Public-Key Cryptography
14.4 Public-Key Cryptography
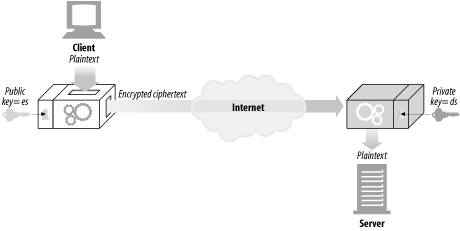
Instead of a single encoding/decoding key for every pair of hosts, public-key cryptography uses two asymmetric keys: one for encoding messages for a host, and another for decoding the host's messages. The encoding key is publicly known to the world (thus the name public-key cryptography), but only the host knows the private decoding key (see Figure 14-8). This makes key establishment much easier, because everyone can find the public key for a particular host. But the decoding key is kept secret, so only the recipient can decode messages sent to it.
Figure 14-8. Public-key cryptography is asymmetric, using different keys for encoding and decoding
Node X can take its encoding key ex and publish it publicly.[7] Now anyone wanting to send a message to node X can use the same, well-known public key. Because each host is assigned an encoding key, which everyone uses, public-key cryptography avoids the N2 explosion of pairwise symmetric keys (see Figure 14-9).
[7] As we'll see later, most public-key lookup actually is done through digital certificates, but the details of how you find public keys don't matter much nowjust know that they are publicly available somewhere.
Figure 14-9. Public-key cryptography assigns a single, public encoding key to each host
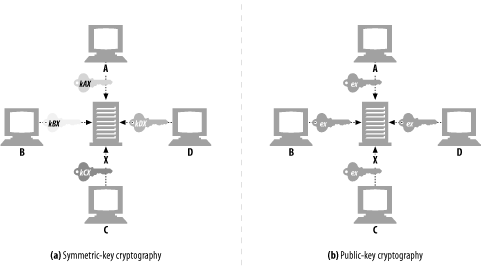
Even though everyone can encode messages to X with the same key, no one other than X can decode the messages, because only X has the decoding private key dx. Splitting the keys lets anyone encode a message but restricts the ability to decode messages to only the owner. This makes it easier for nodes to securely send messages to servers, because they can just look up the server's public key.
Public-key encryption technology makes it possible to deploy security protocols to every computer user around the world. Because of the great importance of making a standardized public-key technology suite, a massive Public-Key Infrastructure (PKI) standards initiative has been under way for well over a decade.
14.4.1 RSA
The challenge of any public-key asymmetric cryptosystem is to make sure no bad guy can compute the secret, private keyeven if he has all of the following clues:
The public key (which anyone can get, because it's public)
A piece of intercepted ciphertext (obtained by snooping the network)
A message and its associated ciphertext (obtained by running the encoder on any text)
One popular public-key cryptosystem that meets all these needs is the RSA algorithm, invented at MIT and subsequently commercialized by RSA Data Security. Given a public key, an arbitrary piece of plaintext, the associated ciphertext from encoding the plaintext with the public key, the RSA algorithm itself, and even the source code of the RSA implementation, cracking the code to find the corresponding private key is believed to be as hard a problem as computing huge prime numbersbelieved to be one of the hardest problems in all of computer science. So, if you can find a fast way of factoring large numbers into primes, not only can you break into Swiss bank accounts, but you can also win a Turing Award.
The details of RSA cryptography involve some tricky mathematics, so we won't go into them here. There are plenty of libraries available to let you perform the RSA algorithms without you needing a Ph.D. in number theory.
14.4.2 Hybrid Cryptosystems and Session Keys
Asymmetric, public-key cryptography is nifty, because anyone can send secure messages to a public server, just by knowing its public key. Two nodes don't first have to negotiate a private key in order to communicate securely.
But public-key cryptography algorithms tend to be computationally slow. In practice, mixtures of both symmetric and asymmetric schemes are used. For example, it is common to use public-key cryptography to conveniently set up secure communication between nodes but then to use that secure channel to generate and communicate a temporary, random symmetric key to encrypt the rest of the data through faster, symmetric cryptography.
EAN: 2147483647
Pages: 294