Adopting Claims-based Authorization
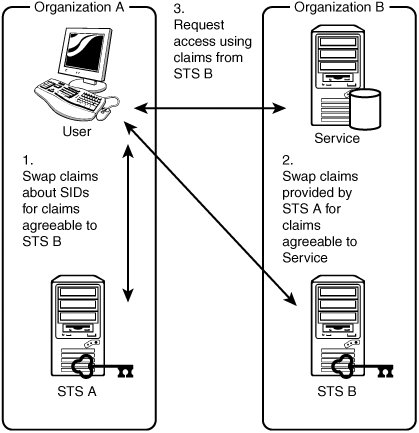
| However, despite these advantages of claims-based authorization over role-based authorization and access control lists, one should not necessarily eschew role-based authorization and access control lists in favor of claims-based authorization. The use of role-based authorization and access control lists is supported by a vast number of powerful tools. Many such tools are built into Microsoft Windows and their use is customary among network administrators. Support for claims-based authorization is mostly limited to XSI. So instead of seeing claims-based authorization as a superior alternative to role-based authorization and access control lists, a wiser approach would be to use them together, leveraging their respective strengths where it is most appropriate to do so. Claims-based authorization is especially effective for controlling access to resources across platforms and between organizations. Therefore, in cases in which the users of one organization need to access resources managed by the systems of another organization, have them exchange their access tokens for claims that the other organization can use to decide whether to grant the users access. How exactly might such a solution be implemented? Well, the Web Services Trust Language (WS-Trust) is a standard language for requesting and issuing claim sets. A system that issues claim sets in accordance with that language is called a security token service (STS) (Gudgin and Nadalin 2005, 7; Cabrera and Kurt 2005, 24-27). An organization whose users need to access the facilities of another organization's systems could provide their users with an STS from which they could request claim sets that the other organization's systems would understand. That STS would take the claims constituted by the SIDs in the users' access tokens and apply an authorization policy that would yield claims with types, rights, and values agreed on with the other organization. That other organization would provide a second STS to accept those claims and apply an authorization policy of its own to yield claims that the other systems within that organization could then use to decide whether to grant a user access to their resources. This solution is depicted in Figure 4.1. The approach has several important virtues. Figure 4.1. Cross-organization claims-based authorization. First, trust relationships are minimized and the management of them is centralized. Specifically, the services with resources to protect need to trust the claims from only a single issuer, namely, their own organization's STS. That STS can be configured to trust claims issued by any number of other organizations' STSs. Configuring an STS to trust claims issued by another organization's STS is simply a matter of giving it access to the other organization's public key. Second, the claims that one organization makes about its users attempting to access another organization's services are also hidden from the services by the authorization policy of the STS they trust. That STS applies the authorization policy to translate the claims made by the other organizations into claims that are familiar to the services. That process of translating the diverse sorts of claims that various organizations might make into the sorts of claims that are familiar to a suite of services is commonly referred to as claims normalization. Third, the administration of access to services is truly federated. Federation is the formation of a unity in which the participants retain control over their internal affairs (Oxford Dictionary of Current English 2001), thereby minimizing the cost of maintaining the unity. In this case, the addition or removal of users and the elevation or reduction in users' privileges by the system administrators in one organization will determine their rights to access the services of the other organization, without the system administrators of that other organization needing to be involved. This benefit will be vividly demonstrated in the following exercise. |
EAN: 2147483647
Pages: 132