the details of most certificate management, to make browsing easier. But, when you are browsing through secure connections, all the major browsers allow you to personally examine the certificates of the sites to which you are talking, to be sure all is on the up-and-up.
Figure 14-12. Verifying that a signature is real
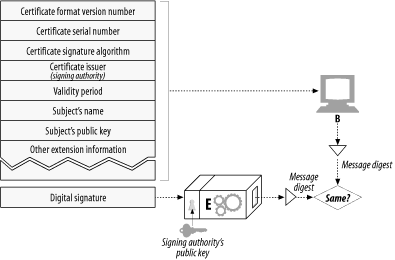
If the signing authority is unknown, the browser isn't sure if it should trust the signing authority and usually displays a dialog box for the user to read and see if he trusts the signer. The signer might be the local IT department, or a software vendor.
EAN: 2147483647
Pages: 294